AZ 900 Practice Test 5
1/25
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
26 Terms
Which resource lock type is equivalent to limiting all authorized users to the “reader” role’s permission?
ReadOnly
There are two kinds of resource locks: one restricts users from removing resources, and the other restricts modifying or deleting resources.
Delete: Delete implies that a resource is no longer available for reading or editing by authorized users.
ReadOnly: A resource marked as ReadOnly can only be updated or deleted by authorized users. Applying this lock is equivalent to limiting all authorized users to the “reader” role’s permissions.
Delete
Delete implies that a resource is no longer available for reading or editing by authorized users.
ReadOnly
A resource marked as ReadOnly can only be updated or deleted by authorized users. Applying this lock is equivalent to limiting all authorized users to the “reader” role’s permissions.
Which type of access is required to save Azure BluePrint definitions to a management group or subscription?
Contributor Access
Azure BluePrints can be created through the Azure portal, Azure PowerShell, the Azure CLI, ARM templates, or the REST API. BluePrint definitions are saved to a management group or subscription, which requires contributor access.
Azure BluePrints deploy and update cloud environments in a repeatable manner using which composable artifacts? (Refer to the following exhibit and choose three.)
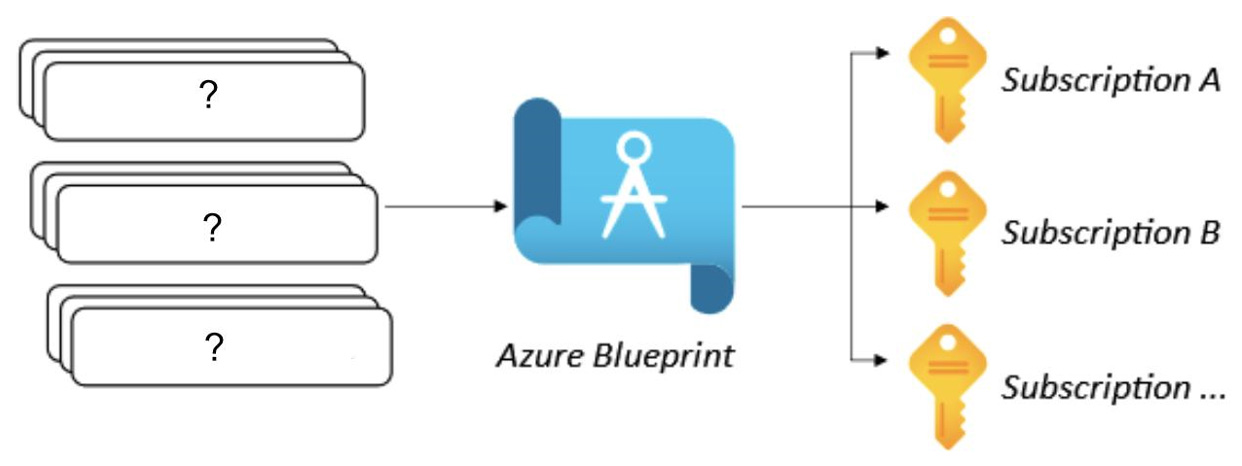
ARM templates, Role-based Access Control, Policy definitions
Azure BluePrints allow governed environments to be quickly and repeatably deployed across subscriptions to a governed resources standard using a set of composed artifacts like ARM templates, RBAC, and policy definitions.
Azure Portal is a GUI console for interacting with Azure resources. Which underlying service is used by the portal to perform activities in the background, providing progress notifications of completed and failed tasks?
ARM API
All tasks carried out in the portal use the underlying Azure Resource Manager (ARM) API. The ARM API performs all the activities in the background and will notify you of progress and whether any tasks have been completed or failed.
An administrator is installing the Azure PowerShell module. Which commands set the PowerShell script execution policy to remote signed or less restrictive? (Choose two.)
