Professor Messer 4.5 - 4.9 Study Sets
1/101
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
102 Terms
Network-Based Firewalls
Filter traffic by port number or application.
Encrypt traffic by using a VPN between sites.
Most firewalls can be layer 3 devices (routers).
Next-Generation Firewall (NGFW)
Begins at the OSP Application Layer, a layer 7 firewall.
Can be called different names
- Application layer gateway
- Stateful multilayer inspection
- Deep packet inspection.
Requires some advanced decodes.
- Every packet must be analyzed, categorized, and a security decision determined.
Ports and Protocols
Makes forwarding decisions based on protocol (TCP or UDP) and port number.
Based on destination protocol and port and whether a next gen firewall or traditional firewall:
- Web server: tcp/80, tcp/443
- SSH server: tcp/22
- Microsoft RDP: tcp/3389
- DNS query: udp/53
- NTP: udp/123
Firewall Rules
A logical path.
Can be general or very specific.
Implicit deny
- Most firewalls include a deny list at the bottom even if you didn't put one.
Access control lists
Based on :
- Allowing or disallowing traffic
- Groupings of categories.
- Source IP< Destination IP, port number, time of day, apps, etc.
Screened Subnet
An additional layer of security between you and the internet.
- Public access to public resources.
- Private data remains inaccessible.
IPS Rules
Intrusion Prevention System
- Usually integrated into a NGFW.
Different ways to find malicious traffic:
- Look at traffic as it passes by.
- Signature-based - Look for a perfect match.
- Anomaly-based - You build a baseline of what's "normal" and you determine what happens when unwanted traffic appears. Unusual traffic patterns are flagged.
Thousands of rules or more.
- Rules can be customized by group.
- This can take time to find the right balance.
Content Filtering
Control traffic based on data within the content.
Corporate control of outbound and inbound data.
Control of inappropriate content.
- Not safe for work.
- Parental controls.
Protect against attackers.
URL Scanning
Allow or restrict based on url - Uniform Resource Locator.
Also called a Uniform Resource Identifier (URI)
Managed by category.
Can have limited control.
Often integrated into an NGFW.
Agent Based
Install client software on the user's device.
Users can be located anywhere.
The agent makes the filtering decisions.
Agents must be updated, updates must be distributed to all.
Proxies
A device that sits between users and the external network.
Receives the user requests and sends the request on their behalf (the proxy)
Useful for catching information, access control - URL filtering, content scanning, etc.
Forward/Internal Proxy
A "centralized" proxy inside the internal network with the user.
- Commonly used to protect and control user access to the internet.
Block Rules
Based on a specific URL
- professormesser.com: Allow.
Category of site content
- Usually divided into 50 different topics: Adult, educational, gambling, government, etc.
Reputation
Filters URLs based on perceived risk: Trustworthy, low risk, medium risk, suspicious, high risk.
Sites are scanned and assigned a reputation.
Rep can be manually assigned.
DNS Filtering
Before connecting to a website, get the IP address to perform a DNS lookup.
DNS is updated with real-time threat intel.
DNS doesn't give IP addresses to bad sites.
Works on more than just web pages
Operating System Security
Operating System Security
Active Directory
Database of everything on the network.
Mainly Windows-based.
Managed authorization.
Centralized access control
- determine which users can access resources.
Commonly used by the help desk to reset passwords, add and remove accounts.
Group Policy
Manage the computers or users with group policies This is run from a central console.
Allows us to configure:
- Login scripts.
- Network configs.
- Security parameters.
Security Enhanced Linux (SELinux)
A security feature/patches built for the Linux kernal.
- Adds mandatory access control (MAC) to Linux since Linux traditionally uses Discretionary Access Control (DAC).
Limits application access
- Through least privilege - so apps and processes can do exactly what they're supposed to do - reducing the risk of security breaches.
Open sourced.
