AQA A-Level Computer Science
5.0(1)
5.0(1)
Card Sorting
1/174
Earn XP
Description and Tags
Study Analytics
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
175 Terms
1
New cards
Functional abstraction
A mapping from one set of values to another. The result of this mapping is unique to a given set of inputs, and a value must always be returned
2
New cards
Procedural abstraction
Using a procedure to carry out a sequence of steps for achieving some task
3
New cards
Information hiding
Where data is not directly accessible and can only be accessed through defined procedures/functions
4
New cards
Decomposition
Breaking down a complex problem into a number of sub-problems, each of which performs an identifiable task
5
New cards
Composition
Combining procedures to form compound procedures (e.g. BuildHouse, BuildStreet). It can also mean combining objects to form compound data, for example records or a data structure such as a queue, tree or list.
6
New cards
Automation
Building and putting into action models to solve problems
7
New cards
Finite state machine
Abstract model of computation used to design computer programs and sequential logic circuits. It can be in one of a finite number of states and changes from one state to the next state when triggered by some condition or input (say, a signal from a timer).
8
New cards
In a finite state machine:
* The machine can only be in one state at a time
* It can change from one state to another in response to an event or condition; this is called a **transition**. Often this is a switch or a binary sensor.
* The Finite State Machine (FSM) is defined by a list of its states and the condition for each transition
* The machine can only be in one state at a time
* It can change from one state to another in response to an event or condition; this is called a **transition**. Often this is a switch or a binary sensor.
* The Finite State Machine (FSM) is defined by a list of its states and the condition for each transition
9
New cards
Finite state automaton
Finite state machine which has no output
10
New cards
Deterministic final state automaton
In a finite state machine, when you are in a particular state, and the next state is uniquely determined by the input
11
New cards
Integer (ℤ)
Any whole number
12
New cards
Natural number (ℕ)
A whole number used in counting
13
New cards
Rational number (ℚ)
Any value that can be expressed as a ratio, or fraction, including all integer values
14
New cards
Irrational number
A value that cannot be expressed as a fraction and has an endless series of non-repeating digits
15
New cards
Ordinal numbers
Describe the numerical positional of objects
16
New cards
Parity bit
Additional bit that is used to check that the other bits transmitted are likely to be correct
17
New cards
Odd parity
The total number of 1s in each bye, including the parity bit, equals an odd number
18
New cards
Even parity
The total number of 1s in each bye, including the parity bit, equals an even number
19
New cards
Majority voting
System that requires each bit to be sent three times. If a bit value is flipped erroneously during transmission over a noisy line, the recipient computer would use the majority rule and assume that the two bits that have not changed were therefore correct
20
New cards
Checksum
Mathematical algorithm that is applied to a ‘unit’ or packet of data. The data in the block is used to create a checksum value which is transmitted with the block. The algorithm is applied to the block after transmission and if the two checksums match, the transmission is deemed to have been successful.
21
New cards
Check digit
Similar to a checksum. An additional digit at the end of a string of other numbers designed to check for mistakes in input or transmission.
22
New cards
Unsigned binary number
Can represent only positive numbers
23
New cards
Signed binary number
Can represent both positive and negative numbers
24
New cards
Two’s complement
One representation of a signed binary number
25
New cards
Fixed point binary number
A way to represent fractions in binary. A binary point is used to separate the whole place values from the fractional part.
26
New cards
Bitmap/raster images
Contain pixels that make up an image
27
New cards
Pixel
A smallest identifiable area of an image, attributed a binary value which represents a single colour
28
New cards
Resolution
Width in pixels \* height in pixels
29
New cards
PPI
Pixels per inch
30
New cards
Pixels per inch
Indicates the density of pixels within an image
31
New cards
Colour depth
The number of bits per pixel, which determines the number of colours that a pixel can represent
32
New cards
Metadata
Data about data
33
New cards
Image metadata
* Width/height in pixels
* Colour depth
* GPS coordinates where the image was taken
* Camera or device used to take the image
* Exposure time
* Focal length
* Colour depth
* GPS coordinates where the image was taken
* Camera or device used to take the image
* Exposure time
* Focal length
34
New cards
Vector graphics
Images made up of geometric shapes or objects. The file contains only the necessary details about each shape in order to redraw the object when the file loads.