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
Get-ExecutionPolicy -List
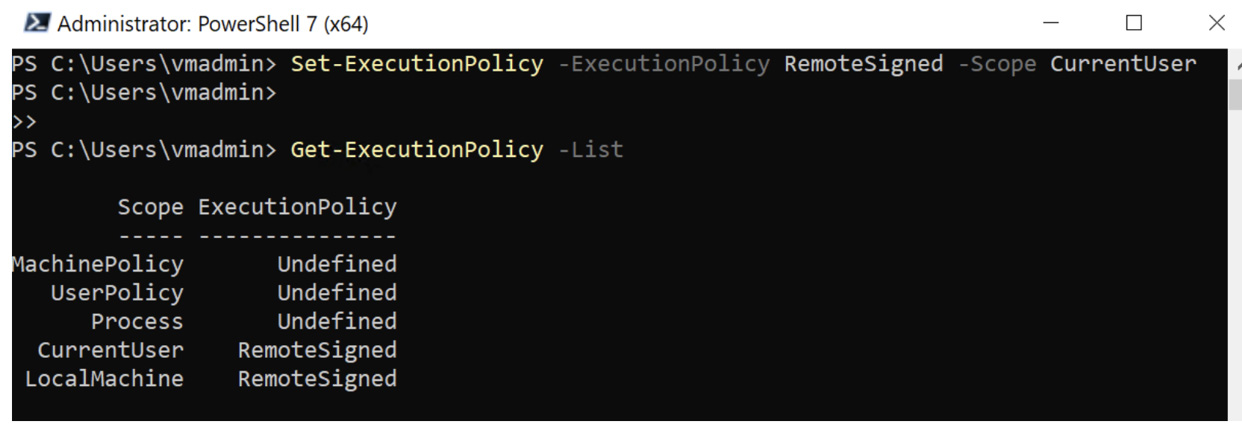
When installing the Azure PowerShell module, the administrator must set the execution policy before installing the Az module. The execution policy can be set to remote signed or less restrictive. The following command should be entered first:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
To confirm the PowerShell script execution policy, the following command is used:
Get-ExecutionPolicy -List
The output is as follows:
Which command updates the PowerShell module for Azure?
Update-Module -name Az
To update the Azure PowerShell module (Az module) to the latest version, you can use the Update-Module command. Here’s how you do it:
1. Open PowerShell with administrative privileges.
2. Run the following command:
Update-Module -name Az
This command updates the Az module to the latest version available in the PowerShell Gallery.
An administrator wants to install Azure CLI (a cross-platform CLI management tool for interacting with Azure resources) on a RedHat Enterprise Linux platform.
Which package is suitable for the RHEL platform?
YUM package manager
The Azure CLI can be installed for each OS like so:
Windows: MSI installer package file format
Ubuntu, Debian Linux: Apt package manager
RHEL, Fedora, CentOS: YUM package manager
openSUSE, SLES: Zypper package manager
macOS: Homebrew package manager
Which Shell environments are offered by CloudShell as a hosted shell and scripting environment for Microsoft hosted on Ubuntu containers? (Choose two.)
Bash with the Azure CLI installed, PowerShell with the Azure PowerShell module installed
Cloud Shell provides two Shell environments so that you can choose the one that best suits your requirements:
Bash with the Azure CLI installed
PowerShell with the Azure PowerShell module installed
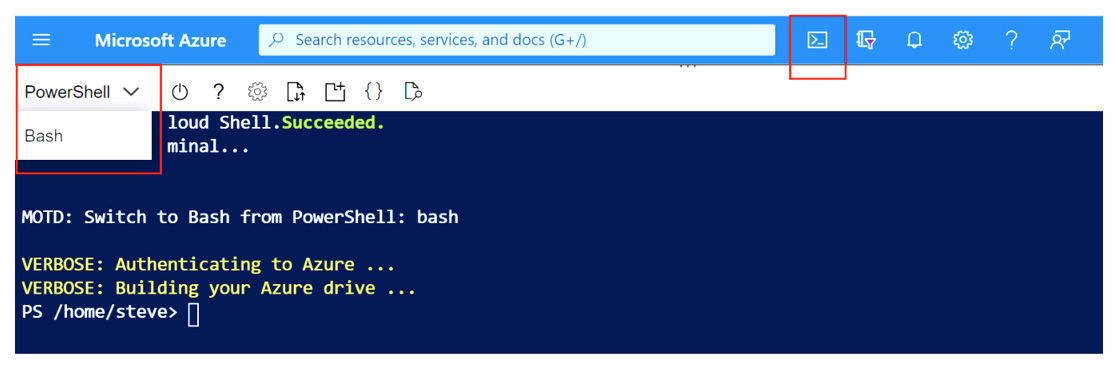
Cloud Shell can be accessed directly within the Azure portal via the code icon at the top of the portal toolbar, as shown in the above screenshot:
What type of storage account should be used to store unstructured data?
