Intro to Comp Networks Final Exam
0.0(0)
0.0(0)
Card Sorting
1/116
Earn XP
Study Analytics
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No study sessions yet.
117 Terms
1
New cards
1824
* Suppose that the RTT delay between the client and server is 30 msecs; the time a server needs to transmit an object into its outgoing link is 1 msecs; and any other HTTP message not containing an object has a negligible (zero) transmission time. Suppose the client again makes 60 requests, one after the other, waiting for a reply to a request before sending the next request.
* Assume the client is using HTTP 1.1 and the IF-MODIFIED-SINCE header line. Assume 60% of the objects requested have NOT changed since the client downloaded them (before these 60 downloads are performed)
How much time elapses (in milliseconds) between the client transmitting the first request, and the completion of the last request?
* Assume the client is using HTTP 1.1 and the IF-MODIFIED-SINCE header line. Assume 60% of the objects requested have NOT changed since the client downloaded them (before these 60 downloads are performed)
How much time elapses (in milliseconds) between the client transmitting the first request, and the completion of the last request?
2
New cards
false
(T/F) A user requests a Web page that consists of some text and three images. For this page, the client will send one request message and receive four response messaes.
3
New cards
false
(T/F) With nonpersistent connections between browser and origin server, it is possible for a single TCP segment to carry two distinct HTTP request messages.
4
New cards
a) The cookie value itself doesn’t mean anything. It is just a value that was returned by a web server to this client during an earlier interaction.
What is the purpose of a cookie value in the HTTP GET request?
* a) The cookie value itself doesn’t mean anything. It is just a value that was returned by a web server to this client during an earlier interaction.
* b) The cookie value indicates whether the user wants to use HTTP/1, HTTP/1.1, or HTTP/2 for this GET request
* c) none of the others
* d) The cookie value encodes the format of the reply preferred by the client in the response to this GET request
* e) The cookie value in encoding of a user email address associated with the GET request
* a) The cookie value itself doesn’t mean anything. It is just a value that was returned by a web server to this client during an earlier interaction.
* b) The cookie value indicates whether the user wants to use HTTP/1, HTTP/1.1, or HTTP/2 for this GET request
* c) none of the others
* d) The cookie value encodes the format of the reply preferred by the client in the response to this GET request
* e) The cookie value in encoding of a user email address associated with the GET request
5
New cards
a) all of the others
When a TCP segment arrives to a host, the socket to which the segment is directed depends on
* a) all of the others
* b) the source IP address of the datagram that encapsulated the segment
* c) the destination port number
* d) the source port number
* a) all of the others
* b) the source IP address of the datagram that encapsulated the segment
* c) the destination port number
* d) the source port number
6
New cards
d) none of the others
UDP has which of the following characteristics:
* a) connection state at the server
* b) three-way handshake for the connection establishment
* c) regulated send rate
* d) none of the others
* a) connection state at the server
* b) three-way handshake for the connection establishment
* c) regulated send rate
* d) none of the others
7
New cards
d) host A will retransmit neither segments
Over a TCP connection, suppose host A sends two segments to host B, host B sends an acknowledgement for each segment, the first acknowledgement is lost, but the second acknowledgement arrives before the timer for the first segment expires.
* a) host A will retransmit both segments
* b) host A will retransmit the second segment
* c) host A will retransmit the first segment
* d) host A will retransmit neither segments
* a) host A will retransmit both segments
* b) host A will retransmit the second segment
* c) host A will retransmit the first segment
* d) host A will retransmit neither segments
8
New cards
d) all of the others
Pipelining requires which of the following
* a) transmitting many packets before receiving acknowledgements
* b) sender-side buffering of unacknowledged packets
* c) unique sequence numbers for each in-transit packet
* d) all of the others
* a) transmitting many packets before receiving acknowledgements
* b) sender-side buffering of unacknowledged packets
* c) unique sequence numbers for each in-transit packet
* d) all of the others
9
New cards
true
(T/F) In the End-End congestion control approach, congestion is inferred from observed loss or delay.T
10
New cards
false
(T/F) The size of the TCP RcvWindow never changes throughout the duration of the connection.
11
New cards
false
(T/F) Host A is sending a large file to host B over a TCP connection. If the sequence number for a segment of this connection is m, then the sequence number for the subsequent segment will necessarily be m+1.
12
New cards
b) increases utilization
TCP uses pipelining to:
* a) none of the others
* b) increases utilization
* c) establish connections
* d) control congestion
* a) none of the others
* b) increases utilization
* c) establish connections
* d) control congestion
13
New cards
segments
On the sending side, the transport layer converts the application-layer messages it receives from a sending application process into transport-layer packets, known as transport-layer ______________________.
14
New cards
001001010000011
What is the sum of these two 16 bit numbers?
* 10001011 01001110
* 10011001 10110111
* 10001011 01001110
* 10011001 10110111
15
New cards
110110101111100
What is the checksum of these two 16 bit numbers?
* 10001011 01001110
* 10011001 10110111
* 10001011 01001110
* 10011001 10110111
16
New cards
183,1118,2053,2988; 1118,2053,2988,x
Consider the figure below in which a TCP sender and receiver communicate over a connection in which the sender->receiver segments may be lost. The TCP sender sends an initial window of 4 segments. Suppose the initial value of the sender->receiver sequence number is 183 and the first 4 segments *each* contain 935 bytes. The delay between the sender and receiver is 7 time units, and so the first segment arrives at the receiver at t=8. As shown in the figure below, 1 of the 4 segment(s) are lost between the segment and receiver.
