3.0 CompTIA Security+ SY0-701 Security Architecture
1/140
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
141 Terms
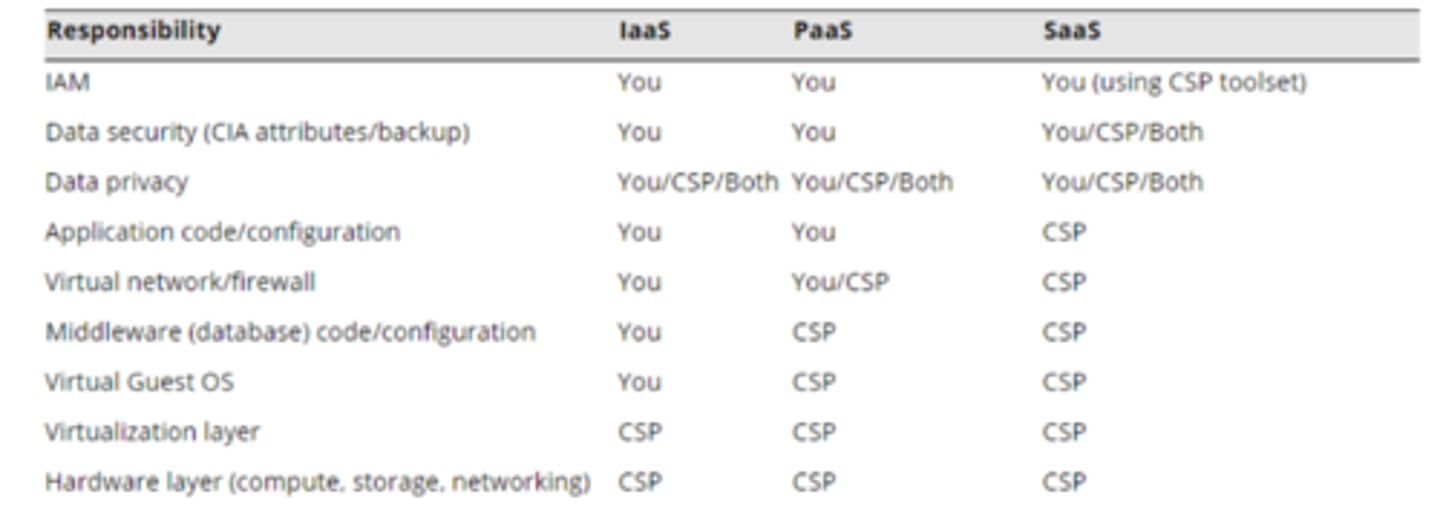
cloud responsibility matrix
Documentation listing which security and management tasks are the responsibility of the cloud provider and which are the responsibility of the cloud consumer.
IaaS, PaaS, SaaS, etc.
-Who is responsible for security?
Security should be well-documented
-Most cloud providers provide a matrix of responsibilities
-Everyone knows up front
These responsibilities can vary
-Different cloud providers
-Contractual agreements
Hybrid considerations
Hybrid cloud
-More than one public or private cloud
-This adds additional complexity
Network protection mismatches
-Authentication across platforms
-Firewall configurations
-Server settings
Different security monitoring
-Logs are diverse and cloud-specific
Data leakage
-Data is shared across the public Internet
Third-party vendors in the cloud
You, the cloud provider, and third parties
-Infrastructure technologies
-Cloud-based appliances
Ongoing vendor risk assessments
-Part of an overall vendor risk management policy
Include third-party impact for incident response
-Everyone is part of the process
Constant monitoring
-Watch for changes in unusual activity
Infrastructure as code (IaC)
Describe an infrastructure
-Define servers, networks, and applications as code
Modify the infrastructure and create versions
-The same way you version the application code
Use the description (code) to build other application instances
-Build it the same way every time based on the code
An important concept for cloud computing
-Build a perfect version every time
Serverless Architecture (FaaS)
Function as a Service (FaaS)
-Applications are separated into individual, autonomous functions
-Remove the operating system from the equation
Developer still crates the server-side logic
-Runs in a stateless compute container
It may be event-triggered and ephemeral
-May only run for one event
Managed by a third-party
-All OS security concerns are at the third-party
Microservices and APIs
Monolithic applications
-One big application that does everything
The application contains all decision-making processes
-User interface
-Business logic
-Data input and output
Code challenges
-Large codebase
-Change control challenges
Application Programming Interfaces (API)
API is the "glue" for the microservices
-Work together to act as the application
Scalable
-Scale just the microservices you need
Resilient
-Outages are contained
Security and Compliance
-Containment is built-in
Network infrastructure
Physical isolation
-Air-gapped
Logical segmentation
Software-defined networking (SDN)
Physical isolation
Devices are physically separate
-The air gap between Switch A and Switch B
Must be connected to provide communication
-Direct connect, or another switch or router
Web servers in one rack
-Database servers on another
Customer A on one switch, customer B on another
-No opportunity for mixing data
Physical segmentation
Separate devices
-Multiple units, separate infrastructure

Logical Segmentation with VLANs
Virtual Local Area Networks (VLANs)
-Separated logically instead of physically
-Cannot communicate between VLANs without a layer three device/ routers
Software Defined Networking (SDN)
Networking devices have different functional planes of operation
-Data, control, and management planes
Split the functions into separate logical units.
-Extend the functionality and management of a single device
-Perfectly built for the cloud
Infrastructure layer/ Data plane
-Process the network frames and packets
-Forwarding, trunking, encrypting, NAT
Control layer/ control plane
-Manages the actions of the data plane
-Routing tables, session tables, NAT tables
-Dynamic routing protocol updates
Application layer/ Management plane
-Configure and manage the device
-SSH, browser, API
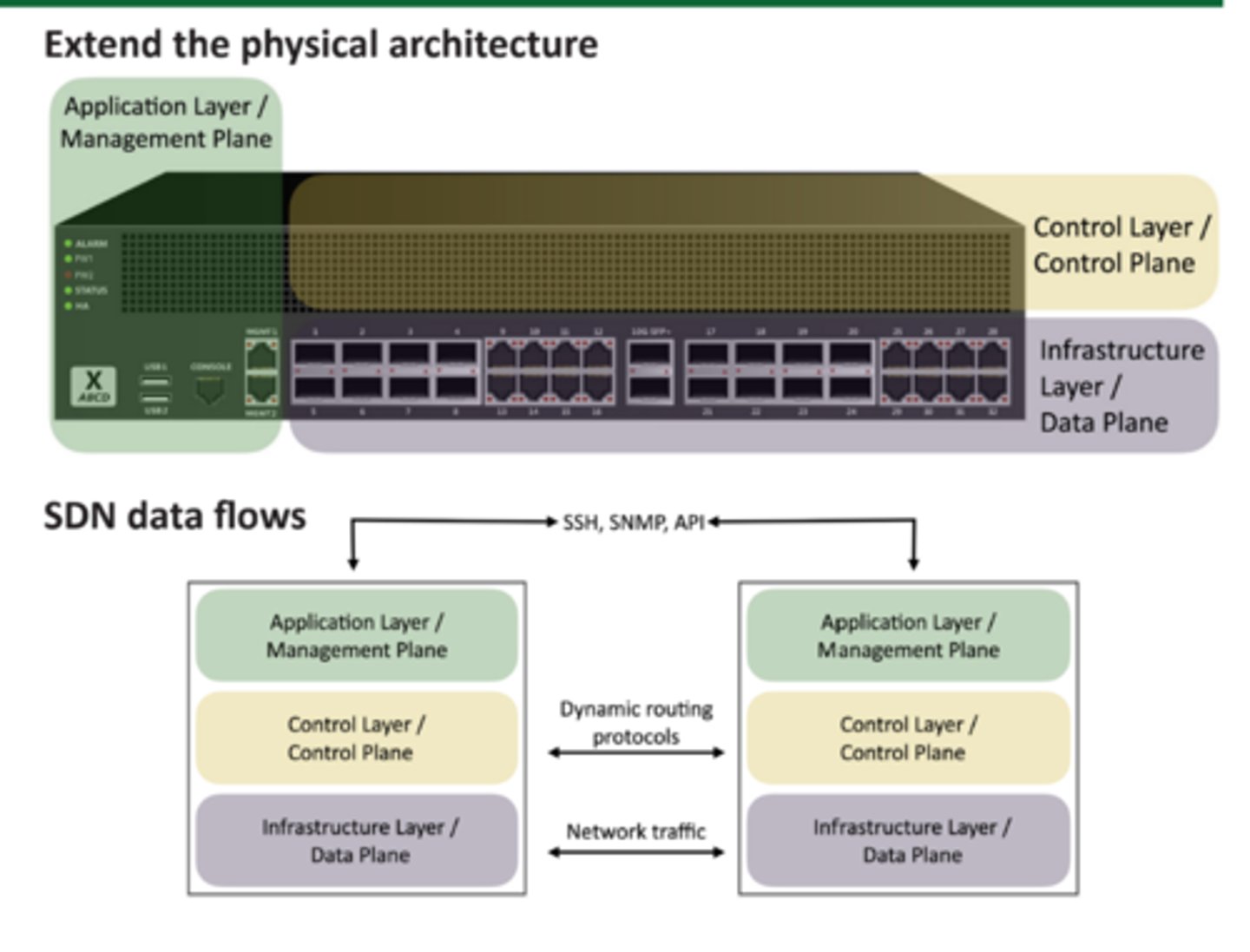
SDN data flows
SDN Security
Due to SDN's plane separation, security must be implemented for each interface. After designing the SDN architecture, security methods should be considered. The chosen security solution must be secure, scalable, and efficient
On-premises security
Customize your security posture
-Full control when everything is in-house
On-site IT team can manage security better
-The local team can ensure everything is secure
-A local team can be expensive and difficult to staff
The local team maintains uptime and availability
-System checks can occur at any time
-No phone call for support
Security changes can take time
-New equipment, configurations, and additional costs
Centralized vs. Decentralized
Authority can either be focused at the top levels, or it can be delegated to lower-level staff
Most organizations are physically decentralized
-Many locations, cloud providers, operating systems, etc.
