CYB.ISP
5.0(1)
Card Sorting
1/136
Earn XP
Description and Tags
Cybersecurity Fundamentals
Last updated 7:13 PM on 11/23/22
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
137 Terms
1
New cards
Tranquility Principle
This principle states that the classification of a subject or object does not change while it is being referenced
2
New cards
Principle of strong tranquility
This principle states that security levels do not change during the normal operation of the system
3
New cards
Principle of weak tranquility
This principle states that security levels may never change in such a way as to violate a defined security policy
(It's also desirable as it allows systems to observe the principle of least privilege)
(It's also desirable as it allows systems to observe the principle of least privilege)
4
New cards
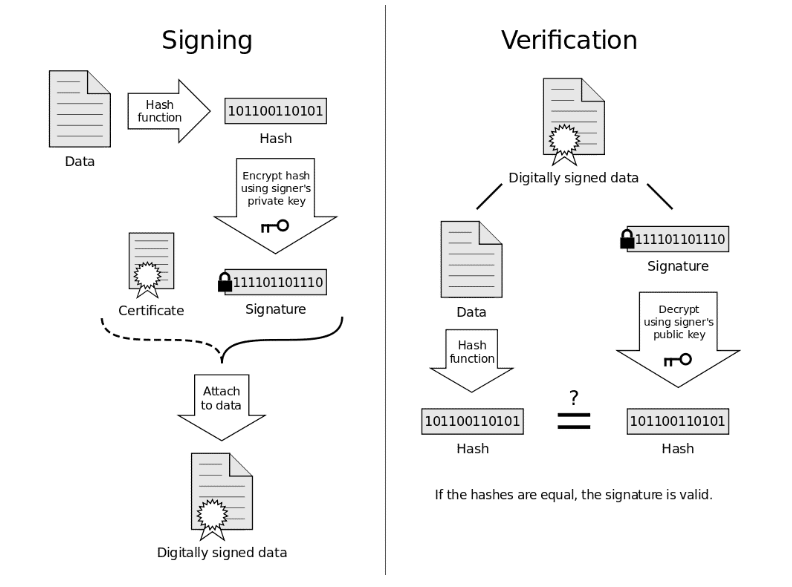
Digital Signatures
It lets the receiver know that the data was sent by a known sender (authentication) and that the message was not altered during transit (integrity)
5
New cards
Multi-Touch Verification System
A system that authenticates users by performing multi-touch gestures on a device's screen
6
New cards
Anonymity
The state of being not identifiable within a set of subjects
(The idea of hiding the aspects of metadata)
(The idea of hiding the aspects of metadata)
7
New cards
Anonymity Set
The group of people that you’re indistinguishable from
8
New cards
OWASP (Open Web Application Security Project)
An organization that collects information about how popular attacks are at a given time
9
New cards
Authentication
The act of proving one's identity to another entity
10
New cards
Two Factor Authentication (2FA)
An approach to authentication which requires the presentation of two different kinds of evidence that someone is who they say they are
11
New cards
Security Model
A model that defines essential aspects of security and their relationship with the OS and its performance
12
New cards
Bell-LaPadula (BLP) Security Model
A security model that provides confidentiality to a system
13
New cards
BLP's simple security property
This security property states that a subject at a given security level may not read an object at a higher security level (NO READ UP)
14
New cards
BLP's * security property
This security property states that a subject at a given security level may not write to any object at a lower security level (NO WRITE DOWN)
15
New cards
BLP's strong * security property
This security property states that a subject at a given security level may only write to objects with a matching security level
16
New cards
BLP's discretionary security property
This security property uses an access matrix to specify the discretionary access control
17
New cards
Biba Integrity Security Model
This security model describes a set of access control rules designed to ensure data integrity by grouping objects and subjects into ordered levels of integrity
18
New cards
Biba's simple integrity property
This security property states that a subject at a given level of integrity must not read data at a lower integrity level (NO READ DOWN)
19
New cards
Biba's * integrity property
This security property states that a subject at a given level of integrity must not write to data at a higher integrity level (NO WRITE-UP)
20
New cards
Biba's invocation property
This security property states that a process from below cannot request higher access, only with subjects at an equal or lower integrity level
