Information technology terminologies
1/51
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
52 Terms
FTP (File Transfer Protocol)
Is a standard network protocol used for the transfer of files from one host to another over a TCP-based network, such as the Internet.
Transmission Control Protocol (TCP)
Is a communications standard that enables application programs and computing devices to exchange messages over a network. It is designed to send packets across the internet and ensure the successful delivery of data and messages over networks.
The difference between FTP and TCP in it
FTP (File Transfer Protocol)
Manages the commands (e.g.,
GET,PUT) and data streams for file operations.Layer: Operates at the Application Layer of the TCP/IP model.
TCP (Transmission Control Protocol)
Function: Breaks data into packets, numbers them, sends them, and reassembles them at the destination, managing flow and retransmitting lost packets.
Layer: Operates at the Transport Layer.
Basically TCP is everything that happens in between of transferring files
Difference between TCP and IP
They're often mentioned together as "TCP/IP" because they work as a team—IP gets packets to the right destination, while TCP makes sure the data arrives correctly and completely.
Telnet
Which is a network protocol that lets you remotely access and control another computer over a network or the internet.
Telnet works like a virtual terminal—you can connect to a remote machine and type commands as if you were sitting right in front of it. It was widely used in the early days of the internet for remote administration of servers and network devices.
Largely replaced by SSH (Secure Shell), which encrypts all communication
Ports
They are essentially virtual "doors" or endpoints on a computer that allow different network services and applications to communicate simultaneously over the same network connection.
Why we need ports:
Your computer has only one IP address, but you might be running multiple network applications at once—web browsing, email, gaming, video calls, etc. Ports let your computer keep track of which data belongs to which application.
Port numbers:
Range from 0 to 65535
0-1023: Well-known ports (reserved for common services)
1024-49151: Registered ports (assigned to specific applications)
49152-65535: Dynamic/private ports (used temporarily by applications)
SSH (Secure Shell)
Is a protocol for securely connecting to and controlling remote computers over a network. It's the modern, secure replacement for Telnet.
The browser (web browser)
Is the application you use to access and view websites on the internet—like Chrome, Firefox, Safari, Edge, or others.
Internet telephony (also called VoIP - Voice over Internet Protocol)
Is technology that lets you make voice and video calls over the internet instead of traditional phone lines.
Range check
This is a type of validation rule that ensures data entered into a field falls within a specified minimum and maximum value.
Purpose: It prevents invalid or unrealistic data from being stored in the database by checking if a value is within acceptable boundaries.
Examples:
Age field:
Range: 0 to 120
Rejects entries like -5 or 200
Exam score:
Range: 0 to 100
Rejects entries like 150 or -10
Sequential Organization
Files are stored in order, one record after another, typically sorted by a key field (like ID number or date). To find a record, you must search from the beginning until you find it.
Advantages: Simple, efficient for processing all records in order, good for batch processing
Disadvantages: Slow for searching specific records, inefficient for updating or inserting records
Indexed Sequential Organization
Combines sequential storage with an index (like a book's index). Records are stored sequentially, but an index points to the location of specific records.
Advantages: Faster searching than pure sequential, supports both sequential and direct access
Disadvantages: Requires maintaining the index, uses extra storage space
Direct/Random Organization (Hashing)
Records are stored at locations calculated using a hash function based on the key field. You can go directly to a record's location.
Advantages: Very fast access to specific records, efficient for lookups
Disadvantages: Not suitable for sequential processing, collision handling needed, wasted space
Indexed Organization
Uses separate index files to locate records quickly. Multiple indexes can exist for different fields.
Advantages: Fast searching on indexed fields, flexible
Disadvantages: Overhead of maintaining indexes, uses extra storage
Serial Organization
Records stored in the order they arrive, with no particular sorting.
Advantages: Fast insertion, simple
Disadvantages: Very slow searching, inefficient for most operations
A hash function
This is a mathematical algorithm that takes input data (like a name, ID number, or any value) and converts it into a fixed-size number called a hash value or hash code. This number is then used to determine where to store or find that data.
How it works: Input → Hash Function → Hash Value (storage location)
Simple example: Let's say you're storing student records by ID number, and you have 100 storage locations (0-99).
Simple hash function: ID % 100 (modulo operation—remainder after division)
Student ID 12345 → 12345 % 100 = 45 (store at location 45)
Student ID 98721 → 98721 % 100 = 21 (store at location 21)
Student ID 50003 → 50003 % 100 = 3 (store at location 3)
A key field (or just key)
This is a field in a database table or file that uniquely identifies each record, allowing you to find and reference specific records.
Main purpose: To distinguish one record from all others and provide a way to quickly locate, update, or delete specific records.
Index files
These are separate files that work like a book's index—they contain pointers that help you quickly find records in the main data file without having to search through everything sequentially.
How they work: The index file stores pairs of values:
Key field value (like StudentID or Name)
Pointer/address to where that record is located in the main data file
Transaction processing
This is a method of organizing and managing database operations where related actions are grouped together as a single unit of work called a transaction. The system ensures that either all parts of the transaction complete successfully, or none of them do.
