ISC- S3
1/54
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
55 Terms
1 data breaches, service disruptions, compliance risk

2 cyberattacks and types of cyberattacks chart
3 cyberattacks-network based attacks

4 reverse shell attacks, return-oriented attacks
5 spoofing- address resolution spoofing and dns spoofing

6 application based attacks-structured query language (SQL) injection, cross site scripting (XSS)
7 difference between structured query language (SQL) injection and cross site scripting (XSS)
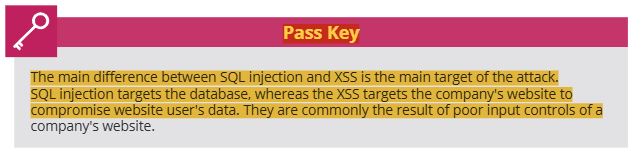
8 race condition, mobile code (including ovewrite virus, multi-partite virus, parasitic virus, polymorphic virus, resident virus)
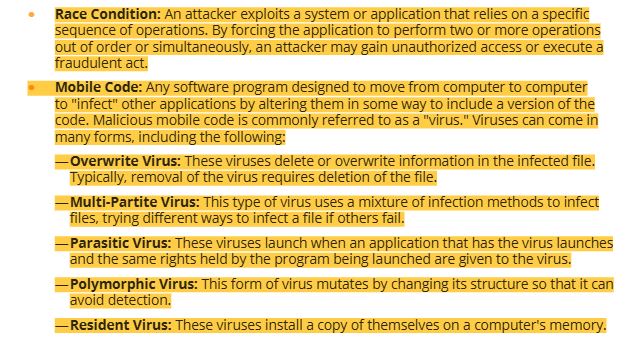
9 host based attacks-brute force attack
10 social engineering attacks- spear phising, business email compromise (BEC), pretexting, pharming, vishing

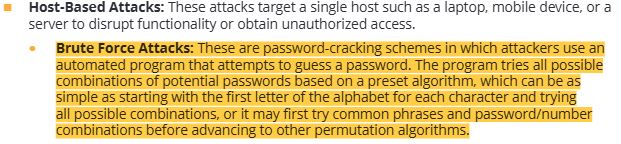
11 physical, on-premises attacks- piggybacking
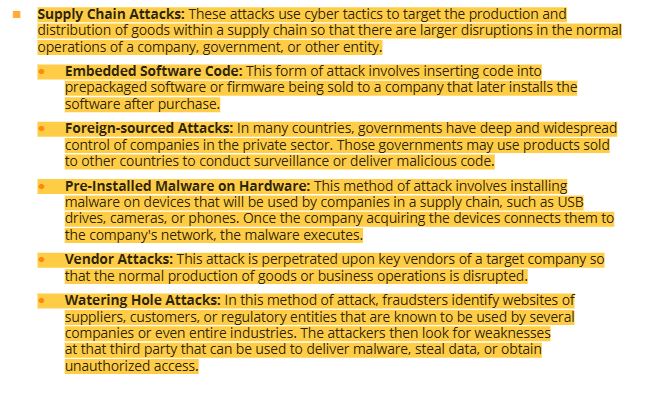
12 supply chain attacks- embedded software code, foreign sourced attacks, pre-installed malware on hardware, vendor attacks, watering hole attacks
13 stages in a cyber attack

14 PASTA threat model

15 VAST threat model

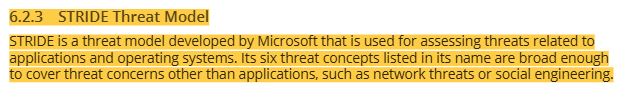
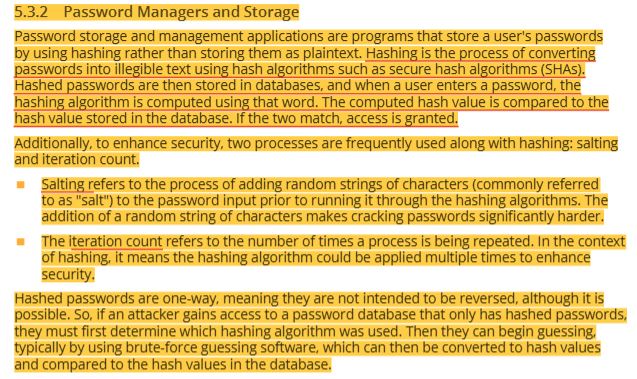
16 STRIDE threat model
17 COSO framework- operational objectives, reporting objectives, compliance objectives

