3-1 Developing Secure Websites and Web Applications
1/79
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
80 Terms
Website interactivity and potential user input allow a variety of attacks, including:
cross-site scripting (XSS), SQL injection, and moreImproperly validated and untrusted user input is:
Improperly validated and untrusted user input is:
a large security risk with web applications
Need input validation methods deployed on:
client side and server side
General guidelines and practices for accepting user input into a website:
- Do not rely solely on client-side validation.
- Ensure server-side validation.
- Use whitelisting and blacklisting.
- Assume all input is malicious.
- Sanitize your input.
RFC:
Request for Comments
Request for Comments (RFC):
- A formal document from the Internet Engineering Task Force (IETF)
- Presents a draft or the revisions to an existing or proposed internet guideline, standard, or procedure
- Acceptable syntax for email addresses, URL input, XML input, and many other standards are detailed in one or more RFCs
Examples of pertinent RFCs:
- RFC 5322—Validating email address syntax and usage
- RFC 2616—Validating HTTP inputs
- RFCs 1738, 1959, 2732, 3986, and others—Validation of URL inputs, including assignment of canonical (preferred) URLs
Technologies and systems used to make a complete functional website:
- Hypertext Markup Language (HTML)
- Common Gateway Interface script
- JavaScript
- SQL database back-end
HTML:
Hypertext Markup Language
Hypertext Markup Language:
- The predominant language for creating webpages
- Allows programmers to embed pictures and interactive forms within a web document
- Created as an online development tool; was not created with security in mind
- A markup language that uses codes, called tags, for formatting a website within a text file
- HTML tags are keywords surrounded by angle brackets that normally come in pairs (Example: <body> and </body>)
How do Malicious users steal information from the user with HTML?
Malicious users can insert their own <form> tags and create interactive content designed to steal information from the user (Such as credit card information and bank account information)
If a website is hacked, maliciously entered tags may do damage. Malicious attacks on HTML can include what?
May include setting up false forms, redirecting to other websites, or running a malicious script whenever the browser goes to the home page
To help prevent malicious users from inserting their own <form> tags in HTML:
Monitor discussion groups to identify which data input is untrustworthy.
Ensure input is validated.
Check HTML code periodically to see if malicious code has been added.
Verify the size of the file; a change in size can indicate a problem.
CGI
Common Gateway Interface
Common Gateway Interface (CGI)
- A standard that defines a method by which a web server can obtain data from or send data to databases, documents, and other programs, and present that data to viewers via the Web
- Programs are commonly written in Perl, C++, or ASP
- Accessed by the web server in response to some action by a web visitor
- Programs often accept user input from the browser to the web server
To help secure CGI:
- Create and program CGI with security in mind.
- Research known vulnerabilities with CGI programming.
- Incorporate security best practices in all programming efforts.
- Review the program periodically to verify and incorporate updated vulnerability information.
- Apply security patches when necessary.
- Use user validation and sanitization.
JavaScript:
- Considered to be the scripting language of the Web.
- Programmers use JavaScript to add functionality and dynamic and interactive content to their websites.
- Web programmer can embed JavaScript code easily into HTML pages:
<html> <body>
<script type=”text/javascript”> document.write (“Text goes
here.”); </script>
</body> </html>
Loading a webpage can cause . . .
arbitrary code to be executed on a computer.
What is required to prevent malicious code from damaging data or privacy?
Stringent security precautions are required to prevent malicious code from damaging data or privacy.
Does JavaScript provide security?
JavaScript provides some security.
- Does not allow writing or deleting files or directories on the client computer
With no file object and no file access functions, a JavaScript program . . .
cannot delete a user’s data or plant viruses on the user’s system.
Back-end database:
- A data-base that is accessed by users indirectly through another application
- Is fronted by a web server, which in turn is accessed by client browsers
SQL back-end database may be vulnerable to . . .
