SASE HPE
0.0(0)
Card Sorting
1/53
There's no tags or description
Looks like no tags are added yet.
Last updated 12:25 PM on 6/1/23
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
54 Terms
1
New cards
N | LAN - Router four functional components
Nat
DMZ
Firewall
Port Forwarding
DMZ
Firewall
Port Forwarding
2
New cards
N | LAN - Gateway
a piece of networking hardware or software used in telecommunications networks that allows data to flow from one discrete network to another
3
New cards
N | LAN - Read these two IP addresses: 196.65.10.20 & 196.65.43.35
\
What can you concur about them?
\
What can you concur about them?
Because the first two values are the same they are in the same LAN
\
The first value and the second value are also the area measurement of the LAN
\
The first value and the second value are also the area measurement of the LAN
4
New cards
N | LAN - Router
networking device that forwards data packets between different computer networks (connects you to devices outside of your LAN)
5
New cards
Network
set of devices talking to each other in within a limited range
\
ex. All devices at your home connected to one wireless router (network)
\
ex. All devices at your home connected to one wireless router (network)
6
New cards
N | LAN
Local Area Network (devices connected to a router makes a LAN)
7
New cards
N | LAN - IP
logical address of a device (similar to sending mail to a physical address)
\
Devices can send messages to the other device by using their IP address (on a LAN)
\
Devices can send messages to the other device by using their IP address (on a LAN)
8
New cards
N | LAN - Switch
connects devices within the same network (close range)
9
New cards
N | LAN - Subnet (Subnetwork)
Defines your LAN range
10
New cards
N | WAN - Firewall
Set of passive rules that protect the network from unauthorized access
11
New cards
N | WAN - DMZ
Demilitarized Zone | One of two ways through the firewall
\
Subnetwork that contains and exposes a device to an untrusted network such as the internet (an extension of the LAN range)
\
Almost a waiting room where the asking device never actually reaches the LAN, the other device simply meets the asking device there
\
Subnetwork that contains and exposes a device to an untrusted network such as the internet (an extension of the LAN range)
\
Almost a waiting room where the asking device never actually reaches the LAN, the other device simply meets the asking device there
12
New cards
N | WAN - Port Forwarding
Setting in your router that connects WAN & LAN a different way
used to give external devices access to computers services on private networks. It does this by mapping an external port to an internal IP address and port.
used to give external devices access to computers services on private networks. It does this by mapping an external port to an internal IP address and port.
13
New cards
N | WAN - Nat
Network Address Translation
\
Remapping an IP address while they are in transit across a traffic routing device - a process that enables one, unique IP address to represent an entire group of computers
\
Remapping an IP address while they are in transit across a traffic routing device - a process that enables one, unique IP address to represent an entire group of computers
14
New cards
LAN vs WAN
Local Area network & Wide Area Network
15
New cards
Axis Security
cloud security provider
16
New cards
**Axis Security’s Security Services Edge (SSE) platform function**
improves application performance & Increases network security because:
* Number of remote users increases
* Enterprises continue to migrate applications to the cloud
* Number of remote users increases
* Enterprises continue to migrate applications to the cloud
17
New cards
The HPE GreenLake edge-to-cloud platform will _________ Axis Security’s cloud-native SSE platform, offering customers one single monthly subscription with no capital expenditure
integrate
18
New cards
SASE - SSE | SWG (Secure Web Gateway) (Pronounced Swig)
A point in between a user and the IoT (website, software,etc.) they are trying to reach (operates as a forward proxy - a.k.a. intermediary)
\
(used best with company issues devices)
\
* Enforces & reports on acceptable use policy
* Blocks known bad URL’s
* Protects from malicious file downloads
* Detects and blocks malicious content hosted within a site
\
(used best with company issues devices)
\
* Enforces & reports on acceptable use policy
* Blocks known bad URL’s
* Protects from malicious file downloads
* Detects and blocks malicious content hosted within a site
19
New cards
CASB
Visibility and policy control point that sits between users and the cloud
20
New cards
# **SD-WAN**
(software-defined wide area network)
is a type of networking technology that uses software-defined networking (SDN) principles to manage and optimize the performance of wide area networks (WANs).
is a type of networking technology that uses software-defined networking (SDN) principles to manage and optimize the performance of wide area networks (WANs).
