Professor Messor 4.1 | Defense in Depth & Authentication Methods
1/18
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
19 Terms
Layering the defense
Involves implementing multiple security techniques to protect your systems, recognizing that no single measure is foolproof. By combining various layers of controls, you create a more resilient defense strategy.
Physical controls: These prevent unauthorized physical access to technology, using methods like door locks, fences, rack locks, and surveillance cameras.
Technical controls: These use hardware and software to enforce security, such as firewalls, Active Directory authentication, and disk encryption.
Administrative controls: These encompass policies and procedures that govern security practices, including onboarding/offboarding processes and backup media handling.
By integrating these layers, you strengthen your overall security posture.
Defense in depth
By using a combination of defenses, you cover a broad range of potential vulnerabilities.
Firewall
Screened subnet (DMZ)
Hashing and salting passwords:
Authentication:
Intrusion prevention system (IPS):
VPN access:
Card/badge access:
Anti-virus and anti-malware software:
Security guard:
Each of these controls addresses different aspects of security, and they work together without replacing one another
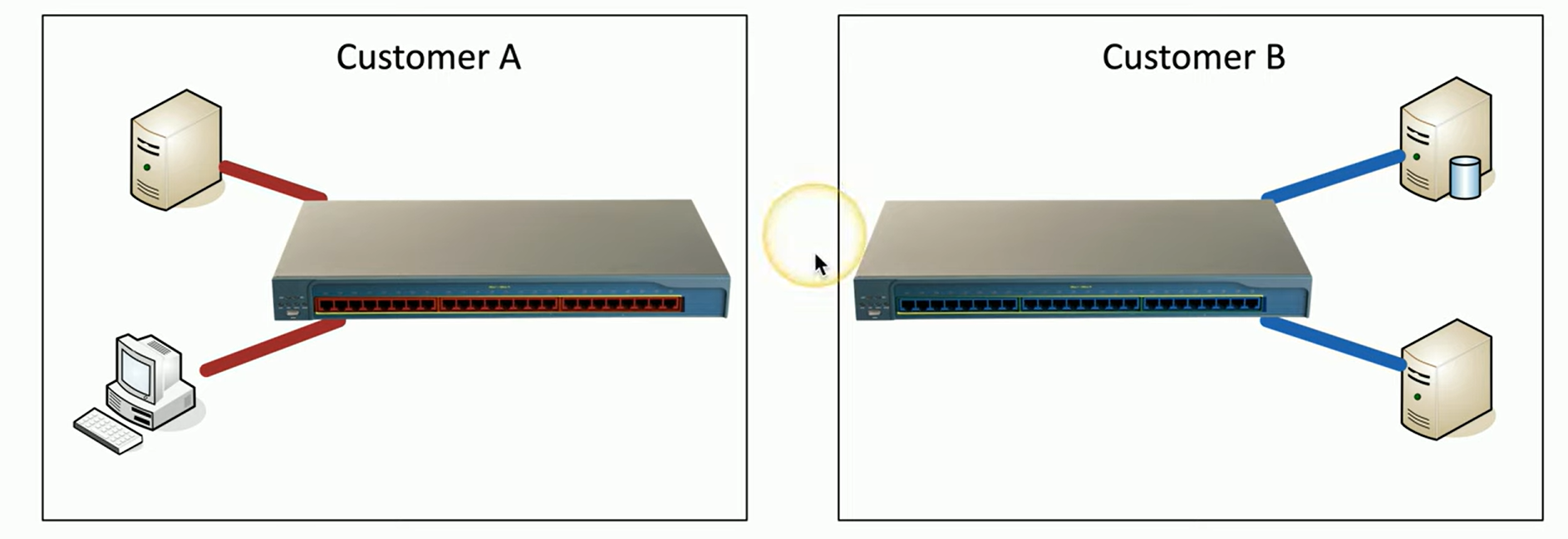
Physical segmentation
Involves separating network devices and infrastructure to create distinct, isolated environments. Each segment runs on its own physical network.
