Previous exams - forensic
1/126
Earn XP
Description and Tags
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
127 Terms
Which of the following are part of the forensic process, and the correct order of it to be executed?
Identification, Collection, Examination, Analysis, Reporting
What is COC?
Chain of Custody
What best describes slackspace?
Slack space refers to the unused portion of a storage unit, such as a disk sector or cluster, that occurs when the space allocated for a file is larger than the actual size of the file. Slack space may contain remnants of deleted or overwritten files.
What is the fossilization of data?
Files that are deleted but still available on disk
Which of the following is not a UNIX file system?
NFTS
Given that you need data from all named data sources. In perspective of the principle of OOV, in which order should you collect data?
Main memory, HDD, Floppy, CD
How can we create digital fingerprints?
Cryptographic hash algorithms
In digital forensics, what is the purpose of hash signature analysis?
Identifying known good and known bad files
What is meant by dual-tool verification?
To verify analyzed results using two or more distinct forensic tools, to identify human and software errors
Which of these is a typical Active Method in Internet Investigations?
Portscan
Which is not a method for handling encrypted evidence`?
Known-bad hashsets
The CYBER CRIME CONVENTION addresses which of the following?
Copyright infringements , computerrelated hacking and testing, child pornography, and violation of network security
What evidence cannot generally be found on a smart- or cellphone?
Physical owner
Of the following, which is the most challenging with regards to mobile device forensics?
Vast amount of cell phone makes, models and operating systems
What is problematic with Solid State Drives with regards to digital forensics?
Garbage Collection making recovery of data hard
What does the ISO/IEC 17025 standard contain?
Forensics laboratories requirements
What does a digital retention specialist do?
Keeps track of chain-of-custody
What does the logical positivist believe?
That only that which can be empirically verified or induced/deduced from said is what can be known
What does the phrase “on a preponderance of evidence” mean for decisions of what is true?
Evidence is weighed and the more likely version of events is deemed true
What does the BGP protocol do?
Announces what networks are reachable from a router
What is the “blockchain”?
Is a protocol that allows all participants to agree on a version of history
What are fast flux domains
Obfuscation technique where the TTL of the DNS records is set extremely low, and the domain points to a large number of IP addresses that changes rapidly. This makes tracing difficult
Why are social networks important in internet forensics?
People often post personally relevant information on-line; like name, phone number etc. in the open
What is evidence dynamics?
How evidence change, disappear, is destroyed etc. regardless of ill intent
Which answer contains only file systems?
exFAT, FAT16, HFS, HFS+, EXT, NTFS
What are the attributes for Master File Table records?
$STANDARD_INFORMATION, $FILE_NAME and $DATA for files+directorties, while $INDEX is for directories only
Refer to the Master File Table timestamps, which one represents the “true” creation time for this file?
$FN Created. FN signifies data from the $FileName attribute, which requires root access to manipulate. $SI or $StandardInformation on the other hand can easily be manipulated without root access. The creation time given by the $FN attribute is therefore the most likely to be correct. Windows however use $SI values to set $FN values, when a file is moved within directories found on the same volume.
Why would you look at Handles in Windows?
To examine process’ functionality such as input/output files and registry keys
What is a digital signature?
A value created using a cryptographic hash function
Which type of hash functions are used to verify evidence integrity?
Cryptographic hash functions
How could evidence be excluded from a case (deemed not admissible)?
Not documenting vital elements of the chain of custody
What is the correct DLL load order?
Known DLLs
Directory where the application is loaded
%Systemroot%\system32
%Systemroot%\system
%Systemroot%
Current working directory
%PATH% variables
When are data protection rules applicable by law enforcement agencies?
When storing and using personal data
Which standards below relates to digital forensic investigation processes and digital forensic readiness?
ISO/IEC 27037
ISO/IEC 17025
NIST SP 800-86
What is a forensic image or forensic copy?
It is an exact image or copy (bit for bit) of a hard disk, taken using specialised hardware or software that do not write to the drive.
What is a Windows Prefetch file (2 points)?
Why is this a good artifact to look for (2 points)?