Azure Blob Storage
Azure Blob Storage is a simple, scalable, cost-effective solution for unstructured data. It is designed to store and serve large amounts of unstructured data, such as text or binary data, images, videos, and log files.
To manage the permission at the key vault which Permission Model can be used? (Choose two.)
Vault access policy, Azure role-based access control
A Key Vault access policy determines whether a given security principal, namely a user, application or user group, can perform different operations on Key Vault secrets, keys, and certificates.
Azure role-based access control (Azure RBAC) is an authorization system built on Azure Resource Manager that provides centralized access management of Azure resources. Azure RBAC allows users to manage keys, secrets, and certificates permissions, and provides one place to manage all permissions across all key vaults.
Which resource types located outside of Azure can be managed by Azure Arc? (Choose three.)
SQL Server, Kubernetes Clusters, Virtual Machines (preview)
Currently, Azure Arc manages the following resource types located outside of Azure:
Servers
Kubernetes Clusters
Azure Data Services
SQL Server
Virtual Machines (preview)
The following diagram outlines the ARM (Azure Resource Manager) architecture. Which service is the missing link between the resource group and the Azure resource manager?
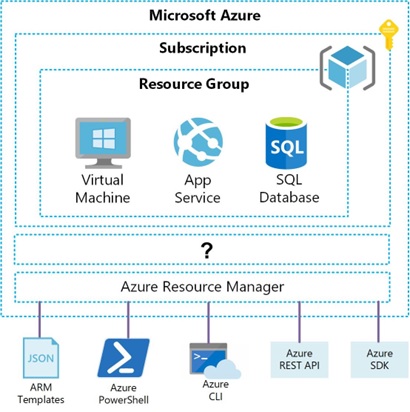
Resource providers
The main component of the logical architecture is the resource group. This is a logical container for grouping resources that typically share the same life cycle. The resource group can then be a target for applying access control and policies instead of individual resources. Resource providers are not logical, but the actual service contains and provides the Azure resources. Consider a book as a reading resource and the library as the provider. Resource providers act as an aggregator and provider of resources in a resource group.
How many declarative templates are submitted by the Azure Resource Manager template as opposed to non-declarative IAC (infrastructure-as-code)? Refer to the following exhibit.
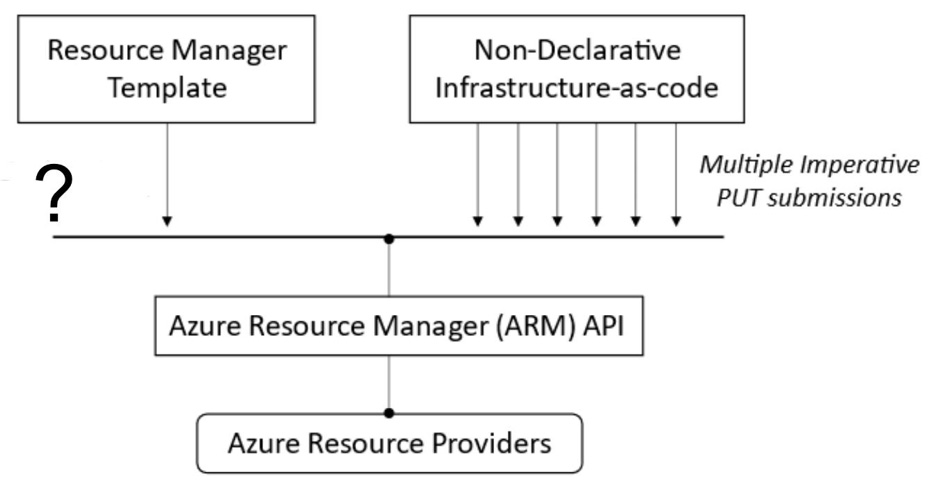
One declarative template
ARM templates are JSON files (a minimal, readable format for structuring data as an alternative to Extensible Markup Language) that define the configuration for resource deployment. These templates utilize a declarative syntax (as opposed to an imperative syntax), meaning that the user defines the desired outcome with all the resources they want created and any properties they wish specified in a single request. Instead of issuing multiple commands at each stage of the process to create each resource individually, and where there is no orchestration, a user must also consider dependencies and in which order commands are processed.