both physical and logical attacks
Physical threats, such as theft of the database server
Logical attacks, such as injection attacks and brute-force password attacks
Common attack against an SQL back-end database is an SQL injection
Securing any database requires a multilayered approach:
- Access controls
- Role-based authentication
- Encryption methods
- Integrity verification
SDLC
Software development life cycle (SDLC)
Software development life cycle (SDLC):
- Defines a six-phase development process, in which each phase is completed before moving on to the next
- Design process is also called “a waterfall process” in which the output of each phase is the input to the following phase
The Waterfall Model
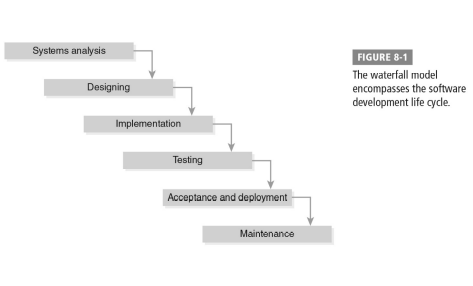
SDLC stages:
- Systems analysis
- Designing
- Implementation
- Testing
- Acceptance and deployment
- Maintenance
Systems analysis:
Seeks clear definition of what software is designed to do and problem or issue it addresses
Designing:
Application’s features and operational functions are clearly established
Implementation:
Code is written
Testing:
Software is tested and examined for bugs, errors, interoperability failures, and more
Acceptance and deployment:
Software product is accepted and shipped, or sent back to design or implementation phase
Maintenance:
Software is improved, enhanced, and updated
SSDLC:
Secure software development life cycle
Secure software development life cycle (SSDLC)
- Defines a developmental process focused not only on the application’s primary functions, but also on ensuring its security and addressing all regulatory requirements
- Provides the same step-by-step definition, design, and development stages as the SDLC but adds security considerations and measures to each phase of development
No one dominant SSDLC standard in use but several development frameworks include:
- NIST SP 800-160 Vol. 1
- Microsoft Security Development Lifecycle (Microsoft SDL)
- OWASP Application Security Verification Standard (ASVS) and Software Assurance Maturity Model (SAMM)
Is SSDLC process a standalone development method?
SSDLC process not necessarily a standalone development method
SSDLC Can be easily integrated into:
- SDLC process
- Agile development workflow
- DevOps
- Rapid application development (RAD) process
(For the most part, all four development models include or define most of the same phases, inputs, and products)
Can a network be secured with a single security approach?
A network cannot be secure with a single security approach.
A complete and layered approach to network security is required:
- Perimeter security
- Host-based security mechanisms
- End-user education
- Authentication and access management
- Input validation
- Vulnerability management
Concept and planning:
Verify the need, worth, and functional concepts of the object of the development project.
Architecture and design:
Create the design document that specifies how each of the requirements identified in the previous phase are to be met.
Implementation (layered approach):
- Complete the application, including writing the programming code, debugging it, and testing.
- Review and enforce secure coding practices and use static application scanning tools (SAST).
Testing and debugging:
- Find and correct any errors in the application’s code or design using different testing methods.
- Testing tools used include dynamic scanning, fuzz testing, and penetration testing.
Release and maintenance:
- Release the application.
- Manage and maintain the security environment of an entire system and not just for a single application.
- Create an incident response plan and team.
- Perform regular vulnerability, threat, and risk assessments and scans.
End of life:
- When the application is no longer viable, follow deprecation procedures and safeguards.
In the Systems analysis stage a qualified security professional should:
- Be involved in development process
- Be tasked with understanding intent of the application and identifying potential security threats such as injection attacks, buffer overflows, directory traversal, more
- Ensure that the software’s functions and operations are not exposed and cannot be exploited
During the designing stage incorporating security at this stage is critical because security foundation for software is established Involves:
- Information gathering
- Threat assessment
- Threat mitigation
In the Implementation stage developers should incorporate security into coding:
- Input validation mechanisms
- Strong encryption
- Securing data that’s stored and in transit
- Authentication mechanisms
- Error handling
During the resting stage:
- Test and retest software to ensure that it is interoperable and functions as it should
- Involves review of software security structure
- Security professional or entire security team tests software for least privilege, buffer overflows, injection attacks, error-handling risks, directory traversal risks, and more
- Final stage tests software in live production environment
- Sometimes called penetration testing or ethical hacking
Acceptance and deployment stage. During deployment, security professional:
- Searches for potential security threats and exploitable areas
- Reviews application’s user manual, looking for security breaches or unforeseen threats
Acceptance and deployment stage. During aeployment stage security plan may include:
- Creating document sources to review the status of the deployment
- Ensuring that user administration and access privileges are established
- Defining response process for handling security bugs
Maintenance security procedures:
- Developing and deploying service packs and patches to manage security threats
- Reviewing logs, audits, and other material to search for new threats and attacks that may have been found
- Reviewing error report messages to see if they are accurate and not revealing information that an attacker could use
- Monitoring feedback from software users
Transmission Control Protocol/Internet Protocol (TCP/IP)
- The set of protocols on which internet communication is based
- Has secure and unsecure protocols
- For example, HTTP is used daily but sends information in cleartext (Is susceptible to man-in-the-middle attacks and can be read if intercepted.)
- For sensitive web communications, Hypertext Transfer Protocol Secure (HTTPS) protocol is used for encryption
Unsecure protocols:
File Transfer Protocol (FTP), Hypertext Transfer Protocol (HTTP), Remote Copy Protocol (RCP)
Secure protocols:
Secure File Transfer Protocol (SFTP), Hypertext Transfer Protocol Secure (HTTPS), Secure Copy Protocol (SCP)
How Secure Sockets Layer Works:
- HTTP sends data in cleartext; too risky for bank sites or other data-sensitive transactions.