What are possible information registered in the Prefetch file? (4 points)
Prefetch files stores specific data about the application which one is trying to runs, in order to help them start faster. (2 points)
Can show that suspicious programs were launched (e.g. CCleaner) to cover up any potential evidence. Prefetch files may still exist on the system after a program has been deleted. (2 points)
Prefetch files uniquely identify running program with their executable name, together with a hash representing the path to the executable. Records last run time, number of times it has been executed and accessed files (read/write) within ten seconds of execution. The file creation timestamp is the first run time. (4 points)
Web browsers store a history of visited URLs. What interesting information can you find there, and how is it stored (assume you can peek into the cache as well)?
The web browser history contains all URLs you've typed, or links you've followed.
Most browsers store this in the form of a SQLite database, so it is easily parsable.
Often contains first and last access and how many times the URL has been visited.
If the URL contains e.g. post information that gets saved to; could contain a complete forum post.
Define and explain the Locard’s exchange principle (2 points)
The principle states, “When a person or object comes in contact with another person or object, a cross-transfer of materials occurs.”
Explain digital archaeology and digital geology, and their application in digital forensics (3 points).
Digital archaeology refers to digital traces in computer systems created by human behavior, whereas digital geology refers to digital traces created by the computer system. (2 points)
The goal of digital forensics is to gather facts about human behavior (archaeology), but it is a prerequisite to understand how computer system behave (geology) in order to interpret digital evidence. (1 point)
What is dual tool verification?
Why is this sometimes required (3 points)?
Digital forensics is typically conducted using third-party or purpose-made software.
Dual tool verification can be applied as a means to detect errors from one tool by using another tool to confirm the results
Important to consider using software from different vendors/developers to avoid common design/programming problems.
What is link analysis and how is it applied to digital forensics (2 points)?
The goal of link analysis is to produce a structured presentation of interconnected and linked objects.
To better understand the relationships and associations among objects. Usually visualized in graphs.
How can timelining of events be of any help during an investigation? (2 points)
It can give contextual awareness by creating a timeline of a chain of events (includes both physical and digital events).
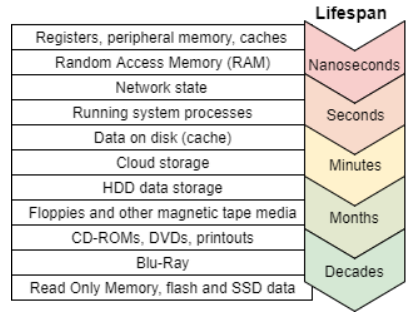
Briefly explain the concept of Order of Volatility. (3 points) Illustrate your explanation with a detailed sketch, inclining the ordering and naming. (5 points)
Prioritisation of the potential evidence sources to be collected according to the volatility of the data. Data have different lifetimes, so one should gather the most volatile data (which is more likely to change or destroyed) first. Data stored on disk is less volatile than data stored in memory
What are the stages of a digital forensic process and what do they entail? (15 points)
1. Identification – Identify what evidence there could be and where it probably is.
2. Collection – Collect the data identified before, e.g. by doing disk imaging of suspected computers.
3. Examination – Interpret the data collected, and making it representable as evidence in court. This is where we identify potential evidence. Often including recovery of deleted files, and interpreting them as a Word document.
4. Analysis – Determine what the evidence says about the case and how that supports relevant hypotheses, e.g by timelining, performing link analysis etc.
5. Reporting – Document what you've done, how it was done, who handled the evidence etc. and what findings the evidence supports.
What are the differences between a criminal investigator and an expert witness? (2 points)
A criminal investigator is a professional from a law enforcement agency which holds a formal position.
An expert witness is a third party that has been mandated by the professionals to analyze the evidence and testify in court.
What is the presumption of innocence and the burden of proof?
Anyone charged with a criminal offense has a right to be presumed innocent until proven guilty according to law.
The burden of proof is placed on the public prosecutor, and it is only fulfilled if the guilt has been proved beyond any reasonable doubt.
