Computer Science, Midterm
5.0(1)
Card Sorting
1/84
Earn XP
Description and Tags
Study Analytics
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
85 Terms
1
New cards
Bit
The smallest unit of information in a computer, it is either a 0 or a 1.
2
New cards
Byte
A series of 8 bits.
3
New cards
How do computing devices represent complex information.
Patterns of bits.
4
New cards
Abstraction
When a programmer hides all but the relevant data about an object in order to reduce complexity and increase efficiency.
Common ones include numbers, characters, and colors.
Common ones include numbers, characters, and colors.
5
New cards
Analog
Data with values that change continuously, or smoothly, over time. Some examples include music, colors of a painting, or position of a sprinter during a race.
6
New cards
Dialog
Data that changes discreetly through a finite set of possible values.
7
New cards
What is the smallest number for which an overflow error occur in a 3-bit computer?
8
8
New cards
What are overflow errors?
With a set amount of bits, some numbers may not be able to be represented, and the binary will "overflow." Fixed numbers will never eliminate the possibility of overflow errors.
9
New cards
What are round-off errors?
When a number that is too precise is attempted to be represented. Fixed numbers will never eliminate the possibility of round-off errors.
10
New cards
What number does the binary representation system start with?
0
11
New cards
Lossy Compression
Removes parts of the original algorithm, minimizes the amount of bits, reduces data size, will not be able to recreate the original algorithm.
12
New cards
Lossless Compression
Packs similar data, will be able to recreate the original algorithm.
13
New cards
Copyright
Applies to all material, even if it is digitized.
14
New cards
What is Creative Commons?
Copyright that enables creators to freely distribute their otherwise copyrighted work.
15
New cards
Could the same sequence of bits represent different types of information?
Yes
16
New cards
Computing Device
A machine that can run a program.
17
New cards
Computing System
A group of computers working together for a common purpose.
18
New cards
Computing Network
A group of connected computers that can send or receive data.
19
New cards
Path
A sequence of direct connections.
20
New cards
Internet Protocols
The Internet protocols are open and used by all devices connected to the network.
They did not change and were designed with the intent that more devices would connect over time.
They did not change and were designed with the intent that more devices would connect over time.
21
New cards
How does data travel from one device to another?
Using any path it wishes to, the data travels from one location to the other.
As long as the two decided are using the same protocols.
As long as the two decided are using the same protocols.
22
New cards
Packet Metadata
The location/IP address added to packets to tell them where to go and how to reassemble, it must be included in every packet.
23
New cards
Packet
Sent data is always divided into packets.
Not always received in the order they are sent.
Take different paths.
Not always received in the order they are sent.
Take different paths.
24
New cards
IP Address
A unique number for identifying devices that send and receive information on the Internet. It is able to be changed.
25
New cards
Which Internet protocol reassembles packets and requests missing packets to form complete messages?
Transmission Control Protocol (TCP)
26
New cards
Which of the following Internet protocols is used to request and send pages and files on the World Wide Web?
Hyper Text Transfer Protocol (HTTP)
27
New cards
Redundancy
Allows devices to stay connected when a particular path is no longer available, making the Internet fault-tolerable and making networks more reliable. This can be done by adding connections to the network.
28
New cards
Design Specification
Requirements for how a program will work and how users will interact with it.
29
New cards
Element ID
The name given to an element of code in order to identify it easily.
30
New cards
What is a string?
A command in quotations, this could be a number or a word, numbers do not need to be in quotations.
31
New cards
Event-Driven Programming
Some program statements run when triggered by an event, like a mouse click or a key press. Programs run differently each time depending on user interactions.
32
New cards
Sequential Programming
Program statements run in order, from top to bottom. No user interaction. Code runs the same way every time.
33
New cards
Comments
Form of program documentation written into the program to be read by people and which do not affect how a program runs.
34
New cards
Pair Programming
A collaborative programming style in which two programmers switch between the roles of writing code and tracking or planning high level progress.
A driver manipulates the keyboard and the mouse, whereas a navigator keeps track of the big picture, and guides the driver towards the goal.
A driver manipulates the keyboard and the mouse, whereas a navigator keeps track of the big picture, and guides the driver towards the goal.
35
New cards
Documentation
A written description of how a command or piece of code works or was developed.
36
New cards
Debugging Strategies
-Keeping your code clean
-Running your code frequently
-Use classmates and resources
-Running your code frequently
-Use classmates and resources
37
New cards
Program
A collection of program statements. Programs run (or “execute”) one command at a time.
38
New cards
Program Statement
A command or instruction. Sometimes also referred to as a code statement.
39
New cards
User Interface
The inputs and outputs that allow a user to interact with a piece of software. User interfaces can include a variety of forms such as buttons, menus, images, text, and graphics.
40
New cards
Input
Data that are sent to a computer for processing by a program. Can come in a variety of forms, such as tactile interaction, audio, visuals, or text.
41
New cards
Output
Any data that are sent from a program to a device. Can come in a variety of forms, such as tactile interaction, audio, visuals, or text.
42
New cards
User Datagram Protocol (UDP)
Used to send and receive packets quickly without error checking.
43
New cards
Topic ideas you came up with. How you and your partner decided upon your final topic.
Sleep resources, waze for amusement parks, and clothing app that helps with outfits.
We both love fashion and Pinterest and decided it would be the most helpful app to design.
We both love fashion and Pinterest and decided it would be the most helpful app to design.
44
New cards
Information gained by interviewing potential users of the app regarding their prior knowledge and how you used this information to plan your app.
Both knew of Pinterest and used it to create outfits, but had not heard of something similar to our app idea.
One recommended a shop to recommend clothing purchase and the other recommended a quiz for clothing in regard to color.
We ended up including both.
One recommended a shop to recommend clothing purchase and the other recommended a quiz for clothing in regard to color.
We ended up including both.
45
New cards
Your initial plan for the app, including layout and functionality.