Properties of each object include:
* Position
* Radius
* Fill colour
* Line colour
* Line weight
Properties of each object include:
* Position
* Radius
* Fill colour
* Line colour
* Line weight
35
New cards
Sampling rate
The frequency with which you record the amplitude of the sound
36
New cards
Sound sample size
Number of samples per second \* Number of bits per sample \* Length of the sample in seconds
37
New cards
Analogue signal
A continuous signal which represents physical measurements
38
New cards
Digital signal
Discrete time signals generated by digital modulation
39
New cards
Analogue representation
Uses a continuous range of values to represent information
40
New cards
Digital representation
Uses discrete or discontinuous values to represent information
41
New cards
Analogue to digital conversion
1. Microphone converts sound energy into electrical energy
2. ADC (analogue to digital converter) samples the analogue data at a given frequency, measuring the amplitude of the wave at each point and converting it into a binary value according to the resolution or audio bit depth being used for each sample
42
New cards
Digital to analogue conversion
1. Binary values for each sample point are translated back into analogue signals or voltage levels
2. These are sent to an amplifier connected to a speaker, producing sound
43
New cards
Frequency
The speed of oscillation or vibration of a wave, measured in Hertz (Hz)
44
New cards
Nyquist’s theorem
In order to produce an accurate recording, the sampling rate must be at least double that of the highest frequency in the original signal
45
New cards
MIDI
Musical Instrument Digital Interface
46
New cards
Musical Instrument Digital Interface (MIDI)
A technical standard that describes a protocol, digital interface, and connectors which can be used to allow computers and electronic musical instruments to connect and communicate
47
New cards
MIDI controller
* Carries event messages that:
* Specify:
* Pitch and duration of a note
* Timbre
* Vibrato
* Volume changes
* Synchronise tempo between multiple devices
* Specify:
* Pitch and duration of a note
* Timbre
* Vibrato
* Volume changes
* Synchronise tempo between multiple devices
48
New cards
MIDI file
List of instructions that tell it to synthesise a sound based on pre-recorded digital samples and synthesised samples of sounds
49
New cards
Lossy compression
Unnecessary information is removed from the original file
50
New cards
Lossless compression
All the information required to replicate the original file exactly is retained
51
New cards
RLE
Run Length Encoding
52
New cards
Run Length Encoding (RLE)
A method of lossless compression whereby repetitive and consecutive data is replaced with counts of how many are in a row
53
New cards
Dictionary-based compression
A method of
54
New cards
Encryption
The transformation of data from one form to another to prevent an unauthorised third party from being able to understand it.
55
New cards
Plaintext
The original data or message before encryption
56
New cards
Ciphertext
The encrypted data
57
New cards
Key
The secret information to lock or unlock the message
58
New cards
Caesar cipher/shift cipher
A type of substitution cipher that works by shifting the letters of the alphabet along by a given number of characters, the number of characters being the key
59
New cards
Vernam cipher
A type of one-time pad cipher that offers perfect security. A Boolean XOR operation is carried out between the binary representation of each character of the plaintext and the corresponding character of the one-time pad
60
New cards
One-time pad
To provide perfect security, the encryption key must be:
* equal to or longer in characters than the plaintext
* truly random
* used only once.
The sender and recipient must meet in person to securely share the key and subsequently destroy it after encryption and decryption.
Not susceptible to cryptanalysis due to its truly random distribution of characters.
* equal to or longer in characters than the plaintext
* truly random
* used only once.
The sender and recipient must meet in person to securely share the key and subsequently destroy it after encryption and decryption.
Not susceptible to cryptanalysis due to its truly random distribution of characters.
61
New cards
Hardware
The electrical or electro-mechanical parts of a computer and its input, output, and storage devices
62
New cards
Software
All the programs that are written to make computers function
63
New cards
System software
The software needed to run the computer’s hardware and application programs
64
New cards
Operating system
A set of programs that lies between applications software and the computer hardware.
It provides an Application Programming Interface (API) for hardware and software to communicate.
Its functions include:
* Resource management
* Memory management
* Processor scheduling
* Backing store management
* Management of all input and output
* Provision of a user interface
It provides an Application Programming Interface (API) for hardware and software to communicate.
