L17 - T17C - S6 – Best Practices for Malware Removal
1/4
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
5 Terms
The 7-step process for malware removal (IQDRSEE)
Investigate and verify malware symptoms.
Quarantine infected systems.
Disable System Restore in Windows.
Remediate infected systems
Update anti-malware software.
Scanning and removal techniques (e.g., safe mode, preinstallation environment)
Schedule scans and run updates.
Enable System Restore and create a restore point in Windows.
Educate the end user
On-access scanning
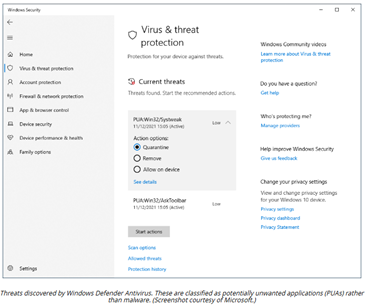
Detection
Most malware is discovered via ______ by an antivirus product.
If the malware is sophisticated enough to evade automated _____, certain symptoms may lead you to suspect infection
Malware Encyclopaedia / Bestiary
Library of information held by antivirus vendors with complete information about the type, symptoms, purpose, and removal of viruses, worms, Trojans, and rootkits
Can be used to verify the symptoms that you discover on a local system against known malware indicators and behaviours
The first 4 steps of the 7-step malware best-practice routine
Investigate and verify malware symptoms.
Quarantine infected systems.
Disable System Restore in Windows.
Remediate infected systems
Update anti-malware software.
Scanning and removal techniques (e.g., safe mode, preinstallation environment)
Last 3 steps of the 7-step malware best-practice routine
Schedule scans and run updates.
Enable System Restore and create a restore point in Windows.
Educate the end user