Explain the two terms repeatability and reproducibility when used during the acquisition phase. (2 Points)
An experiment is repeatable when it can be performed twice with in the same lab and with the same lab setup, and still give the same outcome/result.
A reproducible experiment can be done independently in another lab, with another lab setup, and give the same results.
Data acquisitions methods can be split into three main categories, explain what they are and how they differ from each other: manual, logical and physical acquisition
Physical acquisitions is done by removing the flash memory chip, putting it into a device for reading the chip, and then reading the raw data. No software used, meaning that it cannot be compromised.
Logical acquisition is to use the API for synchronizing the device contents with a PC. API can be compromised, which can result in only retrieving some “harmless” parts of the data. Also cannot retrieve deleted files since the OS only sees the logical data units.
Manual acquisition to use the user interface for acquiring data. Phone= looking through apps with touch screen, Computer = searching through the file explorer. Can compromise evidence integrity
Small devices are easier to accidentally or intentionally damage.
List and explain at least two ways a device can be damaged.
How do you minimize the risk of losing data?
1. External force: Physical damage might arise from accidents or attempts to destroy evidence. In case only the PCB is damaged, do chip-off and resolder it to a working PCB. Be aware that some PCB’s are identified with a digital ID. (2 points)
2. Water, liquids and blood: Water can cause damage. Water also cause oxidation of electrical conducting materials. Can also cause it to short-circuit. (2 points)
Add 1) Possibility to repair broken memory chip to get a good enough electrical connection (broken soldering pads) or to bond new threads (broken threads) to the dye. (2 points)
Add 2) Remove the battery or other electronic power sources. Make sure that the oxidation process proceeds as slowly as possible before cleaning the device, don’t add oxygen by pulling a submerged device out of the water. Clean the salt (if present from seawater or blood) off the device and clean with deionized water and alcohol before drying with silica bags. (4 points)
What are the three types of acquisition, referring to where evidence is located?
Local acquisition - Carried out on the endpoints involved in the incident (attacker and/or victim). Involves acquiring digital evidence directly from the physical device
Network acquisition - Carried out on the local networks which hold the IP address of the endpoints.
Remote acquisition - Carried out on systems or endpoints not directly connected to the incident. Involves acquiring digital evidence from a remote device or system without physically accessing the device.
What are the types of Internet artifacts you can collect from a local acquisition? Explain at least four different types of artifacts.
Local Acquisition is the process of collecting information directly from the involved endpoints.
The browser history stores typed or clicked URLs, first and last timestamps of access, and number of times accessed.
Browser cookies are used to remembering state between requests (like login information).
Email applications store when a mail was downloaded and information about sender and receivers.
Messaging and chats have information from logs, chat history and information about senders and receivers.
What are the types of Internet artifacts you can collect from a network acquisition? Explain at least two different types of artifacts.
Network Acquisition is carried out on the local network of the endpoints
Valuable artifacts may be found in network logs and captured traffic. Traffic can easily be capture with software like Wireshark.
DHCP logs are useful to identify which Media Access Control (MAC) address had a specific IP address at what time.
What are the types of Internet artefacts you can collect from a remote acquisition? Explain at least four different sources of artefacts.
This is an area where forensic investigators does not have physical control over, usually servers and web applications.
Web server logs store a lot of information about each request (HTTP/HTTPS) to the server. More specific examples are referrers, timestamps, agent, IP for client, and so forth. Web application logs from other applications running on the server (PHP, Python, Java, C#, etc).
Virtual hosts allow different web pages to be served by the same server, but they can configure log file locations.
Cloud services often need collaboration to retrieve information.
Open source intelligence is collecting open information available on the Internet through social media. Often includes information such as personal information, user accounts, contact lists, publication of content, interaction with content, public interaction and association with groups and communities.
When we have collected data from a computer (computer forensics) and go to examination we have two main areas of interest; disk structures and file systems.
What's LBA and how does it differ from what came before it?
Before LBA we had CHS – Cylinder, head, sector. Pointing to a data block required you to specify the correct values for cylinder, head and sector.