21
New cards
Lipner's Security Model
This security model combines the elements of the BLP and Biba models to provide confidentiality and integrity to the system
22
New cards
Separation of duty
Requiring at least two different people to perform the steps if two or more steps are required to perform the duty
23
New cards
Separation of function
Isolating the assets of an organization from each other based on function
24
New cards
Auditing
Analyzing systems to determine what actions took place and who performed them
25
New cards
Clark-Wilson Integrity Security Model
This security model, based on the notion of a transaction, provides a foundation for specifying and analyzing an integrity policy for a computing system
(A well-formed transaction is a series of operations that transition a system from one consistent state to another consistent state)
(A well-formed transaction is a series of operations that transition a system from one consistent state to another consistent state)
26
New cards
Chinese Wall Security Model
This security model concentrates on confidentiality that helps prevent there from being conflicts of interest between different businesses and organizations
27
New cards
Operating System
The software that supports a computer's basic functions, such as scheduling tasks, executing applications, and controlling peripherals
28
New cards
MULTICS
A time-sharing operating system that allowed multiple Processes to use the same machine all at once
(This meant that no one could not make superficial assumptions about one Process not being able to access the memory or state of another)
(This meant that no one could not make superficial assumptions about one Process not being able to access the memory or state of another)
29
New cards
UNIX
It's the modern successor to MULTICS and a multiuser, multitasking OS designed for flexibility and adaptability
30
New cards
Process Isolation
Making sure that two or more processes that are running on the same machine do not interfere with each other in any way, but still have ways of communicating with each other
31
New cards
Hash Value/Digest
A fixed-length code sequence outputted by a hash function
32
New cards
Hashing
A one-way process that maps variable-length data to a fixed-length hash
33
New cards
Hash Function
An algorithm that takes a piece of data as input and outputs a hash value
34
New cards
Weak-collision resistance property
Given an input X and a hashing function H(), it's very difficult to find another input Y on which H(X) == H(Y)
Hint: Hash functions have this resistance property
Hint: Hash functions have this resistance property
35
New cards
Strong-collision resistance property
Given a hashing function H() and two inputs X and Y, there exists an absolute minimum chance of H(X) == H(Y)
Hint: Hash functions have this resistance property
Hint: Hash functions have this resistance property
36
New cards
One-wayness property
Being able to compute hashes given the original data as input but not being able to restore it back to the original data by passing its hash value through the hashing function again
Hint: Hash functions have this security property
Hint: Hash functions have this security property
37
New cards
Collision
When different data inputs result in the same hash after being processed by a hashing function
38
New cards
Encryption