* What is the sequence numbers associated with each of the 4 segments sent by the sender. Format your answers as: a,b,c,… (no spaces)
* Give the ACK numbers the receiver sends in response to each of the segments. If a segment never arrives use ‘x’ to denote it, and format your answer as: a,b,c,…
* What is the sequence numbers associated with each of the 4 segments sent by the sender. Format your answers as: a,b,c,… (no spaces)
* Give the ACK numbers the receiver sends in response to each of the segments. If a segment never arrives use ‘x’ to denote it, and format your answer as: a,b,c,…
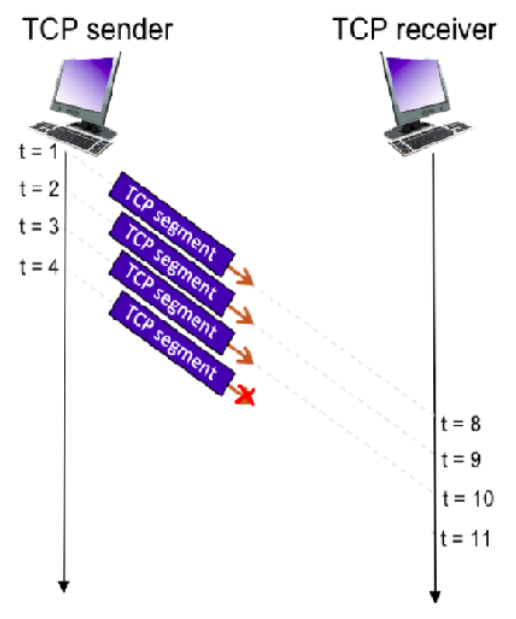
17
New cards
d) there is no queueing delay in the router
Suppose a router has n input ports each with identical line speeds, n output ports each with identical line speeds, and the line speed of an output port is at least n times as that of an input port. Further suppose that the switching fabric speed is at least n times as fast as an input line speed. Then
* a) queueing can occur in an output port
* b) queueing can occur in an input port
* c) queueing can occur in the switching fabric
* d) there is no queueing delay in the router
* a) queueing can occur in an output port
* b) queueing can occur in an input port
* c) queueing can occur in the switching fabric
* d) there is no queueing delay in the router
18
New cards
b) in the input ports and in the output ports
In a router, queueing can occur
* a) only in the output ports
* b) in the input ports and in the output ports
* c) none of the others
* d) only in the input ports
* a) only in the output ports
* b) in the input ports and in the output ports
* c) none of the others
* d) only in the input ports
19
New cards
d) the sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4 datagram
Suppose one IPv6 router wants to send a datagram to another IPv6 router, but are connected together by intervening IPv4 routers. If the two routers use tunneling, then
* a) none of the others
* b) the sending IPv6 router creates one or more IPv6 fragments, none of which is larger than the maximum size of an IPv4 datagram
* c) the sending IPv6 router creates an IPv4 datagram and puts it in the data field of an IPv6 datagram
* d) the sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4 datagram
* a) none of the others
* b) the sending IPv6 router creates one or more IPv6 fragments, none of which is larger than the maximum size of an IPv4 datagram
* c) the sending IPv6 router creates an IPv4 datagram and puts it in the data field of an IPv6 datagram
* d) the sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4 datagram
20
New cards
true
(T/F) With a datagram network layer, each packet carries the address of the destination host
21
New cards
true
(T/F) The network portion of an IP address is the same for all the hosts on the same IP network
22
New cards
b) could increase the end-end delay
Increasing the amount of per-hop buffer
* a) could decrease the end-end delay
* b) could increase the end-end delay
* c) will not decrease packet loss
* d) none of the others
* a) could decrease the end-end delay
* b) could increase the end-end delay
* c) will not decrease packet loss
* d) none of the others
23
New cards
true
(T/F) Multiple packets can be transferred by the switch fabric in parallel, as long as their output ports are different
24
New cards
b) the transmission of packet A will not be interrupted. so, packet B has to wait after fully transmitting packet A
Assume packet A has begun transmission. If packet B (a high-priority packet) arrives during the transmission of packet A (a low-priority packet), then
* a) packet B will be transmitted immediately while packet A is still being transmitted
* b) the transmission of packet A will not be interrupted. so, packet B has to wait after fully transmitting packet A
* c) the transmission of packet A will be interrupted to allow the transmission of packet B
* d) transmission cannot be based on priorities
* a) packet B will be transmitted immediately while packet A is still being transmitted
* b) the transmission of packet A will not be interrupted. so, packet B has to wait after fully transmitting packet A
* c) the transmission of packet A will be interrupted to allow the transmission of packet B
* d) transmission cannot be based on priorities
25
New cards
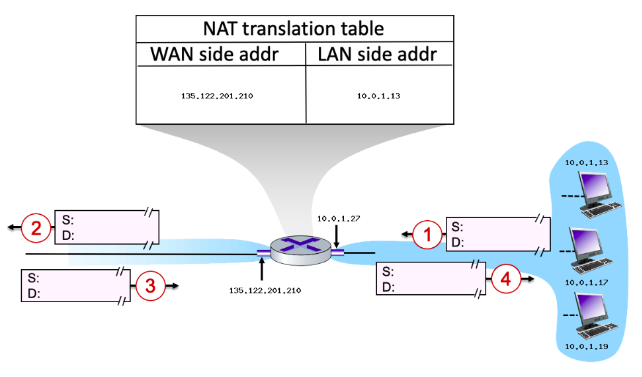
10\.0.1.13
Suppose that the host with IP address 10.0.1.13 sends an IP datagram destined to host 128.119.173.181. The source port is 3461, and the destination port is 80.