What is a transaction?
A sequence of database operations that must be completed as one atomic unit. If any part fails, the entire transaction is rolled back (undone).
Classic example - Bank transfer: Transferring $100 from Account A to Account B involves:
Deduct $100 from Account A
Add $100 to Account B
Atomic unit
An atomic unit means something that is indivisible
Types of transaction processing systems:
Batch processing: Transactions collected and processed together at scheduled times (like processing all day's checks at night)
Real-time/Online processing: Transactions processed immediately as they occur (like ATM withdrawals, online shopping)
Query by Example (QBE)
Is a visual, user-friendly method of querying databases where you specify what you want by filling in example values in a table-like grid, rather than writing code or complex query language.
Data Definition Language (DDL)
is a subset of SQL commands used to define and manage the structure of a database—creating, modifying, and deleting database objects like tables, indexes, and schemas.
Key point: DDL deals with the structure of the database, not the data inside it.
What DDL defines:
Tables: Structure with columns and data types
Constraints: Rules like PRIMARY KEY, FOREIGN KEY, UNIQUE, NOT NULL, CHECK
Indexes: For faster searching
Views: Virtual tables based on queries
Schemas: Overall database structure
DDL vs DML (Data Manipulation Language):
DDL (structure):
CREATE, ALTER, DROP, TRUNCATE
Defines HOW data is stored
Example: Creating a Students table
DML (data):
SELECT, INSERT, UPDATE, DELETE
Works WITH the data
Example: Adding a new student record
Real-world analogy: Think of building a house:
DDL = Designing and building the structure (rooms, walls, plumbing layout)
DML = Moving furniture in and out, decorating, living in it
SQL (Structured Query Language)
The standard language for managing and querying databases—uses commands like SELECT, INSERT, CREATE, etc.
DATA QUALITY ATTRIBUTES
1. Data Integrity Accuracy, consistency, and reliability of data throughout its lifecycle. Ensures data is correct and trustworthy.
2. Data Consistency Data is uniform and doesn't contradict itself across the database. Same data stored in multiple places has the same value.
3. Data Accuracy Data correctly represents the real-world values it's supposed to model.
4. Data Validity Data conforms to defined formats, types, and ranges (validation rules).
5. Data Completeness All required data is present with no missing values where they're needed.
6. Data Redundancy Duplicate storage of the same data (usually something to minimize through normalization).
7. Data Independence Ability to change data storage structure without affecting applications that use the data.
DATABASE SECURITY CONCEPTS:
8. Data Security Protection of data from unauthorized access, corruption, or theft.
9. Data Privacy Controlling who can access personal or sensitive information.
10. Access Control Managing user permissions (who can read, write, update, delete data).
DATA MANAGEMENT CONCEPTS:
11. Data Redundancy (mentioned above) Storing the same data multiple times.
12. Data Atomicity Operations are indivisible—they either complete fully or not at all (part of ACID properties).
13. Data Durability Once data is committed, it remains saved even after system failures.
14. Data Isolation Concurrent transactions don't interfere with each other.
15. Data Concurrency Multiple users can access data simultaneously without conflicts.
16. Data Recovery Ability to restore data after system failures or errors.
17. Data Backup Creating copies of data for protection against loss.
1. TITLE BAR
The horizontal bar at the very top of a window that displays the window's title (name of the document or application).
Features:
Shows program/document name (e.g., "Document1 - Microsoft Word")
Usually contains window control buttons (minimize, maximize, close)
Can be dragged to move the window
2. MENU BAR
The bar directly below the title bar containing drop-down menus with commands and options.
Examples:
File, Edit, View, Insert, Format, Tools, Help
3. TOOL BAR (or Toolbar)
A bar containing buttons and icons for quick access to commonly used commands.
Features:
Icons/buttons for actions like Save, Print, Cut, Copy, Paste, Bold, Italic
4. SCROLL BAR
Vertical or horizontal bars on the edges of a window that let you navigate through content that doesn't fit on screen.
Types:
Vertical scroll bar: Right side, scrolls up/down
Horizontal scroll bar: Bottom, scrolls left/right
5. STATUS BAR
The bar at the bottom of a window displaying information about the current state or selected item.
Examples of what it shows:
Page number and word count (in Word)
File size and number of items (in File Explorer)
6. TASK BAR
The bar at the bottom (or side) of your screen in the operating system (Windows), not inside individual windows.
Features:
Shows currently running programs/applications
Contains the Start button (Windows)
7. SIZING BAR
The edges and corners of a window that you can drag to resize the window.
8. WINDOW TITLE
This is the same as Title Bar—the text displayed at the top of a window showing the application or document name.