A way of translating data from plaintext (unencrypted) to ciphertext (encrypted)
39
New cards
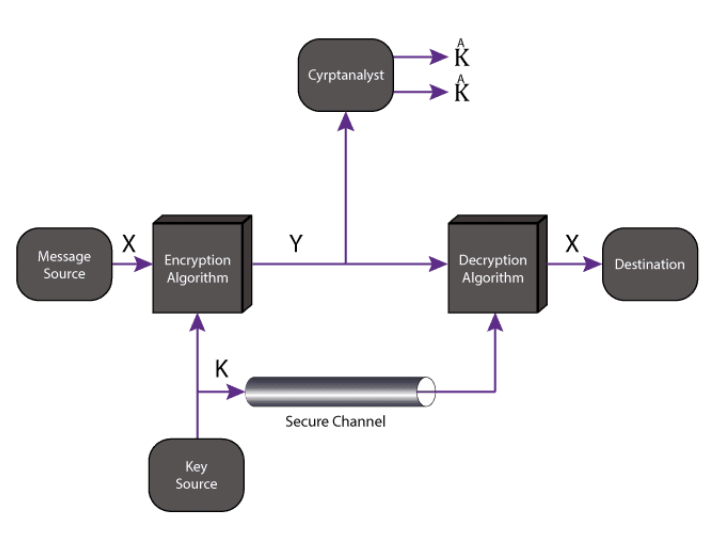
Symmetric (Private Key) Encryption
A type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic data
40
New cards
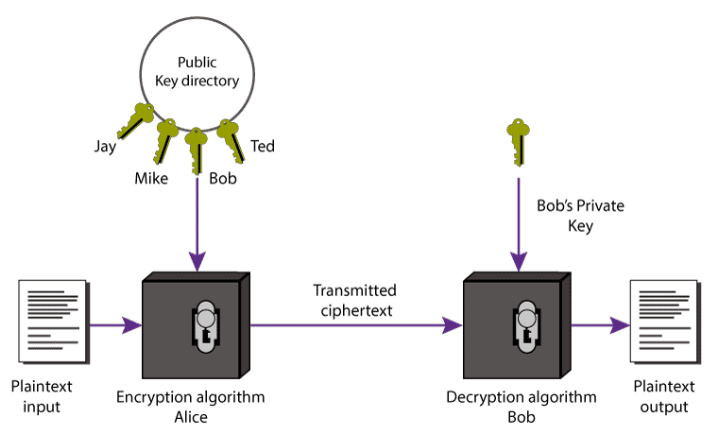
Asymmetric (Public Key) Encryption
A process that uses a pair of related keys (one public key and one private key) to encrypt and decrypt a message and protect it from unauthorized access or use
41
New cards
Pseudonymity
The use of pseudonyms as IDs that link all interactions with each other
42
New cards
CIA Triad
A threat model used for finding vulnerabilities and methods for creating solutions
43
New cards
Confidentiality
Ensures that there's no unauthorized disclosure of data (enforced through encryption)
44
New cards
Integrity
Ensures that there's no unauthorized modification of data (enforced through hashes)
45
New cards
Availability
Ensures that there's no unauthorized withholding of data (enforced through redundancy)
46
New cards
Virtualization
A process that allows for more efficient utilization of physical computer hardware by using software to create an abstraction layer over computer hardware that allows the hardware elements of a single computer to be divided into multiple virtual computers
(This technology drives the cloud computing economics)
(This technology drives the cloud computing economics)
47
New cards
Abstraction Layer
A generalization of a conceptual model or algorithm, away from the specific implementation / A way of hiding the working details of a subsystem
48
New cards
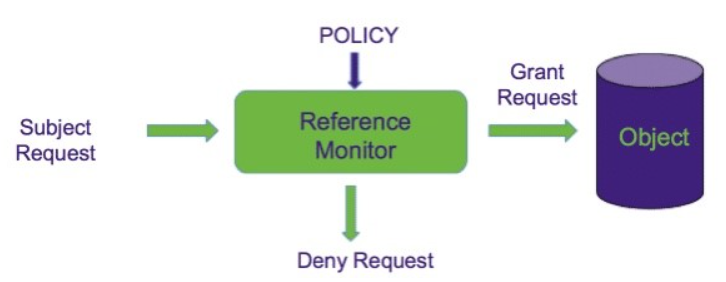
Reference Monitor
A secure, always used and fully testable module that controls all access to data objects and devices by verifying the nature of the request against a table of allowable access types and security policies for each process in the system
49
New cards
Custom Reference Monitor
Used to make decisions that's adapted to our system's security policies and adopted access control model
50
New cards
Virtual Machine (VM)
A computer resource that uses software instead of a physical computer to run programs and deploy applications
51
New cards
Virtual Guest Machine (Guest VM)
A virtual machine that is installed, executed and hosted on the local physical machine
52
New cards
Physical Host Machine
53
New cards
Hypervisor/Virtual Machine Monitor (VMM)
A software that creates and runs VMs by allowing one host computer to support multiple guest VMs by virtually sharing its resources, such as memory and processing
54
New cards
Type 1 Hypervisor (Type 1 VMM)
In this type of hypervisor, VM resources are scheduled directly to the hardware by the hypervisor
(This type of hypervisor is on bare metal)
(This type of hypervisor is on bare metal)
55
New cards
Type 2 Hypervisor (Type 2 VMM)
In this type of hypervisor, VM resources are scheduled against a host operating system, which is then executed against the hardware
(This type of hypervisor is hosted)
(This type of hypervisor is hosted)
56
New cards
Security Design Principles
Principles that help make systems as free of Vulnerabilities and impervious to attacks and breaches
57
New cards
Principle of Open Design
A security design principle that states that your system shouldn't rely on the secrecy of your implementations, meaning that people should be able to comment on your code
58
New cards
Principle of Sweeping Simplification/Keep It Simple Stupid!
