EXAM2
1/69
Earn XP
Description and Tags
chapter 9,18,3,23,22b, 13, COCOMO
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
70 Terms
Program evolution dynamics
The study of the process of system change.
What did Lehman and Belady propose after major empirical studies.
There were a number of ‘laws’ which applied to all systems as they evolved.
(more like sensible observations rather than laws. They are applicable to large systems devolved by large organizations. Perhaps less applicable in other cases.)
Lehman’s law
Continuing change
Increasing complexity
Large program evolution
Organizational stability
Conservation of Familiarity
Continuing growth
Declining Quality
Feedback system
What are Lehman’s laws applicable to?
Large, tailored systems developed by large organizations
(Confirmed in more recent work by Lehman on the FEAST project)
For applicability of Lehman’s laws it is not clear how they should be modified for?
Shrink-wrapped software products
Systems that incorporate a significant number of COTS components
Small organizations
Medium sized systems
Software maintenance
Modifying a program after it has been put into use
Does not normally involve major changes to the system’s architecture.
Changes are implemented by modifying existing components and adding new components to the system
Types of maintenance
To repair system faults (to correct deficiencies)
To adapt software to a different operating environment (changing systems)
To add or modify the system’s functionality (to satisfy new requirements)
Distribution of maintenance effort for Fault repair? (percentage)
17%
Distribution of maintenance effort for Software adaptation? (percentage)
18%
Distribution of maintenance effort for Functionality addition/modification? (percentage)
65%
Distributed systems architectures
Client-server (services that are called on by clients) [servers that provide services are treated differently from clients that use them]
Distributed object (no distinction between clients and servers)
Middleware
Software that manages and supports different components of a distributed system
Usually off-the-shelf rather then specially written software
EX:
transaction processing monitors;
Data converters;
Communication controllers.
Multiprocessor architectures
Simplest distributed system model
System composed of multiple processes that may execute on different processors
model of large real-time systems
may be pre-ordered or under the control of a dispatcher
Client-server architectures
Application is modelled as a set of services that are provided servers and a set of clients that use them
Clients know of servers but servers need not know clients
Clients and servers are logical processes
Mapping to the processes is not 1 : 1
Layered application architecture
Presentation layer
- concerned with presenting the results of the computation to system users with collecting user input.Application processing layer
- concerned with providing application specific functionalityData management layer
- concerned with managing system databases
Thin-client model
all of the application processing and data management is carried out on the server. The client is simply responsible for running the presentation software
Fat-client model
the server is only responsible for data management. The software on the client implements the application logic and the interactions with the system user
COBRA
International standard for an Object Request Broker - middleware to manage communications between distributed objects
Middleware for distributed computing is required at 2 levels:
- at the logical communication level (allows objects on different computers to exchange data and control information)
- at the component level (provides a basis for developing compatible components)
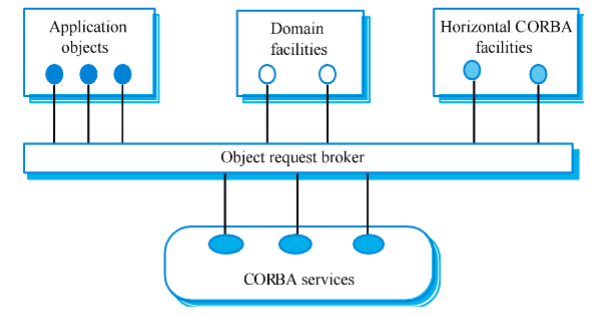
What structure is this?
COBRA
peer-to-peer architectures
Systems are decentralized systems where computations may be carried out by any node in the network
Overall system is designed to take advantage of the computational power and storage of a large number of networked computers
Most p2p systems have been personal systems but there is increasing business use of this technology.
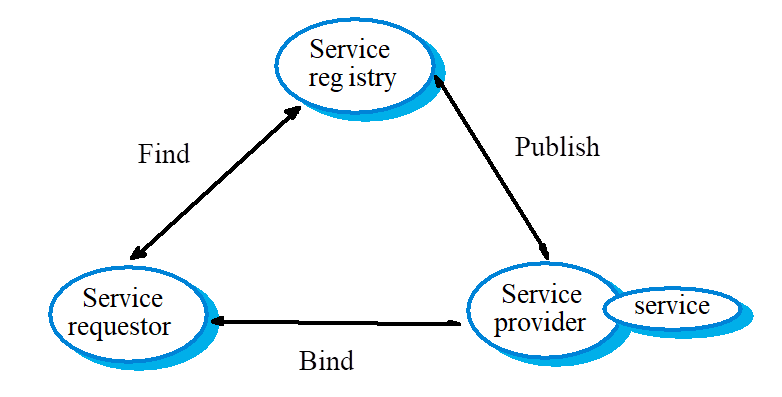
what is this a diagram of?