* Consider the datagram at step 1, after it has been sent by the host but before it has reached the router. What is the source IP address for this datagram?
* Consider the datagram at step 1, after it has been sent by the host but before it has reached the router. What is the source IP address for this datagram?
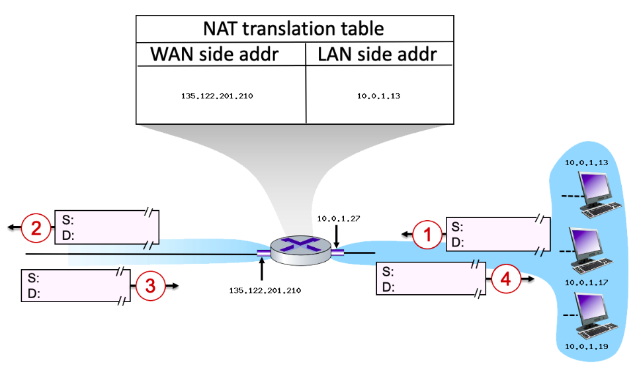
26
New cards
135\.122.201.210
Suppose that the host with IP address 10.0.1.13 sends an IP datagram destined to host 128.119.173.181. The source port is 3461, and the destination port is 80.
* Now consider the datagram at step 2, after it has been transmitted by the router. What is the source IP address for this datagram?
* Now consider the datagram at step 2, after it has been transmitted by the router. What is the source IP address for this datagram?
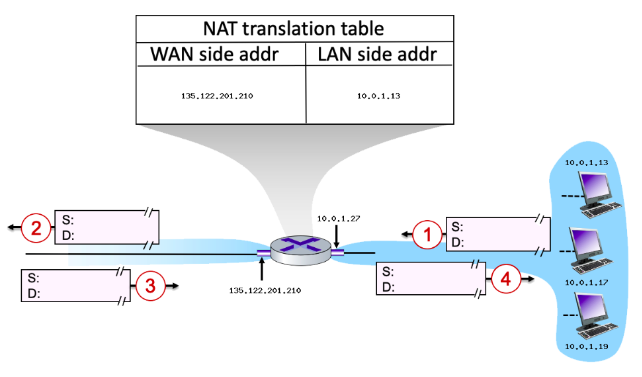
27
New cards
yes
Suppose that the host with IP address 10.0.1.13 sends an IP datagram destined to host 128.119.173.181. The source port is 3461, and the destination port is 80.
* Will the source port (at step 2) have changed (from step 1)? y/n
* Will the source port (at step 2) have changed (from step 1)? y/n
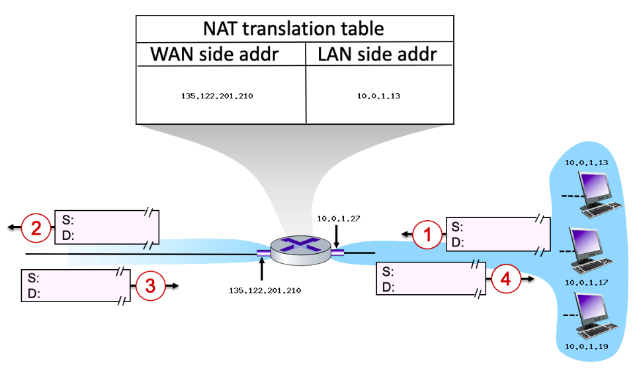
28
New cards
no
Suppose that the host with IP address 10.0.1.13 sends an IP datagram destined to host 128.119.173.181. The source port is 3461, and the destination port is 80.
* Has a new entry been made in the router’s NAT table (between step 3 and step 4)? y/n
* Has a new entry been made in the router’s NAT table (between step 3 and step 4)? y/n
29
New cards
c) all of the others
The link-state algorithm (covered in class) has the following properties:
* a) it determines the shortest path from the source node to all other nodes
* b) after the kth iteration, the least-cost paths are known to k nodes
* c) all of the others
* d) it requires the source node to know the costs between every pair of adjacent nodes in the graph
* a) it determines the shortest path from the source node to all other nodes
* b) after the kth iteration, the least-cost paths are known to k nodes
* c) all of the others
* d) it requires the source node to know the costs between every pair of adjacent nodes in the graph
30
New cards
c) policy
In routing among ASs, which of the following issues dominants:
* a) number of ASs traversed
* b) current congestion levels in the ASs
* c) policy
* d) geographical distance between ASs
* a) number of ASs traversed
* b) current congestion levels in the ASs
* c) policy
* d) geographical distance between ASs
31
New cards
c) runs directly on top of IP
The ICMP protocol
* a) none of the others
* b) runs on top TCP
* c) runs directly on top of IP
* d) runs on top UDP
* a) none of the others
* b) runs on top TCP
* c) runs directly on top of IP
* d) runs on top UDP
32
New cards
c) chooses the gateway that has the smallest cost
As part of hierarchical routing, hot-potato routing does the following:
* a) determines the number of ASes in the shortest As path from router to destination
* b) provides information to a router about the existence of external networks
* c) chooses the gateway that has the smallest cost
* d) labels suspicious packets as “hot”
* a) determines the number of ASes in the shortest As path from router to destination
* b) provides information to a router about the existence of external networks
* c) chooses the gateway that has the smallest cost
* d) labels suspicious packets as “hot”
33
New cards
false
(T/F) In a distance-vector routing algorithm, each node has a map of the entire network and determines the shortest path from itself to all other nodes in the network.