Its functions include:
* Resource management
* Memory management
* Processor scheduling
* Backing store management
* Management of all input and output
* Provision of a user interface
65
New cards
Resource management
Managing all the computer hardware including the CPU, memory, disk drives, keyboard, monitor, printer, and other peripheral devices
66
New cards
Provision of a user interface
Enables users to perform tasks like:
* Running application software
* Changing settings on the computer
* Downloading and installing new software
* Running application software
* Changing settings on the computer
* Downloading and installing new software
67
New cards
Memory management
The allocation and deallocation of memory space for processes, programs, and data.
Virtual memory may be used.
Virtual memory may be used.
68
New cards
Processor scheduling
Allocating processor time to each process in the most efficient way possible, allowing for **multi-tasking**
69
New cards
Roles of the scheduler
* Maximise throughput
* Be fair to all users on a multi-user system
* Provide acceptable response time to all users
* Ensure hardware resources are kept as busy as possible
* Be fair to all users on a multi-user system
* Provide acceptable response time to all users
* Ensure hardware resources are kept as busy as possible
70
New cards
Backing store
A secondary storage device that holds data and programs that are not currently in use by the main memory
71
New cards
Backing store management
* Allocating space on the backing store
* Transferring data and programs between the main memory and the backing store
* Keeping track of the location and status of each file on the backing store
* Keeping track of free areas of storage so new files or applications can be saved
* Allowing users to move files and folders, delete files, and protect others from unauthorised access
* Transferring data and programs between the main memory and the backing store
* Keeping track of the location and status of each file on the backing store
* Keeping track of free areas of storage so new files or applications can be saved
* Allowing users to move files and folders, delete files, and protect others from unauthorised access
72
New cards
Peripheral management
Using device drivers to control the sending and receiving of data to and from peripheral input and output devices. The operating system also ensures peripherals are allocated to processes without causing conflicts.
73
New cards
Interrupt
A signal from a peripheral or software program that causes the operating system to stop processing its current list of instructions
74
New cards
Interrupt handling
When an error occurs and a process interrupted, the operating system must detect the interrupt signal and display an appropriate error message (if appropriate) before deciding what to do next. Interrupts are what allows multi-tasking to take place.
75
New cards
Utility programs
System software designed to optimise the performance of the computer or perform tasks like:
* backing up files
* restoring corrupted files from backup
* compressing or decompressing data
* encrypting data before transmission
* backing up files
* restoring corrupted files from backup
* compressing or decompressing data
* encrypting data before transmission
76
New cards
Disk defragmenter
Program that will reorganise a hard disk so that files which have been split up into blocks and stored all over the disk will be recombined into a single series of sequential blocks
77
New cards
Virus checker
Checks your hard drive, incoming emails, and internet downloads for viruses, and removes them
78
New cards
Library programs
Ready-compiled programs that can be run when needed
79
New cards
Software libraries
Groups of library programs. Most compiled languages have their own libraries of pre-written functions that can be invoked in a defined manner from within the user’s program.
80
New cards
Translators
A translator than translates program code written by a programmer into machine code which can be run by the computer
81
New cards
Compiler
A translator that translates a **high-level language** into **machine code**. It considers the **entire code** and converts it at once, instead of translating code line-by-line.
82
New cards
Interpreter
A translator that contains subroutines to carry out each high-level instruction. It looks at each line of the source program, analyses it, and, if it contains no syntax errors, calls the appropriate subroutine within its own program code to execute the command.
83
New cards
Bytecode
An intermediate representation of a program’s source code combining compiling and interpreting. It is low-level code that is designed for a software interpreter, compiled to run on a virtual machine instead of a CPU.
84
New cards
Advantage of bytecode
Platform independence
85
New cards
Java Virtual Machine (JVM)
An example of a bytecode interpreter that understands Java bytecode and converts it into the machine code for the particular computer it runs on
86
New cards
Advantages of a compiler over an interpreter
* The object code can be saved on disk and run whenever required without the need to recompile
* The object code executes faster than interpreted code
* The object code produced by a compiler can be distributed or executed without having to have the compiler present
* The object code is more secure, as it cannot be read without ‘reverse engineering’
* The object code executes faster than interpreted code
* The object code produced by a compiler can be distributed or executed without having to have the compiler present
* The object code is more secure, as it cannot be read without ‘reverse engineering’
87
New cards
Situations where a compiler would be more appropriate
* When a program is to be run regularly or frequently, with only occasional changes
* When the object code produced by the compiler is going to be distributed or sold to users outside the company that produced the software (as source code is not present)
* When the object code produced by the compiler is going to be distributed or sold to users outside the company that produced the software (as source code is not present)
88
New cards
Advantages of an interpreter over a compiler
* It is useful for program development as there is no need for lengthy recompilation every time an error is discovered
* It is easier to partially test and debug programs
* It is easier to partially test and debug programs
89
New cards
Situations where an interpreter would be more appropriate
* During program development
* In a student environment when students are learning code, as they can test parts of a program before coding it all
* In a student environment when students are learning code, as they can test parts of a program before coding it all
90
New cards
Assembler
Translates an **assembly language** program (source code) into the 0s and 1s of the corresponding **machine code** instruction (object code) **line-by-line**.