It is challenging to manage and protect so many diverse systems
-Centralize the security management
A centralized approach
-Correlated alerts
-Consolidated log file analysis
-Comprehensive system status and maintenance/ patching
It is not perfect
-Single point of failure, potential performance issues
Application containerization
Container
-Contains everything you need to run an application
-Code and dependencies
-A standardized unit of software
An isolated process in a sandbox
-Self-Contained
-Apps can not interact with each other
Container image
-A standard for portability
-Lightweight, uses the host kernel
-Secure separation between applications
Virtualization
Virtualization
-Run many different operating systems on the same hardware
Each application instance has its operating system
-Adds overhead and complexity
-Virtualization is relatively expensive
Internet of Things (IoT)
The idea is that objects are becoming connected to the Internet so they can interact with other devices, applications, or services.
Sensors
-Heating and cooling, lighting
Smart devices
-Home automation, video doorbells
Wearable technology
-Watches, health monitors
Facility automation
-Temperature, air quality, lighting
Weak defaults
-IoT manufacturers are not security professionals
SCADA/ICS
Supervisory Control and Data Acquisition System
-Large-scale, multi-site Industrial Control Systems (ICS)
PC manages equipment
-Power generation, refining, manufacturing equipment
-Facilities, industrial, energy, logistics
Distributed control systems
-Real-time information
-System control
Requires extensive segmentation
-No access from the outside
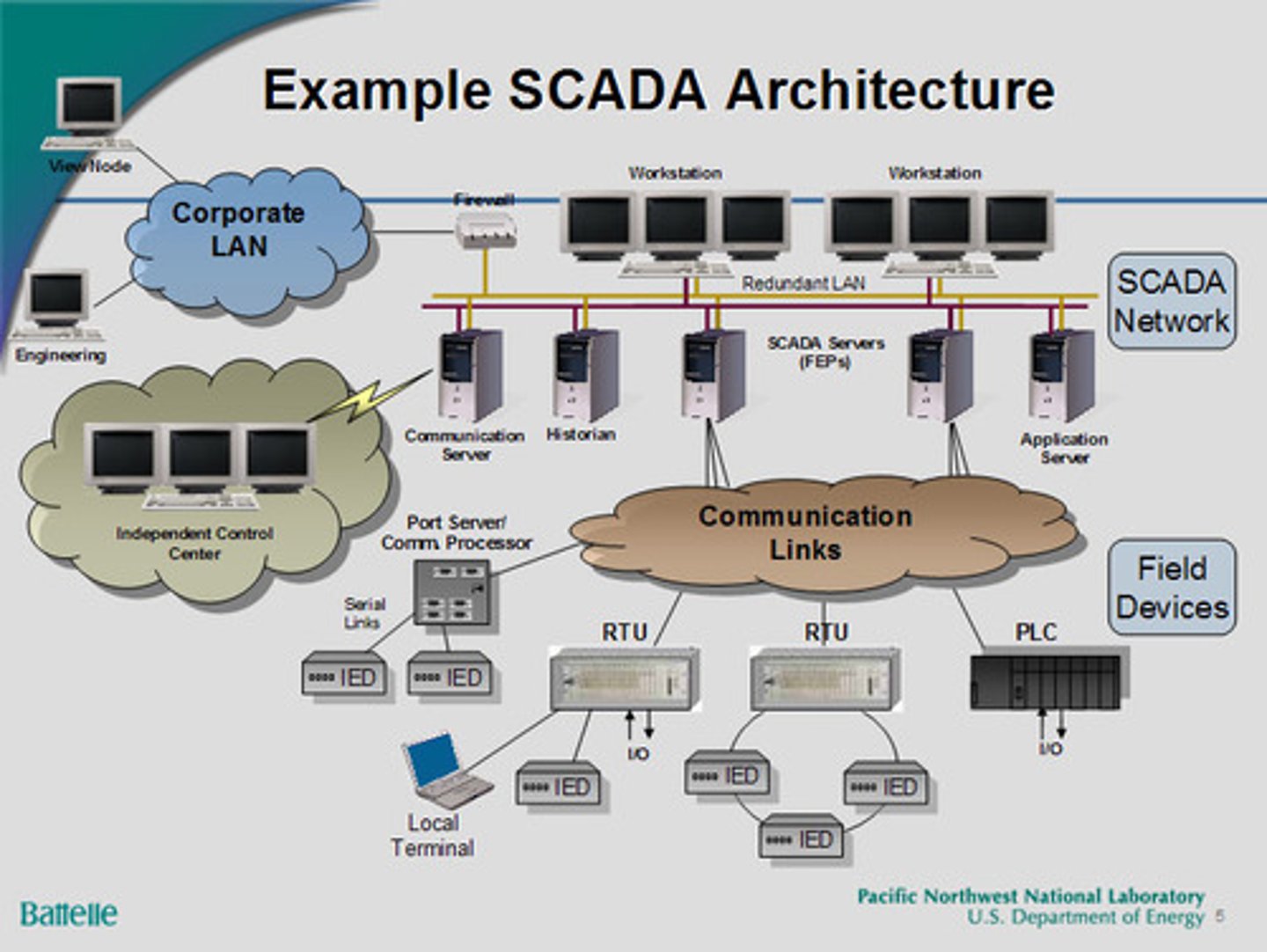
Industrial Control Systems (ICS)
Used to control industrial processes such as manufacturing, product handling, production, and distribution.
Supervisory Control and Data Acquisition (SCADA)
A network that includes software, servers, and communication channels. SCADA is responsible for acquiring real-time data from a physical system and managing the physical system or presenting the data to humans, who monitor and manage the system.
Real-Time Operating System (RTOS)
An operating system with a deterministic processing schedule
-No time to wait for other processes
-Industrial equipment, automobiles
-Military environments
Extremely sensitive to security issues
-Non-trivial systems
-Need to always be available
-Difficult to know what type of security is in place
Embedded systems
Hardware and software designed for a specific function
-Operate as part of a larger system
It is built with only this task in mind
-Can be optimized for size and/or cost
Common examples
-Traffic light controllers
-Digital watches
-Medical imaging systems
High availability
Redundancy does not always mean available
-May need to be powered on manually
HA (high availability)
-Always on, always available
May include different components working together
-Active/Active can provide scalability advantages
Higher availability almost always means higher costs
-There's always another contingency you could add
-Upgraded power, high-quality server components, etc.
Availability
System uptime
-Access data, complete transactions
-A foundation of IT security
A balancing act with security
-Available, but only to the right people
We spend a lot of time and money on availability
-Monitoring, redundant systems
An important metric
-We are often evaluated on total available time
Resilience
Eventually, something will happen
-Can you maintain availability
Can you recover? How quickly?
Based on many different variables
-The root cause
-Replacement hardware installation
-Software patch availability
-Redundant systems
Commonly referenced as MTTR
-Mean Time to Repair
Cost
How much money is required?
-Everything ultimately comes down to cost
Initial installation
-Very different across platforms
Ongoing maintenance
-Annual ongoing cost
Replacement or repair costs
-You might need more than one
Tax implications
-Operating or capital expense
Responsiveness
Request information
-Get a response
-How quickly did that happen?
Especially important for interactive applications
-Humans are sensitive to delays
Speed is an important metric
-All parts of the application contribute
-There is always a weakest link
Scalability
How quickly and easily can we increase or decrease capacity?
-This might happen many times a day
-Elasticity
There is always a resource challenge
-What is preventing scalability?
Needs to include security monitoring
-Increases and decreases as the system scales
Ease of deployment
An application has many moving parts
-Web server, database, caching server, firewall, etc
This might be an involved process
-Hardware resources, cloud budgets, change control
This might be very simple
-Orchestration/ automation
It is crucial to consider during the product engineering phase
-One missed detail can cause deployment issues
Risk transference
Many methods to minimize risk
-Transfer the risk to a third-party
Cybersecurity insurance
-Attacks and downtime can be covered
-Popular with the rise in ransomware
Recover internal losses
-Outages and business downtime
Protect against legal issues from customers
-Limit the costs associated with legal proceedings
Easy of recovery
Something will eventually go wrong
-Time is money
-How easily can you recover?
Malware infection
-Reload operating system from original media - 1 hour
-Reload from corporate image - 10 minutes
Patch availability
Software is not usually static
-Bug fixes, security updates, etc.
This is often the first task after installation
-Make sure you are running the latest version
Most companies have regular updates
-Microsoft's monthly patch schedule
Some companies rarely patch
-This might be a significant concern
Inability to patch
What if patching was not an option?