An app where photos can be uploaded, and with that the app can create outfits from scratch, or based on a specific item. The app also allows one to upload an inspirational photo and will create a similar outfit out of clothes in your uploaded closet.
Included a quiz page, store, search, account, and home page.
Included a quiz page, store, search, account, and home page.
46
New cards
Changes you made during the development process and why you made them.
Added more screens, allowing the user to have more control over what the app does.
Added noise when you open the app, something fun for the users.
Added noise when you open the app, something fun for the users.
47
New cards
A brief description of the layout and functionality of your final app, including inputs and outputs.
Some of the app’s functions include allowing the users to upload photos of clothing to create their online closet, following other users and saving their outfits, building and having outfits built for them out of clothing they already have in their closets, taking fashion quizzes to find out their unique style, recommending stores and purchasing online clothing shops, and searching for outfits for any occasion.
Starts on a blank screen with the actual app icon, when clicked, it makes a cute noise and takes the user to the screen.
The user can toggle between the account, home, search, quiz, and store pages.
When going into settings, notifications can be turned off, the screen can be changed from dark to light mode, the app can be logged out of, or the account can be deleted.
Starts on a blank screen with the actual app icon, when clicked, it makes a cute noise and takes the user to the screen.
The user can toggle between the account, home, search, quiz, and store pages.
When going into settings, notifications can be turned off, the screen can be changed from dark to light mode, the app can be logged out of, or the account can be deleted.
48
New cards
Sampling
A process for creating a digital representation of analog data by measuring the analog data at regular intervals called samples.
49
New cards
Which of the following best describes how computing devices represent information?
A.) A computer will either represent information as bits or bytes but not both.
B.) A computer represents data as a byte which is either a 0 or 1.
C.) A computer represents data as a bit which is either a 0 or a 1.
D.) A computer represents information as bits that contain 8 bytes.
A.) A computer will either represent information as bits or bytes but not both.
B.) A computer represents data as a byte which is either a 0 or 1.
C.) A computer represents data as a bit which is either a 0 or a 1.
D.) A computer represents information as bits that contain 8 bytes.
C.) A computer represents data as a bit which is either a 0 or a 1.
50
New cards
Which of the following is NOT true of how computers represent complex information?
A.) Computing devices use patterns of bits to represent complex information.
B.) Abstraction helps represent complex information by surfacing complexity that might otherwise be hidden.
C.) Depending on the context the same sequence of bits may represent different types of information.
D.) Common abstractions represented by computing devices include numbers, characters, and color.
A.) Computing devices use patterns of bits to represent complex information.
B.) Abstraction helps represent complex information by surfacing complexity that might otherwise be hidden.
C.) Depending on the context the same sequence of bits may represent different types of information.
D.) Common abstractions represented by computing devices include numbers, characters, and color.
B.) Abstraction helps represent complex information by surfacing complexity that might otherwise be hidden.
51
New cards
When visiting a museum Lian takes a photo of a painting with a smartphone which stores the photo as an image file. Which of the following best describes the difference between the painting itself and the photo of the painting stored on the smartphone?
A.) Both the painting and the photo are analog.
B.) The photo is a digital representation of the analog painting.
C.) Sampling can be used to determine whether the analog image is an accurate representation of the painting.
D.) The phone can represent the photo in either digital or analog formats depending on the sampling technique that is used.
A.) Both the painting and the photo are analog.
B.) The photo is a digital representation of the analog painting.
C.) Sampling can be used to determine whether the analog image is an accurate representation of the painting.
D.) The phone can represent the photo in either digital or analog formats depending on the sampling technique that is used.
B.) The photo is a digital representation of the analog painting.
52
New cards
Your computer uses 4 bits to represent decimal numbers in binary. What is the smallest number for which an overflow error occurs?
A.) 14
B.) 15
C.) 16
D.) 17
A.) 14
B.) 15
C.) 16
D.) 17
C.) 16
53
New cards
Which of the following is true of how computers represent numbers?
A.) Using a fixed but large number of bits can eliminate the possibility of round-off error when representing numbers in binary.
B.) With a fixed number of bits some numbers are too large to represent in a computer, which will lead to overflow errors.
C.) Using a fixed but large number of bits, for example, 128, eliminates the possibility of overflow errors.
D.) With a large but fixed number of bits it is possible to eliminate either round-off errors or overflow errors, but not both.
A.) Using a fixed but large number of bits can eliminate the possibility of round-off error when representing numbers in binary.
B.) With a fixed number of bits some numbers are too large to represent in a computer, which will lead to overflow errors.
C.) Using a fixed but large number of bits, for example, 128, eliminates the possibility of overflow errors.
D.) With a large but fixed number of bits it is possible to eliminate either round-off errors or overflow errors, but not both.
B.) With a fixed number of bits some numbers are too large to represent in a computer, which will lead to overflow errors.
54
New cards
Which of the following binary numbers is the largest?
A.) 11000000
B.) 011111111
C.) 00000001
D.) 101111111
A.) 11000000
B.) 011111111
C.) 00000001
D.) 101111111
A.) 11000000
55
New cards
How many total numbers can be represented with an 8-bit binary system?
A.) 127
B.) 128
C.) 255
D.) 256
A.) 127
B.) 128
C.) 255
D.) 256
D.) 256
56
New cards
Which of the following is true of lossy and lossless compression algorithms?
A.) Lossy compression algorithms are used when perfect reconstruction of the original data is important.
B.) Lossy compression algorithms are typically better than lossless compression.
C.) Lossless compression algorithms are only used to compress text data.
D.) Lossless compression algorithms only allow for an approximate reconstruction of the original data.
A.) Lossy compression algorithms are used when perfect reconstruction of the original data is important.
B.) Lossy compression algorithms are typically better than lossless compression.
C.) Lossless compression algorithms are only used to compress text data.
D.) Lossless compression algorithms only allow for an approximate reconstruction of the original data.
B.) Lossy compression algorithms are typically better than lossless compression.
57
New cards
Jorge is sending a large file to a friend as a part of a shared classroom project. Which of the following is most likely true if Jorge opts to compress the image before sending it?