Protocol Selection
Use a secure application protocol
- Ex: HTTPS instead of HTTP, SFTP instead of FTP (file transfer).
A secure protocol may not be available
- This may be a deal-breaker.
Port Selection
Secure and insecure apps commonly use different port numbers.
Ex:
- HTTP:80
- HTTPS: 443
Secure Transport Methods
802.11 wireless open = no encryption.
WPA3: All user data is encrypted.
VPN
- All traffic is encrypted.
- Often requires 3rd party services and software.
Email Security Challenges
Protocols used to transfer emails include few security checks.
-It's very easy to spoof an email.
Spoofing happens all the time.
Email looks as if it originated from james@professormesser.com
- But did it?
Mail Gateway
The gatekeeper
Evaluates the source of inbound email messages
-Blocks it at the gateway before it reaches the user.
Can be on-site or cloud-based.
SPF (Sender Policy Framework)
SPF protocol
- Configures a list of all servers authorized to send emails for a domain.
List of authorized mail servers are added to a DNS TXT record.
- Gateways can check/query your DNS for it.
- Used to check to see if incoming mail really did come from an authorized host.
DKIM (Domain Keys Identified Mail)
Mail server digitally signs all outgoing mail.
- The public key is in the DKIM TXT record.
The signature is validated by the receiving mail servers.
An email authentication standard that uses digital signatures to verify the authenticity and integrity of emails
DMARC
Domain-based Message Authentication Reporting and Conformance
- An extension of SPF and DKIM.
The domain owner decides what receiving email servers should do with emails not validating users using SPF and DKIM. - That policy is written into a DNS TXT record.
- Accept all, send to spam, or reject the email.
Compliance reports are sent to the email administrator.
another feature it has = can send compliance reports to the email administrator and the domain owner can see how emails are received.
- You can see who's spoofing your email domain.
FIM (File Integrity Monitoring)
Monitor important operating system and application files and identify when changes occur.
- These files shouldn't be changing.
Software that monitors:
- Windows = SFC (System File Checker).
- Linux = Tripwire
- Many host-based IPS options
Data Loss Prevention (DLP)
Stops data in real-time before attackers get it.
Often requires multiple solutions in different places
On your computer
- Data in use
- Endpoint DLP
On your network
- Data in motion
On your server
- Data at rest.
USB Blocking
DLP on a workstation.
- Allow or deny certain tasks.
- Bans removable flash media and storage devices like USB drives.
- DLP agent handles uSB blocking.
Cloud-Based DLP
Located between users and the internet
- No hardware or software.
Manages access to URLs
- Prevents file transfers to cloud storage.
Blocks viruses and malware.
DLP and Email
Email continues to be the most critical risk vector
- Inbound threats, outbound data loss.
Check every email inbound and outbound.
- Internal system or cloud-based.
For inbound:
- Block keywords, identify imposters, quarantine email messages.
Outbound:
- Block fake fire transfers, W-2 transmissions, employee info.
The Endpoint
A user's physical device and access. (Laptops, desktops, etc)
Protection is multi-faceted. Layer defense needed.
Edge Control
The edge = where your internal network meets the outside network or "internet"
Usually managed through firewall rules/ protected with firewalls.
Access Control
Limiting a device's access to a certain type of data.
Can be from inside or outside.
Access can be based on many rules: user, group, location, application, etc.
- Can be revoked or changed.
Posture Assessment
Checks to see if devices are up to the latest standard of security.
- Is it a trusted device?
- Running latest antivirus?
- Apps updated to latest versions?
- Is it a mobile device? Is the disk encrypted?
- Etc?
Persistent Agents
Software that is permanently installed onto the system and will do posture checks.
- Can run at anytime.
- Periodic updates are required for it.
Dissolvable Agents
No installation is required.
- Runs during the posture assessment.
- Terminates when no longer required
Agentless NAC
Does not require a dedicated agent or software to be installed, instead is integrated with active directory during authentication.