21
New cards
SD-WAN | Explained
When we have a business that has many different branches, we can allow software to securely and automatically handle the configuration of the entire WAN infrastructure
\
(more of a concept) HPE’s SDWAN is SilverPeak
\
(more of a concept) HPE’s SDWAN is SilverPeak
22
New cards
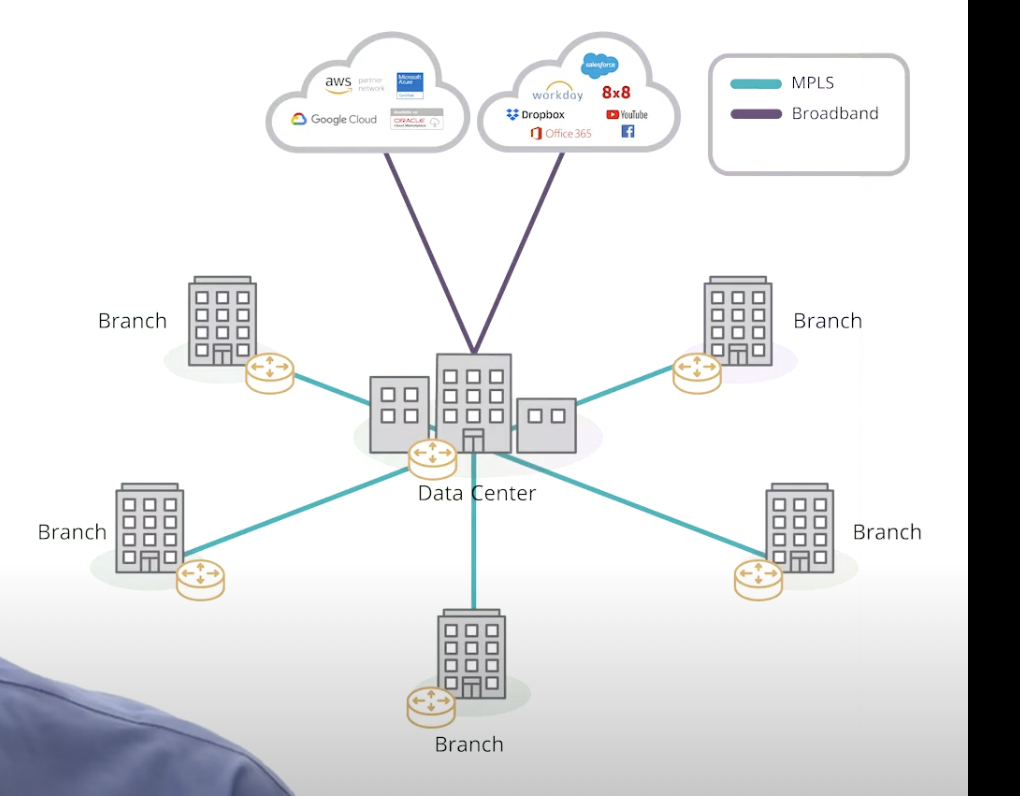
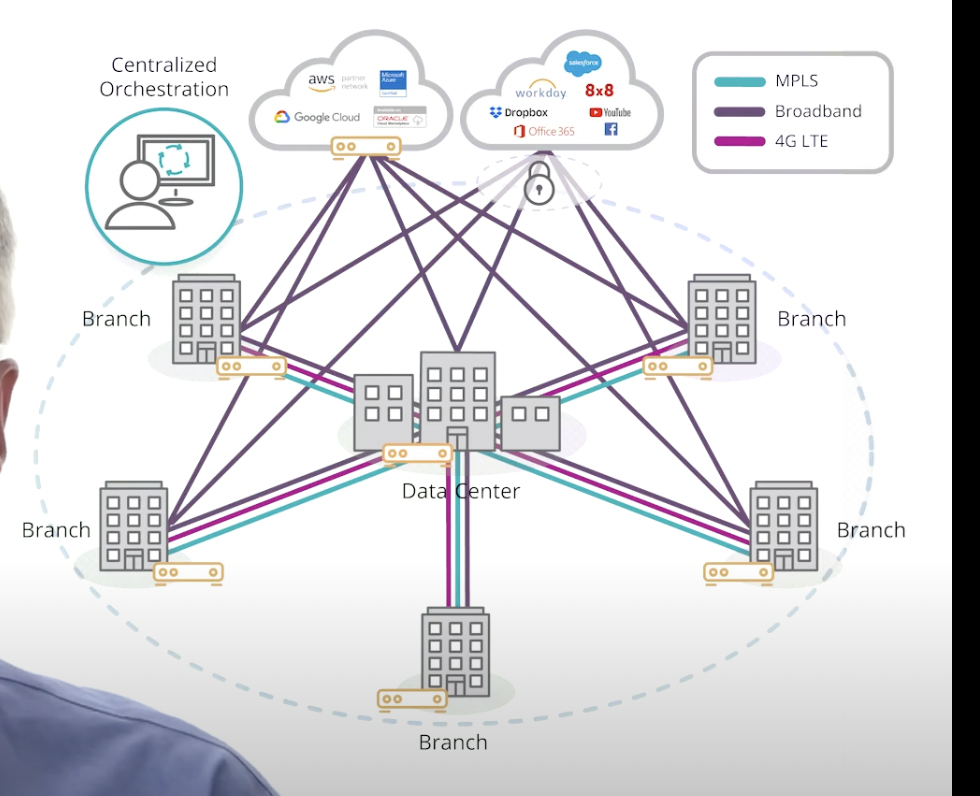
Router Centric Model (old) vs SD-WAN Model (New)
connects branch directly to the internet then to the software (salesforce, MS suite, etc.)
