IB Digital Society S-Z
1/64
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
65 Terms
SaaS
Software as a service; a software distribution model in which a third-party provider hosts the applications with end- users accessing the software through the internet.

Sabotage
The disruption of computers and systems that operate military, economic infrastructure or other vulnerable networks.

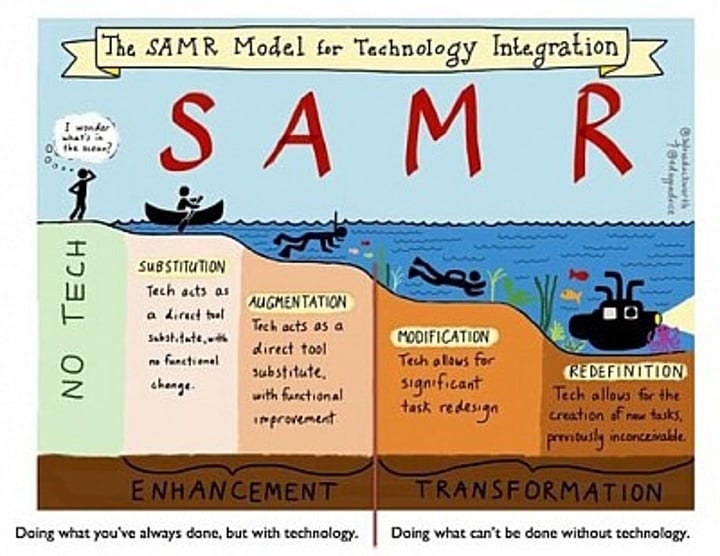
SAMR model
A framework for analysing educational technology.
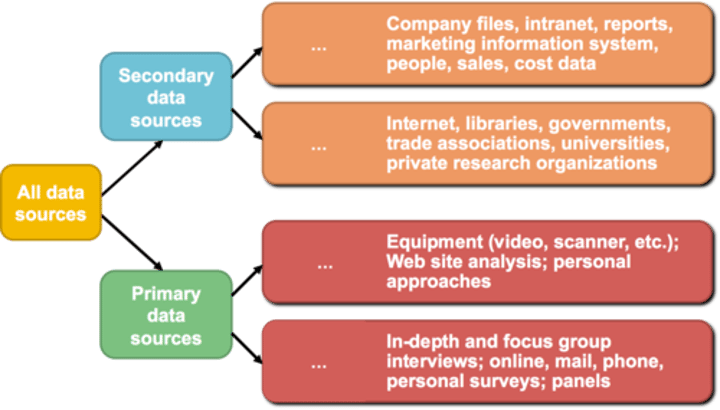
Secondary data
Data that has already been collected by someone else for a different purpose.

Secondary research
Research carried out by someone else.
Secondary storage
Is non-volatile, long-term memory, used to store programs and data until they are required.

Secure Socket Layer (SSL)
Is a protocol developed for sending information securely over the Internet by using an encrypted link between a web server and a browser. Self-guided learning: A strategy that allows students to direct their own learning.

Server
A large computer dedicated to managing network resources. They can use specialised server hardware or can be a regular computer with a server-specific operating system capable of managing network resources.

Service robot
Robot developed to assist humans in completing tasks that are less desirable, such as dull, dirty or dangerous jobs.

Sharing economy
Assets or services that are shared between individuals, often using an online booking system.

Singularity
The hypothetical future where artificial intelligence becomes so advanced that it is superior to human intelligence.
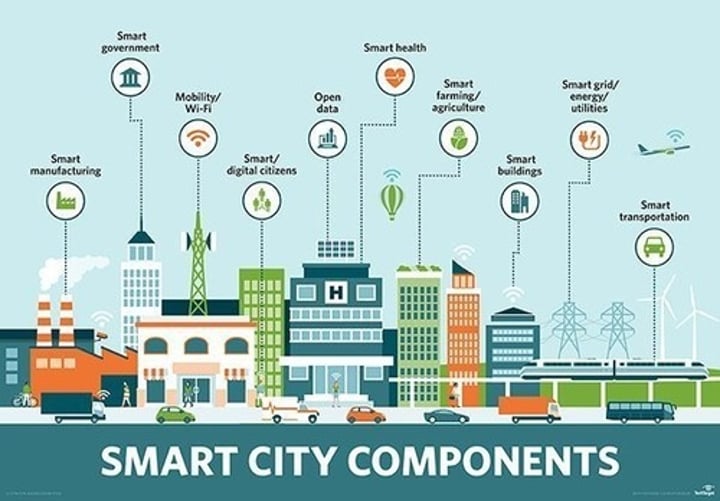
Smart city
A city that integrates sensors, voice recognition and other new technologies to better manage transportation, energy distribution and other services.
Smart home
Home equipped with internet-connected lighting, heating and other electronic devices.

