Threat and Risk Modelling
1/64
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
65 Terms
Enables defenders to analyse attacker profile (goals), attack vectors (steps they follow), and the assets desired by the attacker.
Identify high-value assets.
Identify vulnerabilities.
Identify most relevant threats (e.g. finance industry, healthcare).
Identify any attack vectors that could go unnoticed (e.g. supply chain attack) / indirect attacks
Impossible for a single expert to exist, so roles are broken up.
Red team: trying to break a system, but they still work for the organisation.
Blue team: defending the system against the red team and mitigating problems.
Specialised security experts for different domains (e.g. physical infrastructure, human security, building architecture, network experts).
What are you building or analysing — network, system, application architecture
What can go wrong — identify threats (e.g. DDoS).
What can be done about it — risk analysis (quantitative + qualitative), countermeasures, controls.
Threat modelling needs to occur first to identify the threats and assets.
Prioritisation is required from most to least important asset-threat.
Once prioritised, the full risk register can be developed.
Model the system being attacked.
Model the attacker.
Model the threats and attack vectors.
network diagram,
data flow diagram (context level),
software diagram of architecture or code
Persona-non-Grata (PnG).
STRIDE model.
MITRE ATT&CK and mapping to the attack vectors.
Attack Trees.
Choose one based on the system type, approach, and context.
Threat models can also be combined for better coverage.
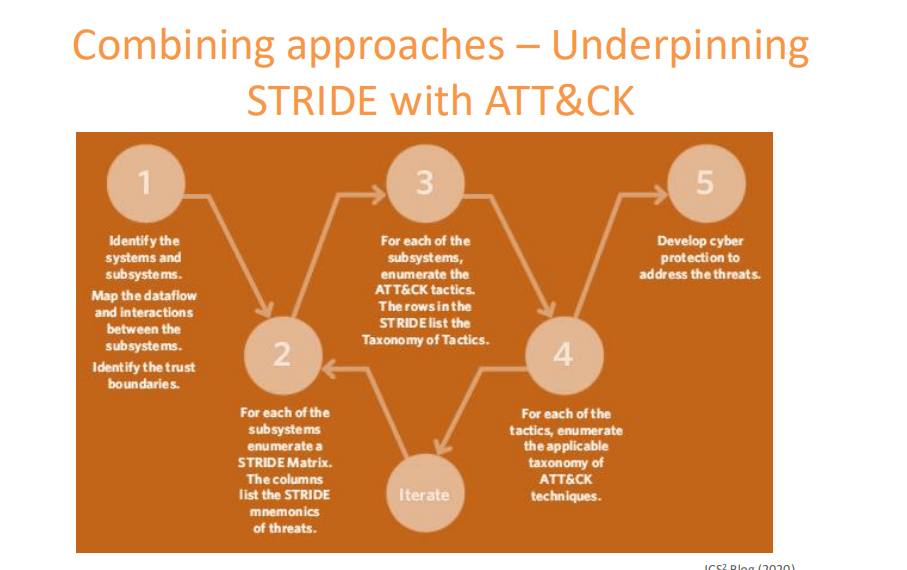
Produce a visual representation of the current situation of the organisation (e.g. network diagram).
Review intelligence that may highlight threats to the network diagram.
Identify possible techniques (e.g. via MITRE ATT&CK matrix).
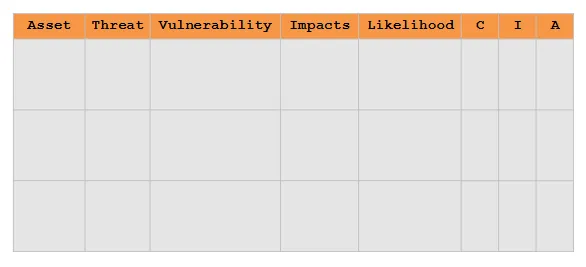
Carry out risk analysis using CIA Triad and create a Risk Register with mitgations.
Select controls (e.g. from MITRE ATT&CK, SANS) to minimise impact and ensure business continuity.
STIX.
MISP.
How to apply controls or countermeasures that address the vulnerabilities or mitigate the effects of the threat.
Understanding the impact of the threat and whether it is severe enough to call for further security measures.
External threats.
Internal threats.
Structured threats.
Unstructured threats.
hackers - programming experts
phisher - email attempt to fish for / trick users to give sensitive information
white hat - find and report vulnerabilities to owners
black hat - find and break systems in an unauthorised method
System admins.
