OSI Model (Section 2)
1/11
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
12 Terms
Protocol
A set of rules for formatting and processing data. Network protocols are like a common language for computers, allowing them to commuinicate
OSI Model
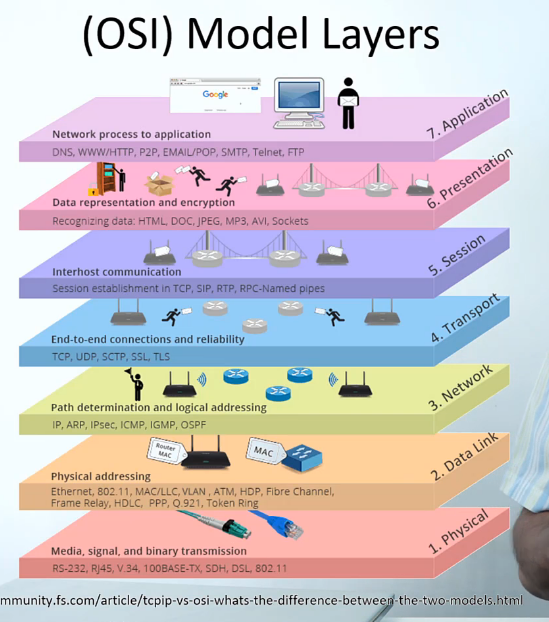
Open System Interconnection Model. A layered approach to how computers/devices communicate. Created to achieve interoperability of diverse vendor devices. Each layer describes a different set of unique functions, composed of various types of hardware and software
Partitions communication systems into abstraction layers.
Protocols are the standard terms that computers use to understand each other
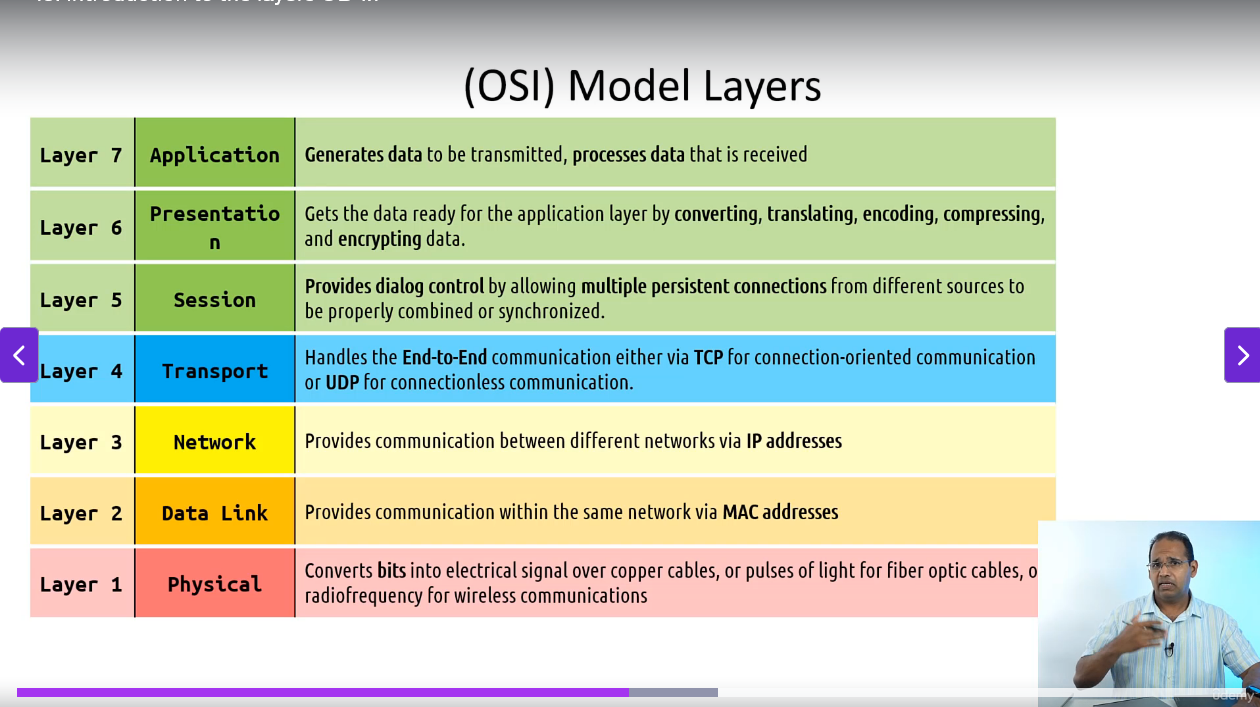
Layer 1: Physical (ex: cables)
Layer 2: Data Link (ex: switch)
Layer 3: Network (ex: router)
Layer 4: Transport (ex: firewall)
Layer 5: Session
Layer 6: Presentation
Layer 7: Application
(Layer 7-5 = all software, 1-3 = responsible for movement of data, Layer 4 = sits on top of the communication)
Please Do Not Throw Sausage Pizza Away (mnemonic device), or All People Seem To Need Data Processing (7-1)
Layer 1 (OSI Model)
Physical: Converts bits into electrical signal over copper cables, or pulses of light for fiber optic cables, or radiofrequency for wireless communication
Physical topologies
Devices: Cables, Connectors, wireless access point, hub, modems, etc
Common connections/cables:
EIA/TIA-232 and EIA/TIA-449
High-Speed Serial Interface (HSSI)
Synchronous Optical Networking (SONET)
V.24 and V.35
Integrated Services Digital Network (ISDN)
Digital Subscriber Line (DSL)
10BASE-T, 10BASE2, 10BASE5, 100BASE-TX, 100BASE-FX, 100BASE-T, 1000BASE-T, 1000BASE-SX
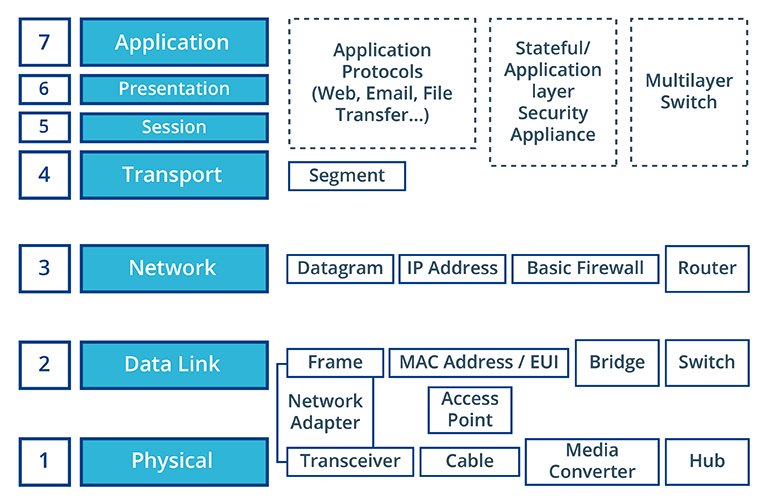
Transceivers, Repeaters, Hubs, and Media converters operate here
Layer 2 (OSI Model)
Data Link: Provides communication within the same network via MAC addresses
Gets packets from the Network Layer
Transmits frames
Detects errors within frames (but doesn’t correct them)
Converts information into bits
Uses MAC/Hardware addresses to communicate
Moves data to the next physically connected device
Two sublayers:
Logical Link Layer (LLC): Upper sublayer, provides flow control and error control
Media Access Control (MAC): Manages protocol access to the physical network medium. It’s responsible for the addressing and channel access control mechanisms that enable several nodes to communicate within a network, typically using a MAC address