For example, Customer A’s devices are connected to one switch, while Customer B’s devices connect to a different switch. Because these switches are physically independent, there’s no way for Customer A to access Customer B’s resources, and vice versa.
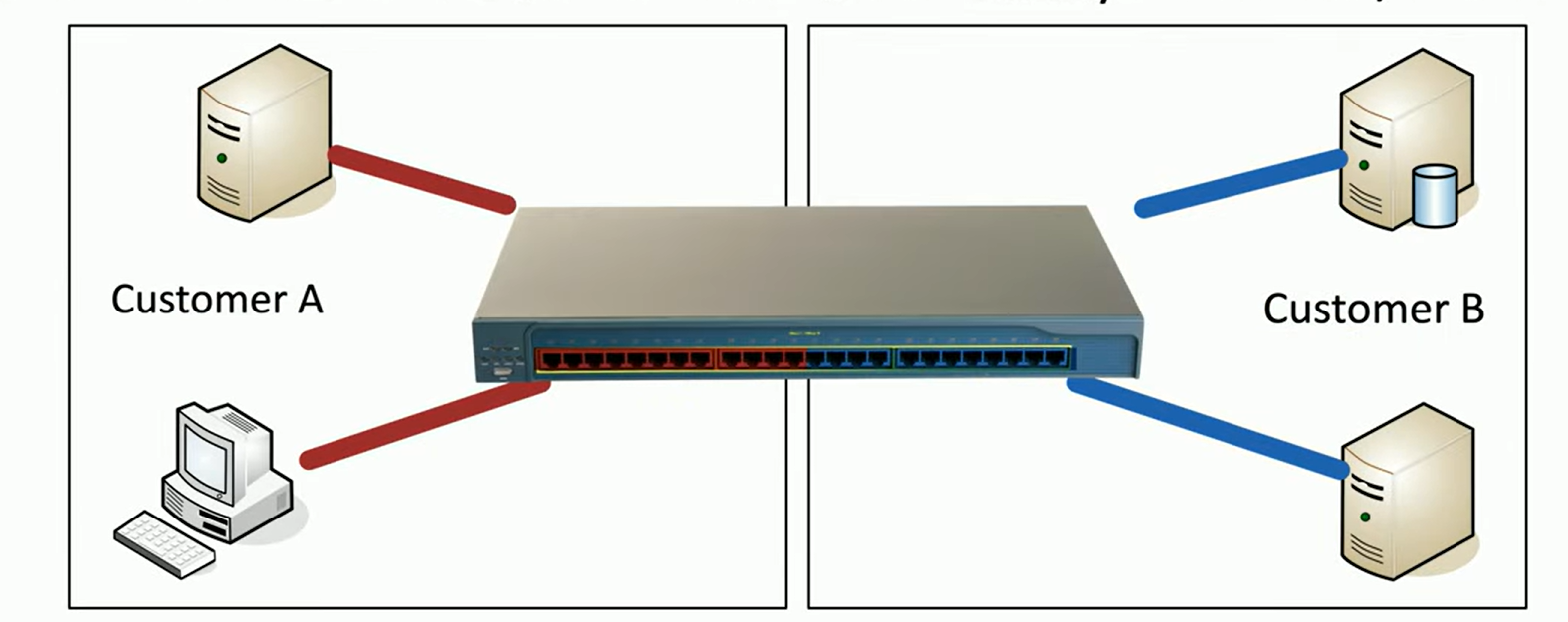
Logical segmentation with VLANs
Involves using Virtual Local Area Networks (VLANs) to separate traffic on a network. Unlike physical segmentation, where devices are isolated using distinct hardware, VLANs create separation through software configurations on the same physical hardware.
On a switch, you could have one VLAN dedicated to Customer A and another VLAN dedicated to Customer B. Although these VLANs exist on the same physical switch, they are logically separated, and their traffic remains isolated unless explicitly routed.
