2.4 Cryptographic Attacks
1/5
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
6 Terms
Cryptographic Attacks
A widely used technology that helps secure data, but its security depends largely on the encryption key.
Instead of targeting the key directly, attackers often focus on attacking the cryptographic system itself.
While modern cryptographic algorithms have proven secure over time, improper implementation can weaken the system and provide vulnerabilities for attackers to exploit
Birthday Attack
Based on the statistical phenomenon where, in a group of 23 people, there's about a 50% chance that two people share the same birthday.
In the digital world, this concept applies to hash collisions, where two different inputs (plaintexts) produce the same hash value.
Attackers can exploit this by using a brute-force method, generating various plaintexts and comparing their hashes to find duplicates.
To prevent this, using a large hash output size makes it more difficult for attackers to find matching hashes, reducing the likelihood of a successful attack.
Collisions
Occurs when two different plaintexts generate the same hash value
Ideally should not happen
The MD5 hash algorithm, once widely used, was found to be vulnerable to collisions
In 2008, researchers exploited this vulnerability by using 200 PlayStation 3 systems to create a forged Certificate Authority (CA).
This attack allowed them to generate a certificate for websites like www.amazon.com that would be trusted by browsers, despite being fraudulent.
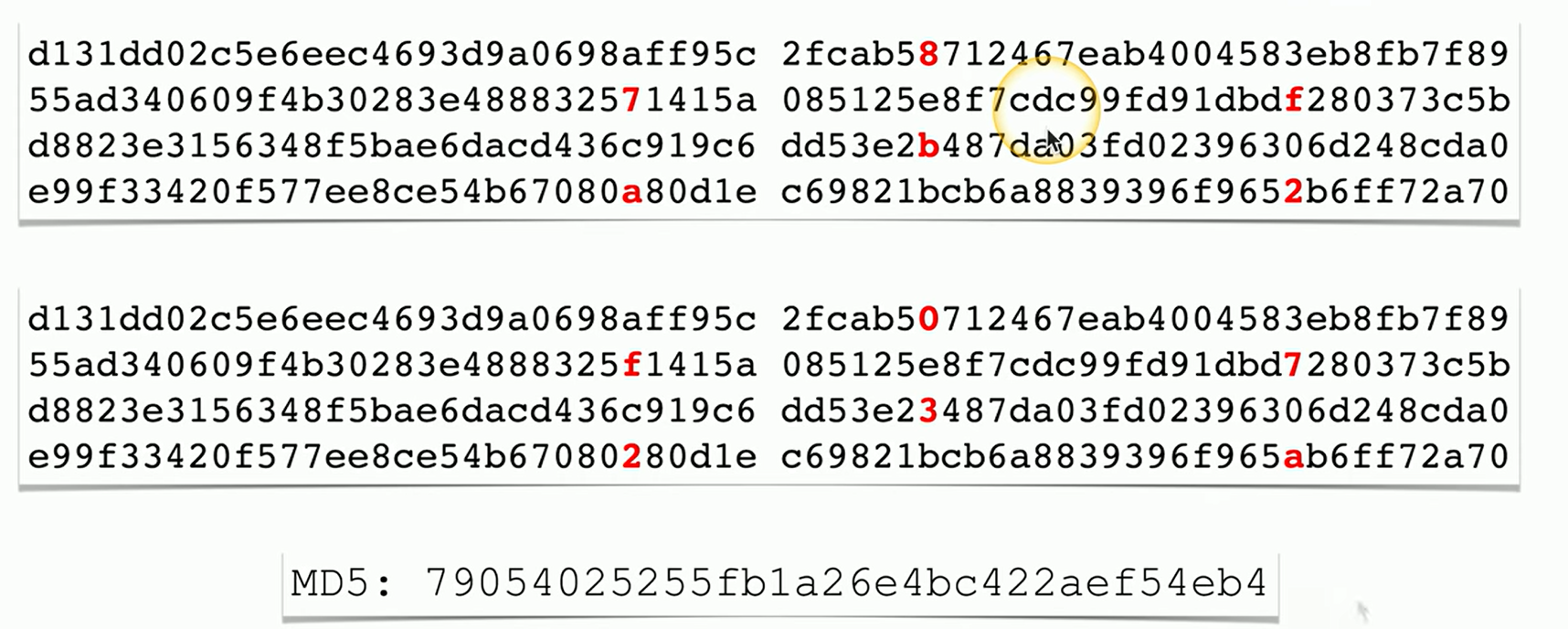
Collision Example
Two types of plaintext put into an MD5 hashing algorithm
The plaintexts are almost identical.
But because these are different, we would expect the resulting hash to also be very different.
If you put both of these plaintexts into the MD5 algorithm, you end up with exactly the same hash, which means we found a collision.
Downgrade Attack
Occurs when an attacker forces systems to use weaker encryption methods or no encryption at all.
