Certified Ethical Hacker (CEHv13) Module 17 Hacking Mobile Platforms
1/89
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
90 Terms
OWASP Top 10 Mobile Risks - 2024
- M1: Improper Credential Usage
- M2: Inadequate Supply Chain Security
- M3: secure Authentication/Authorization
- M4: Insufficient Input/Output Validation
- M5: Insecure Communication
- M6: Inadequate Privacy Controls
- M7: Insufficient Binary Protections
- M8: Security Misconfiguration
- M9: Insecure Data Storage
- M10: Insufficient Cryptography
Anatomy of a Mobile Attack
- Point 1: The Device
- Point 2: The Network
- Point 3: The Data Center/Cloud
Browser-based Attacks
- Phishing
- Framing
- Clickjacking
- Man-in-the-Mobile
- Buffer Overflow
- Caching
Phishing
Phishing emails or pop-ups redirect users to fake web pages that mimic trustworthy sites, asking them to submit their personal information such as username, password, credit card details, address, and mobile number.
Framing
Framing involves a malicious web page integrated into another web page using the iFrame elements of HTML
Clickjacking
Clickjacking is a malicious technique used to trick web users into clicking something different from what they think they are clicking
Man-in-the-Mobile
An attacker implants malicious code into the victim's mobile device to bypass password verification systems that send one-time passwords (OTPs) via SMS or voice calls. Thereafter, the malware relays the gathered information to the attacker.
Buffer Overflow
Buffer overflow is an abnormality whereby a program, while writing data to a buffer, surfeits the intended limit and overwrites the adjacent memory
Data Caching
Data caches in mobile devices store information that is often required by these devices to interact with web applications, thereby preserving scarce resources and resulting in better responses time for client applications. Attackers attempt to exploit these data caches to access the sensitive information stored in them.
Phone/SMS-based Attacks
- Baseband Attack
- SMSing
Baseband Attack
Attackers exploit vulnerabilities in a phone's GSM/3GPP baseband processor, which sends and receives radio signals to cell towers
SMSing
A type of phishing fraud in which an attacker uses SMS to send text messages containing deceptive links of malicious websites or telephone numbers to a victim
Application-based Attacks
- Sensitive Data Storage
- No/Weak Encryption
- Improper SSL Validation
- Configuration Manipulatinon
- Dynamic Runtime Injection
- Unintended Permissions
- Escalated Privileges
Types of Mobile Device Attacks
- Browser-based Attacks
- Phone/SMS-based Attacks
- Application-based Attacks
- The System
Dynamic Runtime Injection
Attackers manipulate and abuse the run time of an application to circumvent security locks and logic checks, access privileged parts of an app, and even steal data stored in memory
System Attacks
- No Passcode/Weak Passcode
- iOS Jailbreaking
- Android Rooting
- OS Data Caching
- Passwords and Data Accessible
- Carrier-loaded Software
- User Initiated Code
iOS Jailbreaking
Jailbreaking iOS is the process of removing the security mechanisms set by Apple
Android Rooting
Rooting allows Android users to attain privileged control within Android's subsystem
OS Data Caching
An OS cache stores used data/information in memory on a temporary basis in the hard disk. An attacker can dump this memory by rebooting the victim's device with a malicious OS and extract sensitive data from the dumped memory.