A.) The image can no longer be represented using bits.
B.) The image will have been converted into an analog form.
C.) The image will require more pixels to display on the screen.
D.) The image will require fewer bits in order to be represented.
A.) The image can no longer be represented using bits.
B.) The image will have been converted into an analog form.
C.) The image will require more pixels to display on the screen.
D.) The image will require fewer bits in order to be represented.
D.) The image will require fewer bits in order to be represented.
58
New cards
Which of the following is true of intellectual property?
A.) Information created on a computer is not owned by anyone since only analog information is protected under copyright law.
B.) You do not need to cite work created by someone else if both the original work and your use of it are in digital form.
C.) Creative Commons enables content creators to freely distribute their otherwise copyrighted work.
D.) Creative Commons has severely hindered broad and open access to digital information.
A.) Information created on a computer is not owned by anyone since only analog information is protected under copyright law.
B.) You do not need to cite work created by someone else if both the original work and your use of it are in digital form.
C.) Creative Commons enables content creators to freely distribute their otherwise copyrighted work.
D.) Creative Commons has severely hindered broad and open access to digital information.
C.) Creative Commons enables content creators to freely distribute their otherwise copyrighted work.
59
New cards
Lucy is completing a project as part of a science class using materials she found online. Which of the following is most likely to lead to legal consequences?
A.) Modifying a piece of open-source software.
B.) Using open access research for when she does not acquire a license.
C.) Failing to publish her work under a Creative Commons license.
D.) Using images posted online by another student without permission or citation.
A.) Modifying a piece of open-source software.
B.) Using open access research for when she does not acquire a license.
C.) Failing to publish her work under a Creative Commons license.
D.) Using images posted online by another student without permission or citation.
D.) Using images posted online by another student without permission or citation.
60
New cards
A “computing device” can be defined as…
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
B.) A machine that can run a program.
61
New cards
A “computing system” can be defined as…
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
D.) A group of computers working together for a common purpose.
62
New cards
A “computing network” can be defined as…
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
C.) A group of connected computers that can send or receive data.
63
New cards
A “path” can be defined as…
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
A.) A sequence of direct connections.
B.) A machine that can run a program.
C.) A group of connected computers that can send or receive data.
D.) A group of computers working together for a common purpose.
A.) A sequence of direct connections.
64
New cards
Which of the following best describes the protocols used on the Internet?
A.) The protocols of the Internet are designed by government agencies to ensure they remain free to use.
B.) The protocols of the Internet are secret to maintain the privacy and security of people using them.
C.) Each device connected to the Internet will use a protocol designed by the company that manufactured it.
D.) The protocols of the Internet are open and used by all devices connect to the network.
A.) The protocols of the Internet are designed by government agencies to ensure they remain free to use.
B.) The protocols of the Internet are secret to maintain the privacy and security of people using them.
C.) Each device connected to the Internet will use a protocol designed by the company that manufactured it.
D.) The protocols of the Internet are open and used by all devices connect to the network.
D.) The protocols of the Internet are open and used by all devices connect to the network.
65
New cards
Jesse purchases a new smartphone and is immediately able to use it to send a photo over the Internet to a friend who lives in a different country. Which of the following is not necessary to make this possible?
A.) Both devices are using the same shared and open protocols.
B.) A single direct connection is established between any two devices connected to the Internet.
C.) The data of the image is routed through a sequence of directly connected devices before arriving at its destination.
D.) Both devices are directly connected to at least one part of the Internet.
A.) Both devices are using the same shared and open protocols.
B.) A single direct connection is established between any two devices connected to the Internet.
C.) The data of the image is routed through a sequence of directly connected devices before arriving at its destination.
D.) Both devices are directly connected to at least one part of the Internet.
B.) A single direct connection is established between any two devices connected to the Internet.
66
New cards
Which of the following is true of how the Internet has responded to the increasing number of devices now using the network?
A.) Internet protocols are changed every year to adapt to the new devices that have been connected to the network.
B.) While the number of devices connected to the Internet had grown, the network itself has not grown.
C.) The protocols of the Internet were designed to scale as new devices are added.
D.) The protocols of the Internet are no longer necessary thanks to the large number of devices now connected to the network.
A.) Internet protocols are changed every year to adapt to the new devices that have been connected to the network.
B.) While the number of devices connected to the Internet had grown, the network itself has not grown.
C.) The protocols of the Internet were designed to scale as new devices are added.
D.) The protocols of the Internet are no longer necessary thanks to the large number of devices now connected to the network.
C.) The protocols of the Internet were designed to scale as new devices are added.
67
New cards
Which of the following is true of how packets are sent through the Internet?
A.) Packet metadata is the only included on important packets to indicate they should get access to faster paths through the network.
B.) Packet metadata is used to route and reassemble information traveling through the Internet.
C.) Information sent through the Internet is only encapsulated in packets if the message is too large to be sent as a data stream.
D.) Information sent through the Internet is split into two packets, one which contains the message and another which contains the metadata.
A.) Packet metadata is the only included on important packets to indicate they should get access to faster paths through the network.
B.) Packet metadata is used to route and reassemble information traveling through the Internet.
C.) Information sent through the Internet is only encapsulated in packets if the message is too large to be sent as a data stream.
D.) Information sent through the Internet is split into two packets, one which contains the message and another which contains the metadata.
B.) Packet metadata is used to route and reassemble information traveling through the Internet.
68
New cards
Emilee is watching an online video. The video is being sent to her laptop by a server over the Internet which splits the video into packets and sends them in the order they appear in the video. Which of the following is true about how the packets will arrive at her computer?
A.) The packets will always be received in the order they were sent.
B.) Either every packet will reach her computer or none of them will.
C.) Packets that arrive out of order will be sent back to the server.
D.) The packets may arrive out of order.
A.) The packets will always be received in the order they were sent.
B.) Either every packet will reach her computer or none of them will.
C.) Packets that arrive out of order will be sent back to the server.
D.) The packets may arrive out of order.
