Week 10: Buffer Overflow
1/11
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
12 Terms
EIP
Extended Instruction pointer - tells the computer where to go next to execute the next command and controls the flow of a program
ESP
Points to the TOP of the stack. When you push or pop data onto the stack, it goes here and ESP is then adjusted to reflect the new stack head.
EBP
Points to the BASE of the stack FRAME. When you call a function, this is saved on the stack and EBP now points to the base of the new stack FRAME. All local variables can be found relative to this pointer.
the instruction pointer controls
which code executes
the instruction pointer is stored
on the stack
Buffer Overflow
If input is longer than intended then the items in the stack will be overread
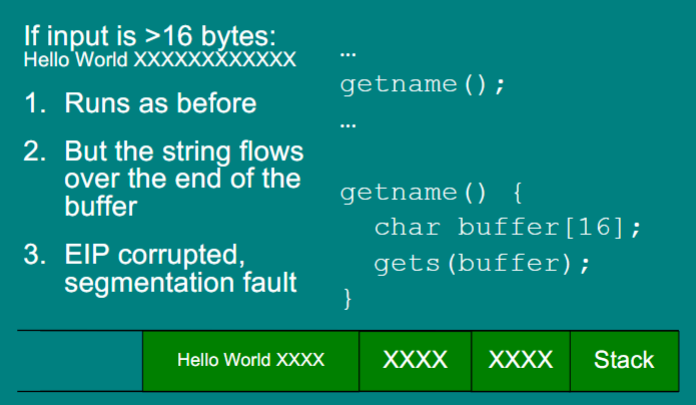
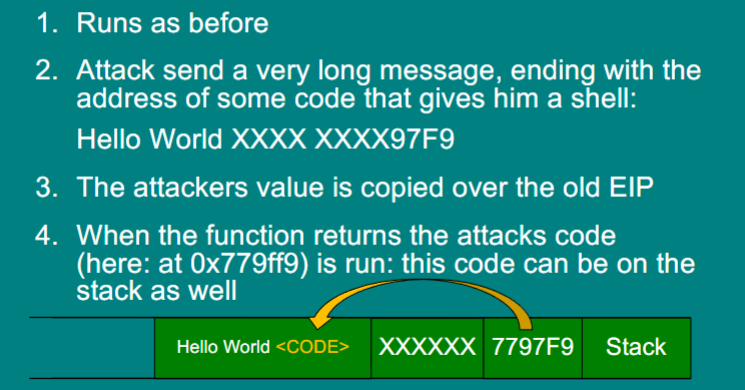
Buffer overflow inputting string with malice
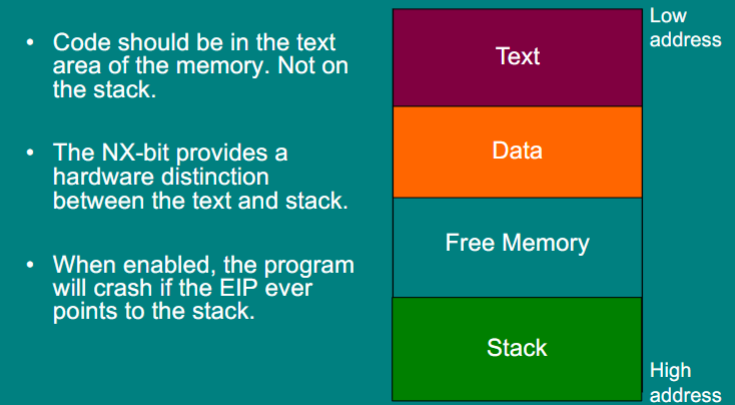
Defense: The NX-bit
what is the standard attack against the NX-bit
Reuse Code from the executable part of memory
• Jump to another function in the program.
• Jump to a function from the standard C library (Return to libc)
• String together little pieces of existing code (Return-oriented programming).
Libc
the C standard library
It is often packaged with executables to provide a runtime environment.
It includes lots of useful calls like “system” which runs any command.
It links to executable memory, therefore bypasses NX- bit protections.
ASLR
Address space layout randomization
ASLR adds a random offset to the stack and code base each time the program runs.
Jumps in the program are altered to point to the right line.
The idea is that its now hard for an attacker to guess the address of where they inject code or the address of particular functions
Metasploit
Metasploit is a framework for testing and executing known buffer overflow attacks.
If a vulnerability in an application is well known their will be a patch for it, but also a Metasploit module for it.
If an application is unpatched it can probably be taken over with Metasploit.
Metasploit also includes a library of shell code which can be injected.
Without wishing to get into another debate, using it against machines you don’t own is illegal. Do not do this.