- Checks are made during login and logoff.
- Can't be scheduled.
EDR (Endpoint Detection and Response)
Detects a threat not only via signatures but also with:
- Behavioral analysis, machine learning, process monitoring.
A lightweight agent at the endpoint.
Investigates threats
- root cause analysis.
Responds to the threat.
- Isolate the system.
- Quarantine the threat.
- Rollback to a previous config.
XDR (Extended Detection and Response)
An evolution of EDR.
Can improve missed detections, false positives.
Adds network-based detection to investigate and respond.
Can correlate data from diff data types and systems (Endpoint, network, cloud).
Uses user behavioral analytics to create a baseline of normal activity and to detect anomalies.
Identity and Access Management (IAM)
A framework of policies and technologies for ensuring that the right permissions are given to the right people at the right time to prevent unauthorized access. This is done through:
Access control.
Authentication and authorization.
Identity governance
- to track an entity's resource access.
Provisioning/De-Provisioning User Accounts
The process of creating, updating, and deleting user accounts.
An important part of the IAM process.
Permission Assignments
Each entity gets limited permissions (least privilege)
- just enough to do their job.
Storage and files that a user create are private to that user
- even if another person is using the same computer.
Identity Proofing (IAM)
The system confirming your identity.
Validating.
- Passwords, security questions.
Verification/attestation.
- Additional info from the user to confirm the identity, passport, in-person meeting, etc.
Single-Sign On (SSO)
Provide credentials at once, get access to what you need.
Usually for a limited time.
The underlying authentication process and infrastructure must support SSO.
- but not always an option.
LDAP (Lightweight Directory Access Protocol)
Protocol for accessing, reading, and writing large directories of data on an IP network
- Organized set of records, like phone directory.
Used to query and update an X.500 directory
- Used in Windows, Active Directory, Apple Open Directory, etc.
X.500 Distinguished Names
A part of LDAP, a unique identifier for an entry in an X.500 directory.
- Attribute = value pairs.
- Ex: CN=WIDGETWEB, 0=Widget, L=London.
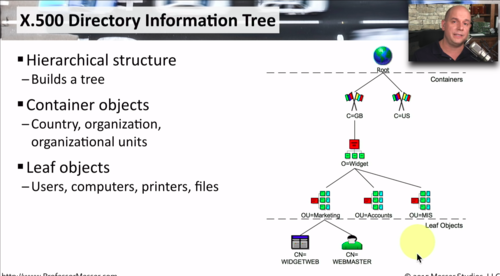
X.500 Directory Information tree
Hierarchal structure
Builds a tree.
Contains:
Container objects.
- Country, org, organizational units.
Leaf Objects.
- Users, computers, printers, files.
SAML (Security Assertion Markup Language)
Open standard used for authentication and authorization.
- Auth is run through a 3rd party.
Not designated for mobile apps.