34
New cards
false
(T/F) In the BGP routing algorithm, each AS advertises to its neighbors its estimates of the shortest distances from the AS to all possible destination ASs.
35
New cards
false
(T/F) Every autonomous system must use the same intra-autonomous system routing algorithm.
36
New cards
false
(T/F) OSPF uses BGP for routing among areas.
37
New cards
4,u
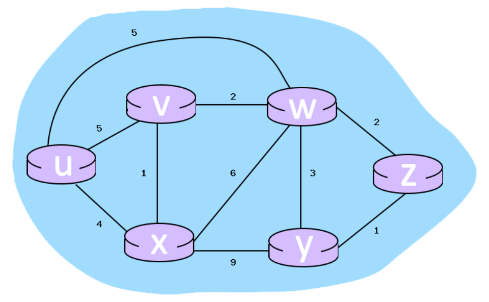
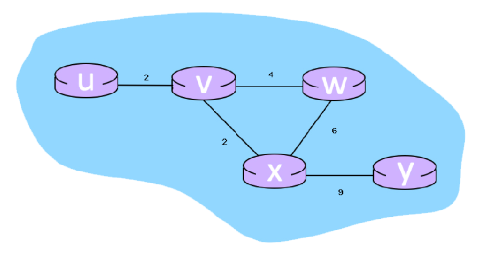
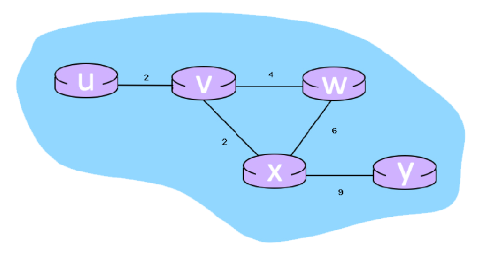
* Consider the 6-node network shown below, with the given link costs.
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node x and what node is its predecessor? Write your answer as n,p
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node x and what node is its predecessor? Write your answer as n,p
38
New cards
7,w
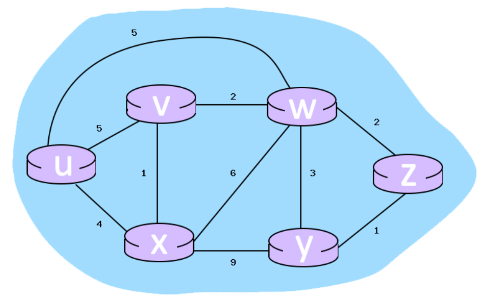
* Consider the 6-node network shown below, with the given link costs.
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node z and what node is its predecessor? Write your answer as n,p
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node z and what node is its predecessor? Write your answer as n,p
39
New cards
8,w
* Consider the 6-node network shown below, with the given link costs.
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node y and what node is its predecessor? Write your answer as n,p
* Using Dijkstra's algorithm, find the least cost path from source node U to all other destinations and answer the following questions:
What is the shortest distance to node y and what node is its predecessor? Write your answer as n,p
40
New cards
x,x,x,9,0
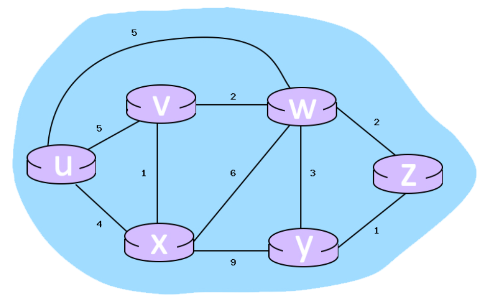
* Consider the 6-node network shown below, with the given link costs:
* What are the initial distance vectors for router 'Y'? Write your answer as u,v,w,x,y and if a distance is ∞, write 'x'
* What are the initial distance vectors for router 'Y'? Write your answer as u,v,w,x,y and if a distance is ∞, write 'x'
41
New cards
0,2,6,4,13
* Consider the 6-node network shown below, with the given link costs:
* When the algorithm converges, what are the distance vectors from router 'U' to all routers? Write your answer as u,v,w,x,y
* When the algorithm converges, what are the distance vectors from router 'U' to all routers? Write your answer as u,v,w,x,y
42
New cards
false
(T/F) In a Client-SErver paradigm, clients can communicate directly with each other.
43
New cards
true
(T/F) In order for 2 processes running on different hosts to exchange messages, two sockets must be involved: one on each side.
44
New cards
80
The default port for processes running on an HTTP server is ____________.