-This happens more often than you might think
Embedded systems
-HVAC controls
-Time clocks
Not designed for end-user updates
-This is a bit short-sighted
-Especially these days
May need additional security controls
-A firewall for your time clock
power
A foundational element
-This can require extensive engineering
Overall power requirements
-Data center vs. office building
Primary power
-One or more providers
Backup services
-UPS (Uninterruptible Power Supply)
-Generators
Compute
An application's heavy-lifting
-More than just a single CPU
The compute engine
-More options available in the cloud
It may be limited to a single processor
-Easier to develop
Use multiple CPUs across multiple clouds
-Additional complexity
-Enhanced scalability
Device Placement
Every network is different
-There are often similarities
Firewalls
-Separate trusted from untrusted
=Provide additional security checks
Other services may require their security technologies
-Honeypots, jump server, load balancers, sensors
Security zones
Zone-based security technologies
-More flexible (and secure) than IP address ranges
Each area of the network is associated with a zone
-Trusted, untrusted
-Internal, external
-Inside, Internet, Servers, Databases, Screened
This simplifies security policies
-Trusted to Untrusted
-Untrusted to Screened
-Untrusted to Trusted
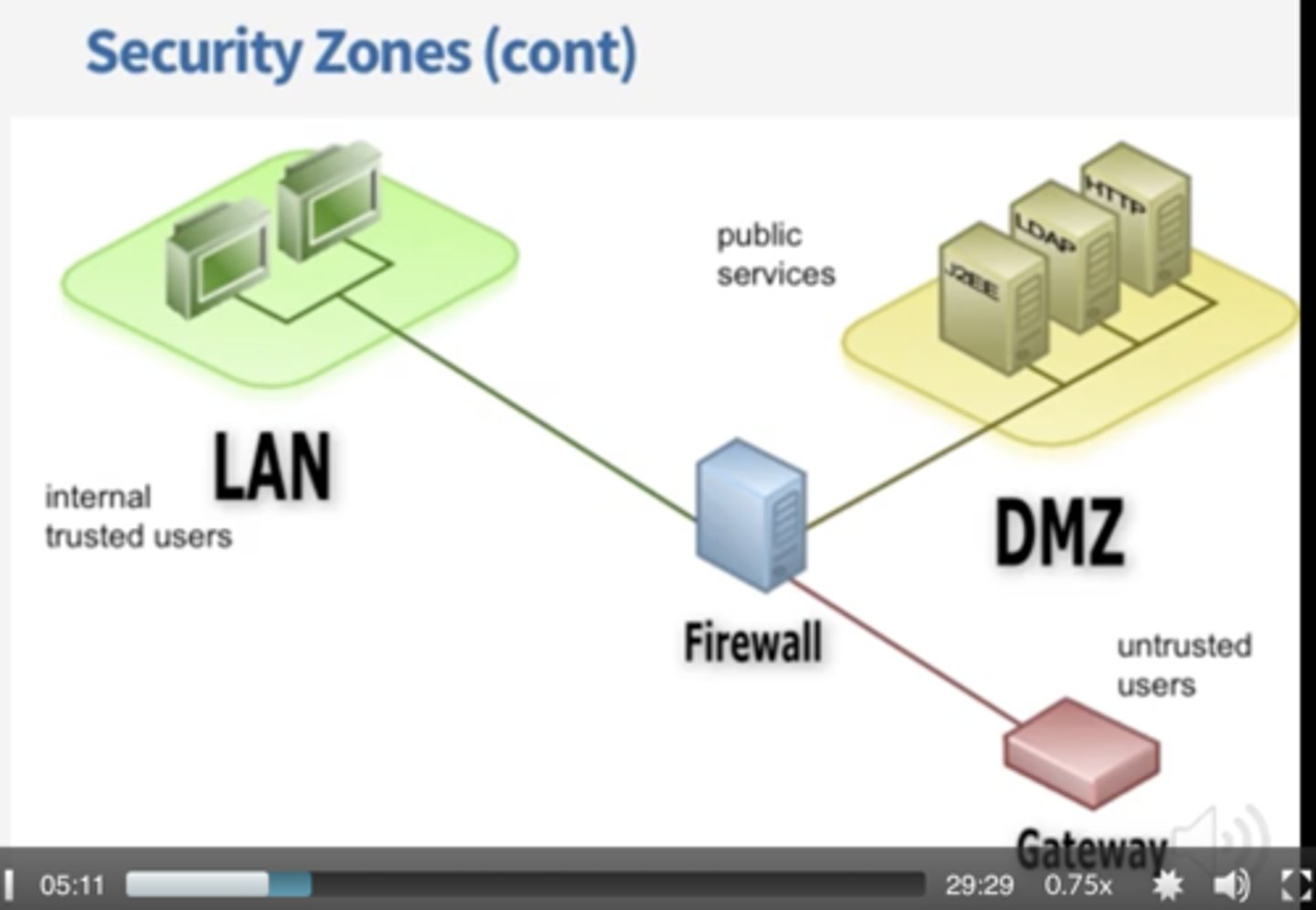
Attack surface
How many ways into your home?
-Doors, windows, basements
Everything can be a vulnerability
-Application code
-Open ports
-Authentication process
-Human error
Minimize the surface
-Audit the code
-Block ports on the firewall
-Monitor network traffic in real-time
Connectivity
Everything contributes to security
-Including the network connection
Secure network cabling
-Protect the physical drops
Application-level encryption
-The hard work has already been done
Network-level encryption
-IPsec tunnels, VPN connections
Failure Modes
We hope for 100% uptime
-This is not realistic
-Eventually, something will break
Fail-open
When a system fails, data continues to flow
Fail-closed
-When a system fails, data does not flow
Device connections
Active monitoring
-System is connected inline