D.) The packets may arrive out of order.
69
New cards
Which of the following best describes the purpose of an IP address?
A.) IP addresses provide a unique number for identifying devices that send and receive information on the Internet.
B.) IP addresses assist in the reconstruction of a message that has been divided into many packets.
C.) IP addresses indicate the location where an internet-connected computing device.
D.) IP addresses indicate how many times an individual packet has been requested by a router.
A.) IP addresses provide a unique number for identifying devices that send and receive information on the Internet.
B.) IP addresses assist in the reconstruction of a message that has been divided into many packets.
C.) IP addresses indicate the location where an internet-connected computing device.
D.) IP addresses indicate how many times an individual packet has been requested by a router.
A.) IP addresses provide a unique number for identifying devices that send and receive information on the Internet.
70
New cards
Which of the following Internet protocols is MOST important in reassembling packets and requesting missing packets to form complete messages?
A.) Transmission Control Protocol (TCP)
B.) Internet Protocol (IP)
C.) User Datagram Protocol (UDP)
D.) HypterText Transfer Protocol (HTTP)
A.) Transmission Control Protocol (TCP)
B.) Internet Protocol (IP)
C.) User Datagram Protocol (UDP)
D.) HypterText Transfer Protocol (HTTP)
A.) Transmission Control Protocol (TCP)
71
New cards
Which of the following Internet protocols is used to request and send pages and files on the World Wide Web?
A.) Transmission Control Protocol (TCP)
B.) Internet Protocol (IP)
C.) User Datagram Protocol (UDP)
D.) HypterText Transfer Protocol (HTTP)
A.) Transmission Control Protocol (TCP)
B.) Internet Protocol (IP)
C.) User Datagram Protocol (UDP)
D.) HypterText Transfer Protocol (HTTP)
D.) HypterText Transfer Protocol (HTTP)
72
New cards
Two devices are connected to the Internet and communicate with one another. A squirrel chews through one of the wires in the network that is currently being used by the devices to communicate. The network immediately begins using a different path through the network and communication continues as normal. This situation best exemplifies which principle?
A.) Fault-tolerance
B.) Scalability
C.) Protocol
D.) Pathing
A.) Fault-tolerance
B.) Scalability
C.) Protocol
D.) Pathing
A.) Fault-tolerance
73
New cards
An Internet Service Provider (ISP) is a company that buids the routers and wired connections that allow individuals to access the Internet. An ISP is considering adding additional redundant connections to its network. Which of the following best describes why the company would choose to do so?
A.) It costs less to design a network that is redundant.
B.) The protocols of the Internet only work on networks that are redundant.
C.) Redundant networks are more reliable.
D.) Adding additional connections reduces the fault tolerance of the network.
A.) It costs less to design a network that is redundant.
B.) The protocols of the Internet only work on networks that are redundant.
C.) Redundant networks are more reliable.
D.) Adding additional connections reduces the fault tolerance of the network.
C.) Redundant networks are more reliable.
74
New cards
Which of the following actions would usually be helpful in designing and developing an app?
A.) Interviewing potential users of the app.
B.) Writing the entire program code before testing any parts of it.
C.) Observing users attempting to use the app.
A.) Interviewing potential users of the app.
B.) Writing the entire program code before testing any parts of it.
C.) Observing users attempting to use the app.
A.) Interviewing potential users of the app. C.) Observing users attempting to use the app.
75
New cards
Which of the following best describes the purpose of a design specification?
A.) Tracking errors that arise through user testing.
B.) Documenting comments that will need to be added to a program.
C.) Describing the requirements for how a program will work or users will interact with it.
D.) Listing detailed questions that will be asked of users during interviews.
A.) Tracking errors that arise through user testing.
B.) Documenting comments that will need to be added to a program.
C.) Describing the requirements for how a program will work or users will interact with it.
D.) Listing detailed questions that will be asked of users during interviews.
C.) Describing the requirements for how a program will work or users will interact with it.
76
New cards
Which of the following best describes the differences between sequential and event-driven programming?
A.) In sequential programming commands run one at a time. In event-driven programming, all commands run at the same time.
B.) In sequential programming commands run faster than in event-driven programming.
C.) In sequential programming each command is run many times in sequence. In event-driven programming, all commands are run a single time as an event.
D.) In sequential programming commands run in the order they are written. In event-driven programming, some commands run in response to user interactions or other events.
A.) In sequential programming commands run one at a time. In event-driven programming, all commands run at the same time.
B.) In sequential programming commands run faster than in event-driven programming.
C.) In sequential programming each command is run many times in sequence. In event-driven programming, all commands are run a single time as an event.
D.) In sequential programming commands run in the order they are written. In event-driven programming, some commands run in response to user interactions or other events.
D.) In sequential programming commands run in the order they are written. In event-driven programming, some commands run in response to user interactions or other events.
77
New cards
Which of the following is NOT a reason to include comments in programs?
A.) Comments help the computer decide whether certain components of a program are important.
B.) Comments help programmers debug issues in their own code.
C.) Comments help document how code was written for other programmers to use.
D.) Comments enable programmers to track their work throughout the development process.
A.) Comments help the computer decide whether certain components of a program are important.
B.) Comments help programmers debug issues in their own code.
C.) Comments help document how code was written for other programmers to use.
D.) Comments enable programmers to track their work throughout the development process.
A.) Comments help the computer decide whether certain components of a program are important.