45
New cards
false
(T/F) Generally, a file transfer application can tolerate some loss of data
46
New cards
c) at most one object is sent
In a non-persistent HTTP connection:
* a) the connection will remain open until all objects are sent
* b) multiple objects can be sent
* c) at most one object is sent
* d) the objects that are sent will not be persisted
* a) the connection will remain open until all objects are sent
* b) multiple objects can be sent
* c) at most one object is sent
* d) the objects that are sent will not be persisted
47
New cards
* d) cookies
In order for web sites and client browsers to maintain some state between transactions, they use:
* a) persistent TCP
* b) none of the others
* c) persistent HTTP connections
* d) cookies
* a) persistent TCP
* b) none of the others
* c) persistent HTTP connections
* d) cookies
48
New cards
true
(T/F) HTTP/2 increased flexibility at server in sending objects to client
49
New cards
false
(T/F) One similarity between HTTP and SMTP is that both are pull protocols.
50
New cards
a) IMAP
When a user agent retrieves an e-mail message from its e-mail server, it uses this protocol:
* a) IMAP
* b) UDP
* c) none of the others
* d) SMTP
* a) IMAP
* b) UDP
* c) none of the others
* d) SMTP
51
New cards
a) The HTTP GET request message is used by a web client to request a web server to send the requested object from the server to the client
What is the purpose of the HTTP GET?
* a) The HTTP GET request message is used by a web client to request a web server to send the requested object from the server to the client
* b) The HTTP GET request message is sent by a web server to a web client to get the next request from the web client
* c) The HTTP GET request message is used by a web client to post an object on a web server
* d) The HTTP GET request message is sent by a web server to a web client to get the identity of the web client
* a) The HTTP GET request message is used by a web client to request a web server to send the requested object from the server to the client
* b) The HTTP GET request message is sent by a web server to a web client to get the next request from the web client
* c) The HTTP GET request message is used by a web client to post an object on a web server
* d) The HTTP GET request message is sent by a web server to a web client to get the identity of the web client
52
New cards
a) yes, because this is a conditional GET, as evidenced by the If-Modified-Since field
* Suppose the client-to-server HTTP GET message is the following:
GET /kurose_ross_sandbox/interactive/quotation1.htm HTTP/1.1 \\n Host: gaia.cs.umass.edu \\n Accept: text/plain, text/html, image/png, image/gif, audio/mp4, audio/basic, video/mp4, video/wmv, \\n Accept-Language: en-us, en-gb;q=0.3, en;q=0.7, fr, fr-ch, zh, de, fi, ar, cs \\n If-Modified-Since: Mon, 12 Dec 2022 17:09:47 -0800 \\n User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3) AppleWebKit/534.53.11 (KHTML, like Gecko) Version/5.1.3 Safari/534.53.10
* Does the client have a cached copy of the object being requested?
* a) yes, because this is a conditional GET, as evidenced by the If-Modified-Since field
* b) There’s not enough information in the header to answer this question
* c) no, because a client would not request an object if it had that object in its cache
* d) yes, because HTTP 1.1 is being used
GET /kurose_ross_sandbox/interactive/quotation1.htm HTTP/1.1 \\n Host: gaia.cs.umass.edu \\n Accept: text/plain, text/html, image/png, image/gif, audio/mp4, audio/basic, video/mp4, video/wmv, \\n Accept-Language: en-us, en-gb;q=0.3, en;q=0.7, fr, fr-ch, zh, de, fi, ar, cs \\n If-Modified-Since: Mon, 12 Dec 2022 17:09:47 -0800 \\n User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3) AppleWebKit/534.53.11 (KHTML, like Gecko) Version/5.1.3 Safari/534.53.10
* Does the client have a cached copy of the object being requested?
* a) yes, because this is a conditional GET, as evidenced by the If-Modified-Since field
* b) There’s not enough information in the header to answer this question
* c) no, because a client would not request an object if it had that object in its cache
* d) yes, because HTTP 1.1 is being used
53
New cards
1512\.5
Assume that the RTT delay between the client and server is 30 msecs and the TCP connection is already established
* the time a server needs to transmit an object into its outgoing link is 0.5 msecs
* any other HTTP message not containing an object has a negligible (zero) transmission time.
Suppose the client again makes 50 requests, one after the other, waiting for a reply to a request before sending the next request.
* Assume the client is using HTTP 1.1 and the IF-MODIFIED-SINCE header line.
* Assume 50% of the objects requested have NOT changed since the client downloaded them (before these 50 downloads are performed)
How much time elapses (in milliseconds) between the client transmitting the first request, and the completion of the last request?
* the time a server needs to transmit an object into its outgoing link is 0.5 msecs
* any other HTTP message not containing an object has a negligible (zero) transmission time.
Suppose the client again makes 50 requests, one after the other, waiting for a reply to a request before sending the next request.
* Assume the client is using HTTP 1.1 and the IF-MODIFIED-SINCE header line.
* Assume 50% of the objects requested have NOT changed since the client downloaded them (before these 50 downloads are performed)
How much time elapses (in milliseconds) between the client transmitting the first request, and the completion of the last request?
54
New cards
40
* Assume an RTT of 10 msec is needed for each:
* to initiate and establish a TCP connection
* for HTTP request and first few bytes of HTTP response to return
* Assume an object transmission time is 0.5 msec
* Assume the HTML page being requested references % objects in addition to the base HTML file and that HTTP/1.0 is being used.
What is the total response time for the entire page to be delivered to the browser?
* to initiate and establish a TCP connection
* for HTTP request and first few bytes of HTTP response to return
* Assume an object transmission time is 0.5 msec
* Assume the HTML page being requested references % objects in addition to the base HTML file and that HTTP/1.0 is being used.