Employees.
Archetypes of possible attackers—represents an aggregate of target users (attackers) who share common behavioural characteristics and skills, a dummy persona with
name
attributes/skills
goals
misuse activities from the system perspective

Put controls specifically against these archetypes.
Used when mapping social engineering threats.
Employee data.
Databases and threat intelligence reports.
News on emerging threat types.
What is the STRIDE model
Threat modelling approach comprising of 6 key threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege.
Relies on staff expertise and accurate data flow diagrams—errors lead to inaccurate modelling.
Requires more training effort.
A rogue person or program impersonating another legitimate user or program.
Affects integrity.
Illegitimate modification of application resources, such as in-memory data.
Affects integrity.
A user denying execution of an action within the system.
Affects integrity.
Access to private information by an unauthorised agent.
Affects confidentiality.
Making a system resource unavailable to intended users.
Affects availability.
Gaining privileged access to protected resources.
Affects confidentiality.
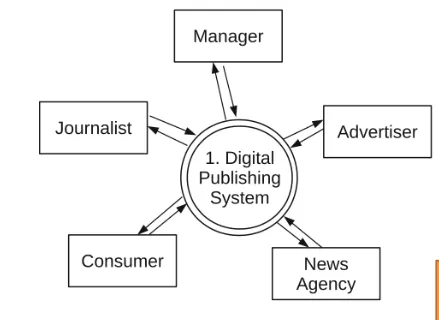
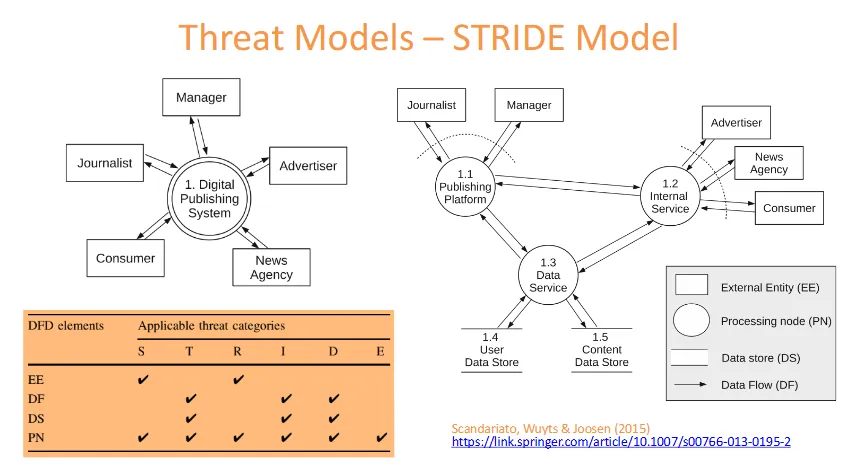
Identify and visualise the system (e.g. Digital Publishing System).
Assess (DFD) elements or directly list assets (e.g. server, WiFi point).
Fill STRIDE table with a column for each STRIDE point and a row for each element and tick the risks.
Assumptions must be written and justified.
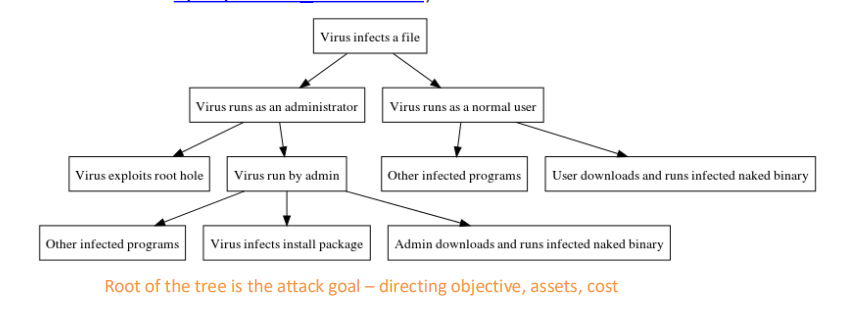
what are attack trees
oldest and most widely used threat model technique - visual representation of how an attacker might comprise a system or asset
how are attack trees structured
what are the pros of attack trees
easy to understand
what are the cons of attack trees
relies on expertise of staff
more effort required to train the staff on the hardware and software of system
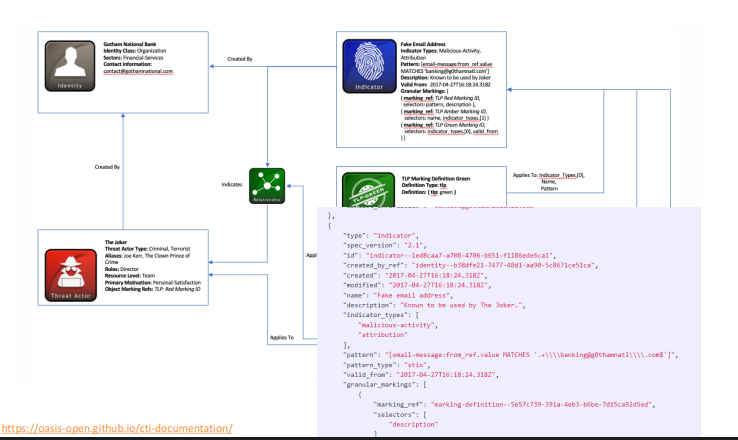
Structured Threat Information Expression
a language and JSON-based format to exchange cyber threat intelligence, used with the TAXII protocol.