Cylinder = All the tracks with the same distance from the middle, Its like track 1 on all platters on the disk (top and bottom as well)
LBA or Logical block addressing rather gives each block a unique number. Which makes it a lot easier to reference data blocks on the disk.
When we have collected data from a computer (computer forensics) and go to examination we have two main areas of interest; disk structures and file systems.
What's an MBR and what has replace it (to a large extent)?
Master Boot Record – Developed by IBM in 1983. Contains boot code, disk signature, primary partition definitions (can only be four) that used to start at track 63, but now sector 2048 or 4096. Replaced by GPT – Guid Partition Table, uses GUIDs to reference partitions and uses 64-bit LBAs for storing sector numbers and contains CRC32 checksums to guard against corruption.
When we have collected data from a computer (computer forensics) and go to examination we have two main areas of interest; disk structures and file systems.
What's a volume and how does it differ from a partition?
A volume is a logical storage unit with a specific file system that can span one or more partitions. Volumes are what the operating system recognizes and interacts with, while partitions are the physical divisions on the storage device that can contain one or more volumes.
When we have collected data from a computer (computer forensics) and go to examination we have two main areas of interest; disk structures and file systems.
NTFS is the Microsoft filesystem that took over after FAT. List three advantages that it brought over FAT.
In the course we mentioned:
Added Access Control Lists (ACLs)
Scalability
Compression
Encryption
Journaling
Mobile and embedded forensics: When reading device memory through chip-off there are a couple of complications, list and explain two of them
Three major questions, is it potted/underfilled, how is it soldered, and is it temperature sensitive
Some devices are potted/underfilled with epoxy. The properties of epoxy make it difficult to perform a chip-off without damaging the chip (Heat resistant and strong bonding properties).
Modern dense form factors (TSOP and BGA) are very dense and can be tricky to desolder.
Some phones now have PCM – Phase Change Memory, that will drop all contents when heated. Makes desoldering difficult/impossible.
There are two major legal systems in the world, common law and civil law, what are the attributes of, and differences between them?
Common law – Not all the law has been explicitly designed/written by a governing body. A large portion of law is based on previous court decisions (legal precedence). Current court decisions are based on how similar cases has been ruled previously. Often related to Jury trials
Civil law - The law is the law that is written in the books. Less legal precedence, as in it does not define the law. Previous ruling do however help interpret the law. Only the highest courts can set precedent.
Differences:
Common law – You have to argue why something should be allowed to be admitted as evidence. Strict rules and case law about what evidence is, and how it must be collected, preserved, interpreted etc.
Civil Law – You have to argue why something should not be allowed to be admitted as evidence. The sitting court decides, on a case-by-case basis, what is allowed as evidence. Much fewer, and less strict rules of evidence
When performing an internet investigation and tracing (e.g. by trying to tie an IP-adress of a computer to that computer/user) there are many problems that can make that tracing impossible or very difficult. We mentioned at least four in the course, list and explain two of the possible problems. (2+2p)
Stepping stones – An attacker uses many computers in different jurisdictions, logging in on one, to log in on another, and a third etc. makes tracing take time and involve many different jurisdictions.
Anonymisation networks and tunneling – ToR and other techniques actively hide the sender of the traffic (it’s their sole purpose), and make direct tracing (almost) impossible.
Network architechture - NAT/VPN etc. hides many different sending addresses behind a single address making identification of the actual sender difficult.
Registration issues – WHOIS information etc. can be wrong or misleading, even on purpose, which makes finding contacts etc. difficult.
Explain the concept of link analysis and when it can come in handy in an investigation of digital crime. What can it help to prove in a case? (3p)
Link analysis is the process of identifying links between persons, computers, phones, addresses, emails, i.e. any kind of digital and other evidence that can be linked in time, place, communication etc. This can for example be used to find the source of a virus infection, identify a leader of a criminal enterprise (through communication patterns) etc
What’s an MBR? Where would you typically come across it? What does it contain? (3p)
Stands for Master Boot Record and is a partition table that stores information about the different partitions on the disk.
Usually found at the very beginning of a storage device. Most likely a PC-based system with a Microsoft related file system (or several) on it.