\
you can also control the security, settings, adding branch locations, etc. easier
\
“Cloud first WAN”
\
rather than running every request through the data center (router centric model)
\
you can also control the security, settings, adding branch locations, etc. easier
\
“Cloud first WAN”
\
rather than running every request through the data center (router centric model)
23
New cards
# **SASE | Secure Access Service Edge**
Secure Access Service Edge (one half of SASE)
24
New cards
SWG & ZTNA (Zero Trust) are under the umbrella of
SSE & SASE
25
New cards
SASE - SSE | CASB (Cloud Access Security Broker) (Pronounced Caz-B)
Visibility and policy control point that sits between users and the cloud (SaaS) (On-prem)
\
CASB Four Pillars:
* Visibility (see what users are doing/downloading)
* Compliance
* Threat Prevention
* Data Security
\
CASB Four Pillars:
* Visibility (see what users are doing/downloading)
* Compliance
* Threat Prevention
* Data Security
26
New cards
SASE | Zero Trust Security Model (Philosophy)
No more access given based on location (because before only people at the office building were accessing the network, now with WFH it could be anywhere)
* All users must be fully verified before being given as minimal access as possible to accomplish the task
* Set of areas accessible dependent on your job title/rank/etc.
* Verification is never suitable for an extended period of time, it is checked every single time & runs continuously as you are using the network
* All users must be fully verified before being given as minimal access as possible to accomplish the task
* Set of areas accessible dependent on your job title/rank/etc.
* Verification is never suitable for an extended period of time, it is checked every single time & runs continuously as you are using the network
27
New cards
SASE - SSE | Three pillars of verification
1. Identity
2. Context (privilege level)
3. Security (is your computer safe and have anti-virus/updated OS?)
28
New cards
SASE | Two components of SASE
WAN Service Edge & SSE
29
New cards
SASE - SSE - ZTNA | Trust Broker
in charge of verifying three pillars of ZTNA verification
\
(could be netwrok device or cloud provider)
\
(could be netwrok device or cloud provider)
30
New cards
SSE | SASE = SD-WAN + SSE | Can SSE stand alone?
Yes, SSE covers needs without a wide area network (networking in this case has been completely removed)
\
(connection straight to the cloud/internet of things)
\
(connection straight to the cloud/internet of things)
31
New cards
SASE & SSE | Why choose SSE over SASE?
Whether or not you have on-premise connectivity requirements
\
If you have them = SASE
If you don’t have them = SSE
\
If you have them = SASE
If you don’t have them = SSE
32
New cards
SSE Difference/Uniqueness
Instead of the user connecting to the network and then the internet or application/software, once they verify the user, they bring the application/software to them (replaces VPN or Firewall)
33
New cards
SSE | Security Services Edge Provided Services
Sensitive Data Awareness & Context
* Secure Web Gateway
* CASB (Cloud Acess Security Broker)
* ZTNA/VPN
* Remote Browser Application
* FWaaS
* Encryption/Decryption
and more…
* Secure Web Gateway
* CASB (Cloud Acess Security Broker)
* ZTNA/VPN
* Remote Browser Application
* FWaaS
* Encryption/Decryption
and more…
34
New cards
SASE | WAN Edge Services
Threat Awareness & User-Device Identity
* SD-WAN
* WAN Optimization
* Quality of Service
* Routing
* Saas Acceleration
* Content delivery/Caching
and more…
* SD-WAN
* WAN Optimization
* Quality of Service
* Routing
* Saas Acceleration
* Content delivery/Caching
and more…
35
New cards
“As we transition from a post-pandemic world, and a hybrid work environment has become the new normal, a new approach is needed for network edge security to protect critical SaaS applications.“
Phil Mottram, executive vice president and general manager, HPE Aruba Networking
36
New cards
### **What strategies do you use on a cold call to build rapport with the caller?**
I ask them a question about themselves
37
New cards
cyber security
the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access.