What is the total response time for the entire page to be delivered to the browser?
55
New cards
a) none of the others
Which of the following is not true about UDP?
* a) none of the others
* b) connection setup is not needed
* c) segments may be delivered out of order
* d) segments may be lost
* a) none of the others
* b) connection setup is not needed
* c) segments may be delivered out of order
* d) segments may be lost
56
New cards
e) data (payload)
Which of the fields below are not in a UDP segment header?
* a) checksum
* b) none of the other
* c) source port number
* d) length
* e) data (payload)
* a) checksum
* b) none of the other
* c) source port number
* d) length
* e) data (payload)
57
New cards
false
(T/F) When computing the Internet checksum for two numbers, a single flipped bit in each of the two numbers will always result in a changed checksum
58
New cards
true
(T/F) It is possibly for two UDP segments to be sent from the same socket with source port 5723 at a server to two different clients
59
New cards
segments, network
The transport protocol in the sender host breaks application messages into __________, and passes to _________ layer
60
New cards
111010110000001
What is the sum of these two 16 bit numbers?
* 00010100 01110001
* 11010110 10010010
* 00010100 01110001
* 11010110 10010010
61
New cards
000101001111110
What is the checksum of these two 16 bit numbers?
* 00010100 01110001
* 11010110 10010010
* 00010100 01110001
* 11010110 10010010
62
New cards
forwarding
Moving packets from a router’s input link to appropriate router output link is called _____________.
63
New cards
32
In Internet protocol version 4, the IP address consists of ______________ bits.
64
New cards
128
In Internet protocol version 6, the IP address consists of ______________ bits.
65
New cards
b) none of the others
Network-layer service model guarantee(s) on:
* a) bandwidth available to end-end flow
* b) none of the others
* c) delivery to destination
* d) timing or order of delivery
* a) bandwidth available to end-end flow
* b) none of the others
* c) delivery to destination
* d) timing or order of delivery
66
New cards
buffering
Because datagrams might arrive from switch fabric faster than link transmission rate, ___________ is required at the output port.
67
New cards
subnet
We refer to device interfaces that can physically reach each other without passing through an intervening router as a _______________.
68
New cards
false
(T/F) Before sending a packet into a datagram network, the source must determine all of the links that packet will traverse between source and destination
69
New cards
false
(T/F) The HTTP protocol was invented at Netscape in the early 1990s.
70
New cards
10
Suppose there are two links between a source and a destination. The first link has transmission rate 100 Mbps and the second link has transmission rate 10 Mbps. Assuming that the only traffic in the network comes from the source, what is the throughput for a file transfer?
71
New cards
a) loss-intolerant and time insensitive
The transfer of an html file from one host to another is:
* a) loss-intolerant and time insensitive
* b) loss-intolerant and time sensitive
* c) loss-tolerant and time insensitive
* d) loss-tolerant and time sensitive
* a) loss-intolerant and time insensitive
* b) loss-intolerant and time sensitive
* c) loss-tolerant and time insensitive
* d) loss-tolerant and time sensitive
72
New cards
d) 304 Not Modified
Suppose a client sends an HTTP request message with the If-modified-since header. Suppose the object in a server has not changed since the last time a client retrieved the object. Then the server will send a response message with the status code:
* a) 404 Not Found
* b) none of the others
* c) 200 OK
* d) 304 Not Modified
* a) 404 Not Found
* b) none of the others
* c) 200 OK
* d) 304 Not Modified
73
New cards
c) cache resource records, but discard them after a period of time that is on the order of a few days
Local DNS name servers:
* a) never cache resource records
* b) obtain resource records from Web caches
* c) cache resource records, but discard them after a period of time that is on the order of a few days
* d) cache resource records and never discard them
* a) never cache resource records
* b) obtain resource records from Web caches
* c) cache resource records, but discard them after a period of time that is on the order of a few days
* d) cache resource records and never discard them
74
New cards
b) all of the others
For BitTorrent, which of the following is true?
* a) at a given instant of time, a peer A may upload to a peer B, even is peer B is not sending anything to A
* b) all of the others
* c) Among the chunks that a peer does not have, the peer will request chunks that appear to be relatively rare in the torrent
* d) Although a peer may have 50 concurrent TCP connections with other peers, at any given instant of time it sends data to less than 10 other peers
* a) at a given instant of time, a peer A may upload to a peer B, even is peer B is not sending anything to A
* b) all of the others
* c) Among the chunks that a peer does not have, the peer will request chunks that appear to be relatively rare in the torrent
* d) Although a peer may have 50 concurrent TCP connections with other peers, at any given instant of time it sends data to less than 10 other peers
75
New cards
true
(T/F) With SMTP, it is possible to send multiple mail messages over the same TCP connection.
76
New cards
false
(T/F) In a Client-server paradigm, the clients can either communicate with the server or communicate directly with each other.
77
New cards
b) real-time audio
Which of the following applications can tolerate some data transfer loss?
* a) file transfer
* b) real-time audio
* c) none of the others
* d) all of the others
* e) web transactions
* a) file transfer
* b) real-time audio
* c) none of the others
* d) all of the others
* e) web transactions
78
New cards
port
To receive messages, processes must have identifier which includes both IP address and _________ number associated with process on host.
79
New cards
true
(T/F) File transfer applications are elastic applications and can make use of whatever throughput they get.
80
New cards
true
(T/F) Interactive game applications can use TCP or UDP.