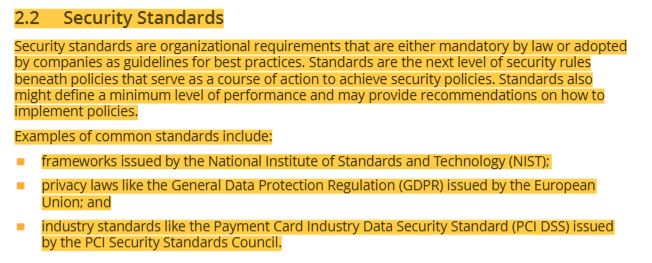
18 security standards
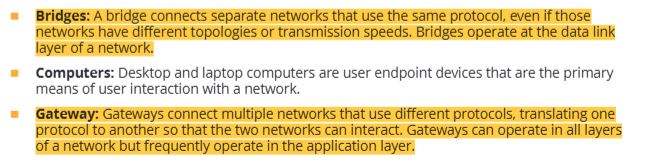
19 network protection methods- bridges, gateway
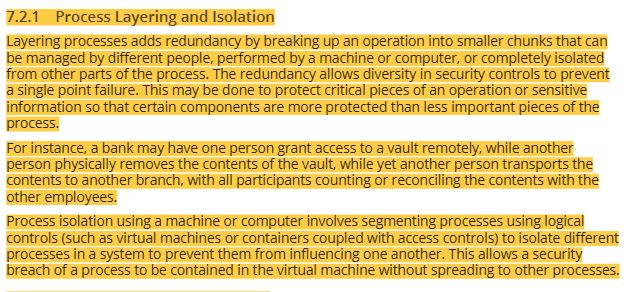
20 network protection methods- signal modifiers, switches

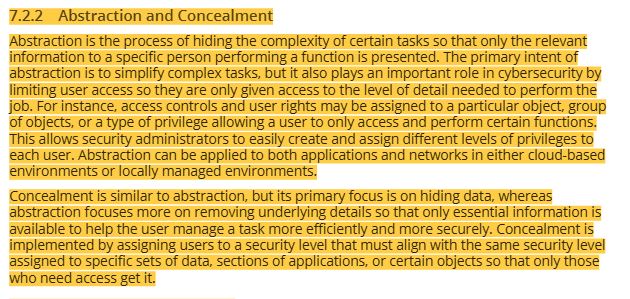
21 network security- network segmentation or isolation, service set identifyer (SSID)

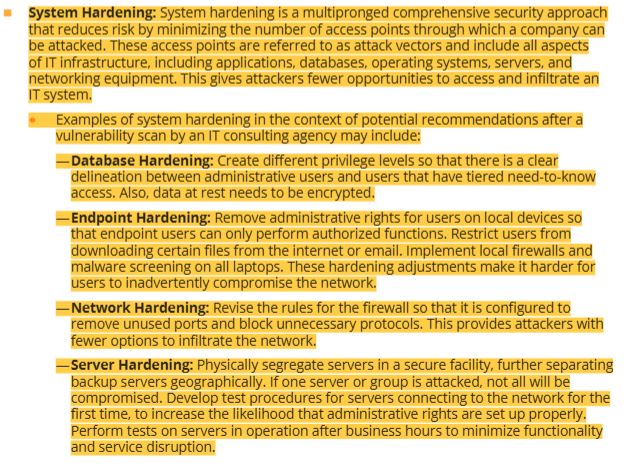
22 system hardening- examples are database, endpoint, network and server hardenings
23 NIST password recommendations

24 password managers- hashing, salting, iteration count definitions
25 provisioning

26 common vulnerabilities and exposures dictionary

27 defense in depth- logical access controls

28 process layering and isolation
29 abstraction and concealment
30 hardware segmentation

31 device and software hardening, intrusion prevention systems (IPS)

32 discretionary access control (DAC), mandatory access controls

33 policy based access control (PBAC), risk based access controls

34 access control lists (ACL)- filesystem ACL, networking ACL

35 detective controls- network intrusion detection system (NIDS), network monitoring tools, intrusion detection systems (IDS)