User Initiated Code
§ User-initiated code is an activity that tricks the victim into installing malicious applications or clicking links that allow an attacker to install malicious code
Network Attacks
- Wi-Fi (weak encryption/no encryption)
- Rogue Access Points
- Packet Sniffing:
- MITM
- Session Hijacking
- DNS Poisoning
- SSLStrip
- Fake SSL Certificates
SSLStrip
SSLStrip is a type of MITM attack in which the attacker invisibly downgrades HTTPS connections to HTTP without encryption
Data Center/Cloud Attacks
- Web-server-based attacks
- Database Attacks
Web Server Based Attacks
- Platform Vulnerabilities
- Server Misconfiguration
- XSS
- CSRF
- Weak Input Validation
- Brute Force Attacks
XSS Attack
Exploits vulnerabilities in dynamically generated web pages, which enable malicious attackers to inject client-side script into web pages viewed by other users
CSRF
CSRF attacks exploit web page vulnerabilities that allow an attacker to force an unsuspecting user's browser to send unintended malicious requests
Database Attacks
- SQLi
- Data Dumping
- OS Command Execution
- Privilege Escalation
SQLi
SQL injection is a technique used to take advantage of nonvalidated input vulnerabilities to pass SQL commands through a web application for execution by a backend database
Data Dumping
An attacker causes the database to dump some or all of its data, thereby uncovering sensitive records
Surveillance Exploits
- Audio
- Camera
- Call Log
- Location
- SMS Messages
- IoT/AI devices
- Smart Appliances
Financial Exploits
- Sending premium-rate SMS messages
- Extortion via ransomware
- Fake anti-virus
- Making Expensive Calls
- Cryptocurrency mining
Data Theft Exploits
- Account Details
- Contacts
- Call logs and phone number
- Stealing data via app vulnerabilities
- Stealing International Mobile Equipment Identity Number (IMEI)
- Personal Health Information
Mobile Exploits
- Data Theft (Account Details, Contacts, Call logs and phone number, Stealing data via app vulnerabilities, Stealing International Mobile Equipment Identity Number (IMEI), Personal Health Information)
- Surveillance (Audio, Camera, Call Log, Location, SMS Messages, IoT/AI devices, Smart Appliances)
- Financial (Sending premium-rate SMS messages, Extortion via ransomware, Fake anti-virus, Making Expensive Calls, Cryptocurrency mining)
- Botnet Activity (DoS Attacks, Click fraud, Sending premium-rate SMS messages)
- Impersonation (SMS redirection, Sending emails, Posting to social media, Stealing passwords)
Botnet Activity Exploits
- DoS Attacks
- Click fraud
- Sending premium-rate SMS messages
Impersonation Exploits
- SMS redirection
- Sending emails
- Posting to social media
- Stealing passwords
Mobile Attack Vectors
- Malware (Application Modification, virus and rootkit, OS modification
- Data Exfiltration (Extracted from data streams and email, Print screen and screen scraping, Copy to USB key and loss of backup)
- Data Tampering (Modification by another application, Undetected tamper attempts, Jailbroken Device)
- Data Loss (Application vulnerabilities, Unapproved physical access, Loss of Device)
Malware Attack Vectors
- Application modification
- Virus and Rootkit
- OS Modification
Data Exfiltration Attack Vectors
- Extracted from data streams and email
- Print screen and screen scraping
- Copy to USB key and loss of backup
Data Tampering Attack Vectors
- Modification by another application
- Undetected tamper attempts
- Jailbroken Device
Data Loss Attack Vectors
- Application vulnerabilities
- Unapproved physical access
- Loss of Device
App Sandboxing
App sandboxing is a security mechanism that helps protect systems and users by limiting the resources that an app can access to its intended functionality on the mobile platform
Spam
Spam is a generic term for unsolicited messages sent via electronic communication technologies
Mobile Phone Spam
Mobile phone spam refers to unsolicited messages sent in bulk form to known/unknown phone numbers/email IDs to target mobile phones.
Bluesnarfing
Bluesnarfing is the theft of information from a wireless device through a Bluetooth connection
Bluebugging
Bluebugging involves gaining remote access to a target Bluetooth-enabled device and using its features without the victim's knowledge or consent.
Bluetooth Attacks
- Bluebugging
- Bluesnarfing
Agent Smith Attack
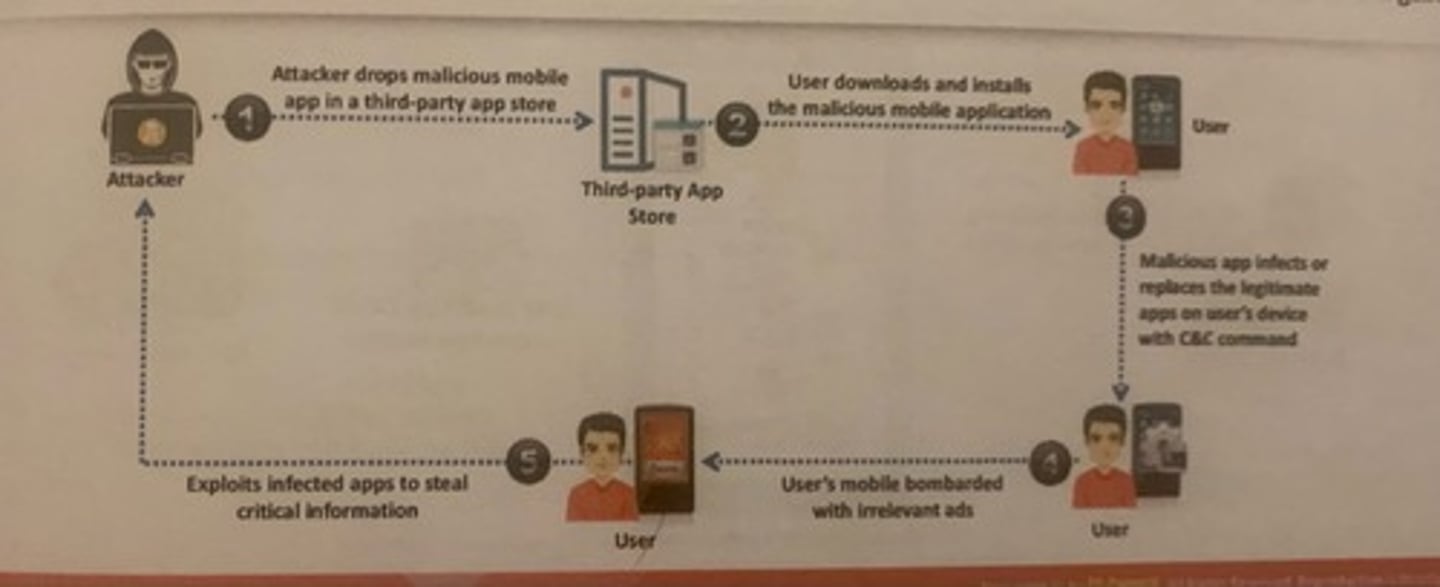