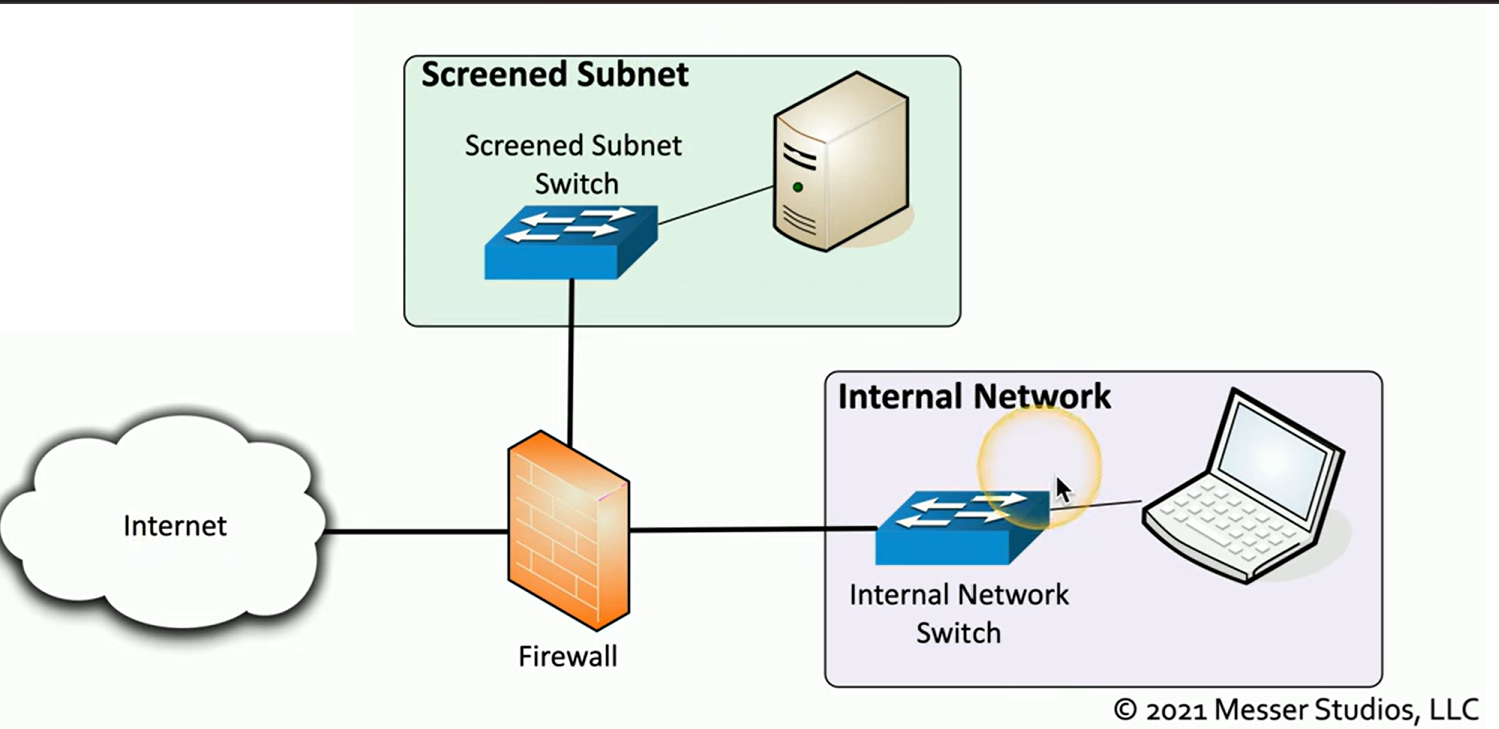
A screened subnet
Also known as a demilitarized zone (DMZ), is a specialized network area designed to host public-facing resources while keeping the internal network secure.
Is placed between the internet and the internal network, typically protected by a firewall. The firewall is configured to allow public access to resources within the subnet but blocks any direct access to the internal network.
This approach ensures that even if an attacker gains control of a resource, they cannot directly access or compromise the internal network.
Separation of duties
Is a security principle where critical tasks are divided among multiple people to prevent fraud, errors, or abuse.