COMMON HTML TAGS:
Document Structure:
<html>- Root element of the page<head>- Contains metadata (not displayed)<title>- Page title (shows in browser tab)<body>- Main content area (what users see)
Headings:
<h1>- Largest heading<h2>- Second level heading<h3>through<h6>- Progressively smaller headings
Text Formatting:
<p>- Paragraph<br>- Line break (self-closing)<hr>- Horizontal line (self-closing)<strong>or<b>- Bold text<em>or<i>- Italic text<u>- Underlined text<mark>- Highlighted text<small>- Smaller text<del>- Strikethrough text<sup>- Superscript<sub>- Subscript
Lists:
<ul>- Unordered (bulleted) list<ol>- Ordered (numbered) list<li>- List item
Links:
<a href="url">- Hyperlink
Images:
<img src="url" alt="description">- Image (self-closing)
<table>- Table<tr>- Table row<th>- Table header cell<td>- Table data cell
Forms:
<form>- Form container<input>- Input field<textarea>- Multi-line text input<button>- Button<select>- Dropdown menu<label>- Form label
Input Types:
type="text"- Text fieldtype="password"- Password fieldtype="email"- Email fieldtype="number"- Number fieldtype="checkbox"- Checkboxtype="radio"- Radio buttontype="submit"- Submit button
Divisions and Sections:
<div>- Generic container (block-level)<span>- Generic container (inline)<header>- Header section<nav>- Navigation section<main>- Main content<section>- Content section<article>- Independent content<aside>- Sidebar content<footer>- Footer section
Media:
<video>- Video player<audio>- Audio player<iframe>- Embedded frame (for other web pages.
HTML ATTRIBUTES:
Tags can have attributes that provide additional information
Common attributes:
id="unique-name"- Unique identifierclass="classname"- CSS class for stylingstyle=""- Inline CSS stylinghref="url"- Link destinationsrc="url"- Image/media sourcealt="description"- Alternative textwidth="100"- Widthheight="100"- Heighttitle="tooltip"- Tooltip text
COMMENTS:
html
<!-- This is a comment, not displayed on the page -->PROCESS
This is a series of actions or steps taken to achieve a particular result or goal.
FORMULA
This is a mathematical rule or relationship expressed using symbols, numbers, and operators.
FUNCTION
This is a reusable block of code or a predefined operation that performs a specific task and can return a value.
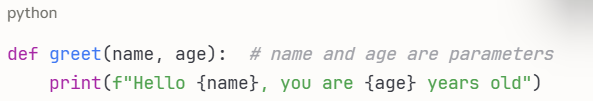
PARAMETER
Also called argument is a value or variable that is passed into a function or formula to customize its behaviour.
TELNET SERVICES
These are network services that can be accessed remotely using the Telnet protocol.
What they include:
Remote login: Access a remote computer's command line
Remote system administration: Manage servers from anywhere
Accessing specific services: Connect to mail servers, web servers, databases
BBS (Bulletin Board Systems): Early online communities accessed via Telnet
MUD games (Multi-User Dungeons): Text-based multiplayer games
INTERNET PORTALS
These are websites that serve as gateways or starting points to the internet, aggregating various services and information in one place.
Characteristics:
Single entry point to multiple services
Personalized content
Search functionality
News, email, weather, stocks
Links to various resources
MESSAGE BOARDS (also called Forums or Discussion Boards)
These are online discussion platforms where users can post messages, reply to others, and have threaded conversations.
Structure:
Categories: Broad topic areas
Forums: Specific subtopics within categories
Threads: Individual discussion topics
Posts: Individual messages within threads
AUTHORING TOOLS
These are software applications used to create digital content, particularly for web pages, e-learning courses, multimedia presentations, and interactive content.
Types of authoring tools:
1. Web Authoring Tools: Create websites and web pages
2. Multimedia Authoring Tools: Create interactive presentations and media
3. E-Learning Authoring Tools: Create educational and training content
4. Document Authoring eg google docs
5. Graphics Authoring eg canva
Terms used to assess and analyze content, information, websites, and media
CURRENCY How recent or up-to-date the information is.
DESIGN Visual layout, organization, and usability.
COVERAGE (SCOPE) Depth and breadth of information; how thoroughly a topic is covered.
AUDIENCE The intended readers or users; who it's designed for.
OBJECTIVITY Presenting information fairly without bias or personal opinions.
ACCURACY Information is correct, error-free, and verifiable.
AUTHORITY (CREDIBILITY) Expertise and trustworthiness of the author or source.
PURPOSE The reason content was created (inform, persuade, sell, entertain, educate).
RELIABILITY Consistency and dependability; can be trusted.
RELEVANCE How closely information relates to your needs or topic.
ACCESSIBILITY How easy it is to obtain and use the information.
COMPLETENESS Information is thorough with all necessary details.
READABILITY How easy the content is to read and understand.
PERSPECTIVE (POINT OF VIEW) The angle or viewpoint from which information is presented.
TONE The attitude or mood conveyed in the writing (formal, casual, serious, humorous).
USABILITY How easy and intuitive it is to use (mainly for websites/apps).
STABILITY Whether information and source will remain available over time.