iot
1/73
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No study sessions yet.
74 Terms
Concept and Planning
This phase defines the problem statement, objectives, and feasibility of the IoT
system.
Problem Identification.
Finding a real-world problem an IoT system can
effectively address comes first. This calls for a thorough understanding of the
background and demands of possible customers. Find first the actual problem
the IoT system will solve.
Stakeholder Analysis.
Focus particularly on recognizing every individual,
business, group, or interest affected by the IoT project. Designing a good and
acceptable solution relies on being aware of their needs and expectations.
Users.
The individuals who will directly connect with or benefit from
the IoT system—farmers employing a smart irrigation system,
homeowners getting flood warnings, company owners using an e-
commerce platform.
Developers.
The team in charge of planning, constructing, and
implementing the IoT system.
Organizations.
Entities such as local government agencies, agricultural
cooperatives, private businesses that might fund, own, or profit from the
IoT system.
Feasibility Study.
One should assess whether the proposed IoT project is
acceptable and feasible before making significant investments. It estimates the
likelihood of success considering numerous elements.
Technical Feasibility.
Can the project be completed with the knowledge
and tools at hand? It involves evaluating:
Financial Feasibility.
Is the project financially viable?
Calculating Total Cost of Ownership (TCO).
Estimating all costs
associated with the project over its entire lifecycle, including
hardware, software development, cloud services, deployment,
maintenance, and operational expenses.
Return on Investment (ROI).
Analyzing the potential benefits
compared to the costs to determine if the investment is
worthwhile.
Funding Sources.
Identifying potential sources of funding for the
project
Operational Feasibility.
Can the organization effectively operate and
maintain the IoT system once it's deployed?
Technology Research.
Identify and evaluate the most suitable technologies for
the IoT system based on the project requirements and feasibility study.
Identify Suitable IoT Devices.
Researching and comparing different
types of sensors (temperature, humidity, motion, etc.), actuators,
microcontrollers (Arduino, Raspberry Pi), and gateways, considering
factors like accuracy, cost, power consumption, durability, and
compatibility.
Identify Cloud Platforms.
Evaluating various IoT platforms (AWS IoT,
Azure IoT, Google Cloud IoT, ThingSpeak, etc.) based on features like
data storage, processing capabilities, analytics tools, security features,
scalability, and pricing.
Identify Communication Protocols.
Selecting appropriate
communication protocols for data transmission between devices and the
cloud, considering factors like range, bandwidth, power consumption,
reliability, and security (e.g., Wi-Fi, Bluetooth, Zigbee, LoRaWAN,
NB-IoT, 5G).
Regulatory Compliance.
Check industry regulations (e.g., GDPR for data
privacy, FCC for wireless communication), ensuring compliance with data
protection laws and industry standards.
Check Industry Regulations.
Identifying any specific regulations that
apply to the industry of the IoT application (e.g., agricultural standards,
healthcare regulations).
Ensure Compliance with Data Protection Laws.
Understanding and
complying with laws related to the collection, storage, and processing of
personal data. In the Philippines, this primarily involves the “Data
Privacy Act of 2012”.
Wireless Communication Regulations.
Adhering to regulations set by
the local telecommunications authority (e.g., the National
Telecommunications Commission (NTC) in the Philippines) regarding
the use of wireless communication frequencies and power levels.
Security Standards.
Following established security standards and best
practices for IoT devices and data to protect against cyber threats.
Problem Definition Document.
This document serves as the foundation of the
entire IoT project. It clearly and concisely articulates the real-world problem or
opportunity that the proposed IoT system aims to address.
Executive Summary.
A brief overview of the problem and the proposed
solution.
Background.
Provides context about the problem, including its
prevalence, impact, and any existing solutions (and their limitations).
Problem Statement.
A clear, concise, and unambiguous statement
defining the core issue.
Problem Validation.
Evidence supporting the existence and significance
of the problem. This could include statistics, research findings, user
feedback, or expert opinions.
Scope.
Defines the boundaries of the problem being addressed by this
specific project.
Goals and Objectives.
This section outline the initial high-level
objectives the project aims to achieve in solving the problem.
Timeline
A high-level timeline for the major phases of
the project.
Market Research Report.
This report analyzes the market landscape relevant to
the proposed IoT solution. It helps understand the potential demand, identify
competitors, and assess the target audience.
Industry Overview.
Provides a general overview of the industry the IoT
solution will operate within
Target Audience Analysis.