Visual models of threats can be generated from the STIX JSON file.
‘object’ = [] - contains list of all mappable objects JSONs, including a separate value for the relationship
https://oasis-open.github.io/cti-documentation/examples/identifying-a-threat-actor-profile
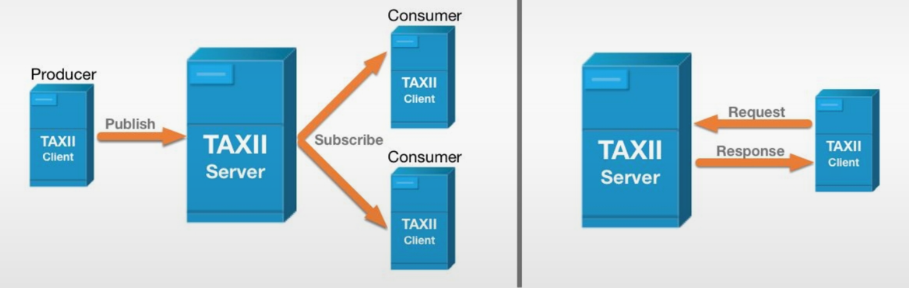
Trusted Automated eXchange of Intelligence Information
an application protocol for exchanging CTI over the web (HTTPS).
Organisations publish new threats to a TAXII server.
Other organisations subscribe to the server to receive the STIX file.
Accessible via API or compatible software.
what is MISP
malware information sharing platform
powerful open source threat intelligence platform organisations can use to store, share and receive information about malware, threats, and vulnerabilities in a structured way.
how does MISP work
MISP organizes threat data into Events with Attributes (e.g., IPs, URLs), enriched by Tags, Galaxies (like MITRE ATT&CK), and Objects. Data is ingested manually or via automation (APIs, parsers), shared securely across platforms, and integrates with security tools via APIs and scripts (e.g., PyMISP).
what are computational simulations in risk modelling
turn our threat and risk models into computational models, transferring our knowledge about the threat and risk into an active simulation that can be observed
what is an approach of Computational Simulation
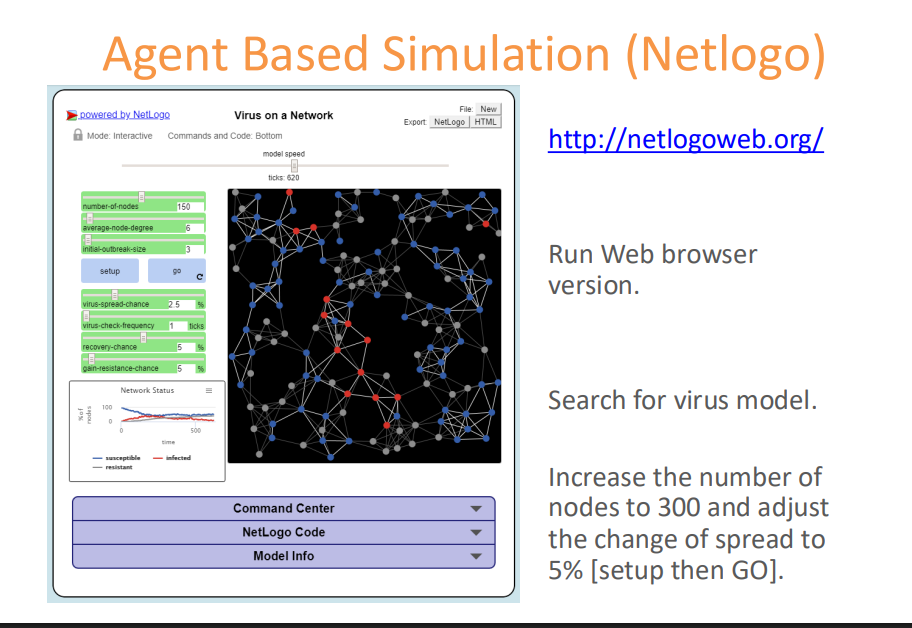
Agent Based Simulation (ABS)
Agents
environments
behaviour
baselining.
