2.2 Zero Trust
1/6
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
7 Terms
Zero Trust
Zero trust (ZT) is a security framework requiring all subjects, assets, and workflows to be authenticated, authorized, and continuously validated before being granted or keeping access to applications , and data.
Zero Trust View of a Network
No implicit zone trust
No ownership assumptions
Insecure connections assume all any remote subjects networks are assumed to be malicious
Consistent Security policy
Core principles of Zero Trust
Continuous Verification
Access Limitation
Limit the Blast Radius
Automate
Control Plane
The control plane is used by infrastructure components to maintain and configure assets, access control, and communication security. In a ZT environment, requests for access are made through the control plane.
Data Plane
The data plane is used for communication (moving data) between software components.
ZTA
Zero Trust Architecure
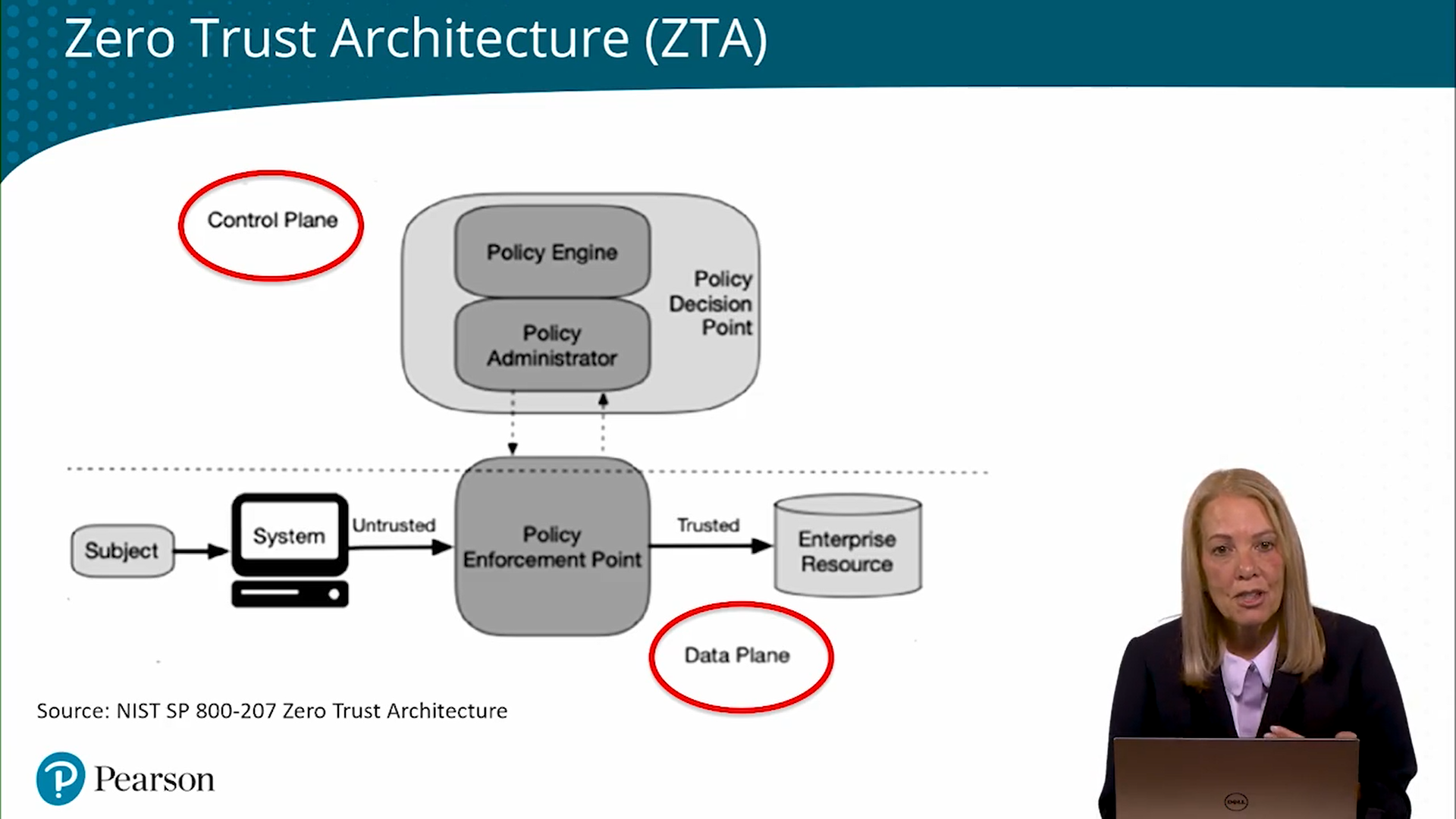
Zero Trust Logical Components
Policy Decision Point(PDP): Functions as a gatekeeper. Has the PE and PA inside
Policy Engine (PE) Responsible for the ultimate decision to grant access to a resource for a given subject
Policy Administrator (PA) Generates any session-specific authentication and authentication token, or credential used to access an enterprise rescource.
Policy Enforcement Point (PEP) responsible for enabling, monitoring, and eventually terminating connections between a subject and an enterprise rescource.