-Data can be blocked in real-time as it passes by
-Intrusion prevention is commonly active
Passive monitoring
-A copy of the network traffic is examined using a tap or port monitor
-Data cannot be blocked in real-time
-Intrusion detection is commonly passive
Active monitoring
IDS/IPS sits physically inline
-All traffic passes through the IDS/IPS
Malicious traffic is immediately identified
-Dropped at the IPS
-Does not proceed through the network
Internet -> Firewall -> IPS -> Core Switch
Passive monitoring
Examine a copy of the traffic
-Port mirror (SPAN), network tap
No way to block (prevent) traffic
-Common with Intrusion Detection Systems
IPS -> Switch -> Server, Clients
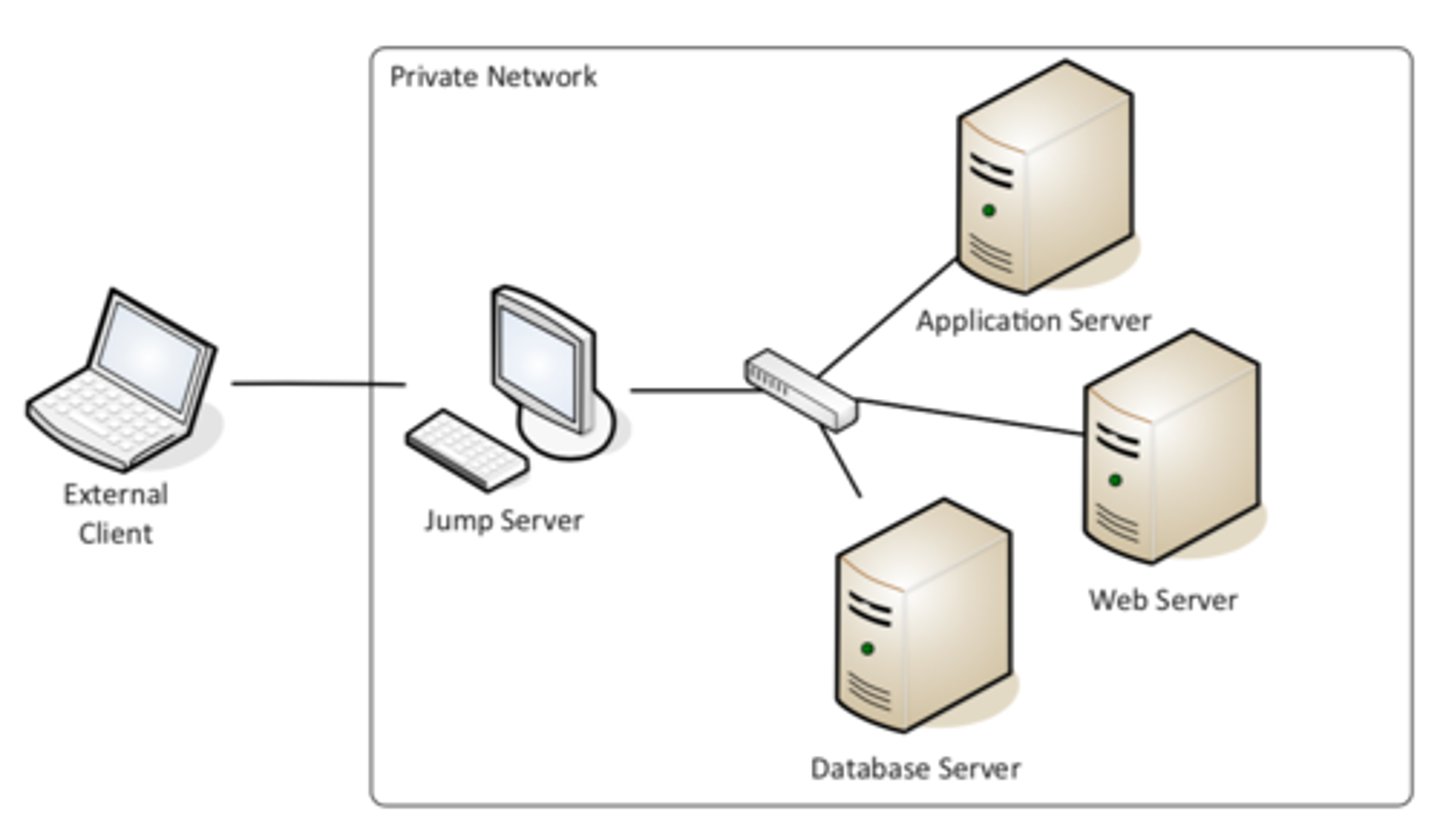
Jump server
Access secure network zones
-Provides an access mechanism to a protected network
Highly-secured device
-Hardened and monitored
SSH/Tunnel/ VPN to the jump server
- RDP, SSH or jump from there
A significant security concern
-Compromise of the jump server is a significant breach
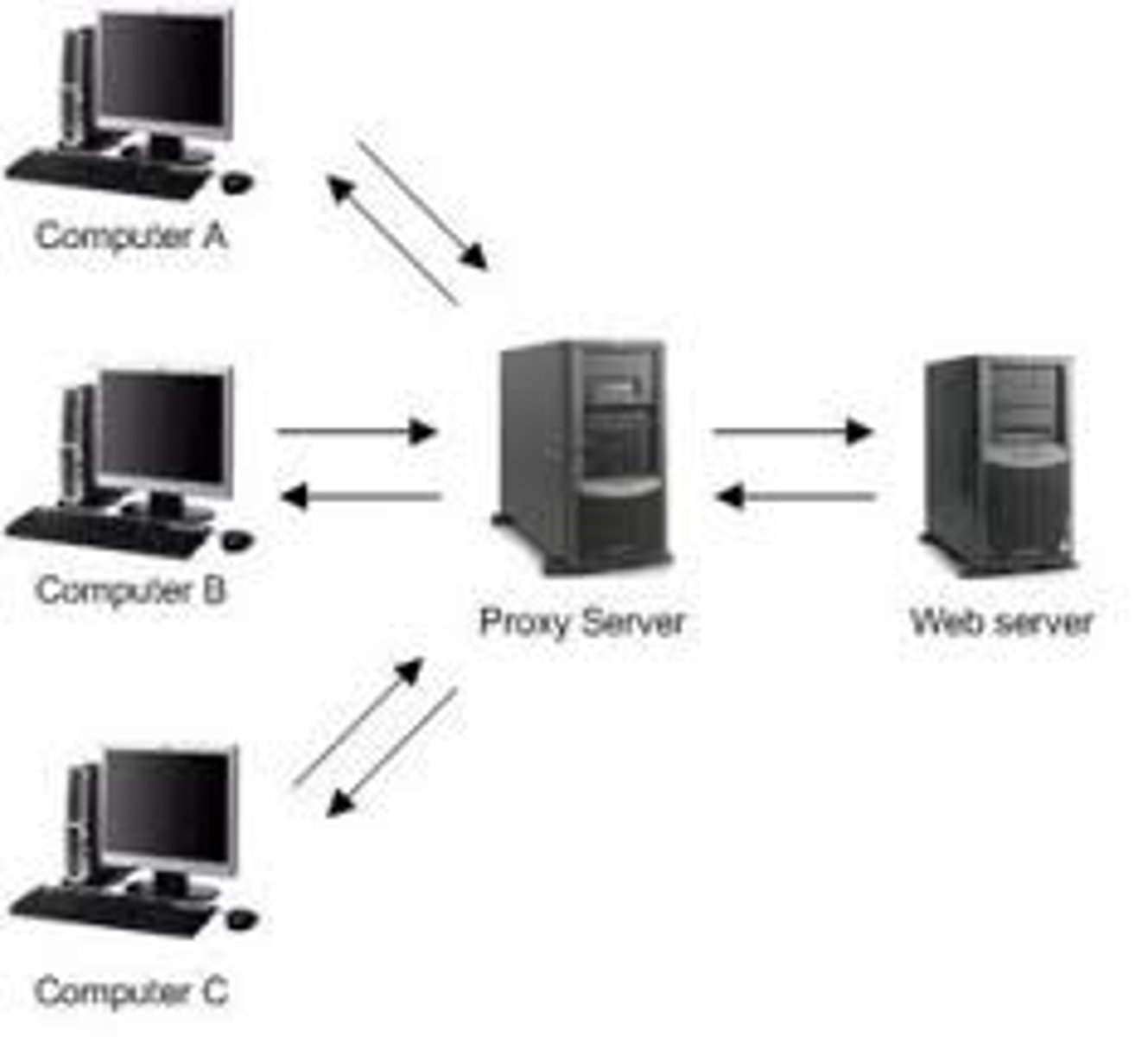
Proxies
Sits between the users and the external network
Receives the user request and sends the request on their behalf (the proxy)
Useful for caching information, access control, URL filtering, content scanning
Applications may need to know how to use the proxy (explicit)
Some proxies are invisible (transparent)
Application proxies
One of the simplest "proxies" is NAT
-A network-level proxy
Most proxies in use are application proxies
-The proxy understands the way the application works
A proxy may only know one application
-HTTP
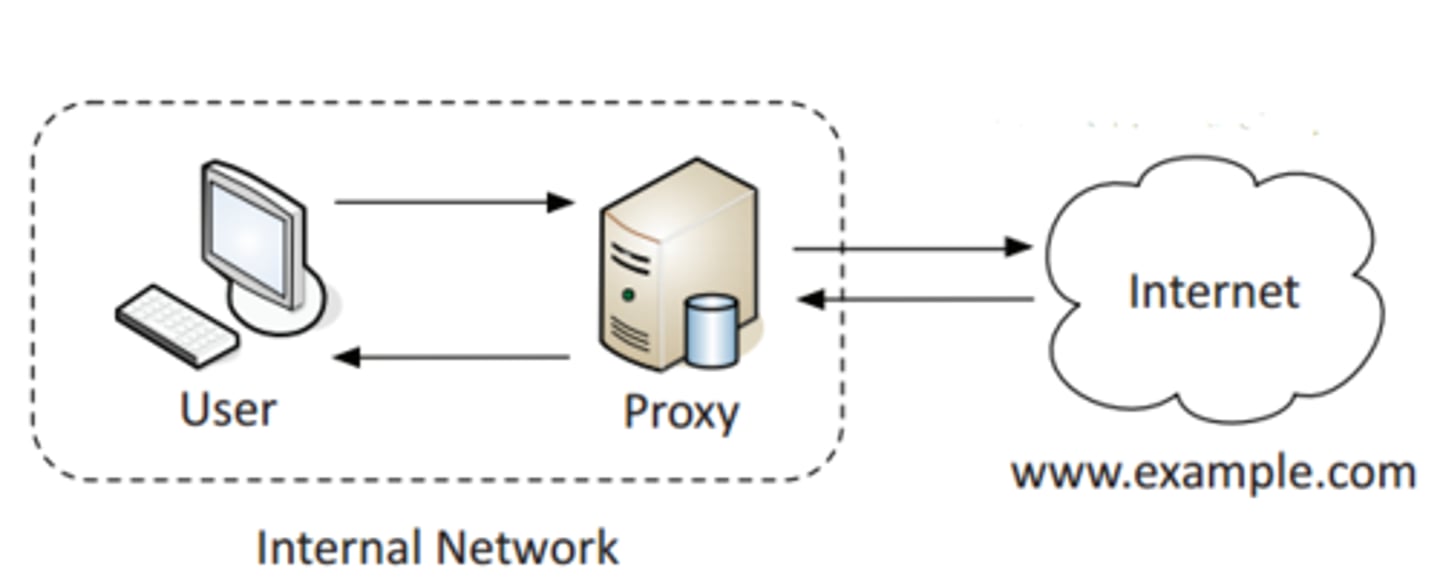
Forward proxy
An "internal proxy."
-Commonly used to protect and control user access to the internet
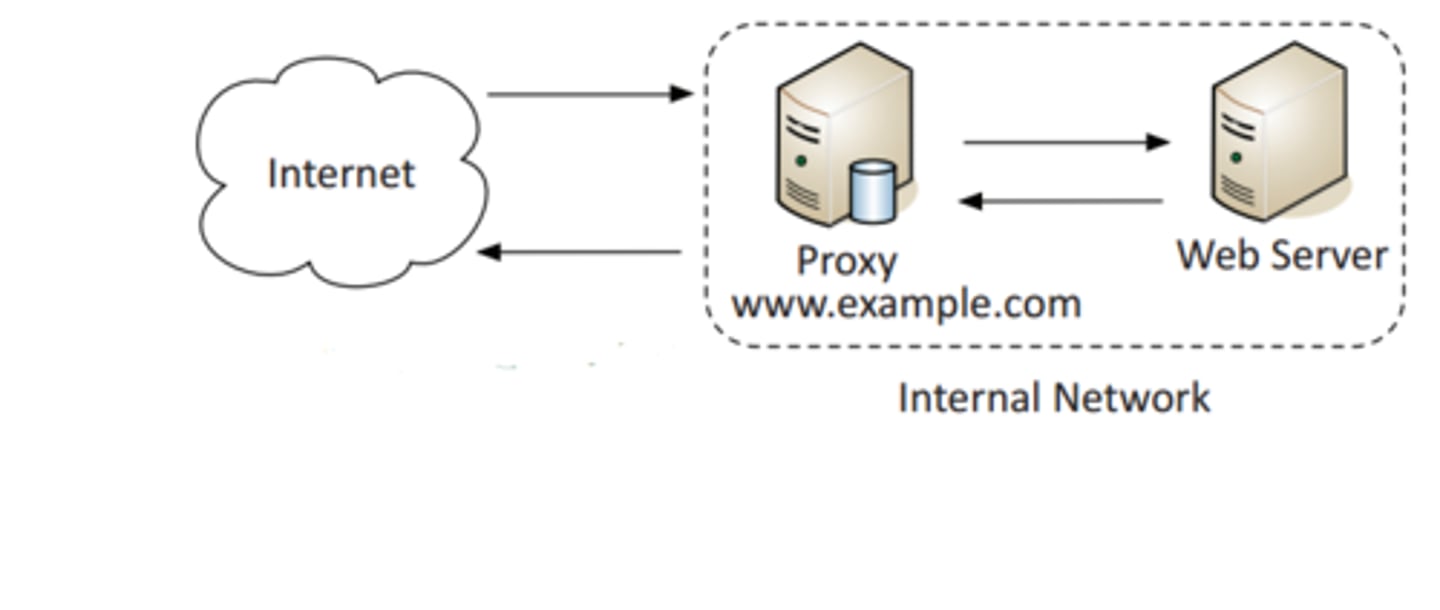
Reverse proxy
Inbound traffic from the internet to your internal service
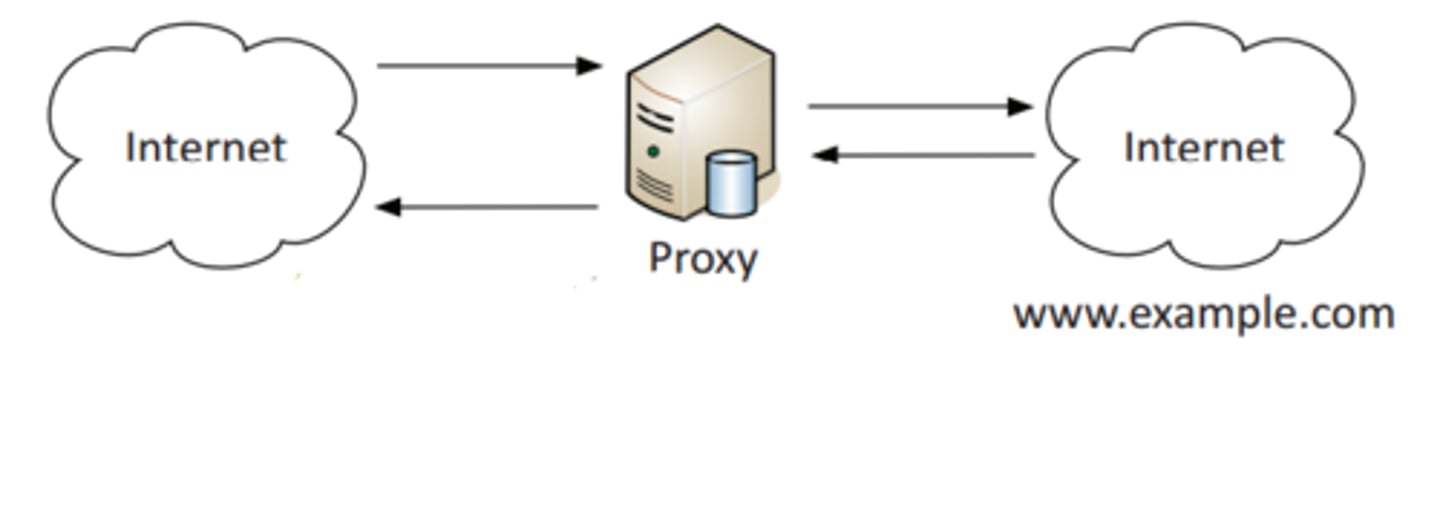
Open proxy
A third-party, uncontrolled proxy
-Can be a significant security concern
-Often used to circumvent existing security controls
Intrusion Prevention System (IPS)
Intrusion Prevention System
-Watch network traffic
Intrusions
-Exploits against operating systems, applications, etc.