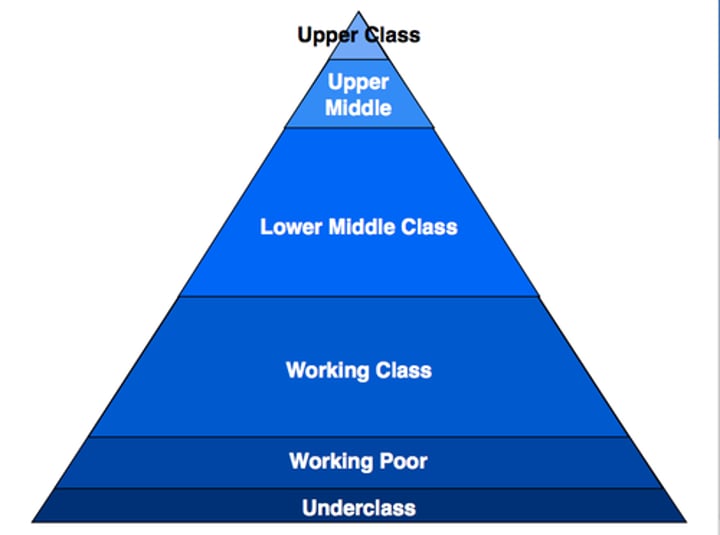
Social class
A method of classifying people and communities according to their social status.
Social engineering
In internet security, this means tricking a user into sharing their username and password with a fraudster.

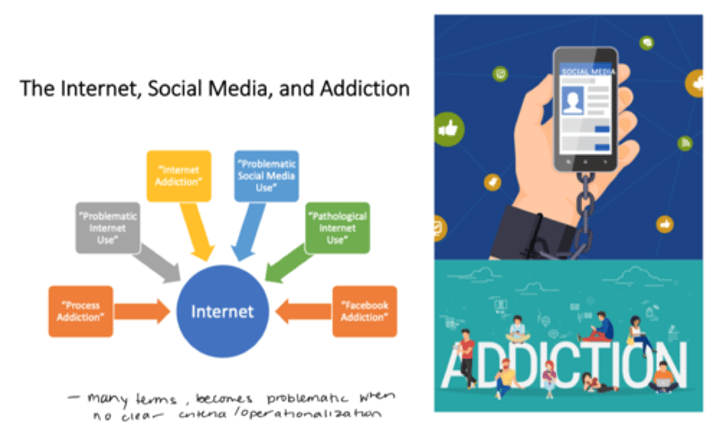
Social media addiction
Psychological or behavioural dependence on social media to the detriment of other important parts of life.
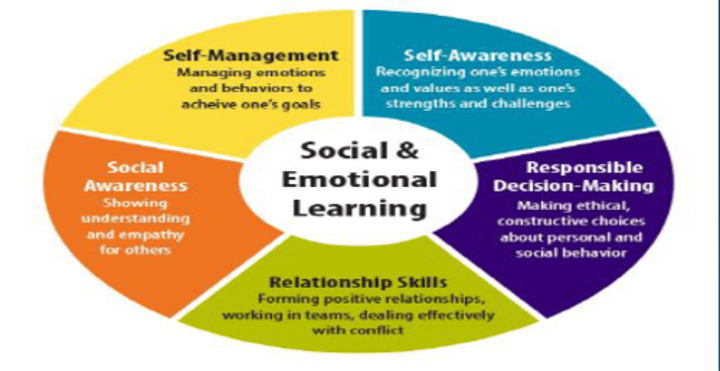
Social-emotional learning
The integration of social and emotional skills into the curriculum.
Solid pollution
Solid waste material.

