Comp Sci Mock PAPER 1 Flashcards
1/35
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
36 Terms
1.1.3 - Outline Compatability Issues (You may need to use 1 of these or multiple in correlation with the exam scenario)
Hardware compatibility: New software may require newer hardware (e.g., not enough RAM, wrong CPU).
Software/platform compatibility: The system might not run on certain OSs or require specific runtime environments.
Data/file format compatibility: Files from old systems may not open correctly in new ones.
Peripheral/device compatibility: Older printers or scanners may not work with the new system.
1.1.4 - Compare the implementation of systems using a client’s hardware with hosting systems remotely.
Client Hardware:
Pros: Greater control over hardware; faster internal access.
Cons: High upfront cost; maintenance responsibility falls on client.
Remote Hosting (Cloud):
Pros: Scalable; lower upfront cost; updates and backups managed by provider.
Cons: Requires stable internet; potential data privacy concerns.
1.1.5 Evaluate alternative installation processes
Direct Changeover
+ Fast transition
– High risk if system fails (no backup)Parallel Running
+ Safe; compare old/new outputs
– Expensive; duplicate effortPhased Implementation
+ Gradual rollout; easier to isolate bugs
– Slower; risk of integration issues
1.1.6 What are the problems that may arise as part of data migration? (USUALLY 4 ONLY NEEDED)
Data Loss – Records may be lost due to failed transfers or incorrect mappings.
Data Corruption – Incompatible formats can damage or distort data during conversion.
Incompatible Data Formats – Old and new systems may store or interpret data differently.
Duplicate Records – Merging data from two systems can create repeated entries.
Inconsistent Data – Conflicting or outdated versions of the same data may exist.
Security Vulnerabilities – Data may be exposed if not encrypted or securely transferred.
System Downtime – Services may become unavailable during the migration process.
Mapping Errors – Incorrect field matching (e.g., date formats or ID fields) leads to errors.
1.1.7 Suggest various types of testing
Unit Testing
Tests individual components or functions.
Ensures each part of the code works independently.
Done by developers.
Integration Testing
Checks how modules/components interact.
Ensures combined parts function correctly together.
Also done by developers.
User Acceptance Testing (UAT)
Performed by the client or end user.
Verifies the system meets user requirements.
Final validation before release.
Beta Testing
Conducted by external users in a real environment.
Identifies bugs and usability issues before launch.
Simulates real-world use.
1.1.8 State the importance of user documentation
Enables users to understand how to operate the system.
Supports effective use of features without technical knowledge.
Reduces need for user support.
Assists in onboarding and training.
Increases user satisfaction and system adoption.
1.1.9 Evaluate different methods of providing user documentation.
User Manuals (Printed/PDF):
✔ Accessible offline
❌ Can become outdated quicklyOnline Help Systems (Web-based):
✔ Searchable, easily updated
❌ Requires internet accessEmbedded Help (Tooltips/Pop-ups):
✔ Contextual guidance during use
❌ Limited depth, may interrupt workflowVideo Tutorials:
✔ Visual, effective for demonstrations
❌ Time-consuming to watch, harder to update
The best method depends on user needs. Combining multiple formats (hybrid approach) is often most effective.
1.2.4 Identify the relevant stakeholders when planning a new system.
End-users: Will use the system regularly.
Clients: Fund the system and set goals.
Project Managers: Oversee system development.
Developers: Design and build the system.
Regulators/Legal authorities: Ensure compliance with laws.
IT Support/Maintenance staff: Maintain and troubleshoot the system.
1.2.5 Describe methods of obtaining requirements from stakeholders
Interviews:
One-on-one, detailed responses but time-consuming.Surveys/Questionnaires:
Collect data from many users; limited depth.Observation:
Watch users in real environments; may lack context.Document Analysis:
Study existing systems or records for insights.
1.2.6 Describe appropriate techniques for gathering information needed to arrive at a workable solution
Interviews: Understand needs through direct questioning.
Surveys: Gather large-scale user opinions quickly.
Observation: Identify workflow issues by watching users.
Prototyping: Create and test early versions for feedback.
Document Analysis: Examine existing systems, manuals, and reports.