38
New cards
AAR (Annual Reoccurring Revenue)
* Used for more long term planning
* Valuations for SaaS Companies are usually based on year over year ARR
\
* Valuations for SaaS Companies are usually based on year over year ARR
\
39
New cards
Value Selling
* Leverage customer anticipation of enjoying the result the product will give them
* How their life will be improved by the products and not the actual features
* Like & Dislikes in the current situation
* How past solutions have helped or not helped them (How the competitor has not been able to solve their problem)
* What is their process for looking for new solutions
* USP (Unique Selling proposition)
* How their life will be improved by the products and not the actual features
* Like & Dislikes in the current situation
* How past solutions have helped or not helped them (How the competitor has not been able to solve their problem)
* What is their process for looking for new solutions
* USP (Unique Selling proposition)
40
New cards
MEDDIC | Metrics
* Show, don’t tell
proof of economic benefit of investing in your solution
proof of economic benefit of investing in your solution
41
New cards
MEDDIC | Economic Buyer
* Talk to the decision makers first
who makes the decisions (who will actually sign off on buying)
\
who makes the decisions (who will actually sign off on buying)
\
42
New cards
MEDDIC | Decision Criteria
* factors your prospect uses to make their decisions
Questions:
* Pricing
* Features
* Level of Service Provided
* Onboarding Assistance
* Product Integration
* Ease of Use
* Brand recognition
* Industry Reputation
Questions:
* Pricing
* Features
* Level of Service Provided
* Onboarding Assistance
* Product Integration
* Ease of Use
* Brand recognition
* Industry Reputation
43
New cards
MEDDIC | Decision Process
Questions:
* How does your organization make buying decisions?
* Is anyone else involved in the buying process?
* What’s your role in the decision making process?
* How does your organization make buying decisions?
* Is anyone else involved in the buying process?
* What’s your role in the decision making process?
44
New cards
MEDDIC | Identify Pain
identify your prospects pain points your able to ease or solve
\
Pain Points:
* Wasting time
* Wasting Money
* Too Complicated
* Tedious
\
Pain Points:
* Wasting time
* Wasting Money
* Too Complicated
* Tedious
45
New cards
MEDDIC | Champion
determine if there is someone associated with prospect that can advocate on your behalf
(choice & agility)
(choice & agility)
46
New cards
We now live in a direct to the internet so Axis is…
bringing security to the cloud
47
New cards
Why did HPE Aruba acquire access
they used to partner with SSE companies, but the customers wanted one vendor to call and rely on for all their networking - so they acquired Axis
\
Aruba had SD-WAN but not SSE. Now that they do they have a full SASE portfolio
\
Aruba had SD-WAN but not SSE. Now that they do they have a full SASE portfolio
48
New cards
Axis wanted ______ & ________ when creating their product
elegance & simplicity
49
New cards
Axis | You can ______ & ________ rules as well as customize them
add and delete
50
New cards
Axis for admins can show:
* where the user went
* what they tried to download
* how much time they spent wherever
* and more
* what they tried to download
* how much time they spent wherever
* and more
51
New cards
DPP
Device Provisioning Protocol (DPP is a provisioning protocol certified by the Wi-Fi Alliance that allows onboarding IoT devices easily, securely, and on a large scale.) is a Wi-Fi.
52
New cards
UXI
User Experience Insight
53
New cards
Aruba Agile NaaS Key Dimensions
1. Capex or Opex?
2. Self or Third Party Managed?
3. Incremental or Full Refresh?
4. On Prem or Public Cloud?
5. Consistent Needs or Peaks and Valleys?
6. Cost Focused or Performance Based?
54
New cards
WAN
they allow localized networks to communicate with one another across great distances