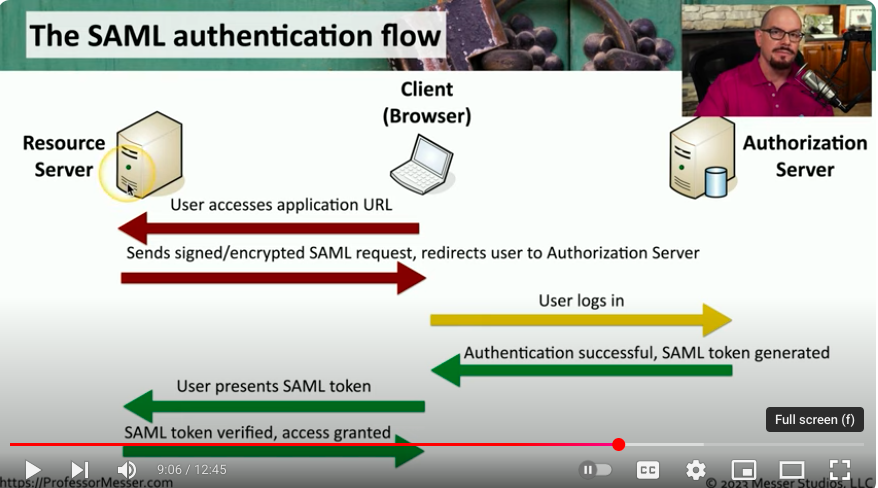
SAML Authentication Flow
1. First, the client (browser/computer) attempts to access a URL on the resource server.
2. Since this user is not logged in, the resource server sends a signed/encrypted SAML request and redirects user to the authorization server.
3. The authorization server then checks the credentials and generates a SAML token.
4. The user then presents the SAML token to the resource server.
OAuth
Authorization framework that determines which resources a user will be able to access.
Created by Twitter, Google, and others in the industry.
Open ID handles the single sign-on authentication.
- Allows authorization between applications
Federation
Provides network access to others - allows network access without using a local authentication database.
- Provides SSO.
- Ex: Login with Twitter/Facebook/etc with those credentials.
Third-parties can establish a federated network.
- Authenticate and authorize between two organizations.
The third-parties must establish a trusted relationship.
Interoperability
When an org is making a decision on which authentication technologies they should be using, they have to make sure that all of these technologies are interoperable, meaning that they can all work together and communicate and exchange information.
Least Privilege
Rights and permissions should be set to the bare minimum.
- You only get exactly what's needed.
Doesn't allow users to run with administrative privileges.
Mandatory Access Control (MAC)
Operating system limits user access to objects by labeling them.
Every user/object gets a label
- confidential, secret, top secret, etc.
The administrator decides who gets access to what security level and users cannot change these settings.
Discretionary Access Control (DAC)
One common type of access control that is used in most operating systems.
Works by you creating a spreadsheet
- and as the owner, you control who has access.
- You can modify access at any time.
Very flexible, but has weak security.
Role-Based Access Control (RBAC)
Admins provide access based on the role a user has in an organization.
Rights are gained implicitly instead of explicitly.
In Windows, use Groups to provide role-based access control.
Rule-Based Access Control
Access is determined through system-enforced rules by the system administrator and not users.
Attribute-Based Access Control (ABAC)
An authorization model that evaluates attributes or characteristics, rather than roles, to determine access.
A "next generation" authorization model.
Can combine and evaluate multiple parameters.
- Resource info, IP address, time of day, desired action, etc.
Multi-Factor Authentication
Using different methods to prove who you are.
Factors:
- Something you know, a password/PIN.
- Something you have, A smart card/USB sec key/token/phone.
- Something you are, biometric authentication.
- Somewhere you are, your location, IP address.
Password Strength
Using an increased amount of entropy
- No single words, obvious passwords.
- Mixing upper and lower case letters, numbers, etc.
Having it be at least 8 characters.
Password Age and Expiration
Passw age: How long since a password was modified.
Expiration: Works for a certain amount of time
- 30 days, 60 days, 90 days, etc.
Passwordless Authentication
Authenticating without a password.
Facial recognition, security key, etc.
Not the primary authentication method, can be used with a password or additional factors.
Passwordless Authentication
Authenticating without a password.
Facial recognition, security key, etc.
Not the primary authentication method, can be used with a password or additional factors.
Just-In-Time Permissions
Granting admin access for a limited amount of time with temporary credentials.
- With temporary password.
- No perm admin rights.
Scripting and Automation
Automates and orchestrates so you don't have to be there.
The script is fast, automated, no human error, saves time.
Automation Benefits
You save time. Enforce baselines.
- Automated patching.
Standard infrastructure configurations.
Secure scaling.
Employee retention.
- Automate the boring tasks and ease the workload.
Reaction time.
- The computer is much faster than you.
Scripting works 24/7
Cases for Automation
User and resource provisioning.
