SHS_ETECH | Q1 EXAMINATIONS REVIEWER
1/269
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
270 Terms
Information and Communications Technology (ICT)
Refers to all technology that is used to handle telecommunication and access information.
Wireless Fidelity (WiFi)
Technology for radio wireless local area networking of devices based on the IEEE 802.11 standards.
Bluetooth
Wireless technology standard for exchanging data over short distances from fixed and mobile devices, and building personal area networks (PANs).
Infrared Radiation Wireless (IR)
The use of wireless technology in devices or systems that convey data through infrared (IR) radiation.
4G
Generation of broadband cellular network technology, succeeding 3G. Potential and current applications include amended mobile web access, IP telephony, gaming services, high-definition mobile TV, video conferencing, and 3D television.
5G
Next great leap in speed for wireless devices. This speed includes both the rate mobile users can download data to their devices and the latency, or lag, they experience between sending and receiving information.
GSM
A standard developed by the European Telecommunications Standards Institute (ETSI) to describe the protocols for second-generation digital cellular networks used by mobile devices such as tablets.
GPRS
Packet oriented mobile data standard on the 2G and 3G cellular communication network's global system for mobile communications (GSM). Data Services – data networking services for mobile phones.
Dial-up Services
Data networking services using modems and telephone lines.
Virtual Private Networks (VPN)
Extends across a public or shared network, and acts like a tunnel so you can exchange data securely and anonymously across the internet as if you were connected directly to a private network.
Wireless Access Point
Allows wireless devices to connect to the wireless network.
WIreless router
Hardware devices that Internet service providers use to connect you to their cable or xDSL Internet network.
Mobile Hotspot
A common feature on smartphones with both tethered and untethered connections.
Portable Wi-Fi hotspot
A small device that uses cellular towers that broadcast high-speed 3G or 4G broadband signals.
Data Services
A service provider that enables data access on demand to users regardless of their geographic location.
1G - First Generation
Generation of commercial cellular network was introduced in the late 70's with fully implemented standards being established throughout the 80's.
2G - Second Generation
Main motive of this generation was to provide secure and reliable communication channel.
3G - Third Generation
Web browsing, email, video downloading, picture sharing and other Smartphone technology were introduced in this generation.
4G - Fourth Generation
This generation’s purpose is to provide high speed, high quality and high capacity to users while improving security and lower the cost of voice and data services, multimedia and internet over IP.
Artificial Intelligence
It is an area of computer science that emphasizes the creation of intelligent machines that work and react like humans.
Robotics
It is the field of computer science and engineering concerned with creating devices that can move and react to sensory input.
Biometrics
the technology used to measure and analyze human body characteristics such as DNA, fingerprints, eye retinas and irises, voice patterns, facial patterns, and hand measurements, mainly for authentication purposes.
Quantum computing
It is an area of computing focused on developing computer technology based on the principles of quantum theory.
Quantum Cryptography
It is the science of encoding and decoding information or messages which depends on physics, not mathematics.
Cryptocurrencies
Are digital currencies (or tokens), like Bitcoin, Ethereum or Litecoin, that can be used to buy goods and services
Blockchain
Is a decentralized and distributed digital ledger technology that records transactions in a secure and irreversible manner.
Computer-Assisted Translation (CAT)
Is the use of computers to assist in the translation of one or more natural languages into another or others, and vice-versa.
3D Imaging and Holography
Is a photographic technique that uses light to project objects in a way that appears threedimensional
Virtual Reality
Is the term used to describe a three-dimensional, computer-generated environment that can be explored and interacted with a person.
Platform
defined as a group of technologies that are used as a base upon which other applications, processes, or technologies are developed.
Social Media
It is a web-based technology that allows the development, deployment, and management of social media solutions and services.
E-Commerce and M-Commerce
Is a collection of software technologies that allows merchants to create a storefront on the Internet while m-commerce transacts business entirely on mobile technologies.
Online Learning
It is an incorporated set of interactive online services that provide teachers, learners, parents, and others involved in the education sector with a wide range of tools and resources to support and enhance the delivery and management of education through the Internet.
Content Sharing Platform
It is a service-providing website where users can upload, share, and discover various types of content, such as videos (YouTube), images (Pinterest), and articles/blogs (Medium).
Communication Platforms
These platforms provide tools for real-time communication, such as instant messaging (WhatsApp, Messenger, Slack), video conferencing (Zoom), and email services.
Gaming Platforms
These are online digital platforms that offer video games and allow players to connect, compete, and collaborate with others online. Examples include Steam, Xbox Live, PlayStation Network, and mobile app stores.
Financial Platforms
Online platforms that provide financial services like banking, payment processing, investing, and crowdfunding. Examples include GCash, PayPal, and PayMaya.
Digital awareness
Refers to the understanding, knowledge, and consciousness of the digital world,including its technologies, opportunities, risks, and impact on individuals and society
Online ethics
Focuses on the acceptable use of online resources in an online environment.
Netiquette
focuses on the acceptable behavior of the person while using the internet resource.
Online safety and security
define how you are going to keep yourself safe while surfing the web andwhen using these technologies.
Data Privacy Act
is a law that seeks to protect all forms of information, be it private,personal, or sensitive. It is meant to cover both natural and juridical persons involved inthe processing of personal information
The limits of presumed freedom of expression
Freedom of expression is not an absolute right and can be subjected to restrictions.
Issues of libel
Defamation involves writing or saying something about someone that damages thatperson’s reputation.
Copyright Law
a part of a law, wherein you have the right/s to your work, and anyone who uses itwithout your consent is punishable by law.
intellectual property
an idea, an invention, a form of literary work, or research, you have theright to how it should be used by others.
trademark
is often used in a general sense to refer to both trademarks andservice marks.
TRUE OR FALSE:
Unlike patents and copyrights, trademarks do not expire after a set term ofyears.
TRUE
Patent
Is an exclusive right granted for an invention, which is a product or a process thatprovides, in general, a new way of doing something, or offers a new technical solution to aproblem.
Fair Use
means that intellectual property may be used without consent as long as it is usedin commentaries, criticisms, search engines, parodies, news reports, research, libraryarchiving, teaching, and education.
Internet Threats
a category of cybersecurity risks that may cause an undesirableevent or action via the internet. Regardless of intent or cause, the consequences of a web threat maydamage both individuals and organizations
Malware
It is a code or software that isspecifically designed to damage, disrupt, steal, or in general inflict some other “bad” or illegitimateaction on data, hosts, or networks
Viruses
a type of malware that often take the form of a piece of code inserted in anapplication, program, or system and they’re deployed by victims themselves.
Worms
a type of malware that replicates itself. can copy itself without any human interaction, and it’s not host-dependent, meaning it does not need to attach itself to a software program to cause damage
Trojans
a type of malware disguised as bona fide software, applications, or files to deceiveusers into downloading it and, unknowingly, granting control of their devices.
Ransomware
Is a type of malware that comes with a ransom. It locks andencrypts a victim’s device or data and demands a ransom to restore access.
Bots
meaning a program that crawls the internet looking for holesin security infrastructures to exploit, and the hacking is done automatically — or robotically if youwill.
Adware
Also known as advertising-supported software, adware displays unwanted advertisements on your computer, sometimes inthe form of pop-up ads that track users’ browsing activity.
Spyware
a type of malware that infiltrates devices without the owner’s knowledge. This is oftenfor the purpose of spying on internet activity, tracking log in and password information, orcollecting sensitive information that can be used for fraudulent purposes.
Spamming
is the use of electronic messaging systems like e-mails and other digital delivery systemsand broadcast media to send unwanted bulk messages indiscriminately.
Phishing
It is identity theft that generally targets users with the aim to con them into revealing their personaland confidential information.
Pharming
t is a complicated form of phishing. A user can fall victim to pharming even on clicking on an authenticlink if the website’s domain name system (DNS) has been hijacked by a hacker.
Internet Security
a branch of computer security specifically related to the Internet, often involvingbrowser security but also network security on a more general level as it applies to other applicationsor operating systems as a whole.
Internet Security
Its objective is to establish rules and measures to use against attacksover the Internet.
Internet Safety
Includes knowing about one’s internet privacy and how one’s behaviorcan support a healthy interaction with the use of the internet” together with the existing applicationstechnological device
Digital Citizenship
the ability to navigate our digital environments in a way that's safe andresponsible and to actively and respectfully engage in these spaces.
Word Processing
refers to the production, storage, and manipulation of text on a computer or wordprocessor.
Word Processor
Is an electronic device or computer software application, that performs thetask of composing, editing, formatting, and printing of documents.
Microsoft Word
word processor developed by Microsoft. It was first released on October 25, 1983 under the name Multi-tool Word for Xenix systems
Quick Access Toolbar
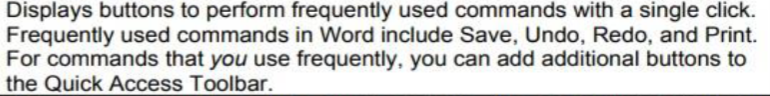
Ribbon