Spamming
Sending unsolicited emails, mainly for the purpose of advertising.

Speed
The length of time it takes for data to be transferred, measured in megabits per second (Mbps).
Stratification
The unequal distribution of resources between people/nations.
Streaming
Multimedia (especially video and audio) that is delivered digitally with little or no intermediate storage.

Strong Al
Artificial intelligence that can develop consciousness and make decisions better than humans.
Subculture
Smaller cultural groups that exist within a larger culture.

Subtractive manufacturing
Creating an object by cutting or carving a larger material into the desired shape.
Super Al
Artificial intelligence that surpasses human intelligence.
Supercomputers
Refers to high-performance computers capable of high-speed calculations that are required in scientific and engineering fields.

Surveillance
Is undertaken to collect information about people which can be used for a variety of purposes, both positive and negative, even though surveillance has mainly negative connotations. Surveillance can be conducted using technology, or through observations by people.

Sustainable development
The ability to meet human development goals without depleting the natural resources that we depend on.
Switch
A networking device that forwards data packets more efficiently than a hub.

Synchronous
Remote learning that happens in real time with a live teacher.
Systems thinking
A way to think about structure and order in human, natural and built environments.
Technique
The way an artist uses their technical skills to create their art.
Telemedicine
The remote treatment of patients.
Terrorism
The unauthorised use of violence/force to create fear and coerce a government or its people toward a political or social cause.
Transaction processing system
A system designed to incorporate all of the resources, software and hardware needed to manage sales, purchases and other transactions.
Transhumanism
A movement that aims to use technology to evolve and augment the human experience.
Translation app
An app that translates one language into another allowing communication in real time.
Transmission control protocol/internet protocol (TCP/IP)
Protocol that defines where data is to be sent to and from (IP), and how the data is to be broken down into smaller sections before sending (TCP).
Transparency in algorithms
the ability to understand and be able to explain the inner workings of the algorithm.
Transport Layer Security (TLS)
Is an improved version of SSL and is a protocol that provides security between client and server applications communicating over the Internet.
Trending
A topic that experiences a sudden surge in popularity on social media platforms for a limited period of time.
Trilateration
Technology that uses three satellites to pinpoint our phone's location.
User interface
The means by which human users interact with a digital technology. The intent is to make the user's experience straight forward, intuitive, and requiring minimum effort to achieve the desired outcome.
Utility software
Software designed to perform specific useful tasks that either help to analyse, configure or maintain the computer.
Validation
In databases, this means that only valid (suitable) data can be entered.
Vertical diversification
When a business takes over a new part of their supply or production chain.
Video game addiction
Psychological or behavioural dependence on playing video games to the detriment of other important parts of life.
Virtual conferencing platform
Digital platform that allows multiple users to video chat at the same time, for example Zoom or Google Meet.
Virtual personal assistant
Voice-controlled helper mainly found in smart speakers or mobile phones.
Virtual reality (VR)
A simulation that provides a completely immersive environment for the user.
Virtual reality exposure therapy (VRET)
Therapy designed to reduce a person's fear and anxiety by confronting the experiences in a computer-generated virtual environment.
Virus
A type of malicious software comprised of small pieces of code, often attached to legitimate programs or emails.
VoIP (voice over internet protocol)
Allows users to make voice calls using a broadband Internet connection instead of an analogue phone line.
Water pollution
Pollution released into water.
Wayfinding
The technologies and systems that give directions to people as they navigate a physical space.
Weak/narrow Al
Artificial intelligence that has a limited function or can only perform a specific task.
Wearable medical device
A device that can be worn to provide continuous, real-time data to improve the treatment, diagnosis and monitoring of patients.
Wide area network (WAN)
A national or international network; the largest example is the internet.
Wireless access point (WAP)
A device that creates a wireless local area network to improve coverage throughout a building.
Wireless networks
Use of wireless technologies to connect the different nodes to form a network.
Wisdom
The application of knowledge.
World Wide Web (WWW)
The websites and web services that are hosted on web servers and identified by their URL (uniform resource locator).
Youth culture
The culture and social norms of teenagers and young adults.
Verification
In databases, these are checks that the data entered is the actual data that you want, or that the data entered matches the original source of data.