It contains information about where partitions start and how large they are, in addition to boot code and primary partition definitions. MBR has since then been mostly replaced by GPT (GUID Partition Table) because of its limitation related to only being able to have 4 primary partitions
What is netcat, and when can it come in handy during a forensics investigation? (2p)
Netcat (nc) is a network tool that can be used to easily sink (or source) network traffic on a server or other investigation workstation. It can be used in live system forensics, e.g. to quickly copy an image of a live system to an investigation server/workstation, or in network forensics to store network streams etc.
If during an investigation involving the “phone company” you come across a “CDR” what is that, and what sort of information would you expect to get out of it? (You would often get several of them as they’re often not that singularly useful. Though of course they can be). (3p)
Call Detail Record. They are the database records “phone companies” and their equipment store with information about single calls made (or other billed transactions, such as some mobile internet usage etc.).
In it you would find metadata about the call, who made it, to whom, when, how long it lasted, whether it was incoming or outgoing, what cell towers (if any) were involved, etc. It can be used to establish communication patterns between suspects and other entities in a case, but will not contain any information about what was actually said, or transferred.
Locard’s exchange principle what is it? What are it’s consequences? How can it be applied to digital forensics? (3p)
With every contact there is an exchange, i.e. every contact leaves a trace. When a perpetrator has been at a crime scene, there are traces of the perpetrator at the crime scene, and traces of the crime scene on a perpetrator.
While it is very useful in physical forensics, it is not as generally useful in digital forensics, but there are some cases where it could be argued it is used, such as the list of WiFi networks that a mobile phone has seen being found on the phone, or routing information listing which cell towers had contact with a phone at a certain time. In the first case the scene leaves traces on the phone, and in the other, the phone leaves traces on the “scene”.
There are many problems with forensics that “forensic readiness” in a company/organization tries to address. Name and explain three such typical problems
Unprepared organisations do things that destroy the value of the evidence:
IT-support “fixes” the problem before it can be investigated
Evidence is handled poorly:
Chain of custody not maintained
Only the “interesting” evidence is collected, so exonerate evidence is not saved (evidence which can liberate the suspect
evidence integrity is compromised (disks are mounted with R/W permissions instead of read-only etc.)
Cost - Directly with forensic activity, and indirectly by disrupting business operations
Two of the roles in a digital forensics team could be “first responder” and “digital retention specialist”. What are the respective responsibilities of these roles? (Especially; when in the investigation are they active, why is there a need for their specialities?) How and when do these roles interact during the investigation? (We’re assuming an idealized world here, where these roles are distinct with no overlap between persons and roles. In a real world setting many of these roles will often overlap and the responsibility will be somewhat diluted between all members of the team). (3+3p)
First responder – Is the first person on site at the first sign of trouble. Is a “CSI”, i.e. a “Crime Scene” Investigator. Knows how to identify potential evidence, and how to collect, document and preserve it. Needed so that the evidentiary value of the evidence isn’t destroyed before it has even been collected, and so that all relevant evidence is collected.
Digital retention specialist – Is the “librarian”, i.e. the person who keeps track of all different pieces of evidence, lists, collates and catalogues it. Keeps track of the chain-of-custody. Needed since there are many cases active at the same time, and we must be able to prove which piece of evidence is part of which investigation, and that no cross contamination or mixup has taken place.
There are many problems in practice when it comes to timestamps. Explain in some detail what the following problems are, how they effect the quality of the evidence, and what you can do to try and work around them:
Accuracy and drift (2p)
Different clocks in different systems have different level of accuracy. Some are synchronized to e.g. GPS and keep time to the micro second, stable over time. Other, such as clocks in built in systems, keep time to the minute and are never synchronized, so can lose/gain a minute or two per month. Correlating timestamps from many different systems like this can be very challenging. This is the reason why you should always log the difference between the device’s internal clock and a known clock.