-Buffer overflows, cross-site scripting, and other vulnerabilities
Detection vs Prevention
-Intrusion Detection System (IDS - Alarm or alert
-Prevention - Stop it before it gets into the network
Balancing the load
Distribute the load
-Multiple servers
-Invisible to the end-user
Large-scale implementations
-Web server farms, database farms
Fault tolerance
-Server outages have no effect
-Very fast convergence
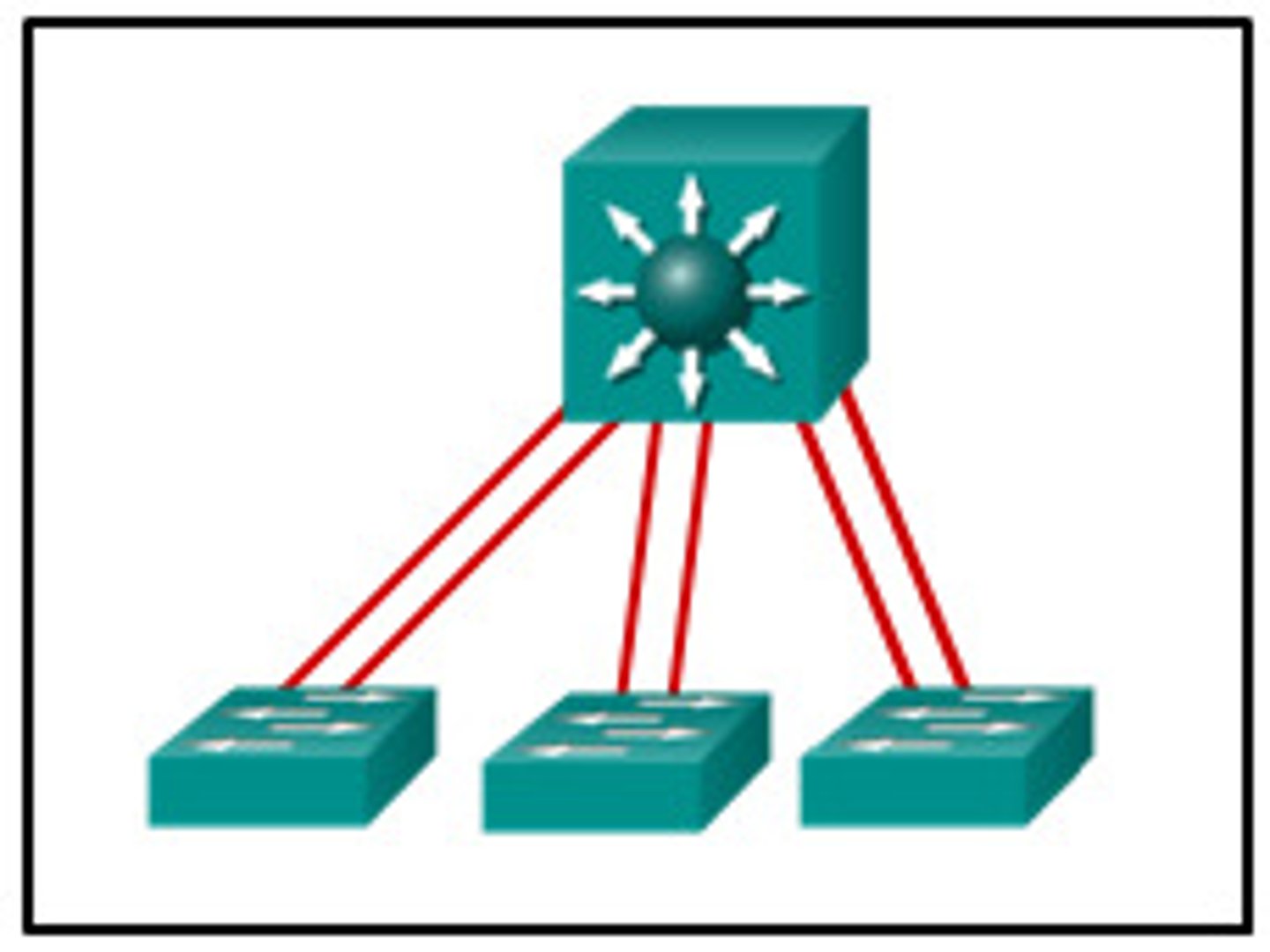
Active/active load balancing
Configurable load
-Manage across servers
TCP offload
-Protocol overhead
SSL offload
-Encryption/Decryption
Caching
-Fast response
Prioritization
-QoS
Content Switching
-Application-centric balancing
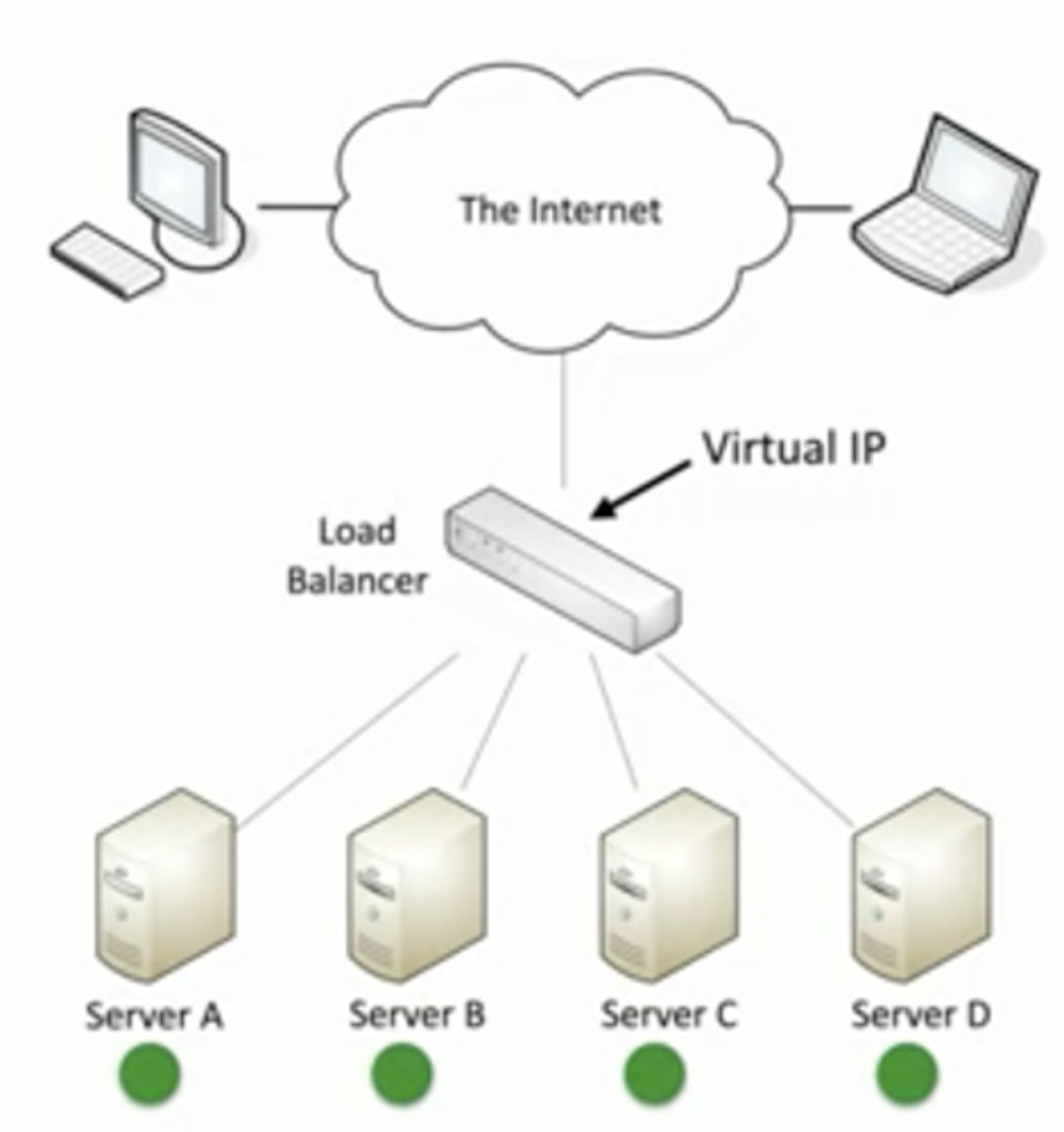
Active/passive load balancing
Some servers are active
-Others are on standby
If an active server fails, the passive server takes it place
Sensors and collectors
Aggregate information from network devices
-Built-in sensors, separate devices
-Integrated into switches, routers, servers, firewalls, etc.