78
New cards
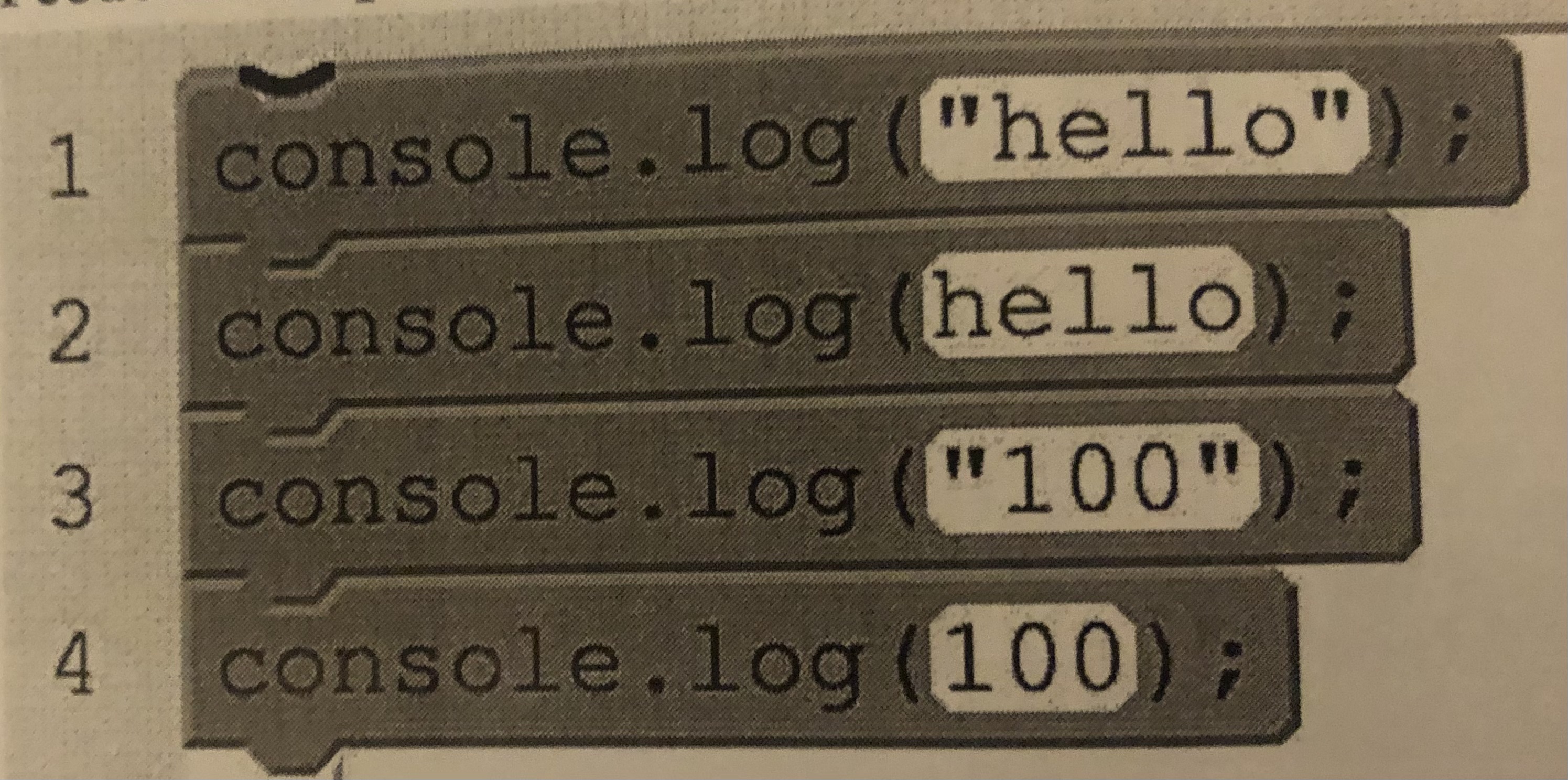
Which line code in this program is most likely to result in an error?
A.) 1
B.) 2
C.) 3
D.) 4
A.) 1
B.) 2
C.) 3
D.) 4
B.) 2
79
New cards
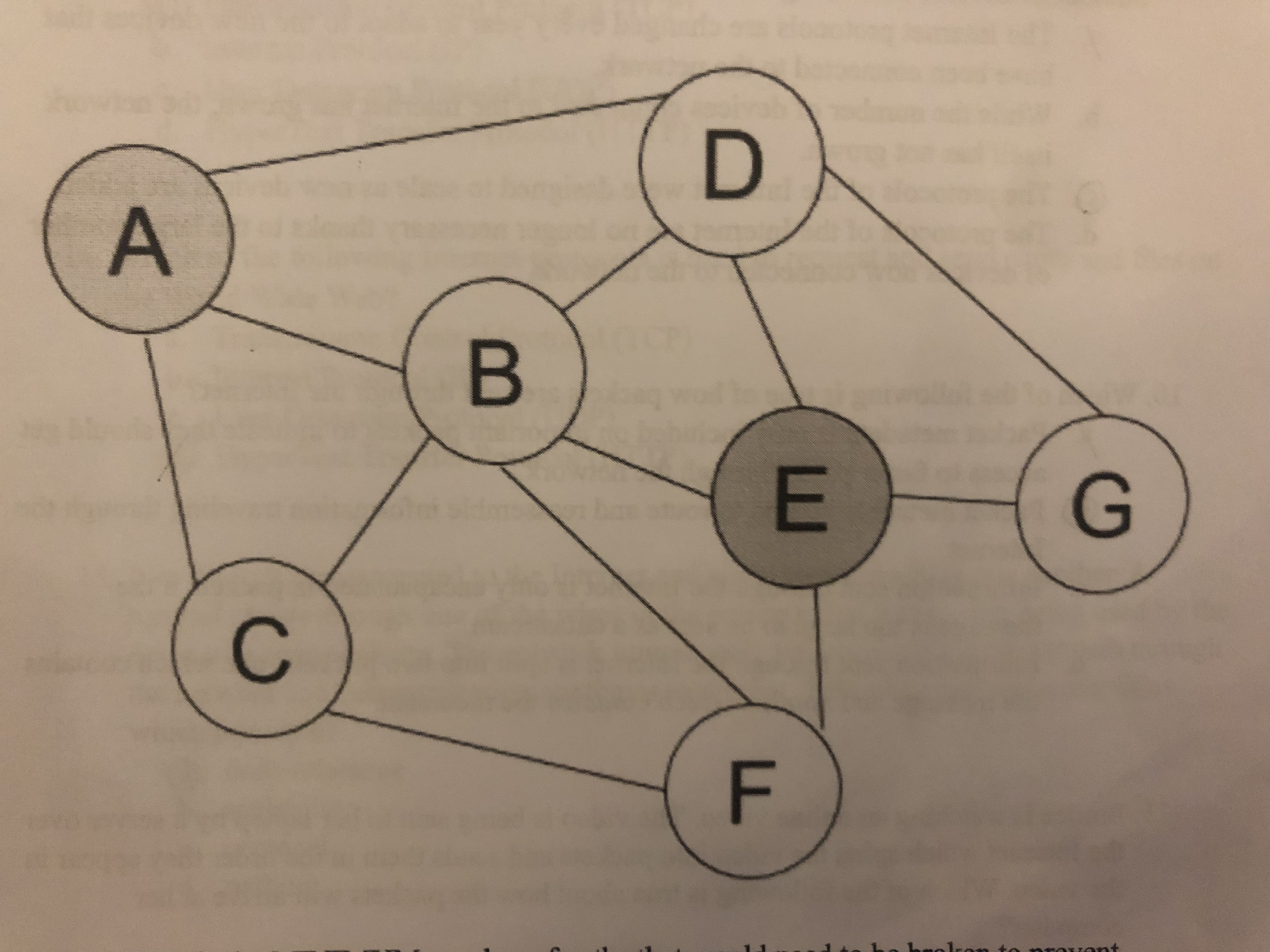
What is the minimum number of paths that would need to be broken to prevent Computing Device A from connecting with Computing Device E?
