Cybersecurity Governance and Key Concepts for IT Security
1/20
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
21 Terms
What is the primary goal of cybersecurity?
To protect information and information systems.
How is cybersecurity defined?
As the protection of information systems against unauthorized access, modification, and denial of service to authorized users.
What does the CIA Triad stand for in cybersecurity?
Confidentiality, Integrity, and Availability.
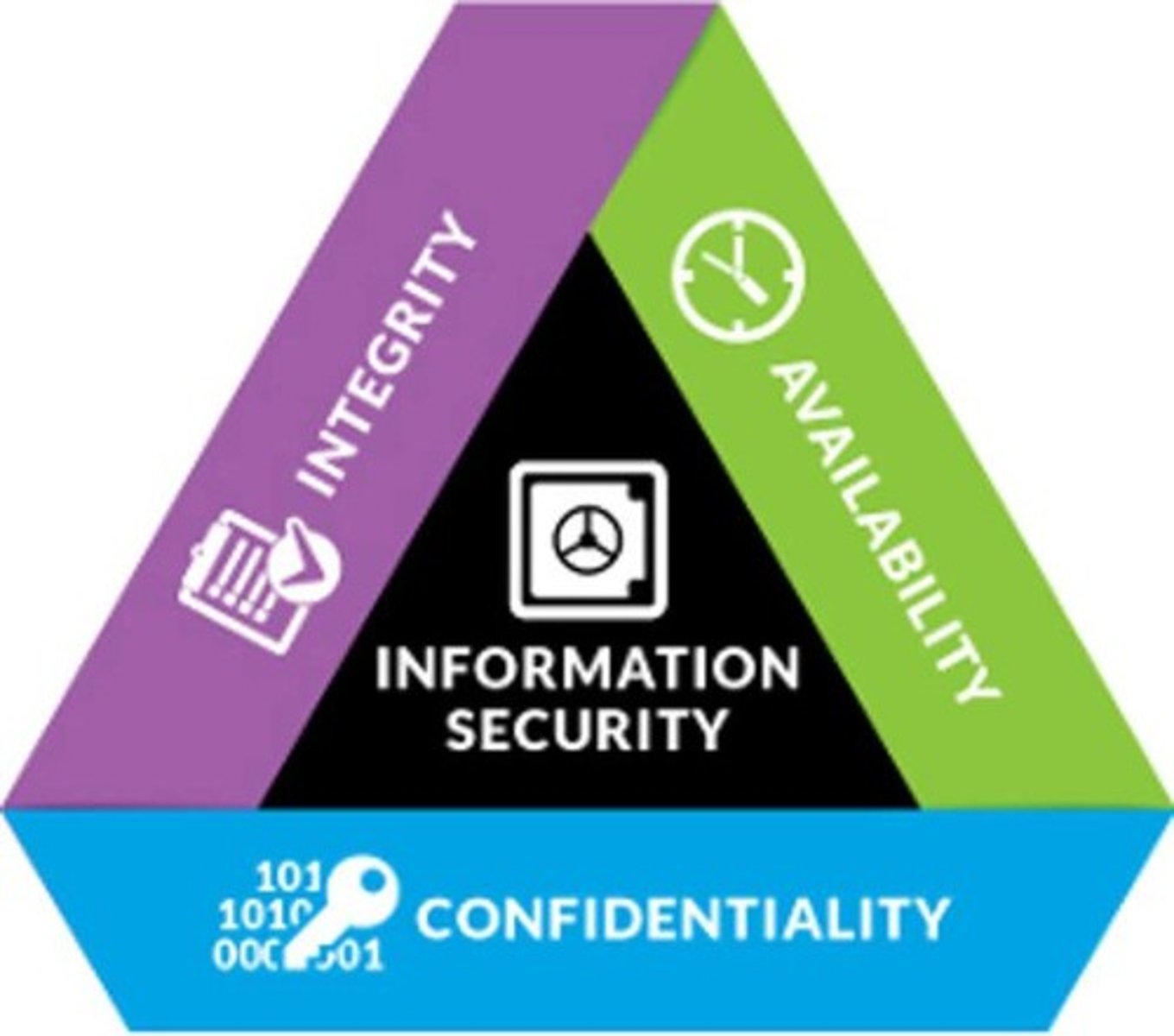
What does integrity in the CIA Triad refer to?
Protection against unauthorized modification or destruction of information.
What is meant by availability in the context of cybersecurity?
Ensuring that information is accessible when needed, including making backup copies.
What does confidentiality safeguard in cybersecurity?
It protects information from being accessed by individuals without proper clearance or need to know.
What is the focus of cybersecurity?
Keeping unauthorized individuals out, protecting internal networks, and recovering from attacks.
What are threats in cybersecurity?
Circumstances or events that can harm an information system by destroying, disclosing, or modifying data.
What are vulnerabilities in an information system?
Weaknesses that could be exploited to harm the system.
What is information privacy?
The relationship between data collection, dissemination, technology, public expectations of privacy, and legal issues.
What types of information are considered sensitive?