Web services
Services standards
are based on agreed, XML -based standards so can be provided on any platform and written in any programming language
Key standards
- SOAP
- WSDL
- UDDI
SOAP stands for
Simple Object Access Protocol
WSDL stands for?
Web services Description Language
UDDI stands for?
Universal Description, Discovery, and integration
Agile Manifesto
Individuals and interactions over processes and tools
Working software over comprehensive documentation
Customer collaboration over contract negotiation
Responding to change over following a plan
Principles of agile methods
Customer involvement
Incremental delivery
People not process
Embrace change
Maintain simplicity
Extreme programming practices
Incremental Planning
Small releases
Simple design
Test-first development
Refactoring
Examples of refactoring
Re-organization of a class hierarchy to remove duplicate code
Tidying up and renaming attributes and methods to make them easier to understand.
The replacement of inline code with calls to methods that have been included in a program library
Test automation
Tests are written as executable components before the task is implemented
Pair programming
Work in pairs, sitting together to develop code
Helps develop common ownership of code and spreads knowledge across the team
Serves an an informal review process as each line is looked at by more than 1 person
Encourages refactoring
similar to that of two people working independently
Software cost components
Hardware and software cost
Travel and training costs
Effort costs
Effort costs must take overheads into account
Software pricing factors
Market opportunity
Cost estimate uncertainty
Contractual terms
Requirements volatility
Financial health
Productivity measures
Size related: based on some output from the software process (lines of source code, object code instructions, etc.)
Function-related: based on an estimate of the functionality of the delivered software.
Factors affecting productivity
Application domain experience
Process quality
Project size
Technology support
Working environment
Estimation Techniques
Algorithmic cost modelling
Expert judgement
Estimation by analogy
Pricing to win
Motivation
An important role of a manager is to motivate the people on a project
It’s a complex issue but it has different types
- Basic needs
- Personal needs
- Social needs
Human needs hierarchy (1 is the top 5 is the bottom)
Self-realization needs
Esteem needs
Social needs
Safety needs
Physiological needs
Personality types
Needs hierarchy is an over-simplification
Different personality types
- Task-oriented
- Self-oriented
- Interaction-oriented
Task-oriented
The motivation for doing the work is the work itself
Self-oriented
The work is a means to an end which is the achievement of individual goals - e.g. to get rich, to play tennis, to travel etc.
Interaction-oriented
The principal motivation is the presence and actions of co-workers. People go to work because they like to go to work
Group organization
Software engineering group sizes should be relatively small (< 8 members)
Break big projects down into multiple smaller projects
Small teams may be organized in an informal, democratic way
Chief programmer teams try to make the most effective use of skills and experience
The people capability maturity model (five stages)
Initial
Repeatable
Defined
Managed
Optimizing
Security Dimensions
Confidentiality
Integrity
Availability
Asset
Something of value which has to be protected
Attack
An exploitation of a system’s vulnerability
Control
A protective measure that reduces system’s vulnerability
Exposure
Possible loss or harm to a computing system
Threat
Circumstances that have potential to cause loss or harm.
Vulnerability
A weakness in a computer-based-system that may be exploited to cause loss or harm
Threat types
Interception
Interruption
Modification
Fabrication
Interception
allow attackers to gain access to an asset
Interruption
Allows an attacker to make part of the system unavailable
Modification
Allow attackers to tamper with a system asset
Fabrication
allows attackers to insert false information into a system
What is Cocomo
Constructive Cost Model
SLOC
Source Line of code
1. One logical line of code
2. Declarations are counted as SLOC
3. Comments are not counted as SLOC
4. Only count delivered code
5. SOURCE lines are created by the project staff
COCOMO Scale Drivers
Precedentedness
Development Flexibility
Architecture/Risk resolution
Team Cohesion
Process Maturity
How many cost drivers does COCOMO have?
17
COCOMO Effort equation
= 2.94 EAF (KSLOC)^E
COCOMO Duration equation
= 3.67 (EFFORT)^SE
COCOMO Average Staff equation
= EFFORT/DURATION
Cloud Computing
Internet-based computing, where shared resources, software, and information are provided to computers and other devices on demand.
What services do cloud computing provide?
Reliability
Elasticity
Affordability
Cloud Computing types
Public
Private
Hybrid
Cloud Computing: Service Models
Infrastructure-as-a-Service (Iaas)
Platform-as-a-Service (PaaS)
Software-as-a-Service (SaaS)
IaaS examples
Amazon web service
Google compute engine
Azure
Digital Ocean
PaaS examples
Amazon web service
Google compute engine
Azure
heroku
Oracle
SaaS examples
Office 365
salesforce
Netflix
GoToMeeting
Google Docs