7.1: Firmware Extraction and Analysis
1/19
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
20 Terms
Firmware
A combination of an OS and the application logic for the device.
Reasons for extracting Firmware
Finding vulnerabilities
Extract data (e.g. cryptographic keys)
Reverse engineering protocols or interfaces
Forensics
Failure analysis
Repurposing EOL devices (Archbook mentioned)
Extracting Firmware from Small Devices (With Force)
May have to take apart or completely destroy it to understand its internals
Access the circuit boards
Read-Out Protection
A protection chip manufacturers may use to prevent chips having their programming read.
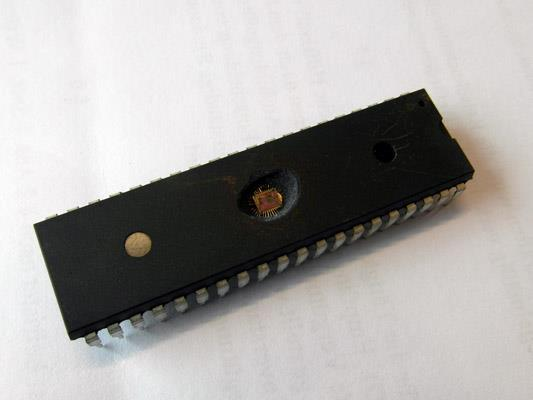
Bypassing Read-Out Protection
Decapping it, removing the top with acids and heat - don’t try this at home!
Check it under a microscope
Fuses area often enforces read-out protection
Cover the whole chip except for the fuses and shine a strong UV light at it
Flip the fuse’s bit and disable ROP
Extracting Firmware from Small Devices (Without Force)
Might not have ROP turned on from the factory
Update blobs available on manufacturers’ websites
Race conditions and bugs in ROP firmware
Or you could just have a silly little screw that you can take out
Chip Readout Protection (CRP)
Protects a chip from being read out, different versions including CRP1 (quite relaxed), CRP2 (a bit stricter), CRP3 (disables the bootloader completely and prevents the chip from being read ever again).
Chip Memory Layout
Programming commands
Stack
Rest of RAM
CRP
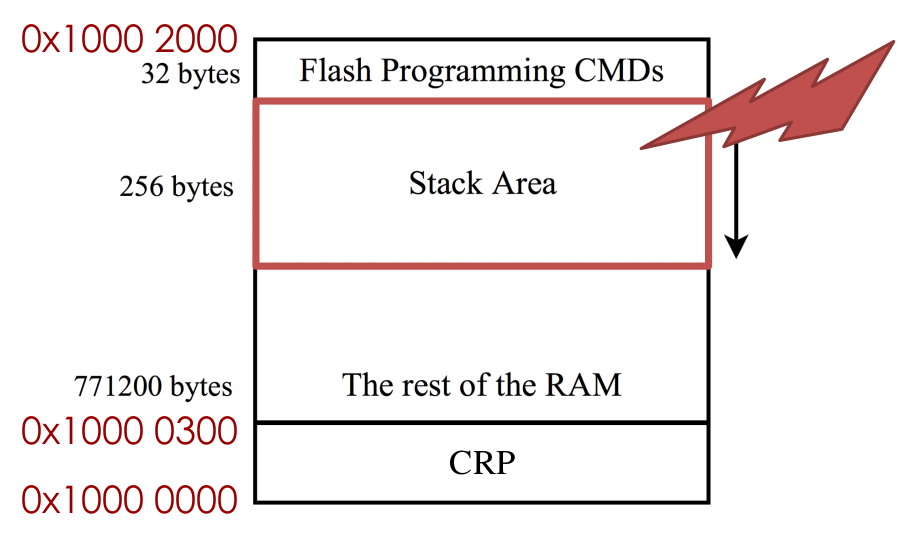
CRP - Bypass
Use Return-Oriented Programming.
Call the write command with a payload overwriting the return address
That return address points inside the read command handler
Use some kind of gadget to prevent a crash
Dump chip contents
Extracting Firmware from Complex Devices
Updates or complex systems that can be reverse engineered
If a device is updated over-the-air, HTTPS is not used due to certificate stores getting old/nonfunctional/outdated
HTTP is used instead which can be easily eavesdropped on
UART Protocol
Universal asynchronous receiver/transmitter - used to exchange serial data between two devices.
UART Debugging
Use a serial debugger, of which a lot of devices have for manufacturers to test them.
Four pins connect to a small USB adapter
Create a terminal session over the UART debugger to interface with the device
Once root is accessed (usually via insecure passwords), can dump what you want
Dumping Firmware via Rebooting
Reboot and interrupt the boot sequence for the chance of accessing the BIOS or low-level bootloader
If using U-boot, can interrupt the boot process by entering the bootloader and using
nand dump 0×0to dump firmwareCan also upload your own bootloader if possible
JTAG
A protocol similar to UART that can test printed circuits after manufacturing.
Directly Attacking Storage
Interfacing directly with soldered chips on the board will often contain firmware.
eMMC (Embedded MMC)
Glorified embedded SD cards - used to store data.
Reading eMMC Chips
Connecting the chip to an SD card reader.
Analysing Firmware - Black-Box Techniques
Port scanning
Network traffic sniffing
Poking web vulnerabilities
Analysing Firmware - Grey-Box Techniques
Combining white-box (proper firmware analysis) and simplifying it (checking TCP connections directly may be easier than reversing the respective binary)
Analysing Firmware - White-Box Techniques
Convert and dump the firmware into an appropriate format
Identify the CPU architecture
Analyse the firmware structure
Decrypt and unpack the firmware
If it’s a bare-metal binary, load into IDA or Ghidra
Otherwise, mount the filesystem and load a forensics tool/automated analyser
Analyse files of interest