2.4 Password Attacks
1/6
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
7 Terms
Plaintext / Unencrypted passwords
Storing passwords in plaintext (unencrypted) is a major security risk
It allows anyone with access to the storage files or database to easily read all users' credentials.
If an attacker gains access to the database, they can immediately exploit the usernames and passwords.
Although it is rare to find applications that do this
If your application saves passwords in plaintext, the best course of action is to switch to a more secure solution
Hashing A Password
Passwords should always be stored as a fixed-length string generated from a variable-length input using a mathematical algorithm.
Process is often referred to as creating a message digest or a fingerprint.
Each unique password should produce a distinct hash
A well-designed hashing algorithm ensures no collisions, meaning different inputs won't produce the same output
A one-way process, meaning it is not possible to reverse-engineer the original password from the hash, much like how fingerprints can't reconstruct an entire person.
Hash Example
On the left side of this list are the passwords
On the right side is a hash that’s been created with the SHA-256 hashing algorithm.
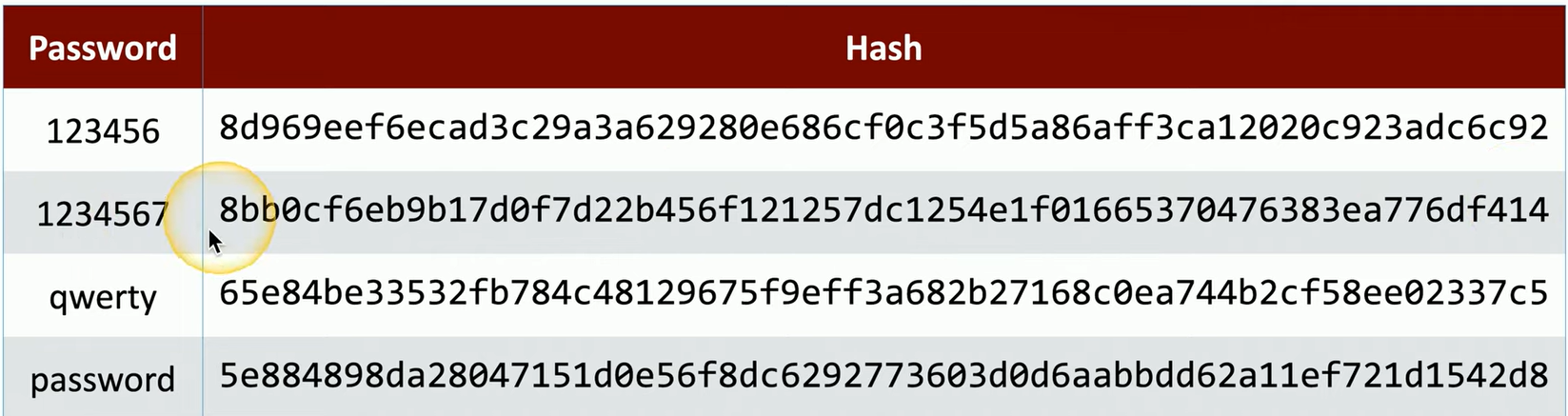
Notice that although the second password itself is only one character difference between the first, but the two different hashes are very different from each other
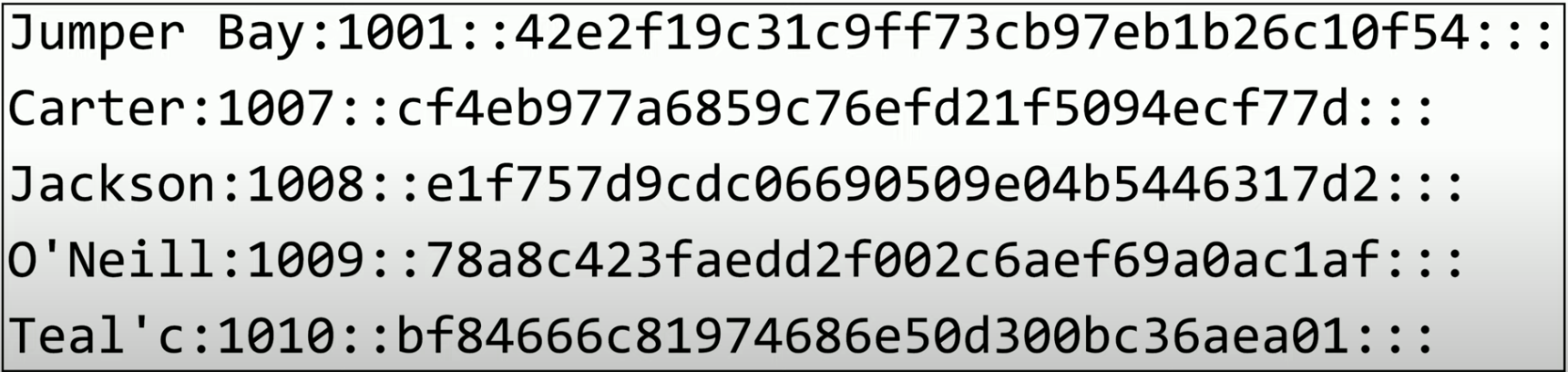
Password File
If we were to look at the section of an operating system or the file where these credentials are saved, you may be able to see the usernames associated with these accounts.