A security design principle that states that your system's designs and interactions should be easy and simple
59
New cards
Principle of Design for Iterations
A security design principle that states that you design your software to ensure you can change parts of it in the future, in case you need to
60
New cards
Principle of Least Astonishment
A security design principle that states that you create something that follows what the user would expect to happen in a given situation
61
New cards
Principle of Minimizing Secrets
A security design principle that states that you minimize the size, quantity and complexity of what is to be protected, and limit externally facing points of attack
62
New cards
Principle of Least Privilege
A security design principle that states that an entity should have exactly the permissions they need in order to fulfill their tasks
63
New cards
Principle of Complete Mediation
A security design principle that states that all access to objects should be checked to ensure that access is allowed
64
New cards
Principle of Least Common Mechanism
A security design principle that states that mechanisms used to access resources should not be shared
65
New cards
Principle of Fail-Safe Defaults
A security design principle that states that if some part of the system fails, it should default in a way that has the appropriate security guarantee for whatever it is you want to have happen, in order not to have your system compromised
(The idea is to "fail-close" in a way that does not compromise the system and its data rather than "fail-open", where the method of failing allows the attacker to achieve some objective)
(The idea is to "fail-close" in a way that does not compromise the system and its data rather than "fail-open", where the method of failing allows the attacker to achieve some objective)
66
New cards
Principle of Economy of Mechanisms
A security design principle that states that security mechanisms should be as simple as possible while still having the security properties that you need
67
New cards
Security Policy
A series of rules that must be followed in order to ensure the safety of an organization and its system
68
New cards
Inclusive Security Policies
These security policies specify a list of all the things that you're allowed to do and anything not mentioned is automatically disallowed
69
New cards
Exclusive Security Policies
These security policies specify a list of all the things that you're not allowed to do and anything not mentioned is automatically allowed
(This type of security policy requires you to update the policy more frequently since there's always a new technology that comes out)
(This type of security policy requires you to update the policy more frequently since there's always a new technology that comes out)
70
New cards
Security Mechanism
Something that enforces a security policy, either in whole or part
71
New cards
Mechanisms based on prevention
This type of security mechanism ensures that an aspect of a security policy cannot be violated
72
New cards
Mechanisms based on detection
This type of security mechanism determines whether a security policy has been violated
73
New cards
Mechanisms based on recovery
This type of security mechanism ensures that you're able to revert back to a secure state after a security policy has been violated
74
New cards
Information Flow Control
Controlling the flow of data in order to ensure its confidentiality by monitoring the shared data
75
New cards
Data Labels
These labels indicate the permitted information flows and specified set of policies for each piece of data
76
New cards
Data Confidentiality Constraints
This type of data labelling specifies a set of policies, such as who may read a given piece of data
Label example: {Alice: Bob, Eve; Charlie: Bob, Eve}
• Alice and Charlie conjointly own a given set of data
• Bob and Eve are permitted to read it
Label example: {Alice: Bob, Eve; Charlie: Bob, Eve}
• Alice and Charlie conjointly own a given set of data
• Bob and Eve are permitted to read it
77
New cards
Data Integrity Constraints
This type of data labelling specifies a set of policies, such as who may modify a given piece of data
Label Example: {Alice ? Bob}
• Alice owns the given set of data
• Bob is permitted to modify it
Label Example: {Alice ? Bob}
• Alice owns the given set of data
• Bob is permitted to modify it
78
New cards
Password
A secret string of characters that allows access to a computer system or service
79
New cards
One-Time Password (OTP)
A password that is valid for only one login session or transaction, on a computer system or other digital device
80
New cards
Software OTP