There are many problems in practice when it comes to timestamps. Explain in some detail what the following problems are, how they effect the quality of the evidence, and what you can do to try and work around them:
Time zones (2p)
Some systems store time according to the local time zone, while others store e.g. according to GMT and take the time zone into account only when presenting time to the user. Time zones also change time (daylight savings time) at different times during the year. Often in large investigations there will be computers/systems in different time zones, which is challenging for correlation as not only time, but also the time zone must be taken into account when performing correlation or time line analysis.
There are many problems in practice when it comes to timestamps. Explain in some detail what the following problems are, how they effect the quality of the evidence, and what you can do to try and work around them:
Tool interpretation/rounding errors
Some tools interpret time according to e.g. the current time zone, even though that might not be correct, they can also round time stamps so that different time stamps all end up with the “same” time, making it look in the tool as something that happened after something else, happened at the same time, or even (due to sorting problems) before the event that caused it.
Deductive vs Inductive reasoning
In summary, deductive reasoning starts with general principles to reach specific conclusions with certainty, while inductive reasoning starts with specific observations to make generalizations, which are not guaranteed to be true
What are the two kinds of imaging one can perform on a disk? What is the difference?
Physical images copies all the bytes on the target device such that an identical physical copy is obtained.
Logical images copy all the files visible for the file system.
Physical images enable investigators to recover deleted files and inspect slack data. Essentially, physical images allow investigators to examine data not visible to the file system.
Name examples of important information that may be found in volatile memory.
Information related to malicious processes running on the computer.
Decryption keys (for disks and other things)
Name some of the most important tools for computer forensics.
FTK Imager is a widely used tool capable of imaging without chaniging the original content. It also provides tools for examination, analysis, and documentation. It works for most operating systems.
Redline allows the capture of volatile memory as well as inspection of file system, event logs, and a threat assessment profiling tool.
What are the two different types of partitions?
Primary partitions are sections of a disk within which an operating system can be stored. Upon boot, a single primary partition will be marked as active. Only the active partition may be accessed during boot. Each primary partition is assigned its own file system.
Extended partitions are used for logical drives, i.e., the partition of an area of the disk. This is handled by the OS so there is no need for a separate file system.
What are partition tables?
A partition table is a method for logically partitioning a disk into different partitions. The OS uses a partition table when accessing disk. An example of a partitioned physical disk is one partitioned into two logical ones, e.g., C and D
What are tracks, sectors, and clusters on a platter?
Tracks are circles of a given diameter on the platter.
A sector is a portion of a track (the tracks with greater diameters will have more sectors). Sectors are the smallest addressable units on an HDD and typically consists of 512-4,096 bytes.
To ensure efficient read and write times, HDDs tries to store data contiguously (avoid fragmenting files over different parts of the disk). As files tend to be much larger than a couple hundred bytes, there is usually a need for more than one sector. The solution employed in most file-systems is to assign a collection of sectors to any file, regardless of size. Such a collection is known as a cluster, and typically contains 8 sectors.
What is a write blocker?
Write blockers are specialized pieces or hardware that enable the copying of one disk’s content over to another. The key advantage with such devices is that they carry out such copying procedures without writing to the disk being copied. Therefore, evidence integrity is maintained.
What are the two key components of an HDD?
The two main components of any HDD are the heads and platters. A head is much like an arm capable of reaching to different points/radii on the platter. Heads can both read from and write data to a platter. For every platter there are two heads so that each side of the platter may be utilized. An HDD tends to consist of several rows of platters.
How can broadband cellular network technologies such as 4G be used to track the position of mobile phones?
Base stations often have several sectors with directional antennas.
By checking the base station that the mobile is connected to, we can get a rough direction and max distance.
It is also possible to triangulate the position of the mobile when the mobile phone is seen by several base stations. Keep in mind that phones are not necessarily connected to the base station that is closest or has the best signal strength.
Also, phones have a identity besides SIM that can still be tracked if someone changes the SIM card. This identity is called IMEI
What is a first responder
The first responder is the first investigator to get to the scene of the event. The main tasks of the first responder is to control the environment and start utilizing standard operating procedures (SOPs) for structured evidence identification activities. One example of such an activity is to perform documentation to maintain chain of custody and evidence integrity. Forensic readiness is essential for ensuring proper first responder conduct.