Devices: Switches, bridges, AP, NICs
Common Protocols:
Address Resolution Protocol (ARP): Resolves IP into MAC
Reverse Address Resolution Protocol (RARP): Resolves MAC into IP addresses
Point-to-Point Protocol (PPP)
Serial Line Internet Protocol (SLIP)
Layer 2 Forwarding (L2F)
Layer 2 Tunneling Protocol (L2TP)
Point to Point Tunneling Protocol (PPTP)
Ethernet (IEEE 802.3) - only remaining
Fiber Distributed Data Interface (FFDI)
Asynchronous Transfer Mode (ATM)
Copper DDI (CDDI)
Layer 3 (OSI Model)
Network: Provides communication between different networks via IP addresses. Moves data between two hosts that are not generally physically connected. Uses IP
IP is at this layer. IP doesnt use guarantee delivery as its not a connection oriented communication (it only finds the best delivery route)
Uses routing tables to deliver info
Common protocols:
Internet Protocol
Internet Control Message Protocol (ICMP)
Routing Information Protocol (RIP)
Open Shortest Path First (OSPF)
Border Gateway Protocol (BGP)
Supports multicasting
Internetwork Packet Exchange (IPX)
Internet Protocol Security (IPSec)
Network Address Translation (NAT)
Simple Key Management for Internet Protocols (SKIP)
Layer 4 (OSI Model)
Transport: Handles the End-to-End communication either via TCP for connection-oriented communication or UDP for connectionless communication
One of the busiest layers. Creates an end-to-end transport between peer hosts. Responsible for checking the data. UDP is connectionless and known as “best effort”, TCP is connection oriented and known as reliable (TCP uses flags). Port numbers are assigned at this layer
Common protocols:
Transmission Control Protocol (TCP): full-duplex connection-oriented
User Datagram Protocol (UDP): simplex connectionless
Secure Sockets Layer (SSL)
Transport Layer Security (TLS)
Sequenced Packet Exchange (SPX)
TCP and UDP ports
Well-known ports: Ports 0-1023
Registered ports: Ports 1024-49151, registered by vendors
Dynamic or Private Ports: Ports 49152-65535
Ports help tell the machine what kind of data it is
multilayer switches can be used here, which can work as load balancers typically. firewalls can also exist here
Layer 5 (OSI Model)
Session: Provides dialog control by allowing multiple persistent connections from different sources to be properly combined or synchronized.