Sensors
-Intrusion prevention systems, firewall logs, authentication logs, web server access logs, database transaction logs, email logs
Collectors
-Proprietary consoles (IPS, firewall), SIEM consoles, Syslog servers
-Many SIEMs include a correlation engine to compare diverse sensor data
Port security
We have created many authentication methods through the years
-A network administrator has many choices
Use a username and password
-Other factors can be included
Commonly used on wireless networks
-Also works on wired networks
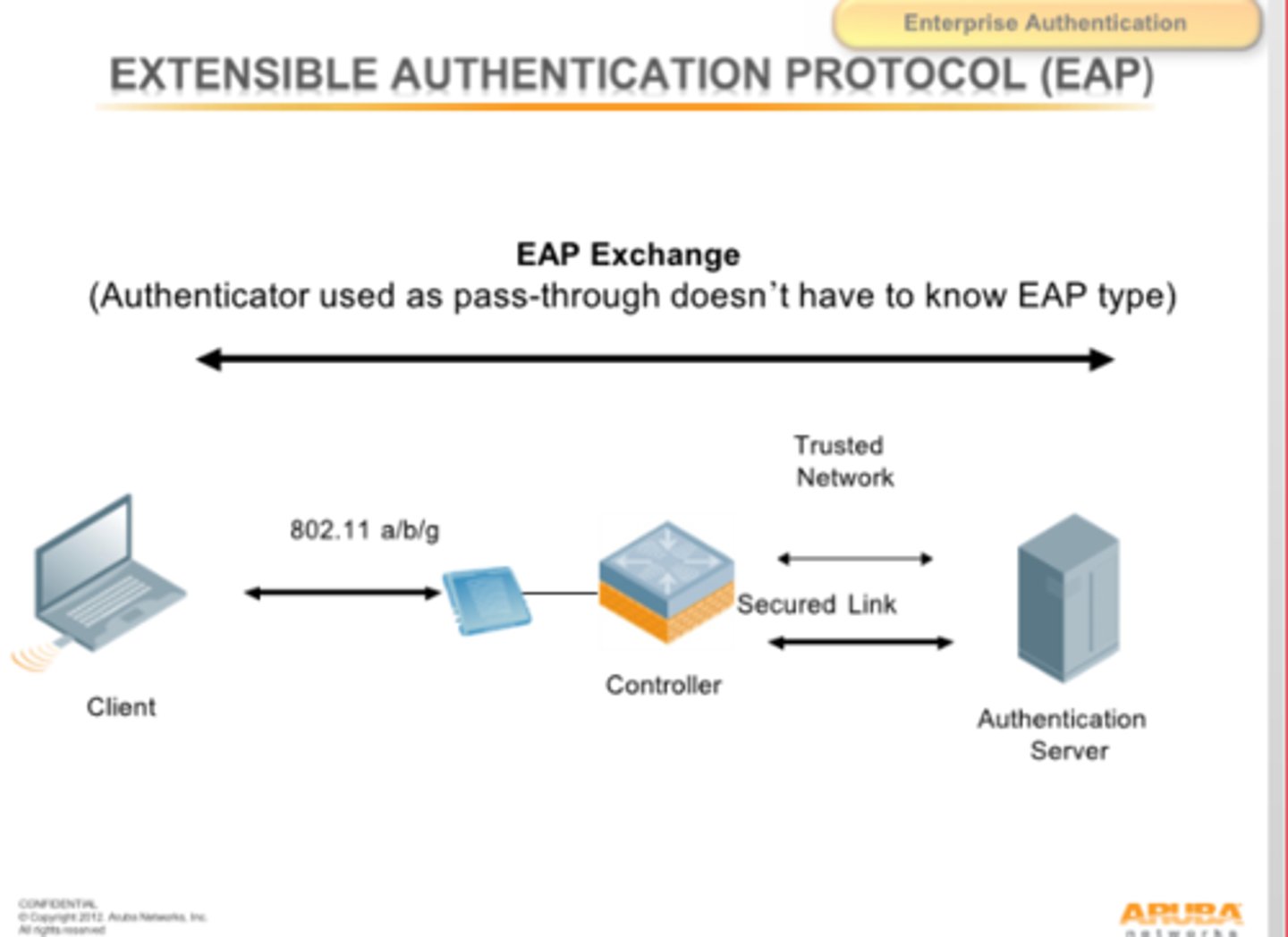
Extensible Authentication Protocol (EAP)
A framework for transporting authentication protocols that define the format of the messages.
There are many different ways to authenticate based on RFC standards
-Manufacturers can build their own EAP methods
EAP integrates with 802.1x
-Prevents access to the network until the authentication succeeds
IEEE
Institute of Electrical and Electronic Engineers. International organization focusing on electrical, electronics, and information technology topics. IEEE standards are well respected and followed by vendors around the world.
IEEE 802.1x Authentication
IEEE 802.1x
-Port-based Network Access Control (NAC)
-You do not get access to the network until you authenticate
EAP integrates with 802.1x
-Extensible Authentication Protocol
-802.1x prevents access to the network until the authentication succeeds
Used in conjunction with an authentication database
-RADIUS, LDAP, TACAC+, KERBEROS, etc.
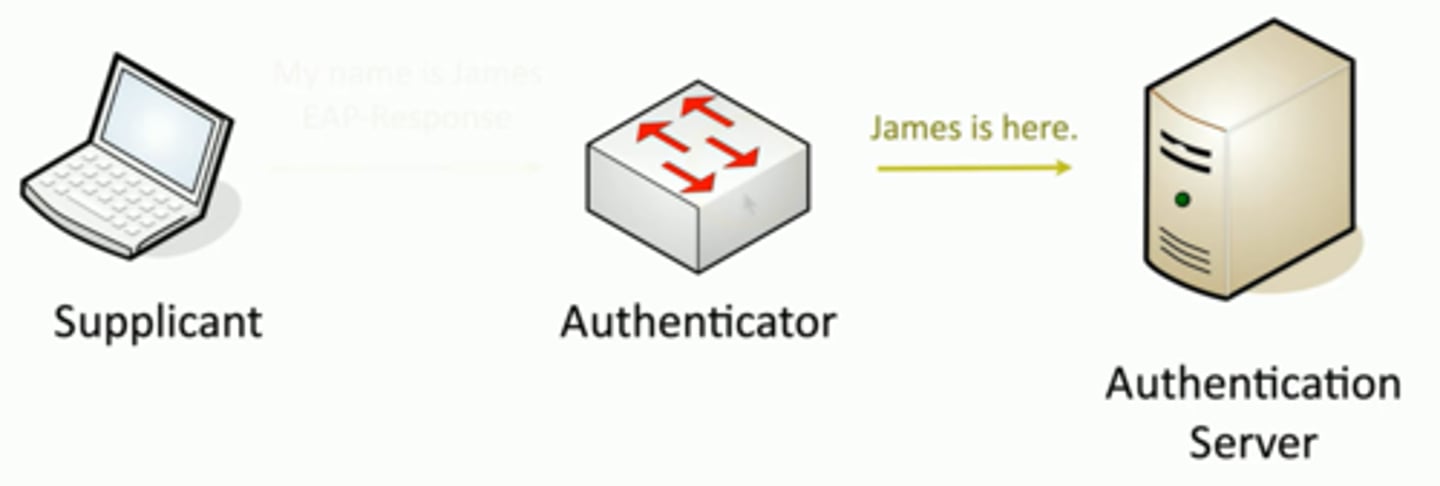
IEEE 802.1X and EAP
Supplicant - the client
Authenticator - The device that provides access
Authentication server - Validates the client's credentials
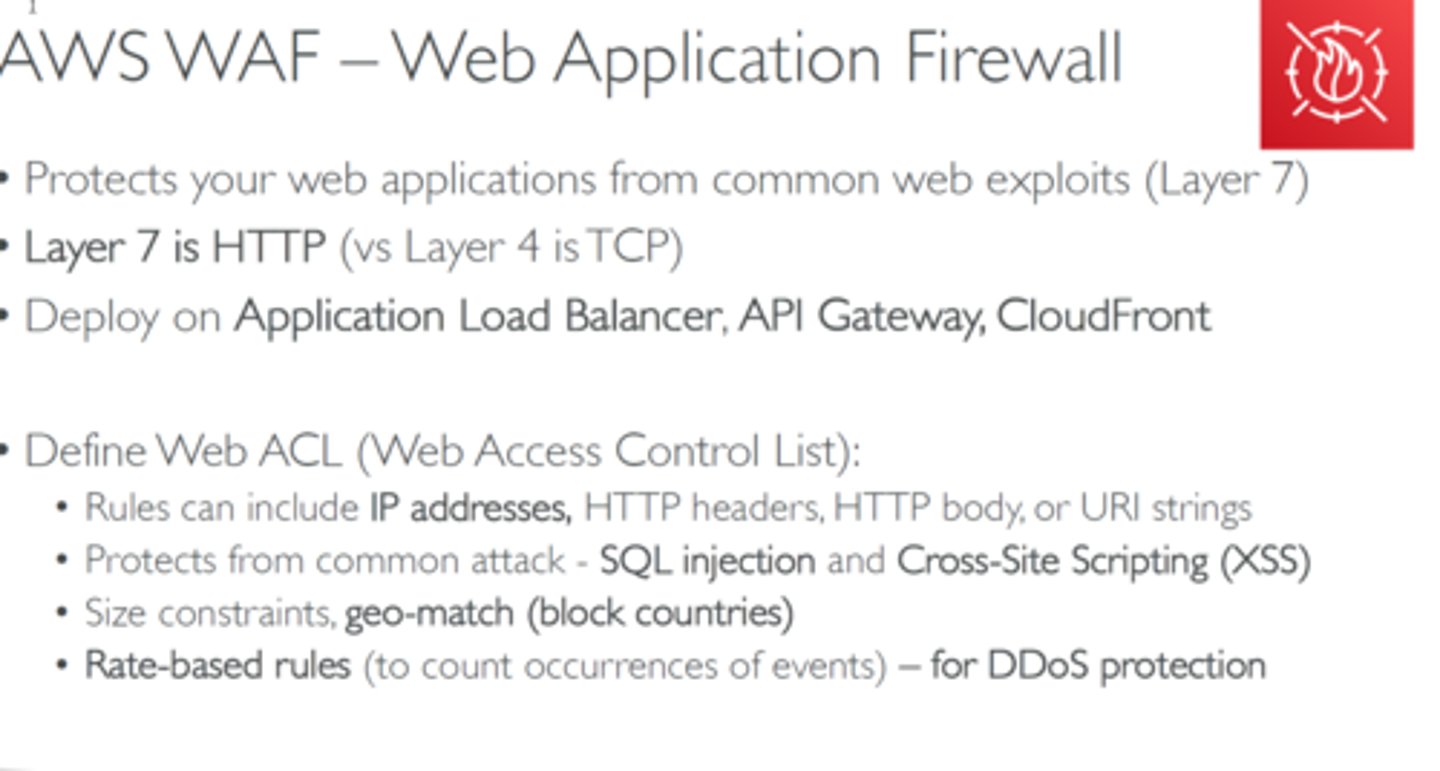
Web application firewall (WAF)
Not like a "normal" firewall
-Applies rules to HTTP/HTTPS conversations
Allow or deny based on expected input
-Unexpected input is a common method of exploiting an application
SQL injection
-Add your own commands to an application's SQL query
A major focus of the Payment Card Industry Data Security Standard (PCI DSS)
The universal security control
Standard issue
-Home, office, and in your operating system
Control the flow of network traffic
-Everything passes through the firewall
Corporate control of outbound and inbound data
-Sensitive materials
Control of inappropriate content
-Not safe for work, parental controls
Protection against evil
-Anti-virus, anti-malware
Network-based firewalls
Filter traffic by port number or application
-OSI layer 4 vs. OSI layer 7
-Traditional vs NGFW firewalls
Encrypt traffic
-VPN between sites
Most firewalls can be layer 3 devices (routers)
-Often sits on the ingress/egress of the network
-Network Address Translation (NAT) functionality
-Authenticate dynamic routing communication
UTM/ All-in-one security appliance
Unified Threat Management (UTM)/ Web security gateway
URL filter/ Content inspection
Malware inspection
Spam filter
CSU/DSU
Router, Switch
Firewall
IDS/IPS
Bandwidth Shaper
VPN endpoint
Next-generation firewall (NGFW)
The OSI Application Layer
-All data in every packet
Can be called different names
-Application layer gateway
-Stateful multilayer inspection
-Deep packet inspection
Requires some advanced decodes
-Every packet must be analyzed and categorized before a security decision is determined.