An OTP generated by the company and sent to your mobile phone or PC
• An event-based OTP (The moving factor is triggered by an event)
• An event-based OTP (The moving factor is triggered by an event)
81
New cards
Hardware OTP
An OTP generated by a security device/token
• A time-based OTP (The moving factor is time)
• A time-based OTP (The moving factor is time)
82
New cards
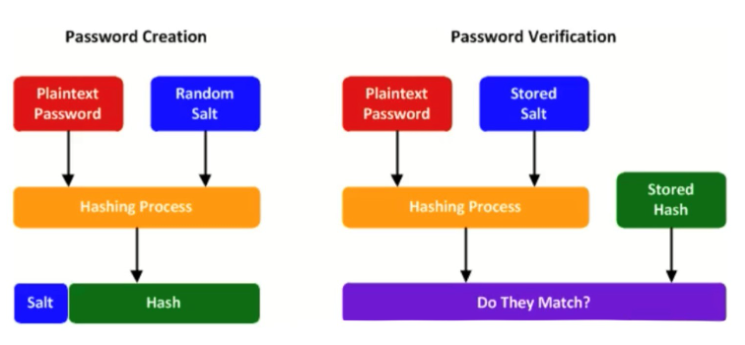
Password Salt
Adding a random value to a plaintext password before putting it through the hashing process
83
New cards
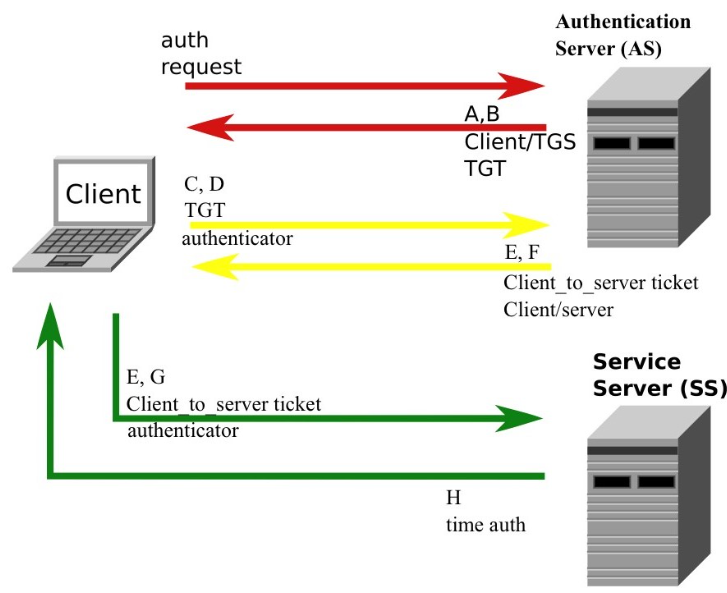
Kerberos
A protocol used to authenticate people on a network based on tickets
84
New cards
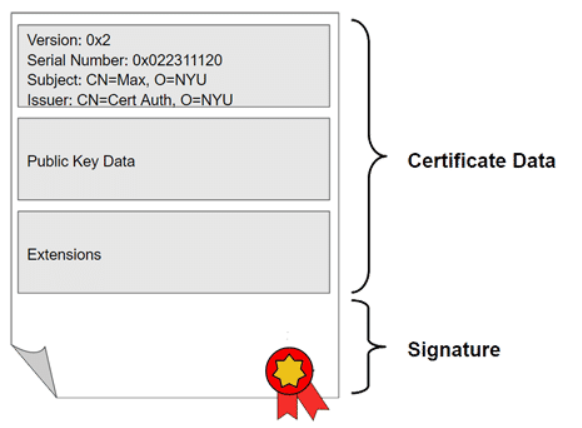
Digital Certificates
An electronic document used to prove the ownership of a Public key
85
New cards
Threat Model
This model helps you understand what can go wrong within a system and the potential vulnerabilities, threats, breaches and attacks
86
New cards
Threat Matrix
A threat modelling tool that allows us to model and subjectively categorize potential threats by applying a structured ranking process
87
New cards
Threat Tree
A threat modelling tool that can be used to calculate risk for any asset
88
New cards
Attack Tree
A threat modelling tool to visualize the security posture of a system and organize ideas about how attackers might attack
89
New cards
Access Control
A series of mechanisms to specify what users do, which resources they can access, and what operations they can perform on a system, as well as identifying users by verifying various login credentials
90
New cards
Access Control: Identification
An access control function method of establishing the subject's identity while being non-descriptive of their position or task
91
New cards
Access Control: Authentication
An access control function method of providing the claimed identity of an entity that has previously identified itself
92
New cards
Access Control: Authorization
An access control function process that determines what level of clearance and access the authenticated user has within the system and the data that they requested to log into or gain access
93
New cards
Access Control Mechanism
Takes as input security policies (What a subject is allowed to do and with what it may interact with) and attempted actions, and outputs an accept or reject response for that action
94
New cards
Access Control Form (ACF)
A method of access control used to request and change access responsibilities of entities within a system
95
New cards
Discretionary Access Control (DAC)
This method of access control is at the discretion of the owner of the resource
96
New cards
Mandatory Access Control (MAC)
This method of access control is based on a security labelling system, meaning users have security clearances and resources have security labels that contain data classifications
(This model is used in environments where information classification and confidentiality are very important)
(This model is used in environments where information classification and confidentiality are very important)
97
New cards
Non-Discretionary Role-Based Access Control (RBAC)
This method of access control uses a centrally administered set of controls to determine how subjects and objects interact
(It is the best know access control form for an organization that has a high turnover)
(It is the best know access control form for an organization that has a high turnover)
98
New cards
Content Dependent Access Control (CDAC)
This method of access control makes decisions based on the type of content contained in an object
(Access control decisions are content-dependent)
(Access control decisions are content-dependent)
99
New cards
Control Based Access Control (CBAC)
This method of access control makes decisions based on the context of a subject's request to an object
(This method of access control requires more information about the subject in order to make a decision, such as their identity, the object that they're requesting access to, etc.)
(This method of access control requires more information about the subject in order to make a decision, such as their identity, the object that they're requesting access to, etc.)
100
New cards
Access Control: Constrained User Interfaces (CUI)
A method of enforcing access control by constraining the user interface used to get access
(This can be done by not allowing certain types of access on the interface, or not including the ability to request certain types of access or objects)
(This can be done by not allowing certain types of access on the interface, or not including the ability to request certain types of access or objects)