91
New cards
Application software
Programs that perform specific user-oriented tasks
92
New cards
General-purpose software
Application software that can be used for many different purposes, e.g.:
* word processors (Word)
* spreadsheet packages (Excel)
* graphics software (Photoshop)
* word processors (Word)
* spreadsheet packages (Excel)
* graphics software (Photoshop)
93
New cards
Special-purpose software
Application software that performs a single specific task or a set of tasks, e.g.
* payroll and accounts packages
* hotel booking systems
* fingerprint scanning systems
* browser software
Can be bought ‘off-the-shelf’, ready to use, or can be specially written by a team of programmers for a particular organisation.
* payroll and accounts packages
* hotel booking systems
* fingerprint scanning systems
* browser software
Can be bought ‘off-the-shelf’, ready to use, or can be specially written by a team of programmers for a particular organisation.
94
New cards
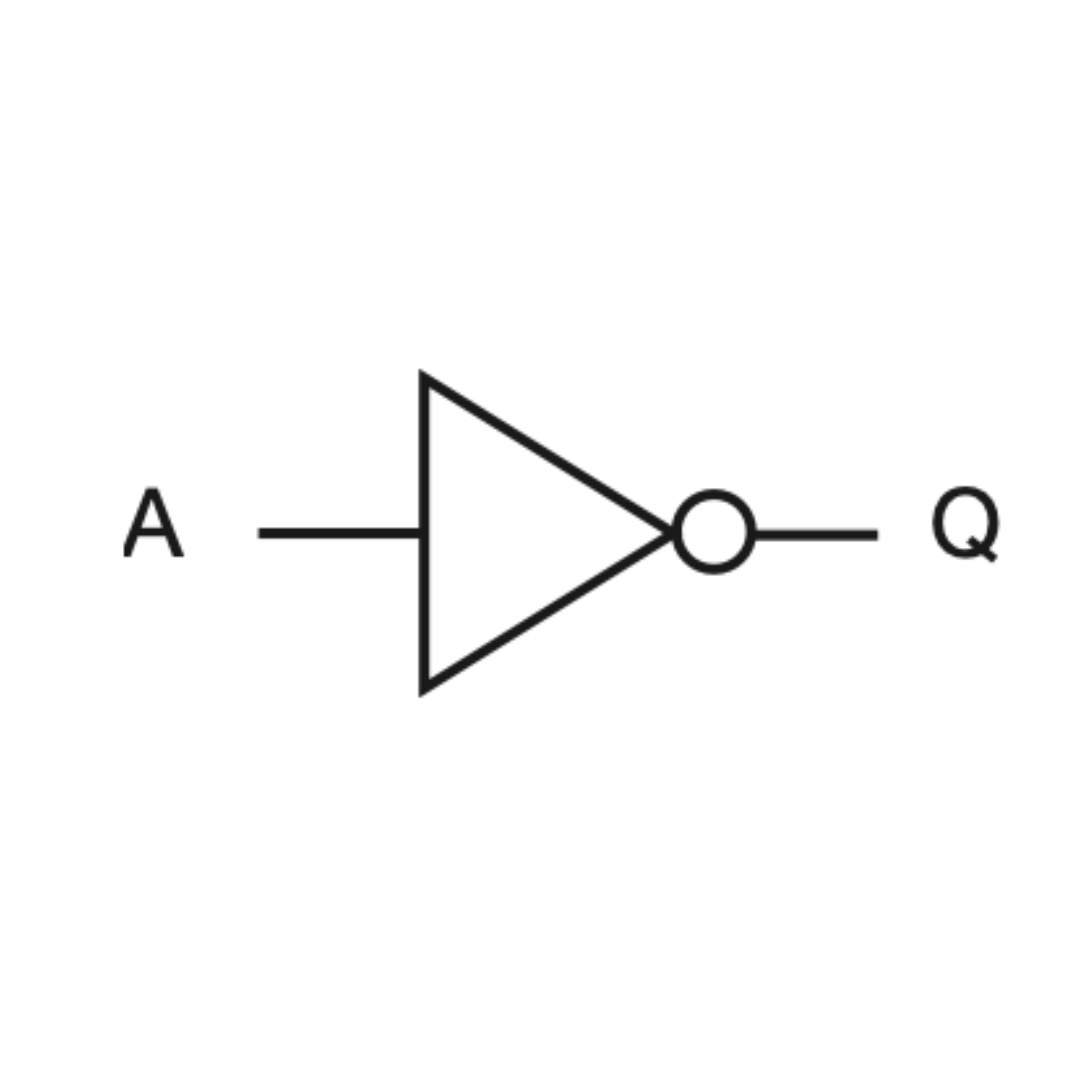
NOT gate
Inverts the input
95
New cards
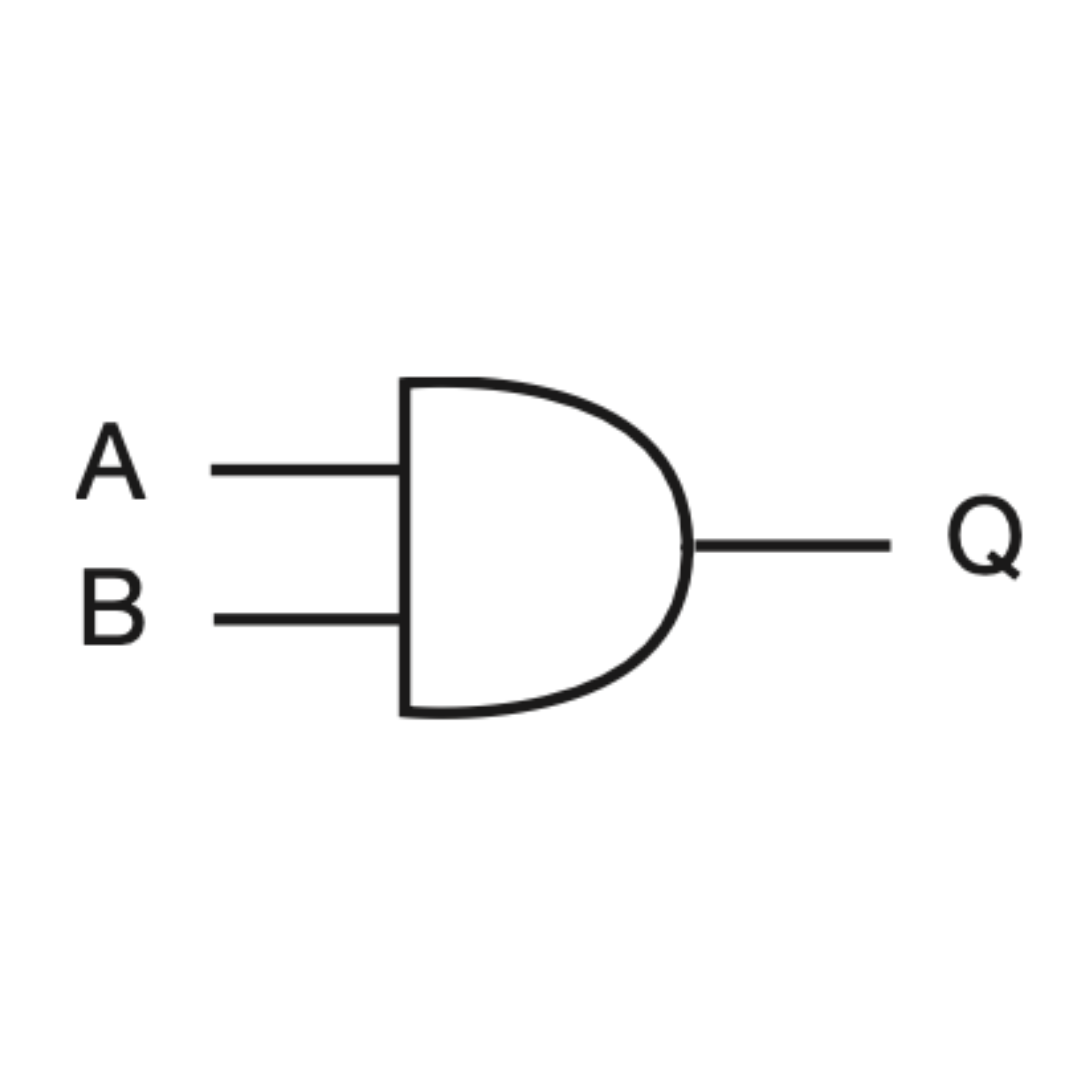
AND gate
The output is only 1 when both A and B are 1
96
New cards
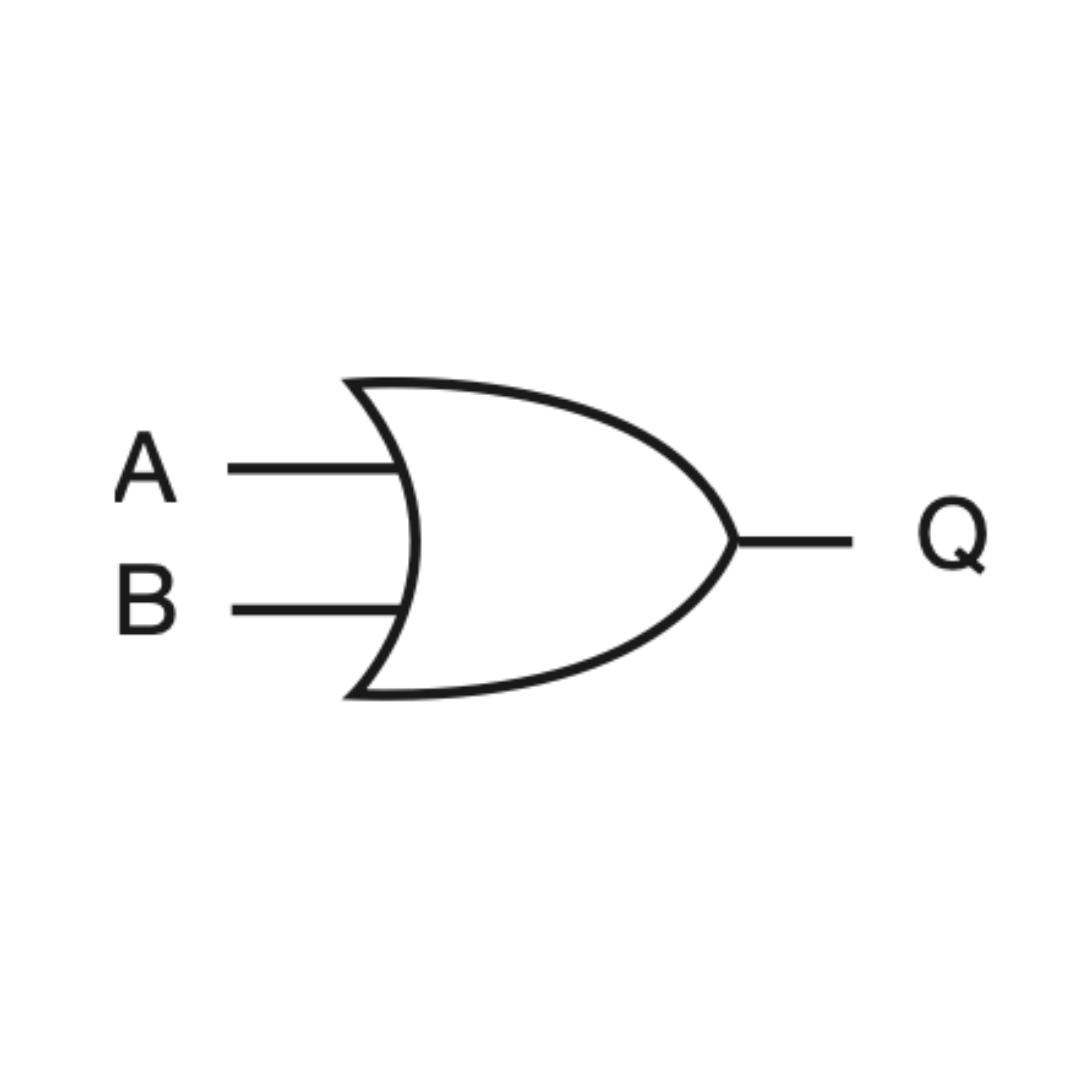