Layer 4/ layer 7
NGFWs
Network-based Firewalls
-Control traffic flows based on the application
-Microsoft SQL, Server, Twitter, YouTube
Intrusion Prevention Systems
-Identify the application-specific
-Apply application-specific vulnerability signatures to the traffic
Content filtering
-URL filters
-Control website traffic by category
Virtual Private Network (VPN)
A private data network that creates secure connections, or "tunnels," over regular Internet lines
Encrypted (private) data traversing a public network
Concentrator
-Encryption/decryption access device
-Often integrated into a firewall
Many deployment options
-Specialized cryptographic hardware
-Software-based options available
Used with client software
-Sometimes built into the OS
Remote Access VPN
A user-to-LAN virtual private network connection used by remote users.
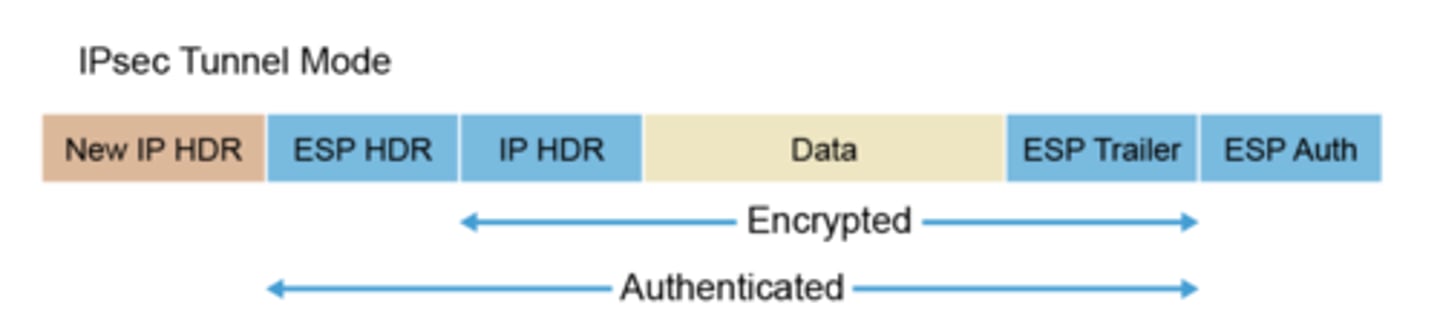
Encrypted Tunnel
The result is placing each packet in an encrypted form within another packet before sending it to add a layer of security that protects each packet on its journey over the Internet. The outer packet protects the contents from public view and ensures that the packet moves within a virtual tunnel.
Keep data private across the public internet
-Encryption is the key
Encrypt your data
-Add new headers and trailers
Decrypt on the other side
-Original data is delivered
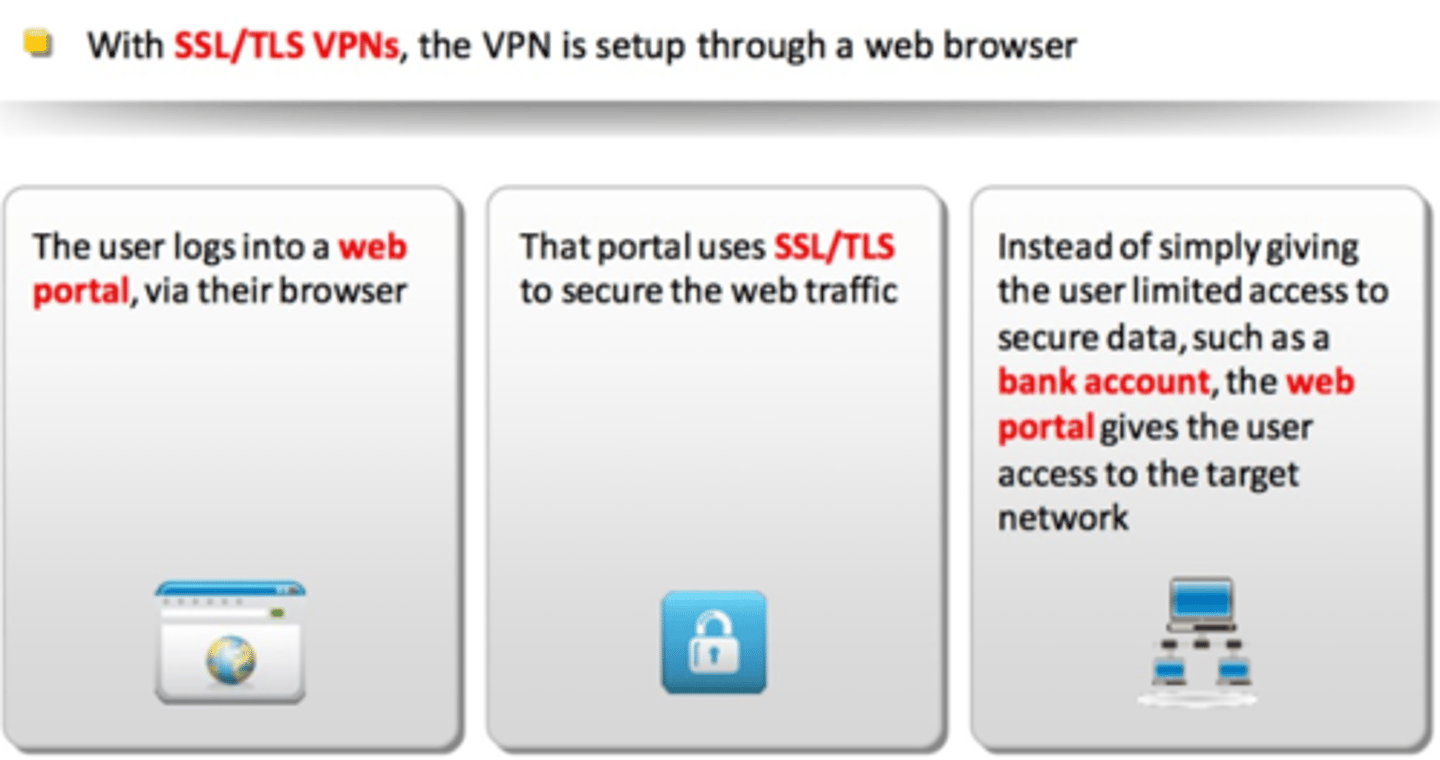
SSL/TLS VPN (Secure Socket Layer VPN)
Uses common SSL/TLS protocol (TCP/443)
-(Almost) No firewall issues
No big VPN clients
-Usually, remote access communication
Authenticate users
-No requirement for digital certificates or shared passwords (like IPSec)
It can be run from a browser or from a (usually light) VPN client
-Across many operating systems
SSL/TLS VPN
VPN setup through a web browser or portal that uses SSL/TLS to secure traffic. Gives users access to the target network.
On-demand access from a remote device
-Software connects to a VPN concentrator
Some software can be configured as always-on
IPSec (Internet Protocol Security)
A set of open, non-proprietary standards that you can use to secure data as it travels across the network or the Internet through data authentication and encryption.