Notice that the hash that is stored for each one of these accounts is very different from each other, and none of it contains the original plaintext.
Spraying Attacks
A type of attack where the attacker tries to guess a password without triggering account lockouts or alerts.
Attack an account with the top three (or more) passwords If they don’t work, move to the next
Allows the attacker to avoid detection, as it typically doesn't exceed the login attempt limits on any single account
Unfortunately, many users still use common passwords, making this type of attack effective.
https://en.wikipedia.org/wiki/List_of_the_most_common_passwords
Brute Force
Involves trying every possible password combination until the correct one is found.
Can take considerable time, especially if the password is long and complex
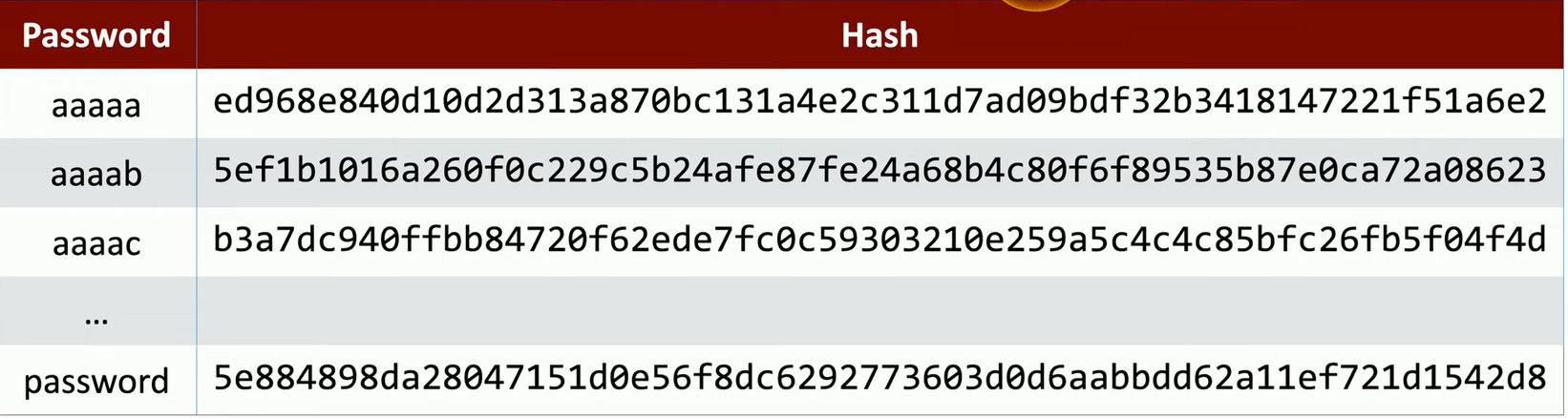
When attempting a brute force attack, the attacker typically has access to the password hash
The attacker begins by generating hashes for potential passwords (e.g., starting with "aaaaa") and comparing them to the stored hash
The process continues iteratively through all combinations until the correct match is found.
A strong hashing algorithm can slow down this process
Brute Force: Online Vs Offline
Brute force attacks can be performed in two main ways:
Involves attempting password guesses directly on a website or service. However, this method is slow and often limited by account lockout mechanisms, which restrict further attempts after a certain number of failed logins.
The attacker obtains a file containing hashed passwords (often along with usernames or other information). Since this is done offline, the attacker is not limited by account lockout restrictions and can try as many password combinations as needed. With enough time and computational power, they can eventually find the matching hash, bypassing the need for live login attempts.