File Tab

Tabs

group name

Dialogue Box Launcher

Insertion Point

Word Document Window

Status Bar

Print Layout Button

View Options

Zoom Slider

Vertical Scroll Bar

Scroll Box

Program Level Control Buttons

Title Bar

Pictures
MICROSOFT WORD MATERIALS:
Generally, these are electronic or digital pictures or photographs you have saved in anylocal storage device.
TRUE
True or False: .GIF is capable of displaying simple animation and can support 256 colors.
FALSE
True or False: .PNG supports animation and is known for its compressible size.
TRUE
True or False: .TIFF is mainly used by professional designers and photographers for illustrations and observations.
FALSE
True or False: .SVG is famous for having a higher quality image but is not resizable without loss of quality.
TRUE
True or False: .RAW images are minimally processed data from the image sensor.
TRUE
True or False: .PSD is the output image type for editing in Adobe Photoshop and produces higher quality images.
c. .PNG
Which image file type supports transparency?
a. .JPG
b. .GIF
c. .PNG
d. .TIFF
b. .GIF
Which image file type can display simple animation?
a. .JPG
b. .GIF
c. .PNG
d. .TIF
a. .JPG
Which image file type is known for having a compressible size?
a. .JPG
b. .GIF
c. .PNG
d. .TIFF
d. .TIFF
Which image file type is mainly used by professional designers and photographers for illustrations and observations?
a. .JPG
b. .GIF
c. .PNG
d. .TIFF
d. .SVG
Which image file type can be resized without loss of quality?
a. .JPG
b. .GIF
c. .PNG
d. .SVG
True
True or False: Desktop publishing (DTP) software is designed for creating visual communications such as brochures, business cards, and web pages.
False
True or False: Adobe Illustrator is primarily used for post-production in film making and motion graphics.
True
True or False: Adobe Photoshop is used for photo editing, artworks, and bitmap graphics.