One common form of downgrade attack is SSL stripping:
The attacker positions themselves between the victim and the server, intercepting the communication.
The attacker then convinces the victim’s browser that the page being visited does not need encryption, causing it to use the unencrypted HTTP protocol instead of the more secure HTTPS.
While difficult to execute, SSL stripping can provide significant returns for attackers
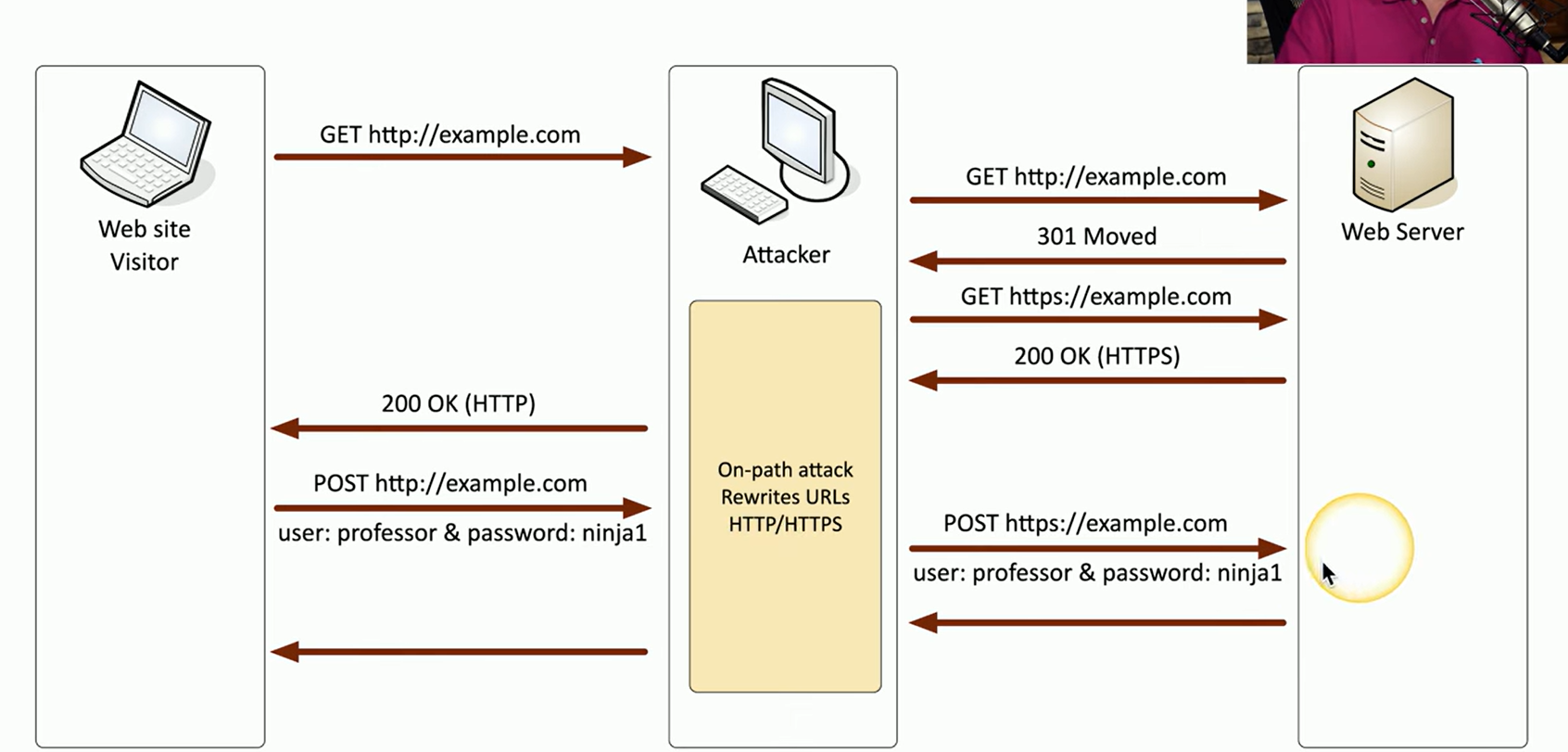
SSL Stripping
The attacker positions themselves between the website visitor and the web server.
The attacker intercepts the initial communication, where the victim sends a GET request using HTTP instead of HTTPS
The attacker allows the initial HTTP request to pass through to the server but blocks the server’s response, which would typically redirect the visitor to HTTPS.
Instead, the attacker then sends a request to the web server using HTTPS themselves
Since the attacker controls the session, they can decrypt and read any data sent between the server and the victim over this secure connection.
Next, when the victim logs in with their username and password, the information is sent over HTTP because the victim was never redirected to HTTPS.
Communication between the attacker and the server remains encrypted, the communication between the victim and the attacker occurs in the clear,