36 difference between security assessments and vulnerability assessments

37 security assessment reports- including the key terms in SARs
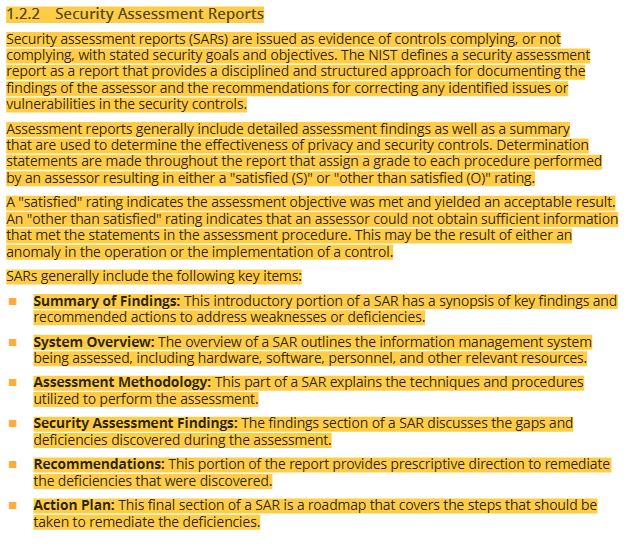
38 tokenization, masking definitions and chart
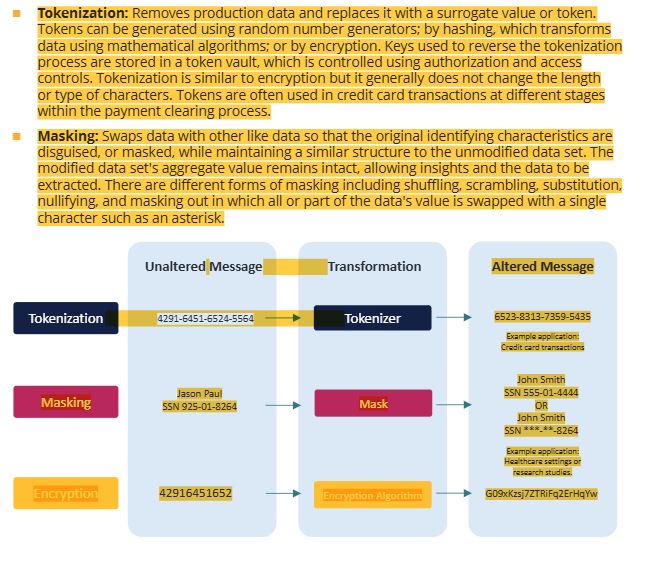
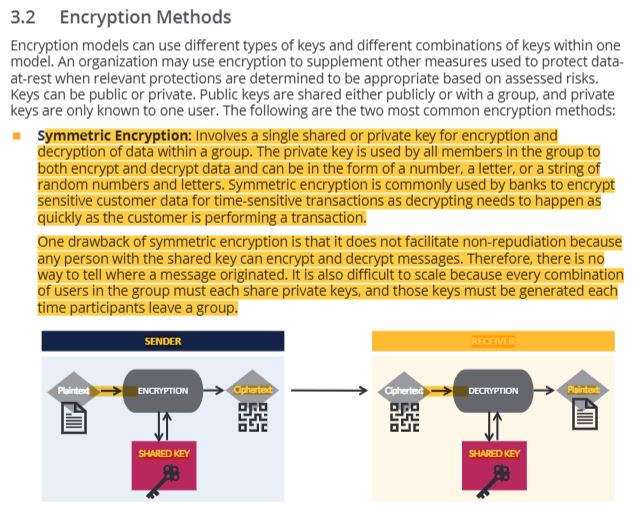
39 symmetric encryption
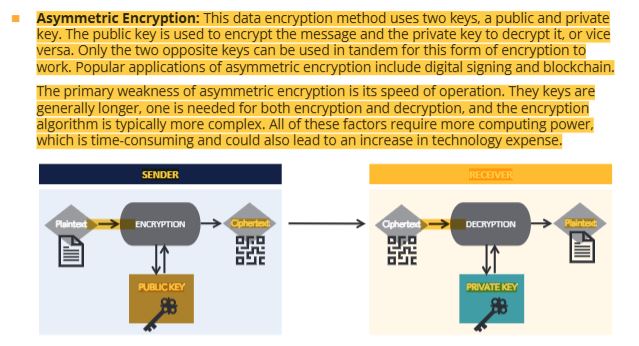
40 asymmetric encryption
41 private keys and whether it is symmetric or asymmetric encryption