A.) 1
B.) 2
C.) 3
D.) 4
A.) 1
B.) 2
C.) 3
D.) 4
C.) 3
80
New cards
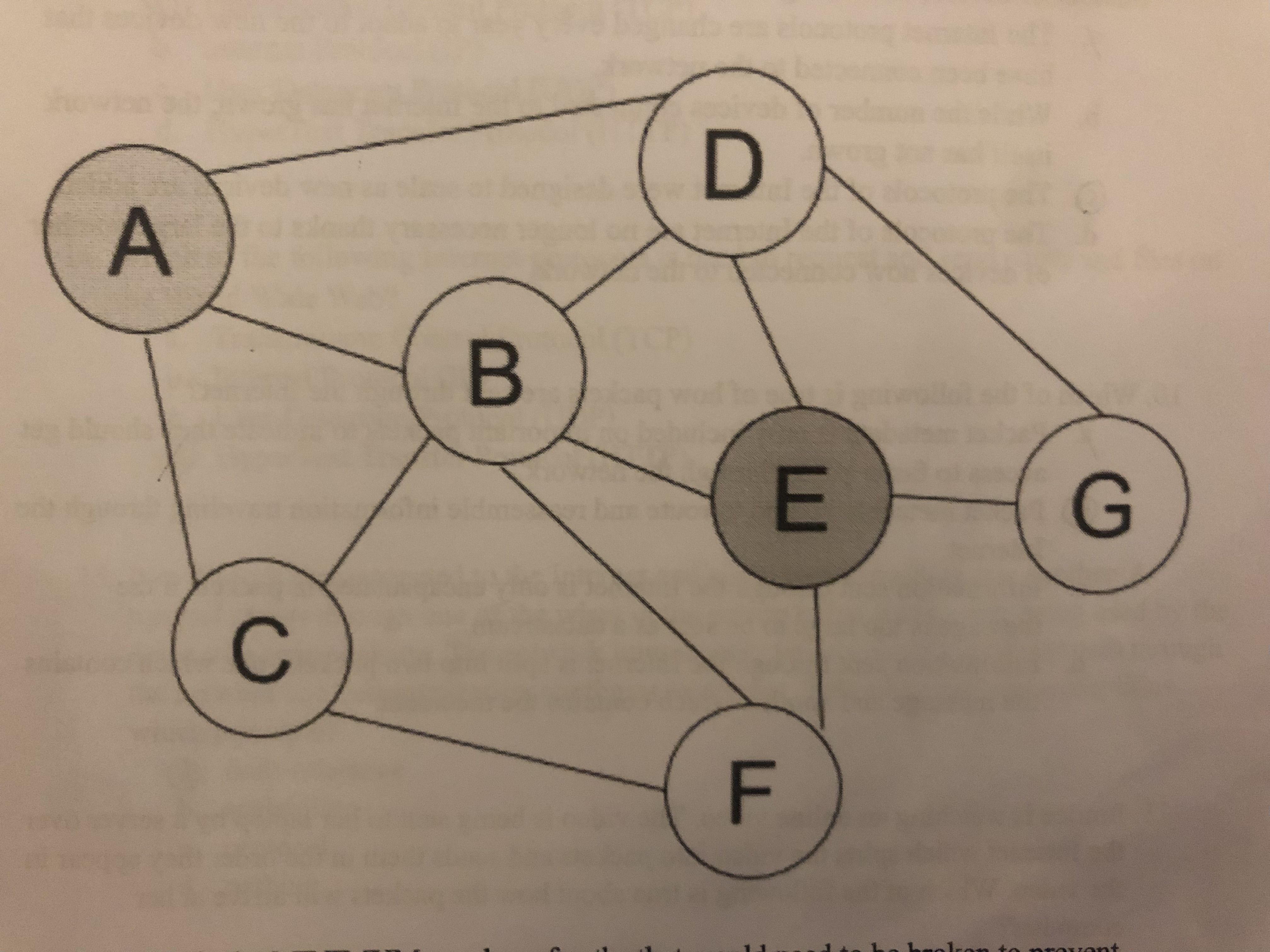
Device A is attempting to send data over the Internet to Device E. Which of the following is true of how data will travel through the network?
A.) The data will always travel through Device B as it is the shortest path.
B.) The data will never be sent to Device G since there are other, shorter paths available.
C.) It is possible that the data travels through any of the devices in the network before arriving at Device E.
D.) If the data travels through Device D then it will not travel through Device B.