2.1.1 Draw a diagram representing a CPU and it’s components
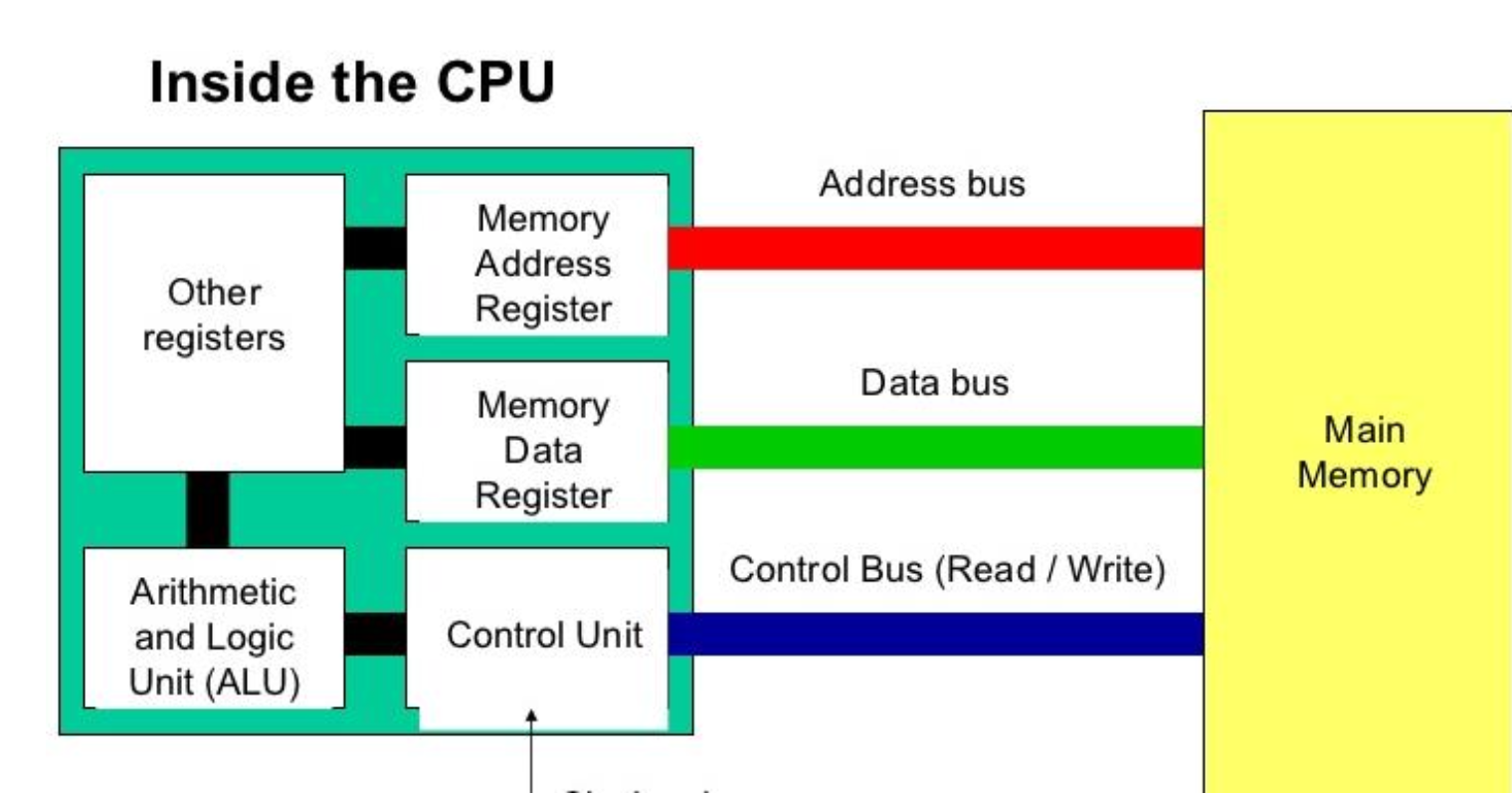
2.1.1 What does the ALU stand for and what does it do.
The Arithmetic Logic Unit does all the
arithmetical and logical calculations.
2.1.1 What does the CU stand for and what does it do.
The control unit handles loading new commands and decoding them.