Provides a logical persistent connection between peer hosts; basically manages conversation between applications exchanging data.
Creates, monitors, and tears down sessions
Full Duplex (send and receive data simultaneously - ex. switch), Half Duplex (only send or receive at a time - ex. hub), Simplex (a device that can only send data - ex. satellite)
Protocols:
Network File System (NFS)
Structured Query Language (SQL)
NetBIOS
Remote Procedure Call (RPC)
Layer 6 (OSI Model)
Presentation: Gets the data ready for the application layer by converting, translating, encoding, compressing, and encrypting data.
This layer is concerned about formatting the data. Main services:
Data Conversion
Character Code Translation
Compression
Encryption/Decryption
Format examples:
American Standard Code for Information Interchange (ASCII)
Extended Binary-Coded Decimal Interchange Mode (EBCDIC)
Tagged Image File Format (TIFF)
Joint Photographic Experts Group (JPEG)
Motion Picture Experts Group (MPEG)
Musical Instrument Digital Interface (MIDI)
Layer 7 (OSI Model)
Application: Generates data to be transmitted, processes data that is received. Application refers to application-level protocols and services used by end-user applications to communicate/send data over a network.
The entry door to network services at a lower level. Apps use this layer to get services when they transfer or receive data over a network.
Applications sit on top of this layer
Responsible for interfacing user applications, network mgmt. services, remote access, etc.
Prone to hackers
ex protocols in this layer:
Simple Mail Transfer Protocol (SMTP) - 25
Simple Network Management Protocol (SNMP) - 161
Hypertext Transfer Protocol (HTTP) - 80
Line Printer Daemon (LPD)
File Transfer Protocol (FTP) - 21
Telnet - 23
Trivial File Transfer Protocol - 69
Electronic Data Interchange (EDI)
Post Office Protocol version 3 (POP3) - 110
Internet Message Access Protocol (IMAP) - 143
Network News Transport Protocol (NNTP)
Secure Remote Procedure Call (S-RPC) RPC - Session
Secure Electronic Transaction (SET)
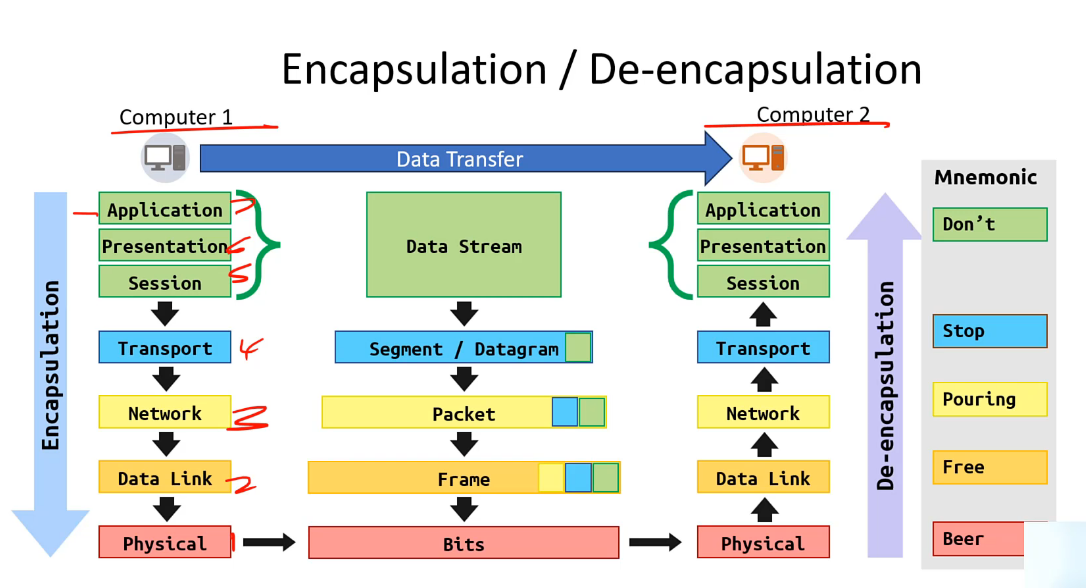
Encapsulation/De-encapsulation
When data goes from one machine to another, data is encapsulated into different things (Data Stream>Segment/Datagram>Packet>Frame>Bits), and then de-encapsulated upon arrival in reverse order.
Ex: Segment section may add port number to the Data Stream, Packet adds IP address, Frame adds MAC address
Dont Stop Pouring Free Beer mnemonic
At which layer of the OSI model does the encapsulation process begin?
Answer: application
Protocol Data unit
Network packet encapsulating a data payload from an upper layer protocol with header fields used at the current layer.