CSUF ISDS 351 Exam 1
1/90
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
91 Terms
information system
set of interrelated components that collect, process, store, and disseminate data to support fundamental business operations, data reporting, and visualization
information systems help with data analysis, decision making, communication, and coordination for an organization
true
competitive advantage
enables an organization to generate more sales or achieve superior profit margins compared to its rivals
cost leadership
a strategy that aims to provide a product or service at as low a price as possible compared to competitors
differentiation
charging higher prices for providing products that are perceived by the customer as being better
focus
understanding and servicing a target market better than anyone else
leavitt diamond
a model of organizational change that says if one key element is changed it likely impacts other elements; structure, tasks, technology, and people
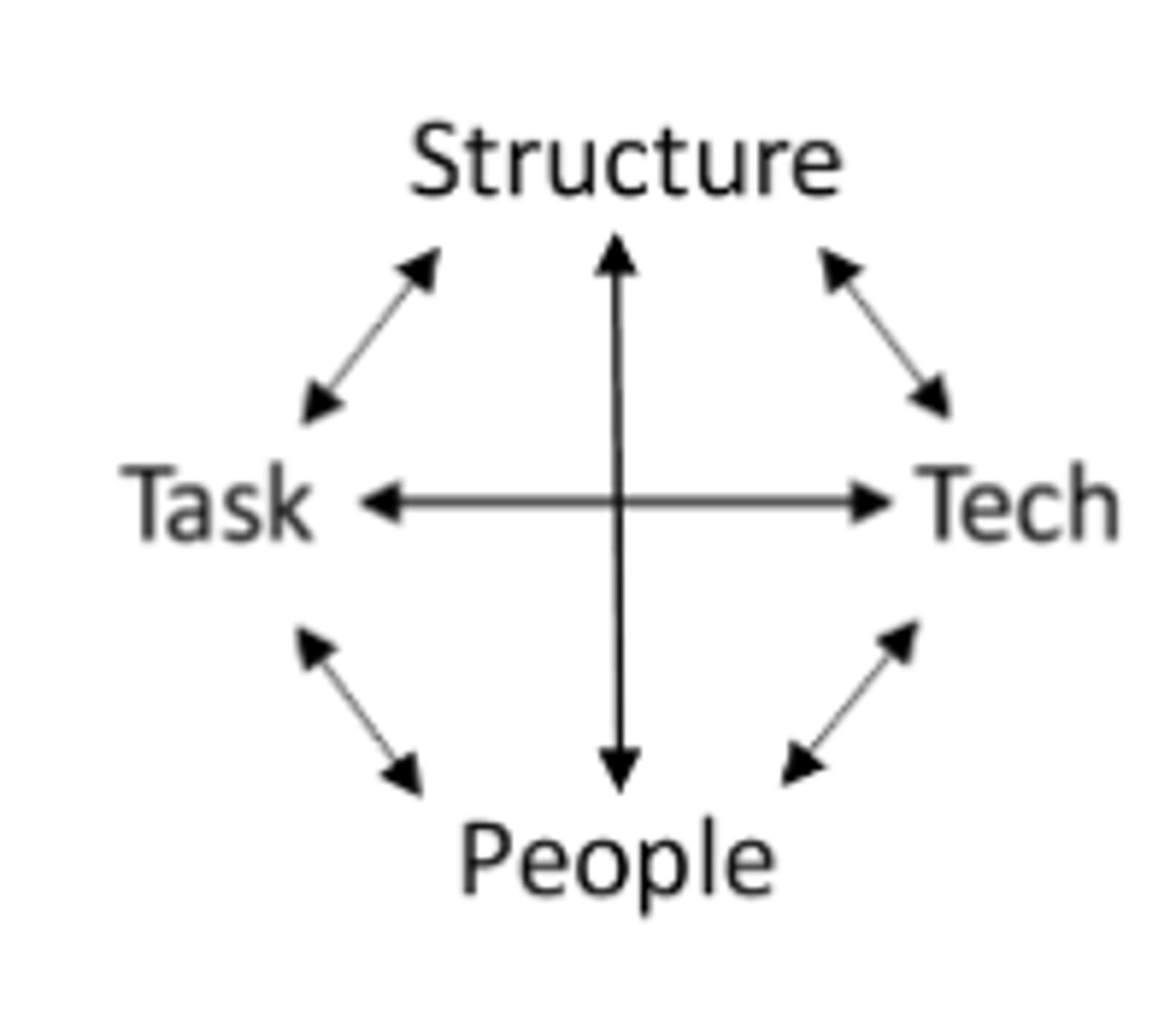
personal information system
improve the productivity of individual users in performing stand alone tasks
workgroup information system
support teamwork and enable people to work together effectively, regardless of location
enterprise information system
meet organizational business needs and share data with other enterprise applicants used within the org
interorganizational information system
enables the sharing of information across organizational boundaries
value chain
a series of activities that an organization performs to transform inputs into outputs in such a way that the value of the input is increased
supply chain
key value chain whose primary activities include inbound logistics, operations, outbound logistics, marketing and sales, and service
strategic planning
process that helps managers identify initiatives and projects that will achieve organizational objectives
certification
process for testing skills and knowledge; successful completion = endorsement
careless insider
an inside (employee, business partner, contractor, consultant) who does not follow the organization's security polices and enables a cyberattack to occur
malicious employees
an insider who deliberately attempts to gain access to and/or disrupt a company's information systems and business operations
cybercriminal
someone who attacks a computer system or network for financial gain
hacktivist
an individual who hacks computers and websites in order to promote political ideology
lone wolf attacker
someone who violates computer or internet security maliciously or for illegal personal gain
cyberterrorist
state-sponsored individual/group who attempts to destroy the infrastructure components of governments, financial institutions, etc
attack vector
gain unauthorized access to a device or network and initiate cyber attack
advanced persistent threat
intruder gains access to a network and stays there undetected with the intention of stealing data over a long period of time
blended threat
sophisticated threat that combines the features of a virus, worm, trojan horse, and other malicious code into a single payload
phishing
fraudulent practice of sending emails to get the recipient to reveal personal data
root kit
a set of software tools that enable an unauthorized user to gain control of a computer system without being detected
smishing
variation of phishing that involves the use of texting
spam
use of email systems to send unsolicited email to large numbers of people
social engineering
using deception to obtain unauthorized access to information resources
trojan horse
seemingly harmless program in which malicious code is hidden
virus
piece of programming code, usually disguised as something else, that causes a computer to behave in an unexpected and usually undesirable manner
vishing
a phone scam that attempts to defraud people by asking them to call a bogus telephone number to confirm their account information
worm
resides in the active memory of the computer and duplicates itself
direct impact
value of assets stolen or damaged due to cyberattack
business disruption
organization is unable to operate in an effective manner for hours/days and can cause a loss of business/customers
recovery cost
may take organization days/weeks to repair affected systems or recover lost data
legal consequences
prospect of monetary penalties for businesses that fail to comply with data protection legislation
reputation damage
eroded trust your organization has established with customers and suppliers
cia triad
confidentiality, integrity, availability
confidentiality
ensures that only those individuals with the proper authority can access data/information
integrity
ensures data can be changed only by authorized individuals
availability
ensures that the data can be accessed when and wherever
biometric authentication