2.1.1 What does the MDR stand for and what does it do.
The Memory Data Register holds data that will be written to the RAM or read from the RAM
2.1.1 What does the MAR stand for and what does it do.
The Memory Address Register contains the RAM Address of the instruction the CPU wants next
2.1.1 What is used to measure CPU speed?
CPU speed is measured in Hertz (Hz)
2.1.2 What are the two types of Primary Memory?
Primary memory has two types RAM - Random Access Memory, and ROM - read only memory
2.1.2 Describe the differences between the two types of Primary Memory?
RAM: Volatile (which means all data is lost if power is lost), it contains all the users programs and data that has been loaded since booting up. usually upgraded, meaning it can be increased.
ROM: Non-volatile (which means data is
always retained. contains BIOS (basic
input/output system) which instructs the
computer to do basic functions like booting
and keyboard control, and is part of the
motherboard, which makes it difficult to
upgrade.
2.1.3 What is the purpose of Cache Memory
The purpose of cache memory is to
temporarily store frequently accessed data
and instructions to provide faster access for
the processor, improving overall system
performance.
2.1.3 How cache memory can speed up the
functioning of a processor
Cache memory speeds up the functioning of a processor by storing frequently used data and instructions closer to the CPU. Since cache memory is much faster than regular RAM, the processor can quickly access the needed information without having to fetch it from slower main memory, reducing the time taken for data retrieval and execution.
4.3.1 - State the fundamental operations of a
computer
Add
Compare
Retrieve/Load
Store/Save
4.3.3 - What are the essential features of a
computer language
Fixed Vocabulary
Unambiguous meaning
Semantics (Consistant grammar, Consistant syntax)
4.3.4 - What are the differences and similarities between High Level Langages, Assembly Languages and Machine Language.
All languages are eventually translated back down to Machine Languages, whereas high level is simliar to human language, Assembly uses mneumonics to create instructions, and Machine uses 1s and 0s (Binary).
4.3.5- Outline the need for a translation
process from a higher level language to a
machine executable
Becuase of the huge difference between higher and machine level languages there needs to be ways to translate between the two. Compilers, Interpreters and Virtual Machines are able to do this translation.
4.3.4 - Explain the need for high-level programming languages. [3]
High-level languages abstract low-level details, making code easier to read, write, and maintain. They are portable across systems and support complex data structures.
4.3.6 - Define a Variable
Storage location for data in a program
4.3.6 - Define a Constant
Identidfier with an associated value which cannot be altered
4.3.6 - Define an Operator
A character or set of characters, or symbol that represents an action
4.3.6 - Define an Object
Instance of a class, a collection of data and methods.
Analyse the use of variables, constants, and operators in this algorithm:
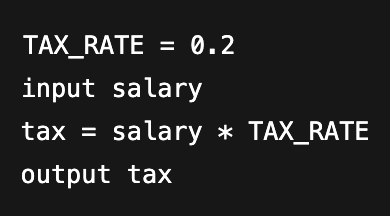
TAX_RATEis a constant.salaryandtaxare variables.*is a multiplication operator.=assigns the result of the expression totax.
4.2.1 Distinguish between sequential search and binary search.
Sequential search: Checks each element one by one; works on unsorted lists.
Binary search: Repeatedly divides sorted list in half; requires sorted array.
Binary search is faster (O(log n)); sequential is O(n).
4.2.2 Outline standard operations of collections.
addItem(): Adds an elementgetNext(): Returns next itemresetNext(): Resets pointer to starthasNext(): Checks for next itemisEmpty(): Returns true if empty
5.1.11 – Describe the features of a Dynamic Data Structures
Can change size during runtime
Memory is allocated as needed
Efficient for unknown or changing data sizes
Examples: linked lists, stacks, queues
5.1.12 Describe how linked lists operate logically.
Each node contains data and a pointer to the next node
Starts with a head reference
Ends with null pointer
Dynamic and allows efficient insertion/deletion
5.1.14 Describe how trees operate logically.
Hierarchical structure of nodes
Each node has 0 or more children
Has a root, branches, and leaf nodes
Binary tree: max 2 children per node
5.1.15 Define the terms: root, node, child, parent, leaf, subtree.
Root: Topmost node
Node: Element of the tree
Parent/Child: Relationship between connected nodes
Leaf: Node with no children
Subtree: Tree formed from any node and its descendants