Split Knowledge: Ensures no single individual has complete control or all the details needed to execute a sensitive operation. For example, in a secure environment, one person might only have half of a safe’s combination, with another person holding the other half.
Dual Control: Requires that two or more individuals work together to perform critical tasks. Both parties must be present and authorize the activity. A classic example is requiring two keys to open a safe or launch a missile.
Network Access Control (NAC)
Is a security solution that controls access to a network by enforcing authentication before granting access.
IEEE 802.1X – Port-based Network Access Control (NAC): This protocol ensures that no device gains network access until it has successfully authenticated. It works on the physical interfaces of a switch, rather than TCP or UDP ports. 802.1X is commonly implemented alongside protocols like Extensible Authentication Protocol (EAP) and Remote Authentication Dial In User Service (RADIUS).
Administrative Controls: Administrators can enable or disable ports manually, which helps secure the network by preventing unauthorized devices from connecting.
Duplicate MAC Address Checking: This feature helps in detecting and preventing unauthorized devices from masquerading as legitimate devices by using the same MAC address, thus stopping potential snoopers from gaining access.
IEEE 802.1X
Is a port-based Network Access Control (NAC) protocol used to secure network access.
It involves three main components: the supplicant (the device seeking access), the authenticator (a switch or wireless access point controlling the connection), and the authentication server (typically a RADIUS server verifying credentials).
The process starts when the supplicant attempts to connect, but access is blocked by the authenticator. The authenticator sends an EAP request, and the supplicant responds with its identity. This information is passed to the authentication server, which checks if the user is valid. If valid, the server sends a challenge back to the supplicant. The supplicant provides its credentials, which are forwarded by the authenticator for validation.
Once validated, the authenticator grants the device network access by enabling the port.
Honeypots
Are security tools designed to attract and trap attackers by mimicking vulnerable systems. Instead of blocking malicious activity, allow attackers to engage with fake systems while logging every move for analysis.
Common solutions include Kippo, Google Hack Honeypot, and Worldport.
Local authentication
Refers to the method where authentication credentials are stored directly on a device, such as a wireless router or switch. When configuring such devices, you need to enter a username and password that are managed locally. This means each device must be individually administered—if you have multiple devices, you must log in to each one to make changes, like updating passwords, which can be a cumbersome process.
Does not depend on external authentication servers, so it remains functional even during network outages.
Multifactor Authentication
Enhances security by requiring multiple forms of verification before granting access. It typically involves:
Something You Know: A password or PIN.
Something You Have: A hardware token or smartphone app.
Something You Are: Biometrics like fingerprints or facial recognition.
Somewhere You Are: Geolocation or IP address.
Something You Do: Behavioral patterns or actions.
Can range from expensive setups with specialized hardware tokens and scanning equipment to more affordable solutions using free smartphone applications.
RADIUS (Remote Authentication Dial-in User Service)
Is a widely-used AAA (Authentication, Authorization, and Accounting) protocol, primarily used over Ethernet networks rather than dial-in connections. It centralizes user authentication, making it suitable for various devices and services, including:
Network Devices: Routers, switches, firewalls.
Server Authentication: Ensuring secure access to servers.
Remote VPN Access: Authenticating users accessing networks remotely.
802.1X Network Access: Managing network access control for devices.
Is popular due to its broad compatibility across different operating systems and devices
TACACS (Terminal Access Controller Access-Control System)
Is a remote authentication protocol originally designed to manage access to ARPANET's dial-up lines. It is commonly used on local networks for authentication purposes.
+ is the latest version, introduced as an open standard in 1993. It offers enhanced functionality, including more comprehensive authentication requests and response codes.
LDAP (Lightweight Directory Access Protocol)
Is used for reading and writing directory information over an IP network. It functions similarly to a phone directory, organizing extensive records about network devices and users.
Originally based on the X.500 specification developed by the International Telecommunications Union (ITU), it operates on a lightweight protocol compared to its predecessor, DAP, which ran on the OSI protocol stack.
Queries and updates X.500 directories and is utilized in various systems such as Windows Active Directory, Apple OpenDirectory, and Novell eDirectory.