Personnel, financial, payroll, and medical information.
What is the Governance, Risk, and Compliance (GRC) Framework?
A framework for aligning IT areas with institutional strategic objectives, identifying risks, and ensuring compliance.
What are the key components of a holistic cybersecurity governance program?
Approve, Define, Interpret, and Implement.
What is the significance of cybersecurity awareness?
It emphasizes that security is everyone's responsibility.
What is the potential impact of cyber attacks?
They can lead to serious, severe, or catastrophic effects on organizational operations and assets.
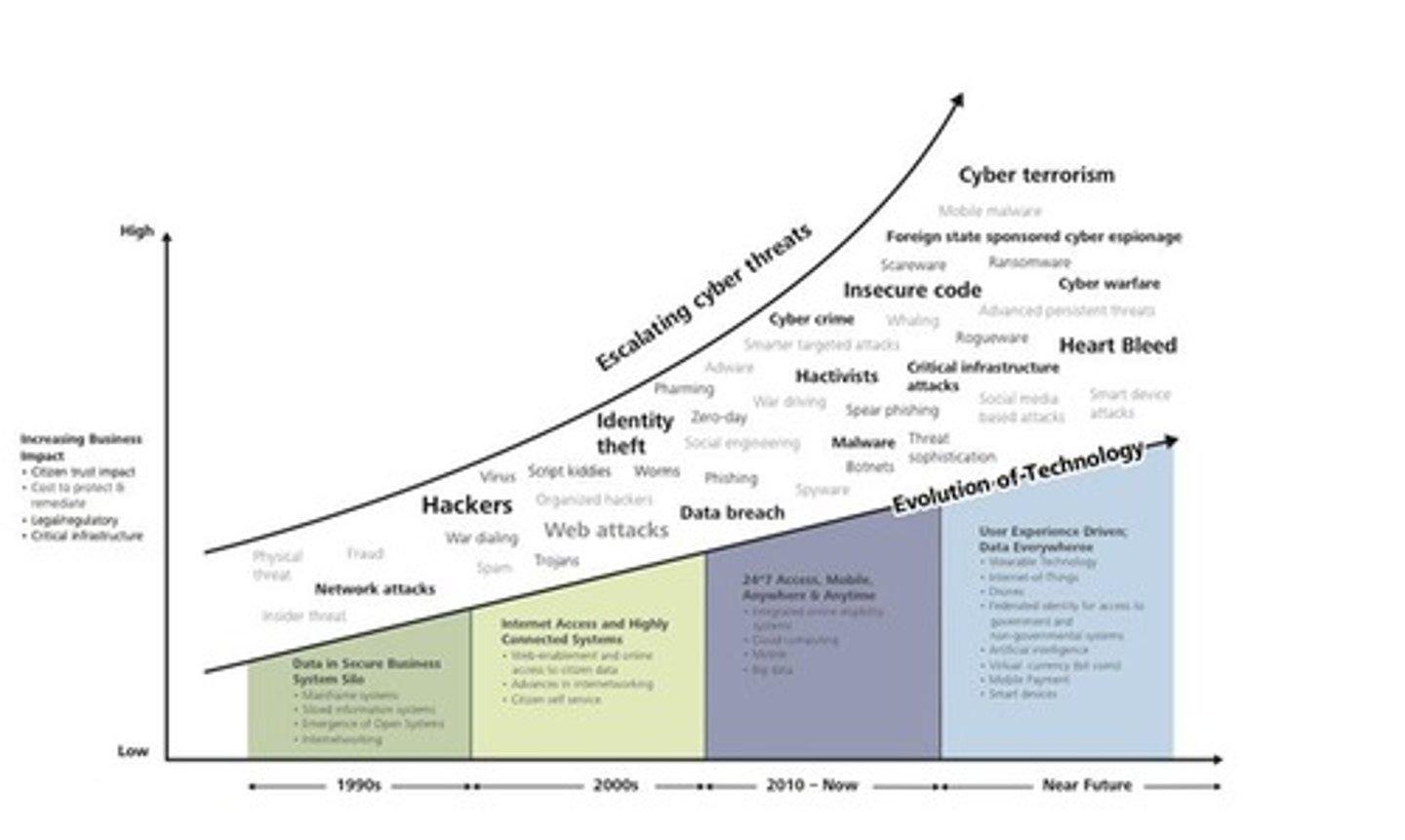
What is the relationship between technology evolution and cyber threats?
As technology evolves, so do the methods and sophistication of cyber threats.
What is the importance of understanding risk management in cybersecurity?
It helps in identifying and mitigating risks associated with information technology.
What are technology audits in the context of cybersecurity?
Evaluations of an organization's IT systems to ensure compliance with policies and standards.
What is the purpose of information security policies and standards?
To establish guidelines for protecting information assets and ensuring compliance.
What does the term 'cybersecurity talent gap' refer to?
The shortage of skilled professionals in the cybersecurity field.

What is the goal of the course on Cybersecurity Governance?
To understand the importance of cybersecurity and governance programs in achieving organizational goals.