uses personal physical characteristics such as fingerprints, facial features, and retinal scans to authenticate users
firewall
a part of a computer system or network that is designed to block unauthorized access
next generation firewall
can detect and block sophisticated attacks by filtering network traffic dependent on the packet contents
routers
provides the capability to specify the unique media access control address of each device connected to the network and restrict access to the network
encryption
the process of scrambling messages or data in such a way that only authorized parties can read it
encryption key
value that is applied, using an algorithm, to a set of unencrypted text to produce encrypted text that appears as a series of seemingly random characters (ciphertext), which unreadable by those without the encryption key
symmetric algorithm
use the same key for encryption and decryption
asymmetric algorithm
two separate keys for encryption and decryption
transport layer security
a communication system of rules that ensures privacy between communicating applications and their users
proxy servers serve as an intermediary between a web browser and another server
true
vpn
virtual private network, enables remote users to securely access computing and storage devices and share data remotely
network administrator
is responsible for monitoring network security web sites frequently and downloading updated antivirus software as needed
computer forensics
discipline that combines elements of law and computer science to identify, collect, examine, and preserve data from computer systems and storage devices in a manner that preserves the integrity of the data gathered so that it is admissible as evidence in a court of law
cce
certified computer examiner
cissp
certified information systems security professional
csfa
cybersecurity forensic analyst
gcfa
global information assurance certification certified forensics analyst
ethics
set of principles about what is right and wrong for individual's decision making
law
system of rules that tells us what we can and cannot do
fostering csr
gaining the goodwill of the community, creating an organization that operates consistently, fostering good business practices, avoiding unfavorable publicity, and protecting the organization and its employees from legal action
professional code of ethics
outlines what the organization aspires to become and consists of rules and principles by which members of the organization are expected to abide
defamation
making either an oral (slander) or a written (libel) statement of alleged fact that is false and harms another person
safety critical systems
failure may cause human injury or death and takes longer and is more expensive than high-quality systems
information
a collection of data that is organized and processed
knowledge
awareness and understanding of a set of information
data management
integrated set of functions that defines the processes by which data is obtained, certified fit for use, stored, secured, and processed which ensures accessibility, reliability, and timeliness of the data
accessible
easily obtainable & meets needs
accurate
error free
complete
contains all important facts
economical
avoids waste when being produced
relevant
relates to the decision maker
reliable
can be trusted by users
secure
cannot be access by unauthorized users
timely
delivered when needed
verifiable
able to check if correct
data cleansing
process of detecting and correcting incomplete, inaccurate, or irrelevant records that reside in a database
big data
data collections that are so enormous and complex that traditional data management that all soft and hardware are incapable of dealing with
bank secrecy act
detects and prevents money laundering by requiring financial institutions to report certain transactions to government agencies and to withhold from clients that such reports were filed about them
data mart
contains a subset of data warehouse information
data warehouse characteristics
large, multiple sources, historical, cross organizational analysis, and supports various types of analyses and reporting
hipaa
protects health information by requiring verbal or written authorization for release of information
basel ii accord
creates international standards that strengthen global capital and liquidity rules
california senate bill
protects consumers from identity theft, 1386
global data regulation
increases the rights of individuals and gives them more control over their information
foreign account tax compliance act
identifies u.s. taxpayers who hold financial assets in non-u.s. financial institutions and offshore accounts
gramm leach bliley act
protects the privacy and security of individually identifiable financial info
velocity
the rate at which new data is being generated
value
refers to the worth of the data in decision making
veracity
measure of the quality of the data