- On-boarding and off-boarding.
- Assigning access to specific resources.
To act as guard rails.
- Reduce human errors.
- Constantly check to ensure proper implementation.
To add and remove users from particular security groups.
For ticket creation.
- to script email submissions into a help-desk ticket.
Escalation.
- Correct issues before involving a human.
- Involve a human or a technician if needed.
Controlling services and access.
Continuous integration and testing
- constant development and code updates.
Integrations and Application Programming Interfaces (APIs)
- Interact with 3rd party devices.
Scripting Considerations
Complexity. Cost.
Single point of failure
- what happens if the script stops working?
Technical debt.
- Patching problems may push issues down the road.
Ongoing supportability.
- The script works great today, but may not work great tomorrow.
Security Incidents
Usr clicks an email attachment and executes malware.
DDoS attack.
Confidential info is stolen.
Usr installs peer-to-peer software and allows external access to internal servers
NIST SP800-61
National Institute of Standards and Technology
- Computer security incident handling guide for organizations.
Contains incident response handling life-cycle:
- Preparation.
- Detection and analysis.
- Containment, Eradication, and Recovery.
- Post incident Activity.
Preparing for an Incident
Communication methods.
- Phones and contact info to contact when an incident occurs.
Incident handling hardware and software.
- Laptops, removable media, forensic software, digital cameras, etc.
Documentation, network diagrams, baselines, critical file hash values.
Incident mitigation software.
- Clean OS and application images.
Policies needed for incident handling.
- So everyone knows what to do.
Detecting Security Incidents.
There are many different detection sources.
A large amount of "volume"
- Attacks are incoming all the time, which are legitimate threats?
Incidents are almost always complex.
Incident Analysis
An incident might occur in the future.
Have a calendar to know when there will be an exploit announcement.
- When Microsoft will release their Monthly Microsoft patch release.
Direct threats.
When an attack is underway or occurs.
-Buffer overflow attempt.
- Anti-virus identifies malware.
- Host-based monitor detects a configuration change.
- Network traffic flows deviate from the norm/ show anomalies.
Isolation and Containment
Don't let an attack run its course or spread.
Some systems will provide a way to test for an attack inside of a sandbox.
Can be sometimes problematic.
- Malware can act differently in a sandbox.
Sandboxes
An isolated operating system.
Can run malware and analyze the results.
Recovery After an Incident
Remove the bad, replace it with a known good.
Remove malware.
Disable breached user accounts.
Fix vulnerabilities.
Recover the system.
- Restore from backups.
- Rebuild from scratch.
- Replace compromised files.
- Tighten the perimeter.
Lessons Learned
Learn and improve.
Post-incident meeting.
Don't wait too long
- better done ASAP.
- Memories fade over time.
Training for an Incident
Train the team prior to an incident.
- Initial response.
- Investigation plans.
- Incident Reporting.
- And more.
This can be an expensive endeavor, especially with larger response teams
Exercising
Test yourself before an actual event.
Use well-defined rules of engagement.
- Do not touch the production systems.
You'll have a limited amount of time to run the event.
Evaluate response
Tabletop Exercises
Talking through a simulated disaster.
- Without physically going through a disaster or drill.
Simulation
Test with a simulated event.
Large orgs will test through phishing and create a phishing email attack.
Test internal security.
Root Cause Analysis
Determine the ultimate/root cause of an incident.
Create a set of conclusions regarding the incident.
Can be more than a single root cause.
Threat Hunting
Trying to find vulnerabilities before the attacker does.
- A constant game of cat and mouse.
Strategies constantly change.
Intelligence data is reactive.
- You can't see the attack until it happens.
Speed up the reaction time
- Use technology to fight.
Digital Forensics
To collect and protect information related to an intrusion.
RFC 3227 = standard for best practices process, Guidelines for Evidence Collection and Archiving.
- Acquisition, analysis, and reporting.