Agent Smith attacks are carried out by luring victims into downloading and installing malicious apps from third-party app stores. Once the user has installed the app, the core malicious code inside the malicious app infects or replaces the legitimate apps in the victim's mobile device C&C commands. The attacker then produces a massive volume of irrelevant and fraudulent advertisements on the victim's device through the infected app for financial gain. Attackers exploit these apps to steal critical information such as personal information, credentials, and bank details, from the victim's mobile device through C&C commands
Signaling System 7 (SS7)
SS7 is a communication protocol that allows mobile users to exchange communication through another cellular network (especially when roaming)
Threats Associated with SS7
- Exposing the subscriber's identity
- Revealing the network identity
- Spying on and intercepting the network to steal personal data
- Allowing phone tapping
- Performing DoS attacks to damage the reputation of the target telecom operator
- Tracking geographic locations
Simjacker
Simjacker is a vulnerability associated with a SIM card's S@T browser (SIMalliance Toolbox Browser), a pre-installed software incorporated in SIM cards to provide a set of instructions.
Call Spoofing
Call spoofing is a technique used by attackers to manipulate the caller ID information displayed on a recipient's phone when they receive a call.
One-time passwords (OTPs)
OTPs are sent by a server via SMS, an authenticator app, or an email for the secure authentication of users
OTP Hijacking
Attackers can hijack OTPs and redirect them to their personal devices. Using the stolen OTP, attackers can login to the victim's online accounts, reset passwords, and steal sensitive information.
Camfecting Attack
A camfecting attack is a webcam capturing attack where the attacker gains access to the camera and microphone of a target's computer or mobile device.
Android OS Architecture Software Components
1. System Apps
2. Java API Framework
3. Native C/C++ Libraries
4. Android Runtime
5. Hardware Abstraction Layer
6. Linux Kernel
Android Device Administration API
The device administration API provides device administration features at the system level. Such APIs allow developers to create security-aware applications that are useful in enterprise settings, in which IT professionals require rich control over employee devices. One can use a device administration ("admin") API to write device admin applications that users install on their devices. The device admin application enforces the desired policies.
Factory Reset Permission
Factory Reset Protection (FRP) is a security feature of Android devices designed to prevent unauthorized access to lost or stolen devices
Man-in-the-Disk Attack (MITD)
Attackers perform a man-in-the-disk (MITD) to install malicious apps on the user's device, thereby blocking access to legitimate apps.
Spearphone Attack
A spearphone attack allows Android apps to record loudspeaker data without any privileges. Attackers can eavesdrop on loudspeaker voice conversations between remote mobile users by exploiting the hardware-based motion sensor.
Analyzing Android Devices Tasks
- Accessing the Android Device through Shell
- Enumerate the List of Installed Applications
- Disassemble the Targeted App Package
- Monitoring Logs
- List Out the Open Files
- List Out the Open Connections
- Signing and Installing Malicious APK
Over-the-Air (OTA) provisioning
OTA is a mechanism that is used to send provisioning data and updates in a mobile device remotely.
SSL Pinning
SSL pinning allows applications to perform operations only after validating trusted certificates and public keys.
Tap 'n Ghost Attack
Tap 'n Ghost is a novel attack technique that exploits NFC-enabled Android devices. This attack targets NFC technology and RX electrodes used in the capacitive touchscreens of mobile devices. If the attacker is able to establish a remote connection with the target mobile device, he/she can take full control of the device.
Tap 'n Ghost Attack Technqiues
- Tag-based Adaptive Ploy (TAP)
- Ghost Touch Generator
Tag-based Adaptive Ploy (TAP)
TAP uses the NFC feature, which can trigger the Android device to visit a specific URL without the victim's consent using the NFC tag emulator. This attack works with a web server that uses the device fingerprinting technique.