What are the 5WH questions and why are they helpful for investigators looking to construct a hypothesis?
The 5WH are:
Who committed the crime?
Why was the crime committed?
What was the committed crime?
Where may potential collaborators be?
When was the crime committed?
How was the crime committed?
These simple question lets the investigators examine important aspects such as motives, likely suspects, and potential sources of evidence, which will aid in the formulation of an early stage hypothesis.
--
What are the key objectives for the identification phase?
The essentials of the identification phase is to get to understand the incident, build a hypothesis, and identify potential evidence. In short, the purpose of the identification phase is to lay the foundation for the remainder of the investigation.
What are the key objectives and challenges for the collection phase?
The collection phase is concerned with gathering data from devices that may be valuable as evidence. Making copies of main memory and disks (images) is usually how data is collected. When retrieving data from the devices, it is essential that the collection is carried out in a manner which does not alter the original data itself (evidence integrity). Some essential steps may require the investigators to affect the system in small ways (especially applicable for main memory). If so, all actions performed on the data must be thoroughly documented (chain of custody).
What are the key objectives and challenges for the examination phase?
In its essence, the examination phase consists of making sense of the raw data extracted in the collection phase. Key techniques are parsing, reconstructing deleted files, and preprocessing of the raw data. To facilitate this phase, analysts usually employ several tools to extract the relevant information. The most important challenge in the examination phase is the amount of data collected and in need of examination. Investigators typically work on a packed schedule and cannot closely inspect all data collected. Consequently, they must prioritize.
What is typically the first step in filtering out files irrelevant to the investigation?
The filtering of irrelevant files from raw data (when inspecting a disk image) can be accomplished with the aid of databases containing cryptographic hash values for known files. his allows investigators to ignore OS and application files of little importance
What are the key objectives and challenges for the analysis phase?
During the analysis, investigators inspect the material extracted to determine what to use as digital evidence for proving or refuting the hypothesis. Timelining and link analysis is often used in this phase.
The analysis phase is further said to be iterative. As the hypothesis tends to be quite crude after the identification phase, it is often altered when more information obtained. The newly formed hypothesis may require more/different evidence. Thus, the collection, examination, and analysis phase may repeat itself several times over during an investigation.
What are the key objectives and challenges for the presentation phase?
The final phase in the digital forensics process is the presentation of the findings and conclusion from the conducted investigation. All findings must be summarized while all steps in the investigation must be accounted for and explained in a manner understandable for the target audience. The presentation of the results must be carried out in a proper manner since this is what will inform the audience about your findings. With improper documentation we might find that the message is not properly carried across, thereby making the entire investigation obsolete
What is a coercive investigation method?
An investigation method is coercive when it lawfully can be applied against an individual without her consent or cooperation, despite that her right to personal liberty, property, or private life is interfered with.
Explain how does cross-jurisdiction affect the work of the police when it comes to the investigation of crimes with data stored in the Cloud?
Cloud computing often means that data is distributed over different providers, locations and often jurisdictions. Therefore, investigators have reduced visibility and control over the forensic artifacts. A state cannot exercise its jurisdiction outside its territory, unless an international treaty or other laws permit to do so.
Why can it be challenging to collect data from mobile phones and embedded system?
Unlike ordinary PCs, these devices have no well defined and standardized interfaces
Other challenges include:
- the device’s security measures. The protection in mobile phone OSes is more complex than normal Unix. Each process in mobiles runs in its own sandbox, as its own user without root.
- finding out which components are relevant.
- Electrostatic discharge (ESD).
- Physical state: broken, state of device, battery, etc.
- Finding other traces such as finger prints
How can data be collected from mobile devices?
We could:
use an application or service on the platform itself. e.g. use phone itself to check recently dialled numbers.
Connect the device to a computer and read its file system.
read through the OS, especially if the device is rooted
use JTAG to read through the flash controller
try to get at the flash subsystem itself
desolder the flash chips and read them directly
grind the physical chips down and look at them with an electron microscope
What is JTAG and what is it used for?