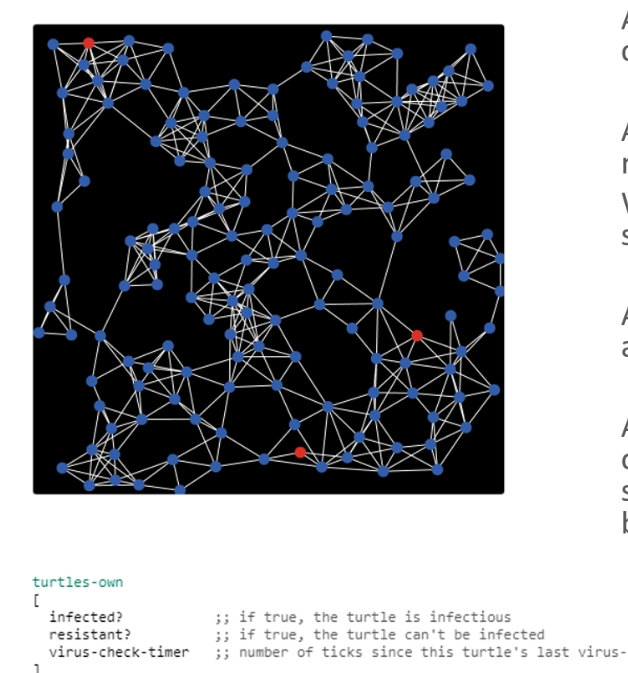
Multiple interacting agents form a system with emergent properties; agents act based on if-else rules, and their properties and actions can be defined and changed.
e.g. agents might cluster together in some way or multiply in some way
e.g. should delete files when agent enters the system
Specific attacks (e.g. virus, malware)
attackers and defenders
phishing emails
hardware and software elements.
Geography
networks
buildings
office layouts.
Dynamic actions of agents based on changing network conditions, e.g. rules for infection spread.
different agent rules (either simple or complex) result in different system behaviour
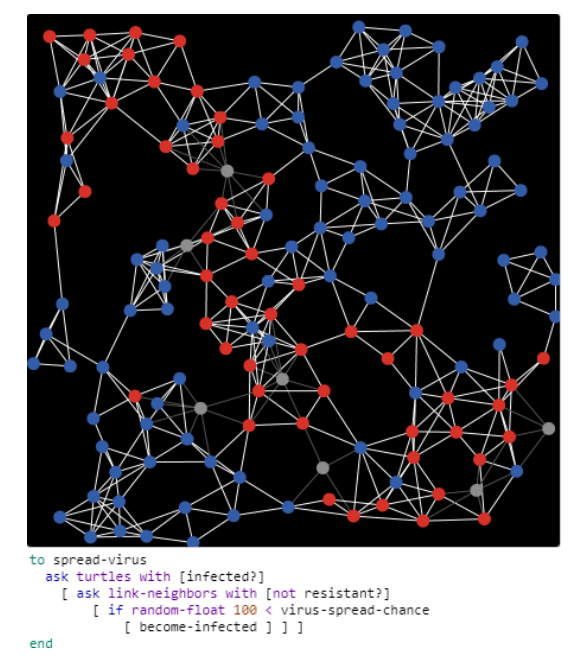
To test hypotheses e.g. the effectiveness of a control or tool in reducing of solving the issue
compare against simulated scenarios for effectiveness evaluation, e.g. compare the baseline of the simulated network infection to the actual spread
with software like Netlogo which runs in the web browser
in code with python