A.) The data will always travel through Device B as it is the shortest path.
B.) The data will never be sent to Device G since there are other, shorter paths available.
C.) It is possible that the data travels through any of the devices in the network before arriving at Device E.
D.) If the data travels through Device D then it will not travel through Device B.
C.) It is possible that the data travels through any of the devices in the network before arriving at Device E.
81
New cards
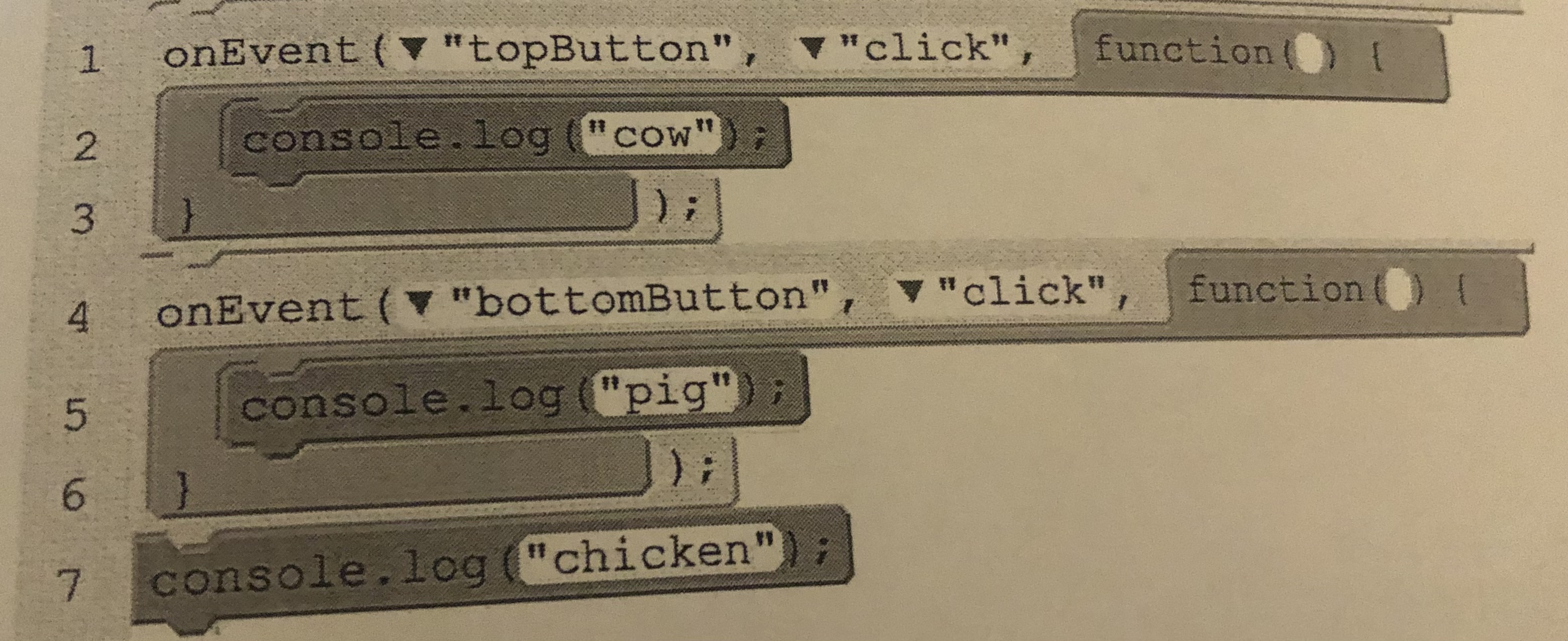
The following program is run. Then the user clicks the “bottomButton” once ad then clicks the “topButton” once. What will be displayed in the console?
A.) cow pig chicken
B.) cow chicken pig
C.) pig cow chicken
D.) chicken pig cow
A.) cow pig chicken
B.) cow chicken pig
C.) pig cow chicken
D.) chicken pig cow
D.) chicken pig cow
82
New cards
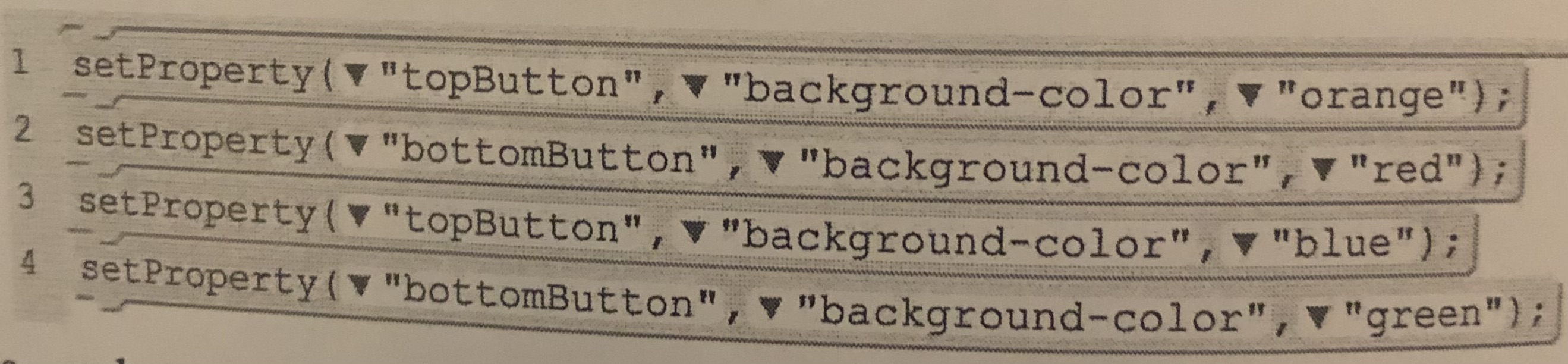
What will the “background-color” of the “topButton” be when the program is finished running?