JTAG is short for Joint Test Action Group and is a standardized interface for boundary scan test.
- Boundary scan is a way to test if a trace connects two points
It can be used for finding defects in integrated circuits and to debug firmware or software running on CPU or micro controllers. The debugging part is particularly interesting because it enables us to run flash memory as if we were the CPU.
What is Flash memory?
Flash memory is a very common storage medium for phones and embedded systems.
There are two types of flash memory:
- NAND, where we can only change ‘1’ to ‘0’
- NOR, where we can only change ‘0’ to ‘1’
If we want to change bits the other way, we have to erase the entire block
A problem with flash memory is that erasing and writing blocks wears down the hardware. With NAND, we can typically only write and erase 100 000 times. To prevent wearing down the hardware, there are some mechanisms that involve reallocation and copying. These mechanisms can leave left overs in previously changed blocks. It can be hard for investigators to know which data is live and what is left over crap.
Examples of flash file systems are YAAFS1 and YAAFS2.
What is considered the main future challenge for digital forensics?
The huge amount unstructured data investigators must look through is already the main hurdle for investigators. This issue is likely to grow in severity as more and more devices and applications become interconnected. The amount of unstructured data is a challenge for all phases in digital forensics investigations
What are the common techniques used for collecting information in internet forensics?
There are two main approaches.
Tracing is concerned with collecting data about the endpoints themselves
Acquisition which are the efforts to collect information from the endpoints.
How may tracing be carried out?
Tracing include all efforts to learn something useful about a host. Useful tools include default UNIX binaries like ping and whois which allow you to perform a routine health check on the device, or get detailed information on the individual/organization or local network attached to the provided network.
Traceroute allows investigators to ping a given host while also getting detailed information on the path the request took through the web (useful for getting a rough outline of the geolocation of the endpoint).
Finally, Nmap is a port scanning tool which enables investigators to see what ports are open on the host. The information gathered through tracing is often useful when acquisition is to carried out later on.
How should a first responder go about collecting data?
It is crucial that the investigator adheres to standards and procedures. In addition, it is almost always recommended that the first responder uses some well established tool when collecting data.
There are two major reasons for this. Firstly, such tools are tried and tested, and will therefore manage to collect the data without tampering with it. Thereby ensuring evidence integrity. Secondly, such tools provide valuable automatically generated signatures (hashes), and documentation of the actions performed on the data, which is critical for chain of custody.
Examples of tools offering such capabilities are Redline and FTK Imager for disks, and SANS SIFT for imaging main memory.
What is a file system?
A file system is an abstraction used for storing data into distinct entities called files. The file system itself stores the content of the files along with metadata. File systems resides in what is known as a volume. A volume can exist on one or more disks. Examples of well known file systems are NTFS in Windows and ext2 in Linux.
What is stored in the $MFT?
A
The master file table serves as a database that keeps track of information about all files and directories on a disk. The file is structured into MFT records containing metadata for files and dictionaries. Each object on the system has at least one entry in $MFT.
There are several fields in an entry, with the first being the entry header which stores information such as the MFT record number, header sequence, whether the object is a file or dir, and its status (active or deleted).
The $STD_INFO attribute contains the MACE timestamps which reveal when the entry was last modified, accessed, when the entry was itself was modified, and when the entry was created. $STD_INFO also contain ID numbers for security, app usage, and flags.
In addition, every MFT entry has a $FILE_NAME stores the name of the object, the parent directory record number, the object size, and the MACE timestamps for the object itself.
Depending on the type of object, there are two additional attributes, $DATA for files and $INDEX for directories.
The $DATA attribute contains the actual data/contents of a file. If a file is too large to fit in the $MFT record, then it must be put into something called an extent, and the MFT record will include a pointer to this extent instead. In these situations, the $DATA attribute are non-resident, meaning that its not present in the MFT record.
The $INDEX attribute contains the attributes for the files and subdirectories of the directory. This means that another set of MACE timestamps can be found here.
Lastly, $FILE_NAME, $STD_INFO and $INDEX is required to be resident.