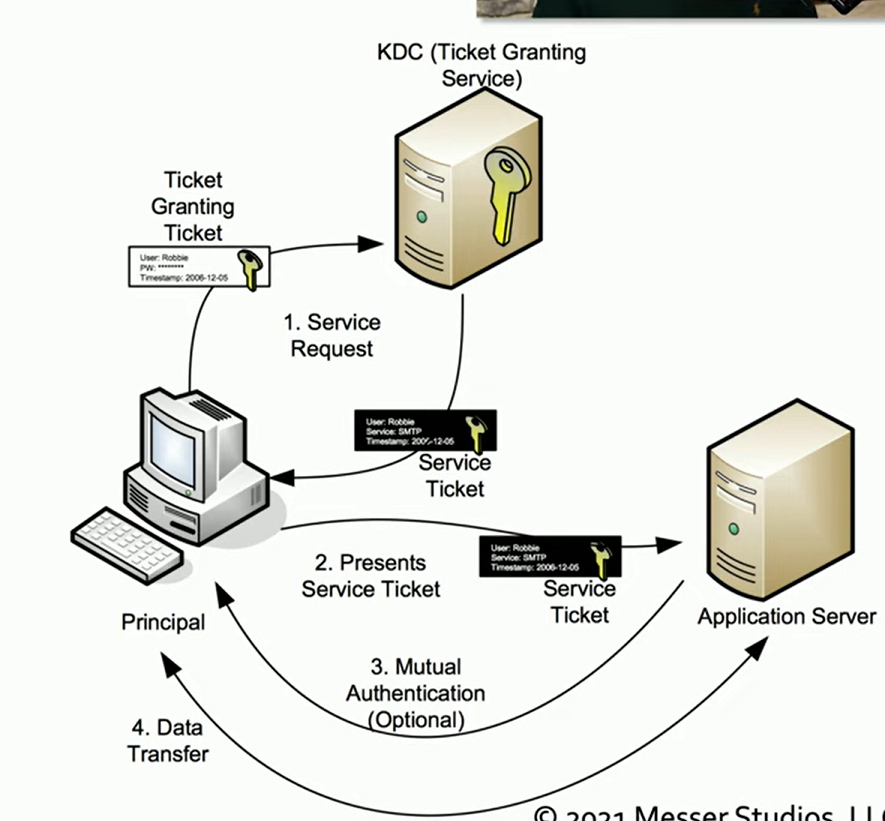
Kerberos
Is a network authentication protocol designed to allow users to authenticate once and gain access to multiple services without needing to re-authenticate. Developed by MIT in the 1980s, it provides mutual authentication, ensuring that both the client and server authenticate each other, protecting against man-in-the-middle and replay attacks.
Has been a standard since its inception and was incorporated into Microsoft Windows starting with Windows 2000, based on the 5.0 open standard. It is compatible with various operating systems and devices.
Single sign-on (SSO) with Kerberos
Allows users to authenticate once and gain access to multiple services without repeatedly entering credentials. It relies on a system of cryptographic tickets, which handles the backend authentication process.
Kerberos is complex, involving various devices and cryptographic methods, and works well for environments where it is supported. However, not all systems are Kerberos-compatible. Other SSO methods include smart cards and SAML (Security Assertion Markup Language).
Choosing an Authentication Method
Depends on the specific requirements and existing infrastructure:
TACACS+: Often used with Cisco devices for network access control.
Kerberos & LDAP: Best for environments with Microsoft networks.
IEEE 802.1X Again
Is a port-based network access control protocol that requires authentication before granting network access.
802.1X Process:
Supplicant: The device seeking access to the network.
Authenticator: The network device (e.g., switch or access point) controlling access.
Authentication Server: The server (e.g., RADIUS, LDAP, TACACS+) verifying credentials
Extensible Authentication Protocol (EAP)
is an authentication framework used across various services, not just 802.1X. Supports multiple authentication methods as defined by RFC standards.
Forms the core of Network Access Control (NAC) by verifying credentials before allowing network access.