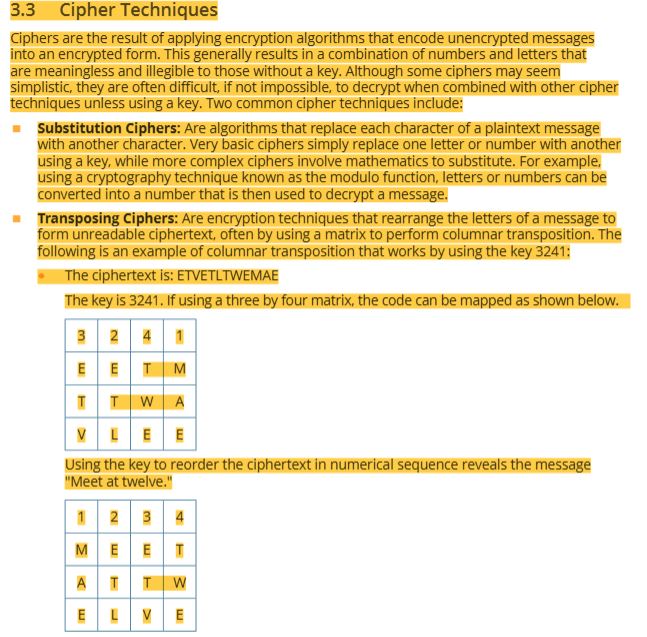
42 cipher techniques- substitution ciphers and transposing ciphers with charts
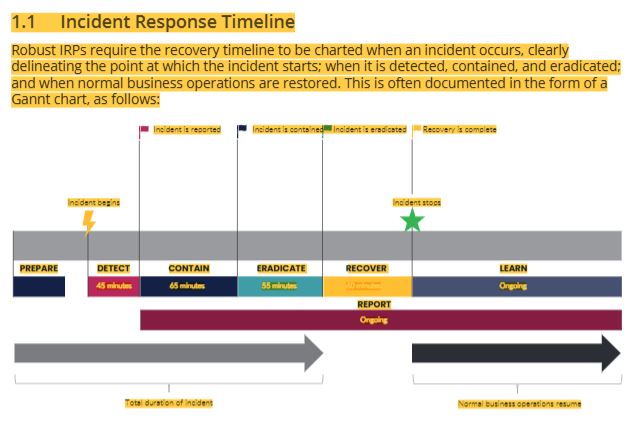
43 incident response timeline chart
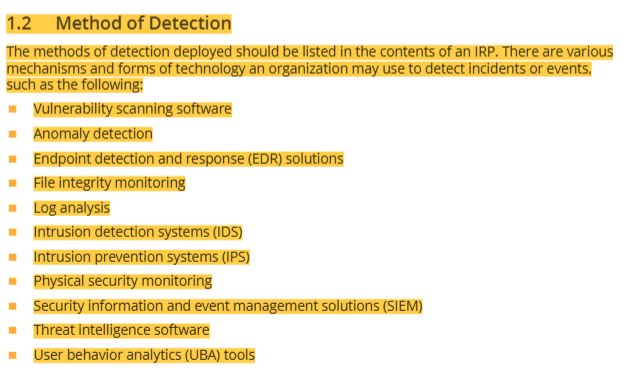
44 method of detection for incident response timeline
45 steps to responding to an incident (there are 7)

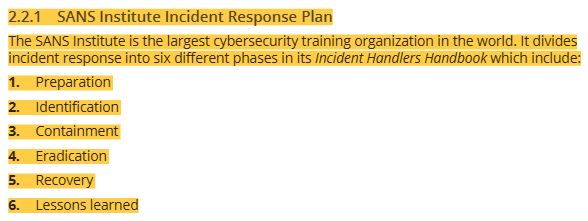
46 SANS institute incident response plan
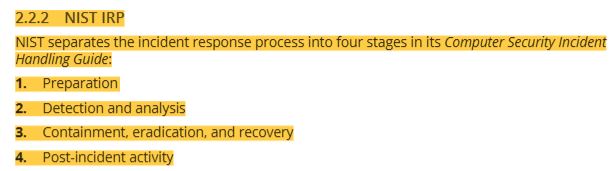
47 NIST IRP
48 international organization for standardization IRP

49 other IRP organizations and frameworks

50 IRPs tailored to specific attacks

51 IRP metrics- mean time to detect (MTTD), mean time to acknowledge (MTTA), mean time to contain (MTTC), mean time to repair (MTTR), mean time between failures (MTBF), system availability or downtime, service level agreement compliance

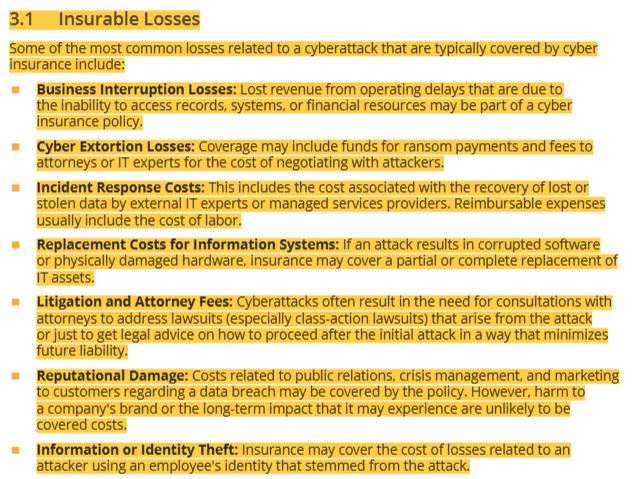
52 insurable losses related to cyberattack
53 cyber insurance requirements for applicants

Typosquatting
A malicious practice where an attacker registers a domain name that is a misspelling of a legitimate brand's domain to deceive users into visiting the fraudulent site.
NIST Risk Management Framework