81
New cards
false
(T/F) In HTTP/1.1, objects are divided into frames which are scheduled to mitigate HOL blocking.
82
New cards
c) Application-layer protocol
The Domain Name System is implemented as:
* a) Transport-layer protocol
* b) Network-layer protocol
* c) Application-layer protocol
* d) none of the others
* a) Transport-layer protocol
* b) Network-layer protocol
* c) Application-layer protocol
* d) none of the others
83
New cards
b) none of the others
When a host makes DNS query, the query is normally sent to:
* a) Top-Level Domain DNS server
* b) none of the others
* c) Authoritative DNS server
* d) Root DNS server
* a) Top-Level Domain DNS server
* b) none of the others
* c) Authoritative DNS server
* d) Root DNS server
84
New cards
b) the client determines what encoding rate to request
In a streaming stored videos application that uses DASH
* a) none of the others
* b) the client determines what encoding rate to request
* c) the CDN closest to the client determines which encoding rate to provide
* d) the server determines what encoding rate to provide
* a) none of the others
* b) the client determines what encoding rate to request
* c) the CDN closest to the client determines which encoding rate to provide
* d) the server determines what encoding rate to provide
85
New cards
0\.00012
* Assume a single router is transmitting packets, each of length L bits, over a single link with transmission rate R Mbps to another router at the other end of the link.
* Suppose that the packet length is L = 12000 bits, and that the link transmission rate along the link to router on the right is R = 100 Mbps.
What is the transmission delay?
* Suppose that the packet length is L = 12000 bits, and that the link transmission rate along the link to router on the right is R = 100 Mbps.
What is the transmission delay?
86
New cards
8333
* Assume a single router is transmitting packets, each of length L bits, over a single link with transmission rate R Mbps to another router at the other end of the link.
* Suppose that the packet length is L = 12000 bits, and that the link transmission rate along the link to router on the right is R = 100 Mbps.
What is the maximum number of packets per second that can be transmitted by this link?
* Suppose that the packet length is L = 12000 bits, and that the link transmission rate along the link to router on the right is R = 100 Mbps.
What is the maximum number of packets per second that can be transmitted by this link?
87
New cards
583\.33
We need to distribute a file that is initially located at a server to clients via either client-server download or peer-to-peer download.
* The problem is to distribute a file of size F = & Gbits to each of these 7 peers. Suppose the server has an upload rate of u = 84 Mbps.
* The 7 peers have upload rates of: u1 = 24 Mbps, u2 = 23 Mbps, u3 = 27 Mbps, u4 = 25 Mbps, u5 = 18 Mbps, u6 = 29 Mbps, and u7 = 27 Mbps
* The 7 peers have download rates of: d1 = 27 Mbps, d2 = 20 Mbps, d3 = 22 Mbps, d4 = 39 Mbps, d5 = 32 Mbps, d6 = 33 Mbps, and d7 = 17 Mbps
What is the minimum time needed to distribute this file from the central server to the 7 peers?
Formula: Dc-s = max{NF/us, F/dmin}
* The problem is to distribute a file of size F = & Gbits to each of these 7 peers. Suppose the server has an upload rate of u = 84 Mbps.
* The 7 peers have upload rates of: u1 = 24 Mbps, u2 = 23 Mbps, u3 = 27 Mbps, u4 = 25 Mbps, u5 = 18 Mbps, u6 = 29 Mbps, and u7 = 27 Mbps
* The 7 peers have download rates of: d1 = 27 Mbps, d2 = 20 Mbps, d3 = 22 Mbps, d4 = 39 Mbps, d5 = 32 Mbps, d6 = 33 Mbps, and d7 = 17 Mbps
What is the minimum time needed to distribute this file from the central server to the 7 peers?
Formula: Dc-s = max{NF/us, F/dmin}
88
New cards
411\.76
We need to distribute a file that is initially located at a server to clients via either client-server download or peer-to-peer download.
* The problem is to distribute a file of size F = & Gbits to each of these 7 peers. Suppose the server has an upload rate of u = 84 Mbps.
* The 7 peers have upload rates of: u1 = 24 Mbps, u2 = 23 Mbps, u3 = 27 Mbps, u4 = 25 Mbps, u5 = 18 Mbps, u6 = 29 Mbps, and u7 = 27 Mbps
* The 7 peers have download rates of: d1 = 27 Mbps, d2 = 20 Mbps, d3 = 22 Mbps, d4 = 39 Mbps, d5 = 32 Mbps, d6 = 33 Mbps, and d7 = 17 Mbps
What is the minimum time needed to distribute this file using peer-to-peer download?
Formula: DP2P = max{F/us, F/dmin, NF/(us + Sigma ui)}
* The problem is to distribute a file of size F = & Gbits to each of these 7 peers. Suppose the server has an upload rate of u = 84 Mbps.
* The 7 peers have upload rates of: u1 = 24 Mbps, u2 = 23 Mbps, u3 = 27 Mbps, u4 = 25 Mbps, u5 = 18 Mbps, u6 = 29 Mbps, and u7 = 27 Mbps
* The 7 peers have download rates of: d1 = 27 Mbps, d2 = 20 Mbps, d3 = 22 Mbps, d4 = 39 Mbps, d5 = 32 Mbps, d6 = 33 Mbps, and d7 = 17 Mbps
What is the minimum time needed to distribute this file using peer-to-peer download?