- HTTPS ensures safe and secure communication between a client and a web server.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS) used to authenticate a service to a client and then to provide confidentiality (encryption) to the data being transmitted.
- SSL/TLS works in a negotiation process—known as a handshake—between client and web server.
SSL:
Secure Sockets Layer
TLS
Transport Layer Security
SSL/TLS handshake negotiation
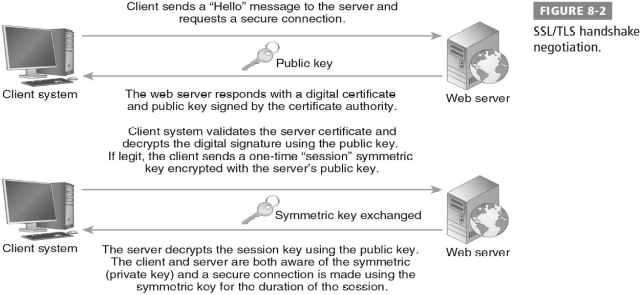
SSL/TLS Encryption and Hash Protocols:
SSL/TLS uses various protocols for encryption and hashing.
Hashing algorithms verify integrity of a data stream; are not used for encryption.
Hashing ensures that data has not been tampered with during transmission.
Two significant hashing algorithms:
Secure Hash Algorithm 1 (SHA1)
An algorithm with a 160-bit function
Provides more security than MD5 but can affect overall performance because it demands more system resources
Message Digest 5 (MD5)
A 128-bit hashing algorithm
Has known vulnerabilities
Secure Hash Algorithm 1 (SHA1:)
- An algorithm with a 160-bit function
- Provides more security than MD5 but can affect overall performance because it demands more system resources
- SSL/TLS communication uses a symmetric key exchange to secure the communication channel.
Message Digest 5 (MD5)
- A 128-bit hashing algorithm
- Has known vulnerabilities
SSL/TLS communication uses _________ to secure the communication channel
a symmetric key exchange
Several key encryption protocols are associated with symmetric key exchanges:
- Data Encryption Standard (DES) (40-bit)
- Data Encryption Standard (56-bit)
- Triple DES (3DES)
- Advanced Encryption Standard (AES)
- Rivest Cipher
Selecting an Appropriate Access Control Solution:
- Access Control
- Privileges dictate who can and who cannot access the application.
- Access can be granted or denied based on criteria. (Network address of the client, time of day, the website visitor’s browser, etc. )
- Access control involves controlling network access by an arbitrary condition that may or may not have anything to do with the attributes of a particular visitor.
- Includes authentication and authorization.
Access control:
- Refers to the mechanisms that identify and control who can and cannot access a network, a resource, an application, specific data, and more
- Is possible to secure a web application by granting users specific rights and privileges
Access control involves controlling network access by:
Access control involves controlling network access by an arbitrary condition that may or may not have anything to do with the attributes of a particular visitor.
Attack Description: Malicious code is embedded in query strings, fields, cookies, and headers. What is the mitigation strategy?
Assume all input is harmful. Constrain, reject, and sanitize all input.
Attack Description: Data-in-transit is captures and use. What is the mitigation strategy?
HTTPS encryption data-in-transit
Attack Description: Sensitive data in log and audit may be vulnerable to an attacker. What is the mitigation strategy?
Use principle of least privilege policy and access controls to limit access
Attack Description: Malicious use of password cracking, privilege elevation, and social engineering to authenticate. What is the mitigation strategy?
Educate users on password security, encrypt passwords, and enforce robust password policies
Attack Description: Malicious users gain access to restricted and sensitive data and resources. What is the mitigation strategy?
Encrypt data files and directories. Validate and audit object authorization.
Attack Description: Malicious users able to hijack a session and use valid credentials. What is the mitigation strategy?
Manual log out of sessions. Automatically log users out of sessions after a period of inactivity.
Attack Description: Hiding or ignoring file, folder, or resource locations. What is the mitigation strategy?
Security by obscurity is not usually enough. Use access control mechanisms and security privileges to protect all resources.
The code, ```html <script>alert('XSS Attack!');</script>``` is an example of what?
- Example of an XSS payload
- This script, when injected into a vulnerable website, executes in the victim’s browser.
How to Prevent XSS:
- Input Validation: Sanitize and validate user input.
- Output Encoding: Encode data before displaying it on the web page.
- Content Security Policy (CSP): Restrict script execution.
- Use HTTPOnly Cookies: Prevent script access to cookies.
- Security Libraries: Use frameworks that auto-sanitize input (e.g., OWASP ESAPI).
Always . . .
sanitize inputs, encode outputs, and apply best security practices.