OR gate
The output is only 1 when either A, B, or both A and B are 1
97
New cards
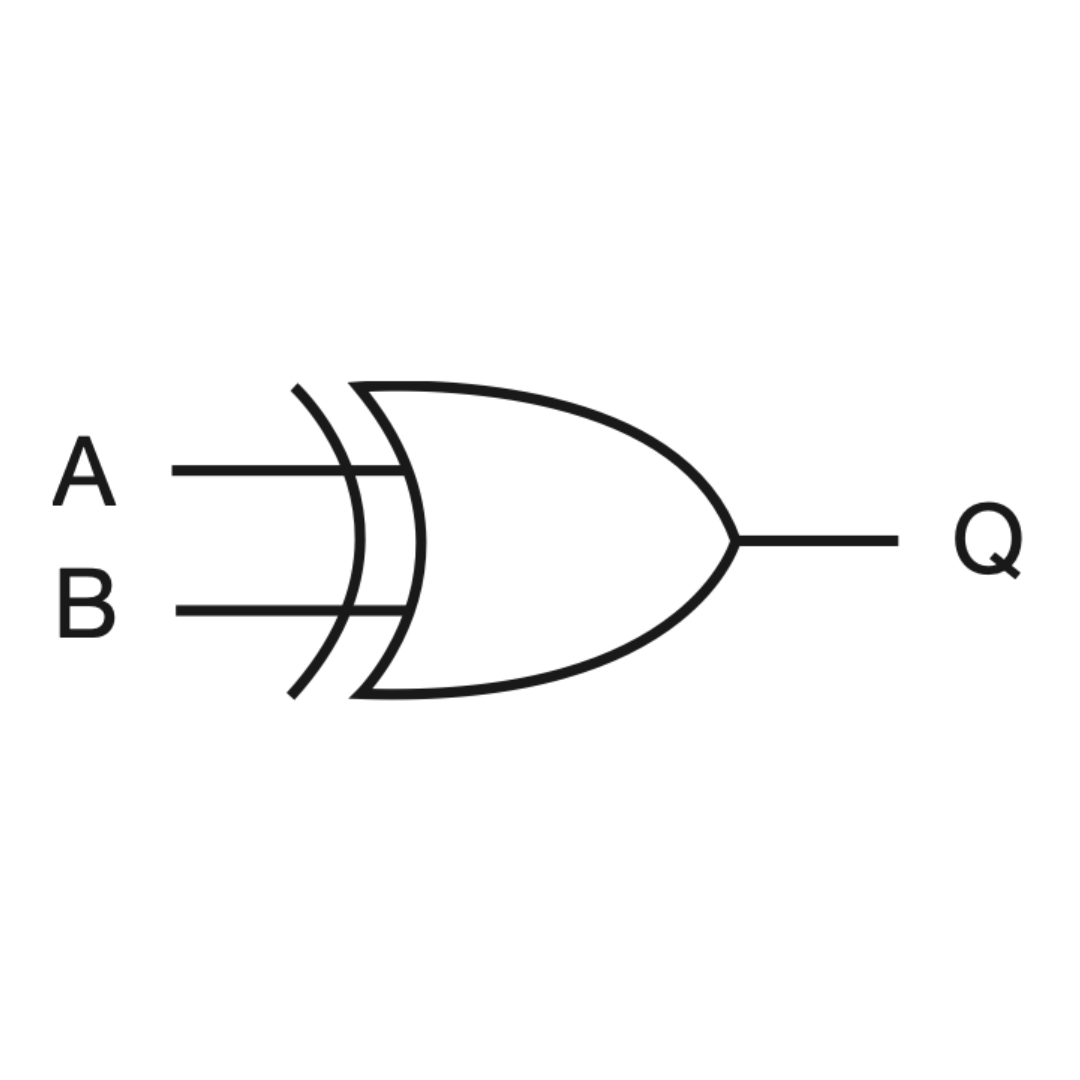
XOR
Exclusive or; the output will be true if one or other input is true, but not both
98
New cards
NAND
Inverts the output of the AND gate
99
New cards
NOR
Only produces an output of true when both inputs are false
100
New cards
De Morgan’s first law
NOT(A + B) = NOT(A) • NOT(B)