4.1 Application Security
1/7
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
8 Terms
Secure Coding Concepts
IT professionals often install security patches to fix vulnerabilities like buffer overflows or SQL injection in applications.
Developing an application is challenging, requiring a balance between rapid development and strong security.
Quality assurance (QA) plays a key role by testing both functionality and security before release.
If vulnerabilities slip past QA, researchers or attackers are likely to discover and potentially exploit them later.
Input Validation
Ensure that any data entered into the application is expected and safe.
Since users can input data through forms, fields, or freeform text, developers must check that this input fits the required format
For example, a zip code field should only accept a specific number of characters.
If input doesn’t match the expected format, the application should alert the user to correct it.
Automated tools called fuzzers test these inputs by sending random data to identify how the application handles unexpected or invalid input
Secure Cookies
Small data files stored in your browser that help websites remember information, like personalizing content or maintaining your login session.
Although they aren’t executable and don’t carry malware, the data they contain can be valuable to attackers.
To protect this data, many browsers use secure this, which are set with an attribute that ensures the it is only sent over encrypted HTTPS connections.
Themselves don’t have built-in security, so developers avoid storing sensitive information in them to prevent exposure to third parties.
Static Code Analyzers
Check their code for security vulnerabilities.
Also called Static Application Security Testing (SAST)
Scans the source code to detect issues like buffer overflows and database injections.
Can’t catch all security problems, such as authentication flaws or weak cryptography.
Might include false positives, so developers need to review the output carefully to identify which issues are real.
Static Code Analyzer Output
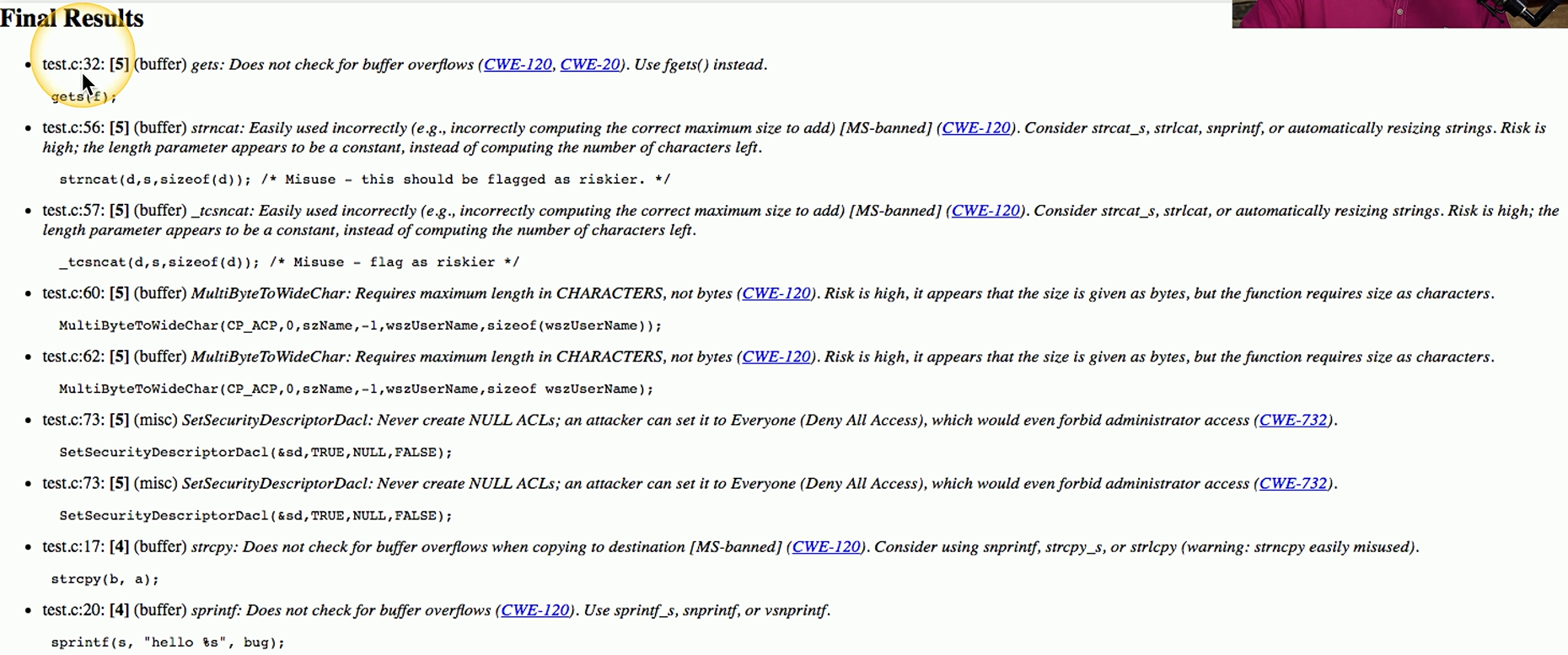
Here’s a sample of some output from a static code analyzer.
You can see there are a number of issues that need to be addressed within the code of the application.
For example, in the first line of this static code analyzer output, you can see that filetest.c on line 32 has a problem with the gets function because it doesn’t check for a buffer overflow.
This analyzer even gives recommendations to use fgets instead of using gets.
The developer would then be responsible for going through this entire set of output to see if these recommendations are ones that apply to the code that’s listed in the application.
By using this static code analyzer output, the application developer can find some of those glaring problems and correct them before the application is distributed.
Code Signing
A security process used to verify that the software you install is exactly what the developer intended to distribute, without any unauthorized changes or malware.
Developers digitally sign their code using a private key certified by a trusted certificate authority.
This signature proves two things: that the code hasn’t been altered since it left the developer, and that it genuinely comes from that developer.
When you install the application, your operating system checks this digital signature.
If the signature is missing or invalid, you’ll get a warning, helping protect you from installing tampered or malicious software.
Sandboxing
A security technique that restricts an application’s access to only the data and resources it needs to function.
It is isolated from other parts of the system, limiting its ability to affect or access unrelated data.
During development, sandboxing also means keeping new code separate from the main production environment to prevent accidental disruptions.
For example, virtual machines (VMs) run in isolated sandboxes, each separated from others on the same system.
Mobile operating systems use this to ensure apps can only access certain data:
For instance, a mobile browser can use your bookmarks but doesn’t automatically have access to your camera roll, reducing potential damage if the app is compromised.
Application Security Monitoring
Developers often build monitoring features into applications to track usage and detect potential security issues.
Allows them to identify attacks such as SQL injection attempts or exploitation of known vulnerabilities.
Generates detailed logs of application activity, which can then be analyzed to uncover unknown threats or unusual behaviors.
If something out of the ordinary happens—like unexpected file transfers or a sudden spike in client access—the monitoring system will highlight these anomalies