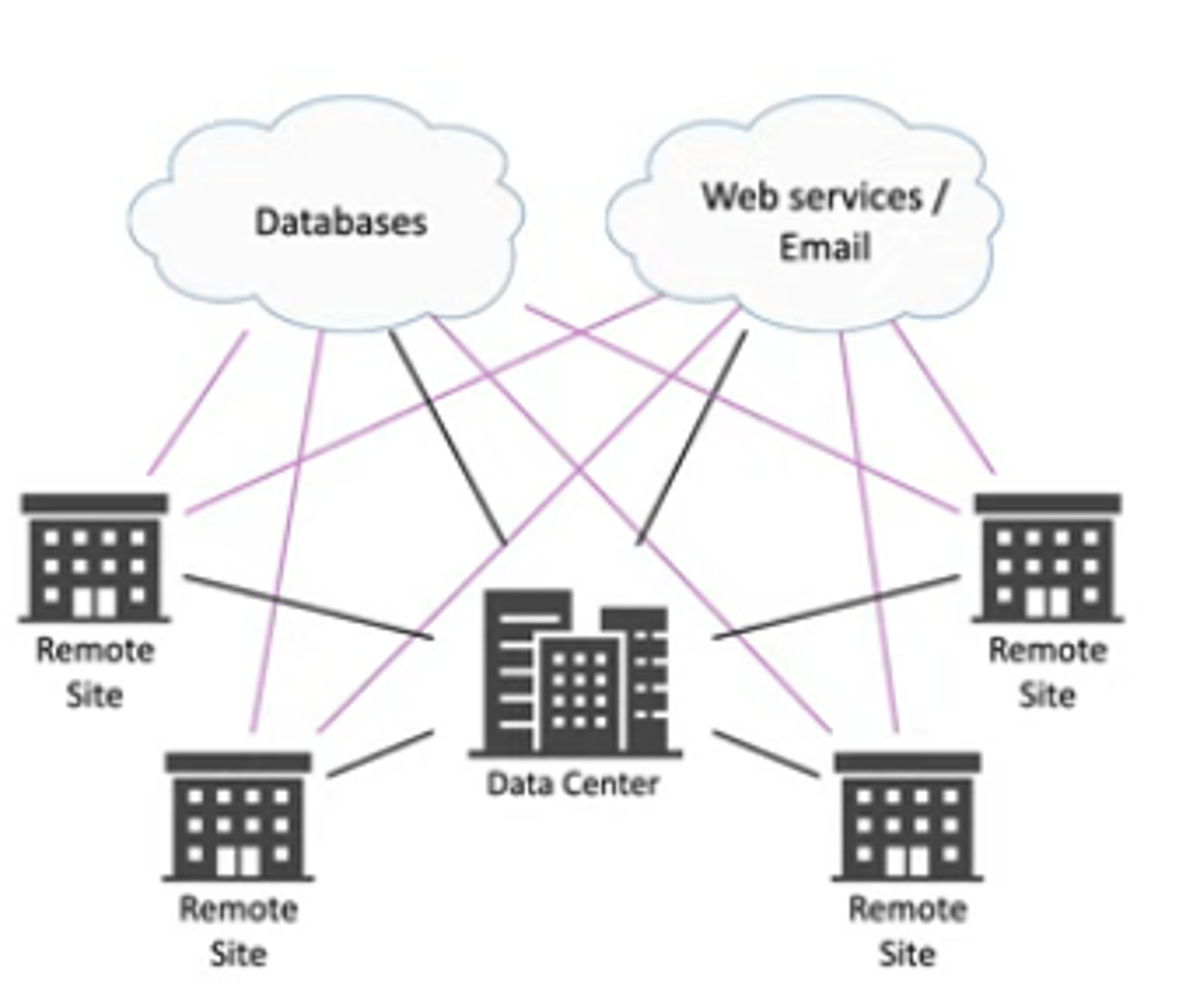
Site-to-site IPsec VPN
Always-on
Firewalls often act as VPN concentrators
-Probably already have firewalls in place

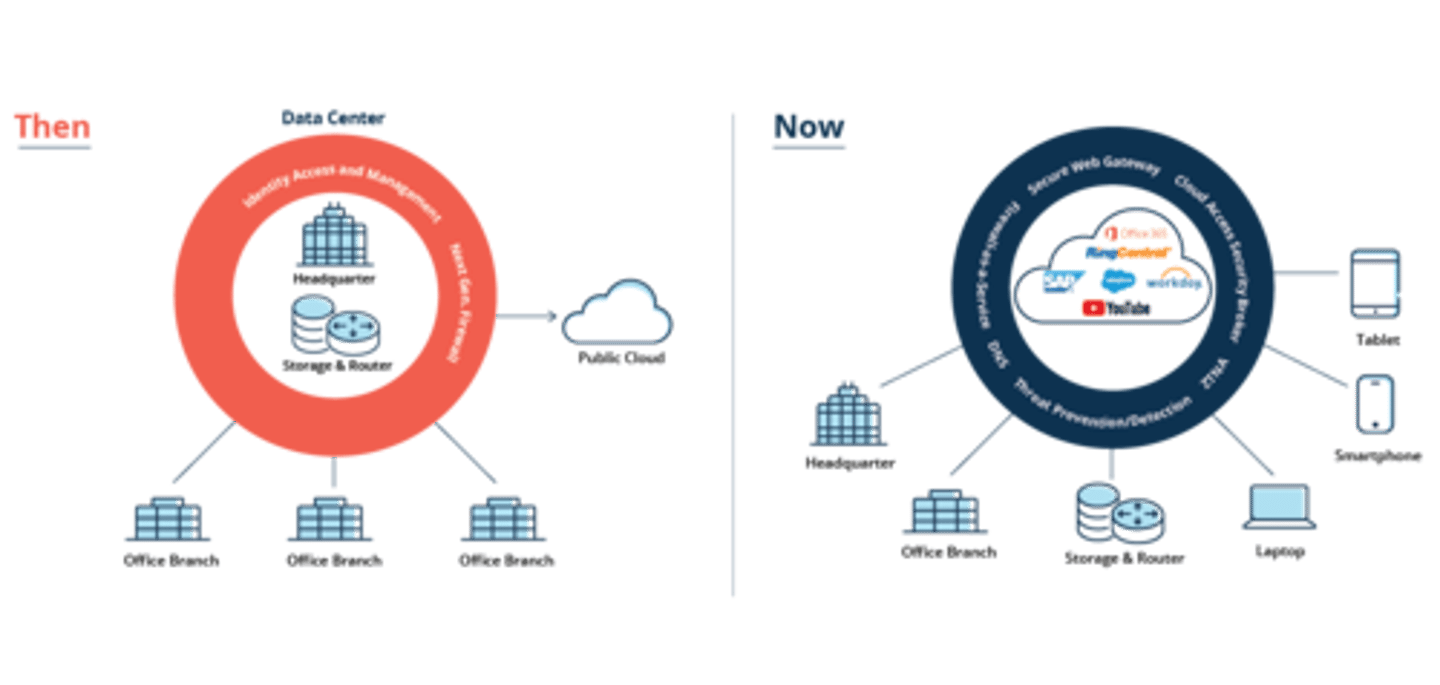
SD-WAN - software-defined wide area network
Software Defined Networking in a Wide Area Network
- A WAN built for the cloud
The data center used to be in one place
-The cloud has changed everything
Cloud-based applications communicate directly to the cloud
-No need to hop through a central point
Selection of effective controls
Many different security options
-Selecting the right choice can be challenging
VPN
-SSL/TLS VPN for user access
-IPsec tunnels for site-to-site access
SD-WAN
-Manage the network connectivity to the cloud
-Does not adequately address security concerns
SASE
-A complete network and security solution
-Requires planning implementation
Secure Access Service Edge (SASE)
Update secure access for cloud services
-Securely connect from different locations
A "next generation" VPN
Security technologies are in the cloud
-Located close to existing cloud services
SASE clients on all devices
-Streamlined and automatic
Data types
Regulated
Trade Secret
Intellectual property
Legal information
Financial information
Human and non human readable
Regulated
Managed by a third-party
Government laws and statutes
Trade secret
An organization's secret formulas
Often unique to an organization
Intellectual property
It may be publicly visible
Copyright and trademark restrictions
Legal information
Court records and documents, judge and attorney information, etc.
PII and other sensitive details
Usually stored in many different systems
Financial information
Internal company financial details
Customer financials
Payment records
Credit card data, bank records, etc.
Human-readable
Humans can understand the data
Very clear and obvious
Non-human readable
Not easily understood by humans
Encoded data
Barcodes
Images
Hybrid formats
CSV, HXM, JSON, etc.
Classifying sensitive data
Not all data has the same level of categorization
-License tag numbers vs. health records
Different levels require different security and handling
-Additional permissions
-A different process to view
-Restricted network access
Data Classifications
Proprietary
-Data that is the property of an organization
-May also include trade secrets
-Often data unique to an organization
PII - Personally Identifiable Information
-Data that can be used to identify an individual
-Name, date of birth, mother's maiden name, biometric information
PHI- Protected health information
-Health information associated with an individual
-Health status, health care records, payments for health care, and much more.
Types
Sensitive
Confidential
Public
Restricted
Private
Critical
Sensitive data
Intellectual property, PII, PHI
Confidential Data
Very sensitive, must be approved to view
Public/ Unclassified
No restrictions on viewing the data
Private/Classified/Restricted Data
Restricted access, may require an NDA
Critical Data
Data should always be available
States of Data
Data at rest
Data in transit
Data in Use
Data at Rest
The data is on a storage device
-Hard drive, SSD, flash drive, etc.
Encrypt the data
-Whole disk encryption
-Database encryption
-File or folder-level encryption
Apply for permissions
-Access control lists
-Only authorized users can access the data
Data in transit
Data transmitted over the network
-Also called data-in-motion
Not much protection as it travels
-Many different switches, routers, devices
Network-based protection
-Firewall, IPS
Provide transport encryption
-TLS (Transport Layer Security)
IPsec(Internet Protocol Security)
Data in use
Data is actively processed in memory
-System RAM, CPU registers and cache
The data is almost always decrypted
-Otherwise, you could not do anything with it
The attackers can pick the decrypted information out of RAM
-A very attractive option
Data sovereignty
Data Sovereignty
-Data that resides in a country is subject to the laws of that country
-Legal monitoring, court orders, etc.
Laws may prohibit where data is stored
-GDPR (General Data Protection Regulation)
-Data collected on EU citizens must be stored in the EU
-A complex mesh of technology and legalities
Where is your data stored
-Your compliance laws may prohibit moving data out of the country
Geolocation
Location details
-Tracks within a localized area
There are many ways to determine a location
-802.11, mobile providers, GPS
Can be used to manage data access
-Prevent access from other countries
Limit administrative tasks unless a secure area is used
-Permit enhanced access when inside the building
Geographic restrictions
Network location
-Identify based on IP subnet
-Can be difficult with mobile devices
Geolocation - Determine a user's location
-GPS - mobile devices, very accurate
-802.11 wireless, less accurate
-IP address, not very accurate
Geofencing
-Automatically allow of restricting access when the user is in a particular location
-Do not allow this app to run unless you are near the office