Formula: DP2P = max{F/us, F/dmin, NF/(us + Sigma ui)}
89
New cards
64
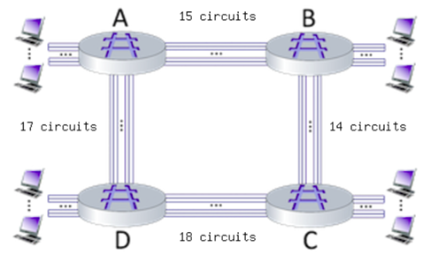
Consider the circuit-switched network shown in the figure below, with circuit switches A, B, C, and D. Suppose there are 15 circuits between A and B, 14 circuits between B and C, 18 circuits between C and D, and 17 circuits between D and A.
What is the maximum number of connections that can be ongoing in the network at any one time?
What is the maximum number of connections that can be ongoing in the network at any one time?
90
New cards
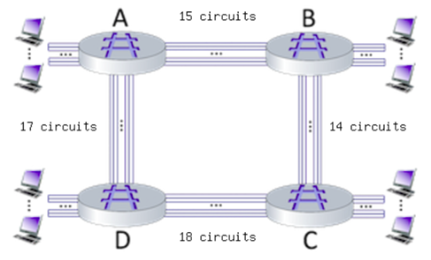
31
Suppose that every connection requires 2 consecutive hops, and calls are connected clockwise. For example, a connection can go from A to C, from B to D, from C to A, and from D to B.
With these constraints, what is the maximum number of connections that can be ongoing in the network at any one time?
With these constraints, what is the maximum number of connections that can be ongoing in the network at any one time?
91
New cards
c) all of the others
When a TCP segment arrives to a host, the socket to which the segment is directed depends on:
* a) the source port number
* b) the destination port number
* c) all of the others
* d) the source IP address of the datagram that encapsulated the segment
* a) the source port number
* b) the destination port number
* c) all of the others
* d) the source IP address of the datagram that encapsulated the segment
92
New cards
a) none of the others
UDP has which of the following characteristics?
* a) none of the others
* b) regulated send rate
* c) connection state at the server
* d) three-way handshake for connection establishment
* a) none of the others
* b) regulated send rate
* c) connection state at the server
* d) three-way handshake for connection establishment
93
New cards
b) host A will retransmit neither segments
Over a TCP connection, suppose host A sends two segments to host B, host B sends an acknowledgement for each segment, the first acknowledgement is lost, but the second acknowledgement arrives before the timer for the first segment expires.
* a) host A will retransmit both segments
* b) host A will retransmit neither segments
* c) host A will retransmit the first segment
* d) host A will retransmit the second segment
* a) host A will retransmit both segments
* b) host A will retransmit neither segments
* c) host A will retransmit the first segment
* d) host A will retransmit the second segment
94
New cards
d) breaking application messages into segments and passing them to network layer
The transport protocols actions in send end systems involves:
* a) breaking application messages into datagrams and passing them to network layer
* b) breaking application messages into frames and passing them to link layer
* c) none of the others
* d) breaking application messages into segments and passing them to network layer
* a) breaking application messages into datagrams and passing them to network layer
* b) breaking application messages into frames and passing them to link layer
* c) none of the others
* d) breaking application messages into segments and passing them to network layer
95
New cards
a) network layer represents a logical communication between hosts while transport layer represents a logical communication between processes
One important difference between the network and transport layer is:
* a) network layer represents a logical communication between hosts while transport layer represents a logical communication between processes
* b) network layer represents a logical communication between hosts while transport layer represents a logical communication between processes as well as between hosts
* c) none of the others
* d) network layer represents a logical communication between processes while transport layer represents a logical communication between hosts
* a) network layer represents a logical communication between hosts while transport layer represents a logical communication between processes
* b) network layer represents a logical communication between hosts while transport layer represents a logical communication between processes as well as between hosts
* c) none of the others
* d) network layer represents a logical communication between processes while transport layer represents a logical communication between hosts
96
New cards
a) no RTT required for connection establishment
Potential benefit(s) for using UDP over TCP:
* a) no RTT required for connection establishment
* b) reliable
* c) maintains connection state
* d) will decrease sending rate when congestion is detected to avoid packet loss
* a) no RTT required for connection establishment
* b) reliable
* c) maintains connection state
* d) will decrease sending rate when congestion is detected to avoid packet loss
97
New cards
d) sender allows multiple, “in-flight”, yet-to-be-acknowledged packets
In pipelining:
* a) sender allows single yet-to-be-acknowledged packets
* b) sender waits for acknowledgements before sending another packet
* c) none of the others
* d) sender allows multiple, “in-flight”, yet-to-be-acknowledged packets
* a) sender allows single yet-to-be-acknowledged packets
* b) sender waits for acknowledgements before sending another packet
* c) none of the others
* d) sender allows multiple, “in-flight”, yet-to-be-acknowledged packets
98
New cards
0001010100100000
What is the sum of these two 16 bit numbers? Do not put spaces.
* 11010000 10111011
* 01000100 01100100
* 11010000 10111011
* 01000100 01100100
99
New cards
1110101011011111
What is the checksum of these two 16 bit numbers? Do not put spaces.
* 11010000 10111011
* 01000100 01100100
* 11010000 10111011
* 01000100 01100100
100
New cards
true
(T/F) TCP can be described as a point-to-point protocol