The code defined in an ARM template is converted to ___________ operations for the resource providers.
ARM API
ARM templates can be edited directly in the Azure portal with a simple text editor such as Notepad or Notepad++, or with something more advanced such as Visual Studio Code. Whatever is defined in the template is converted to ARM API operations for the resource providers.
Azure Advisor generates a list of which kind of recommendations established to notify users of aspects that are not implemented compared to things that are implemented?
VMs not protected by a Network Security Group (NSG)
Azure Advisor recommendations are based on the practice of notifying users of aspects that are not implemented rather than things that are implemented. For example, Azure Advisor will generate a list of the following:
VMs that are not protected by a Network Security Group (NSG).
VMs that do not have backups enabled, updates applied, and a premium SSD when capable.
Storage accounts that do not have soft delete enabled.
In which of the following circumstances does Azure Service Health issue health advisories far in advance to help administrators plan accordingly?
Service retirements and upgrade requirements
Service issues: Problems in the Azure services that affect you right now.
Planned maintenance: Upcoming maintenance that can affect the availability of your services in the future.
Health Advisories: Changes in Azure services that require your attention. Examples include deprecation of Azure features or upgrade requirements (e.g. upgrade to a supported PHP framework).
Service issues
Problems in the Azure services that affect you right now.
Planned maintenance
Upcoming maintenance that can affect the availability of your services in the future.
Health Advisories
Changes in Azure services that require your attention. Examples include deprecation of Azure features or upgrade requirements (e.g. upgrade to a supported PHP framework).
Azure Monitor collects resource and platform data from which of the following data sources? (Choose two.)
On-premises resources, IaaS resources, such as virtual desktops, containers, and VMs
Azure Monitor collects resources and platform data from the following data sources:
PaaS resources, such as applications and databases
IaaS resources, such as VMs, containers, virtual desktops, databases, and storage
On-premises resources
An administrator wants to set up alerts in Azure Service Health for triage outages and planned maintenance. She also wants Azure Service Health to generate incident reports that analyze the problems so that stakeholders can monitor and plan the events in advance. What type of official incident report can be shared with the stakeholders?
Root Cause Analyses
Administrators can configure alerts that assist in prioritizing outages and scheduled maintenance. Following an outage, Service Health provides authorized incident reports, known as Root Cause Analyses (RCAs), that can be shared with relevant parties. These RCAs offer comprehensive insights into the reasons behind the incidents, empowering administrators to keep stakeholders informed and facilitate effective decision-making.
Which Azure monitoring data source records the performance and consumption of a data source and shows the meters and counters being triggered?
Metrics
Azure Monitor consumes two fundamental types of data: logs and metrics. Metrics record a data source’s performance and consumption and represents the triggered meters and counters. Metrics can capture the utilization of CPU, memory, network bandwidth, or disk throughput. They are presented in chart format and use Service Metrics:
Which of the following are ways to provide control for the ports of a VM and allow connectivity from the internet on a chosen network port and protocol such as Remote Desktop Protocol (RDP) (3389), Secure Shell (SSH) (22), HyperText Transfer Protocol (HTTP) (80), or HTTP Secure (HTTPS) (443)? (Choose all that apply.)
Add a rule to a network security group (NSG), Add a rule to an Azure firewall, Add a rule to a third-party vendor's network virtual appliance (NVA)
To allow connectivity from the internet on a chosen network port, a rule must be added to NSG. For allowing the VM ports to get connectivity, ensure that a rule is added to the Azure firewall so that it will not block the port when it receives traffic. If any third-party NVAs are installed, rules should be added to ensure the VM ports get connectivity from the internet and the important protocols can function without any problem.
The Azure Traffic Manager is a high availability (HA) solution, not a security solution.