Legal Hold
A legal technique to preserve legal information.
- Initiated by legal counsel.
Hold notification -
custodians are instructed to preserve this data.
Separate repository for Electronically Stored Info (ESI).
Ongoing preservation
- once notified, there's an ongoing obligation to preserve data.
Chain of Custody
Maintaining the integrity of the evidence.
Use hashes and dig signatures to track everyone who contacts the evidence to avoid tampering.
Label and catalog everything.
- Digitally tag all items for ongoing documentation.
- Seal and store.
Aquisition
To obtain the data.
- Disk, RAM, firmware, OS files, etc.
Some data may not be on a single system, and you may need to collect data through multiple devices.
- Servers, network data, firewall logs.
For virtual systems/vms, get a snapshot.
- Contains all files and info.
Look for any left-behind digital items.
- Artifact
- Log info, recycle bins, browser bookmarks, etc.
Reporting
Document the findings.
Gather summary information and overview of security event.
Detailed, step-by-step explanation of data acquisition process.
Analysis of findings.
Conclusion.
- Results. given the analysis.
Preservation
Handling evidence by isolating and protecting the data.
Manage the collection process by working from copies.
- Keeps the original data you have untouched, and you have backups.
Live data collection = an important skill.
- Data may be encrypted or difficult to collect after a system is powered down.
E-Discovery
Collecting, preparing, reviewing, interpreting, and producing electronic documents.
Gathers data required by the legal process.
- Does not generally involve analysis.
Works together with digital forensics.
- Forensic experts perform the analysis.
- They determine that the data was deleted and attempt to recover the data.
Security Log Files
Detailed security information.
- Blocked and allowed traffic flows, exploit attempts, blocked URL categories, DNS sinkhole traffic.
Critical security info.
- Documentation of every traffic flow.
- Summary of attack info.
- Correlate with other logs.
Firewall Logs
Traffic flows thru a firewall.
- Source/destination IP addresses, port #s, etc..
You can also get info thru NGFW.
- Logs the application used, the URL filtering categories, anomalies and suspicious data.
Application Logs
Information specific to the application.
Windows.
-Uses Event Viewer/Application Log.
Linux and MacOS.
- Uses /var/log.
Parse details on a SIEM tool.
Endpoint Logs
Endpoints and logs of phones, laptops, tablets, desktops, etc.
Attackers often gain access to endpoints.
There's a lot of data.
- Logon events, policy changes, system events, processes, account management, directory services, etc.
Everything rolls up to the SIEM/ Sec Information and Event Manager.
Compare and correlate the data from SEIM with other log data from other devices
OS Specific Security Logs
OS Security events
- Monitoring apps, brute force, file changes, authentication details.
May find problems before they happen.
- Security alerts, brute force attacks, disabled services, other signs of an attack.
May require filtering.
- Don't forward everything/log info to the SIEM, only what's important to make security decisions.
IPS/IDS Logs
Usually integrated into a NGFW.
Contain information about predefined vulnerabilities.
- known OS vulnerabilities, generic security events.
Common data points
- Timestamp.
- Type or class of attack.
- Source and destination IP.
- Source and destination port.
Network Logs
Information we can gather from our network infrastructure devices such as switches, routers, access points, VPN concentrators, and other infrastructure devices.
Log files can identify any network changes such as:
- Routing updates.
- Authentication issues.
- Network security issues.
Metadata
Data that describes other data sources/files. (Data that is stored within the documents that we're transferring over the network.)
Examples:
Email.
- Information within the header details. sending servers. destination address, etc.
Mobile. - Type of phone, GPS location, etc.
Web.
- Operating system, browser type, IP address.
Vulnerability Scan Log Info
Log info that may identify lack of security controls.
- No firewall, anti-virus, anti-spyware.
We can also identify devices that are misconfigured
. - Misconfigurations like open shares, guest access.
Real vulnerabilities need to be patched
- especially newer ones.