Ghost Touch Generator
Ghost Touch Generator works by forcing the victim to touch the cancel button, which does the work of the permit button. Thus, the attacker can trick the victim into granting remote access to the smartphone without the victim's knowledge.
iOS Layers
1. Cocoa Application
2. Media
3. Core Services
4. Core OS
5. Kernel and Device Drivers
Cocoa Application
This layer contains key frameworks that help in building iOS apps. These frameworks define the appearance of the apps, offer basic app infrastructure, and support key technologies.
Jailbreaking
Jailbreaking is defined as the process of installing a modified set of kernel patches that allow users to run third-party applications not signed by the OS vendor. It is the process of bypassing the user limitations set by Apple.
Types of Jailbreaking
- Userland Exploit
- iBoot Exploit
- Bootrom Exploit
Userland Exploit
Userland Exploit uses a loophole in the system application. It allows user-level access but does not allow iboot-level access.
iBoot Exploit
This exploit takes advantage of a loophole in iBoot to delink the code-signing appliance. An iboot jailbreak allows user-level access and iboot-level access.
Bootrom Exploit
Bootrom Exploit uses a loophole in the SecureROM to disable signature checks, which can be used to load patch NOR firmware. A bootrom jailbreak allows user-level access and iboot-level access.
Jailbreaking Technqiues
- Untethered Jailbreaking
- Semi-tethered Jailbreaking
- Tethered
- Semi-untethered Jailbreaking
Untethered Jailbreaking
The device will be jailbroken after each reboot
Semi-tethered Jailbreaking
To use jailbroken addons, the user needs to start the device with the help of the jailbreaking tool.
Tethered Jailbreaking
It must be "re-jailbroken" with a computer each time it is turned on
Semi-untethered Jailbreaking
In this type of jailbreak, when the device reboots, the kernel is not patched. However, the kernel can be patched without using a computer.
iOS Trustjacking
iOS Trustjacking is a vulnerability that can be exploited by an attacker to read messages and emails and capture sensitive information. This vulnerability exploits the "iTunes Wi-Fi Sync" feature whereby a victim connects his/her phone to any trusted computer that is already infected by the attacker.
iOS Method Swizzling
Method swizzling, also known as monkey patching, is a technique that involves modifying the existing methods or adding new functionality at runtime.
Analyzing iOS Devices Techniques
- Accessing the Device Shell
- Listing Installed Apps
- Network Sniffing
- Obtain Open Connections
- Process Exploration
Accessing iOS Device Shell
This technique involves remotely accessing an iOS shell, with or without a USB cable. This allows an attacker to execute arbitrary commands, manipulate system settings, and gain deeper control over the device.
Mobile Device Management (MDM)
MDM provides platforms for distribution of applications, data, and configuration settings for all types of mobile devices. It helps in implementing enterprise-wide policies.
MDM Features
- Uses a passcode for the device
- Remotely locks the device if it is lost
- Remotely wipes data in the lost or stolen device
- Detects if the device is rooted or jailbroken
- Enforces policies and tracks inventory
- Performs real-time monitoring and reporting
Bring Your Own Device (BYOD)
BYOD refers to a policy that allows employees to bring their personal devices to their workplace and use them for accessing the organization's resources as per their access privileges.
BYOD Benefits
- Increased Productivity
- Employee Satisfaction
- Increased Flexibility
- Lower Cost
BYOD Risks
- Sharing confidential data on unsecured networks
- Data Leakage and Endpoint Security Issues
- Improperly disposing of devices
- Support for many different devices
- Mixing personal and private data
- Lost or stolen devices
- Lack of awareness
- Ability to bypass an organization's network policy rules
- Infrastructure issues
- Disgruntled employees
- Jailbreaking/Rooting
- Inadequate Backup
- Outdated Software and Patch Management
- Shadow IT and Unauthorized Cloud Services
BYOD Policy Implementation Principles
- Define your requirements
- Select the devices of your choice and build a technology portfolio
- Develop Policies
- Security
- Support
BYOD Policies Key Components
- Information security concerns
- Data protection concerns
- Confidentiality and ownership issues
- Information regarding any tracking/monitoring
- Considerations regarding the termination of employment
- Guidance regarding how to assess the security of Wi-Fi networks
- Acceptable and unacceptable behavior
Reverse Engineering
Reverse engineering is the process of analyzing and extracting the source code of a software or application and, if needed, regenerating it with required modifications. Reverse engineering is used to disassemble a software program or a mobile application to analyze its design flaws and fix any bugs that are residing in it