Lecture 13 - Firewall and Malware
1/30
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
31 Terms
Intrusion
Any unauthorized activity on a computer network
types of intruders
Casual, hackers, professionals, employees
Casual Intruders
limited knowledge, use hacking tools
Hackers
Usually for status or hobby, crackers cause damage
Professionals
corporate/international espionage, theft of information or assets
Employees
legitimate access to network, unauthorized information
Firewall
Router or special purpose device that examines packets flowing into and out of a network and restricts access to the organization’s network
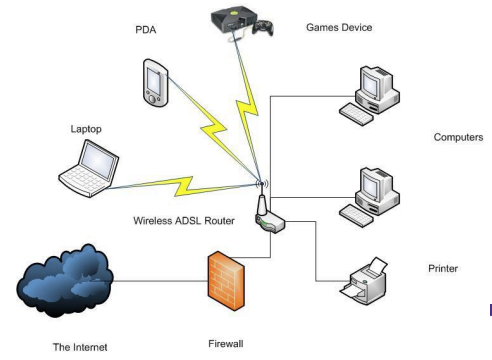
Where are firewalls placed
On every network connection between the organization and the internet
no access permitted expect through firewall
3 Type of firewalls
Packet level, application level, network address translation (NAT)\
Packet Level Firewall
Examines IP addresses (Source and destination)
examines TCP port ID
will permit packet if satisfy certain conditions (IP address and port number)
protect all applications
cheapest, like family doctor (protecting everything)
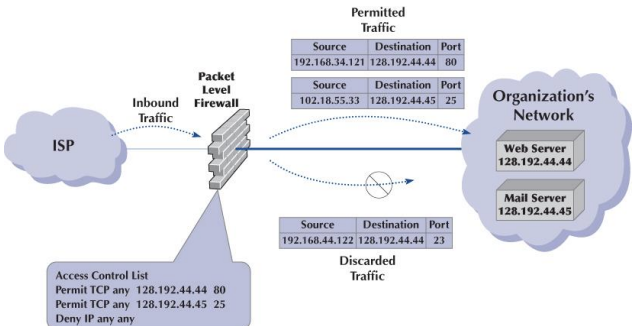
downside to packet level firewall
Simplest, least secure, logic independent of other packets
Application-level firewall
monitors connections, uses rules to determine what client may do (no executable files, no changes to files)
performs checks against know security holes of each application
specialist
Security holes
a bug that permits unauthorized access
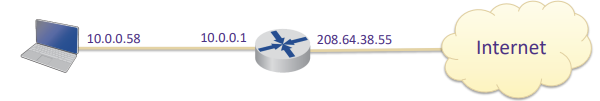
Network Address Translation (NAT) Firewall
Transparent process
hides internal IP address, assigns public address (PO Box)
sometimes used to conserve IP addresses
uses address table relating to ‘port number’ to internal computer
like post office
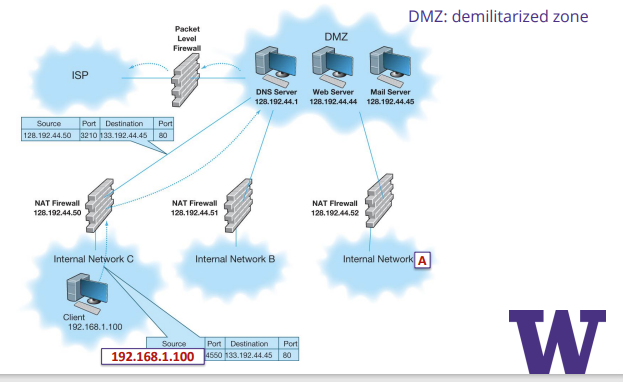
Firewall Architecture
many organization use layers of NAT, Packet level, and application-level firewalls
Network design using firewalls example
Malware (malicious software)
any program or file that is harmful to a computer user
types of malware
computer viruses, worms, trojan horses, and spyware
Virus
malicious code that replicates by copying itself to another program, computer boot sector or document and changes how a computer works
How does Virus spread
With human interaction
requires someone to knowingly or unknowingly spread the infection without the knowledge or permission of a user or system administrator
How does a virus infect
only if someone runs the exe file
Worm
special type of virus that spreads itself without human intervention
sub class of virus
How do worms spread
without human intervention
copies itself from computer to computer
sending copies of themselves via emails or security holes
end result of worms
worm consumes too much system memory (or network bandwidth) causing the servers to stop responding
Trojan Horses
poses as a useful software, once ran will damage
remote access management consoles (rootkits) that enable users to access a computer and manage it from afar
Lasting effects of trojan horses
silly things like random picture
to deleting files
and will create backdoor for bad guy
Do Trojan horses spread
no they cannot infect other files or self-replicate
Spyware
Software that aims to gather information about a person or organization
Ransomware
type of malware designed to deny access to a computer system or data until a ransom is paid
how is ransomware spread
through phishing emails or unknowingly visiting an infected website
How to prevent malware
use security (antivirus) software
keep you security software up to date
update your OS and other software
be wary of email attachments
back up important data to external hard drive