Identifies and describes the potential users or
beneficiaries of the IoT solution. This includes demographics, needs,
pain points, and current behaviors.
Competitor Analysis.
Identifies existing solutions or competitors in the
market, analyzing their strengths, weaknesses, pricing, and market
share.
Market Trends.
Explores current and future trends relevant to the IoT
solution, such as adoption rates, technological advancements, and
market growth projections.
Potential Market Size and Revenue Streams.
Estimates the potential
market size and explores different ways to generate revenue from the
IoT solution.
Requirement Analysis and Design
This phase is very important since it converts the high-level objectives and problem
characterization from the "Concept and Planning" phase into exact technical
requirements and an IoT system blueprint.
System Requirement Analysis.
Determine each requirement the IoT system
needs. This guarantees that the development team recognizes what has to be
developed and that the end result meets the needs of the stakeholders.
Functional Requirements.
These demonstrate what the system is
supposed to do. They outline the particular operations, processes, and
features the system has to be able to execute.
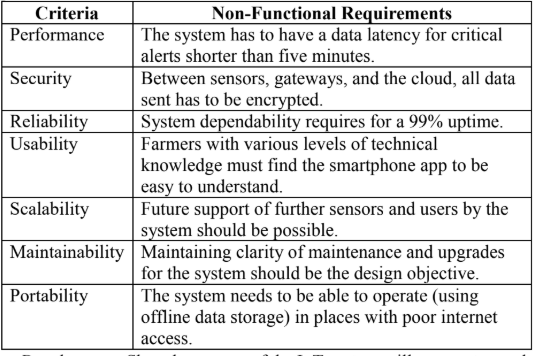
Non-Functional Requirements.
These explain how well the system
should perform. They define the system's limits and characteristics
which includes performance, security, reliability, usability, scalability,
maintainability, and portability.
Non-Functional Requirements.
Use Case Development.
Show how users of the IoT system will engage to reach
particular objectives. Use cases ensures that the design satisfies user needs and
assist one learn about the system from their point of view.
Identifying Actors.
Determining who will be interacting with the IoT
system.
Defining Use Cases.
Explaining the series of steps a user takes to finish
a given task. Usually, each use case consists in a trigger, a set of actions,
and the result.
Creating Use Case Diagrams.
Making a visual representation that
illustrates the connection among actors and use cases.
High-Level Architecture Design.
Specify the overall framework of the Internet
of Things system and the interactions among its various components. For the
development staff, this serves as a road map.
Devices.
The physical devices that collect data from the
environment or perform actions.
Gateways.
Devices that aggregate data from multiple sensors
and provide connectivity to the network.
Network.
The communication channels used to transmit data.
Cloud Platform.
The backend infrastructure for data storage,
processing, analytics, and device management.
Applications.
The user interfaces for interacting with the system.
Defining Communication Flow.
Mapping how data will flow between
the identified components.
Choosing Architectural Patterns.
Selecting appropriate architectural
styles such as centralized, distributed, edge computing, and etc.
Hardware and Sensor Selection.
Select the particular hardware components the
IoT system will make use of. The functioning, performance, and cost of the
system depend on the decision made.
Sensor Selection.
Selecting sensors depending on the type, accuracy,
range, power consumption, cost, and environmental compatibility
Actuator Selection.
Selecting actuators depending on the type, power
consumption, control systems, and the tasks the system must do.
Microcontroller Selection.
Selecting the processor unit for IoT device
such as Arduino or Raspberry Pi based on processing capability,
memory, connectivity choices, and pricing takes careful thought.
Network and Protocol Selection.
Choose the channels of communication among
the several IoT system components. Choice of network and protocols affects
security, bandwidth, power consumption, and range.
Network Selection.
Selecting the suitable network technology such as
Wi-Fi for local networks, Bluetooth for short-range communication,
LoRa/NB-IoT for long-range, low-power communication in agricultural
areas, and/or cellular for more general coverage involves careful
consideration.
Protocol Selection.
Security Planning.
Design and carry out security policies that protect the IoT
system and the data it manages from unauthorized access, use, disclosure,
disruption, alteration, or destruction.
Data Encryption.
Implementing end-to-end encryption to protect data
both in transit and at rest.
Authentication and Authorization.
Ensuring that only authorized devices
and users can access the system. Multi-factor authentication and/or
digital certificates may be used.
Device Security.