COMSEC Quiz 1: L1 (Midterms)
1/31
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
32 Terms
Define as protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction
information security
In a general sense, security means _____
protecting our assets
When securing an asset, system, or environment, we must also consider how the level of security relates to the _____
value of the item being secured
5 items which puts us in the state of being insecure
(1) Not patching our systems
(2) Using weak passwords
(3) Downloading programs from the Internet
(4) Opening e-mail attachments from unknown senders
(5) Using wireless networks without encryption
What does “CIA” triad stand for?
(1) Confidentiality
(2) Integrity
(3) Availability
Is confidentiality the same as privacy?
No. But its a similar concept
A necessary component of privacy and refers to our ability to protect our data from those who are not authorized to view it
A concept that may be implemented at many levels of a process
confidentiality
This can be compromised by the loss of a laptop containing data, a person looking over our shoulder while we type a password, an e-mail attachment being sent to the wrong person, an attacker penetrating our systems, or similar issues
confidentiality
The ability to prevent our data from being changed in an unauthorized or undesirable manner
integrity
This could mean the unauthorized change or deletion of our data or portions of our data, or it could mean an authorized, but undesirable, change or deletion of our data
integrity
The ability to access our data when we need it
availability
Such issues can result from power loss, operating system or application problems, network attacks, compromise of a system, or other problems
availability
Availability
When such issues are caused by an outside party, such as an attacker, they are commonly referred to as a _____
denial of service (DoS) attack
The result of mental activity; it is an intangible product that is transmitted through media
information
In the field of ICT, it is the result of processing, manipulating and organizing data, which is simply a collection of facts
information
In the field of Information Security, information is defined as an _____; it is something that has value and should therefore be protected
asset
Some exert effort to obtain information assets by whatever means
The latter include unauthorized access (1)_____, unauthorized use (2)_____ , destruction of information systems through computer viruses, and others
(1) hacking
(2) piracy
Provide the 4 negative aspects of information-oriented environments
(1) Increase in unethical behavior arising from anonymity
(2) Conflicts over ownership and control of information
(3) Information and wealth gaps between classes and countries
(4) Growing information exposure caused by advanced networks
Provide the 4 Rs of information security
(1) Right information
(2) Right people
(3) Right form
(4) Right time
Information security also requires a clear understanding of the value of information assets, as well as their vulnerabilities and corresponding threats. This is known as _____
risk management
Risk is determined by the (1)_____, (2)_____ and (3)_____
(1) asset value
(2) threats
(3) vulnerabilities
Provide the formula for risk
Risk = ∫(Asset Value, Threats, Vulnerabilities)
Risk is directly proportional to asset value, threats and vulnerabilities
This is done when the likelihood of threats/vulnerabilities is high, but their effect is low
risk reduction (risk mitigation)
It involves understanding what the threats and vulnerabilities are, altering or reducing them, and implementing a countermeasure
However, this does not reduce the value of risk to “0”
risk reduction (risk mitigation)
This is done when the likelihood of threats/vulnerabilities is low and their likely impact is minor or acceptable
risk acceptance
If the risk is excessively high or the organization is not able to prepare the necessary controls, the risk can be transferred outside of the organization. An example is taking out an insurance policy
risk transference
If the threats and vulnerabilities are highly likely to occur and the impact is also extremely high, it is best to avoid the risk by outsourcing data processing equipment and staff, for example
risk avoidance
Draw the graph on methods of risk management
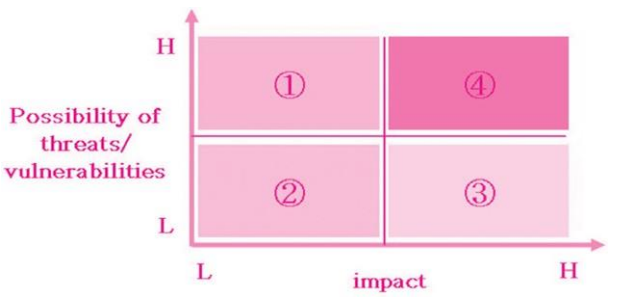
_____ protects all forms of information, digital and physical
Information security (InfoSec)
_____ protects all forms of digital information, including computers, handheld devices, cloud, and networks, and can be considered a subset of InfoSec
Cybersecurity
Cyber security is important because it encompasses everything that pertains to protecting our sensitive data, (1)_____, (2)_____, personal information, intellectual property, data, and governmental and industry information systems from theft and damage attempted by criminals and adversaries
(1) personally identifiable information (PII)
(2) protected health information (PHI)
Provide the 3 impacts of cybercrime
(1) economic costs
(2) reputational costs
(3) regulatory costs