A.) red
B.) orange
C.) blue
D.) green
A.) red
B.) orange
C.) blue
D.) green
C.) blue
83
New cards
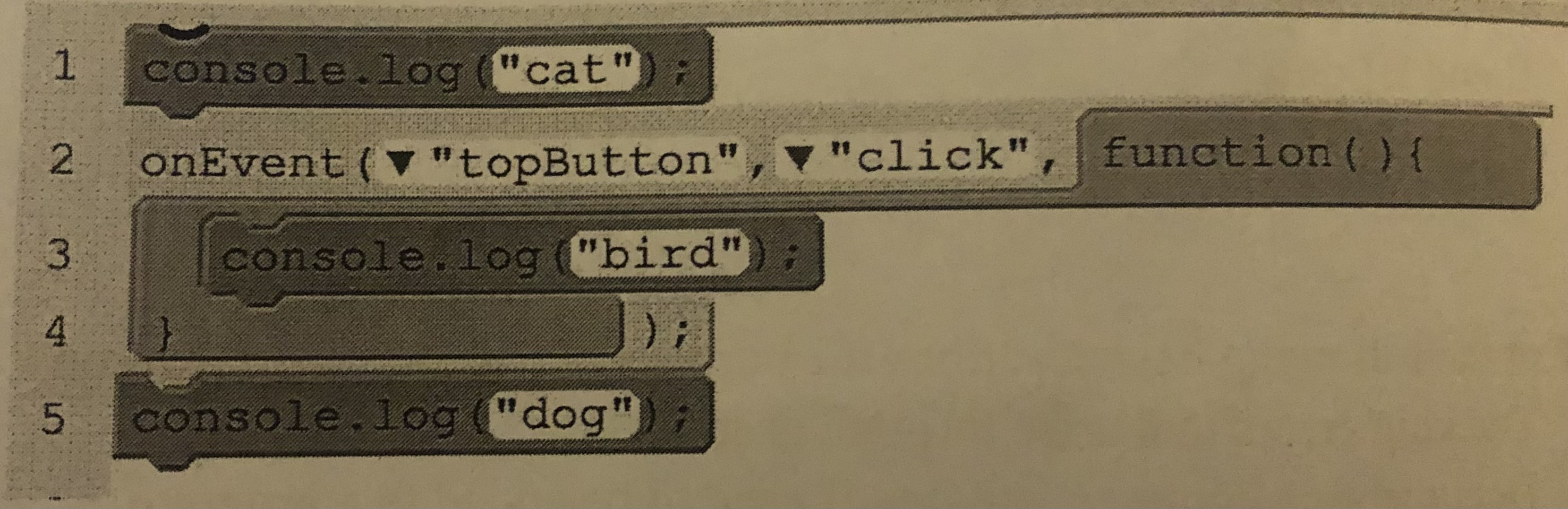
The following program is run. Then the user clicks the “topButton” button once. What will be displayed in the console?
A.) cat bird dog
B.) dog cat bird
C.) cat dog bird
D.) bird cat dog
A.) cat bird dog
B.) dog cat bird
C.) cat dog bird
D.) bird cat dog
C.) cat dog bird
84
New cards
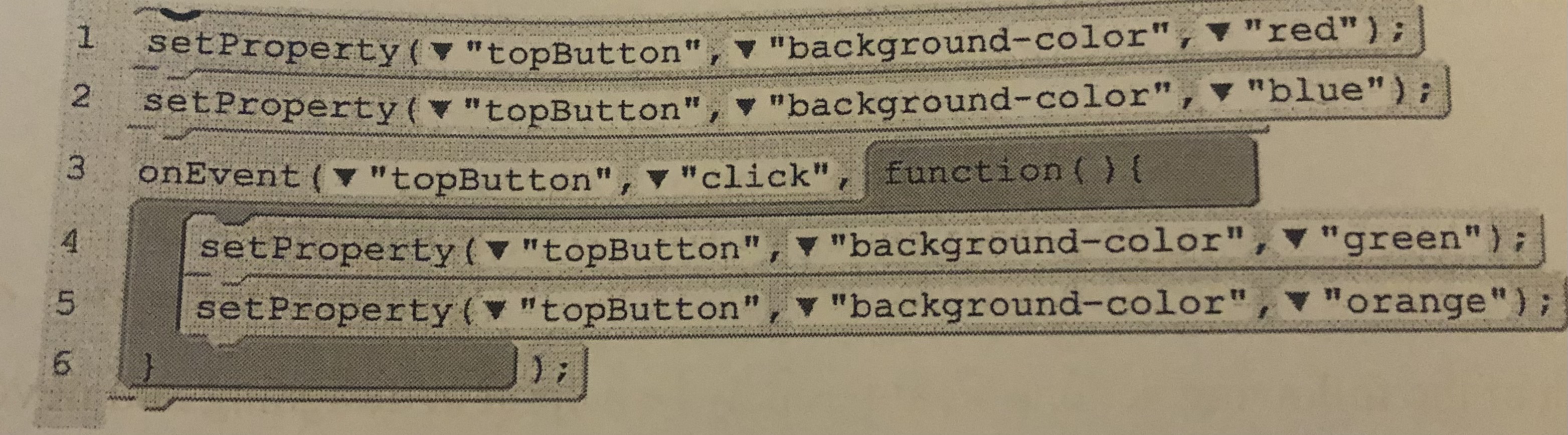
If the user does NOT click the button what color will “topButton” be when this program finishes running?
A.) red
B.) blue
C.) green
D.) orange
A.) red
B.) blue
C.) green
D.) orange
B.) blue
85
New cards

The following program is run. Then the user clicks the “bottomButton” two times. What will be displayed in the console?
A.) apple banana cherry cherry dragon fruit
B.) banana dragon fruit cherry cherry
C.) banana dragon fruit apple apple
D.) banana cherry cherry dragon fruit
A.) apple banana cherry cherry dragon fruit
B.) banana dragon fruit cherry cherry
C.) banana dragon fruit apple apple
D.) banana cherry cherry dragon fruit
B.) banana dragon fruit cherry cherry