2.4 Denial of Service
1/6
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
7 Terms
Denial-Of-Service (DoS):
Occurs when an attacker intentionally forces a service to fail, making it unavailable. Typically involves overwhelming the service with excessive requests or exploiting a known vulnerability or design flaw in the system.
Keep your systems patched
Organizations may create a denial of service against competitors as a form of competitive sabotage
Is used as a distraction, allowing attackers to exploit other vulnerabilities elsewhere in the organization while the focus is on mitigating the service disruption.
Doesn’t have to be complicated—simply turning off the power to a critical system can be enough to cause a significant disruption.
A “Friendly” DoS
Occurs when denial of service happens unintentionally, often due to a simple mistake or misconfiguration
If you connect two switches to each other and then connect them back to each other again, it can create a Layer 2 loop. Without Spanning Tree Protocol (STP) to prevent such loops, the network can become flooded with traffic, leading to a DoS situation
A Bandwidth DoS occurs when limited bandwidth is consumed by a single task.
For example, downloading a large file, like a Linux distribution, over a small DSL line could consume all available bandwidth, leaving none for other essential production applications, effectively causing a denial of service for those services.
Distributed Denial of Service (DDoS):
Involves launching a coordinated attack using an army of computers to overwhelm and bring down a target service.
Attackers typically control these computers through botnets—networks of infected devices that have been compromised with malware.
The attacker doesn't need to sit at each individual device. Instead, they command the botnet to launch an attack against a specific web server, all with a single command.
For example, the Zeus botnet had control over more than 3.6 million computers at its peak.
Considered an asymmetric threat, where the attacker, with relatively few resources, can easily disrupt organizations with far more systems and much greater bandwidth.
DDoS Reflection & Amplification
Attackers exploit internet services to create highly efficient attacks by sending small amounts of data that get amplified into much larger volumes, overwhelming the target system.
Takes advantage of protocols that require little or no authentication or checks, making them vulnerable to abuse.
When an attacker sends a small request to a server, they can receive back a much larger response than they originally requested. By using this amplification effect, the attacker can send small requests but cause significant traffic to be directed at the victim.
Common protocols used for reflection and amplification attacks include:
NTP
DNS
ICMP
Turning Up the Volume
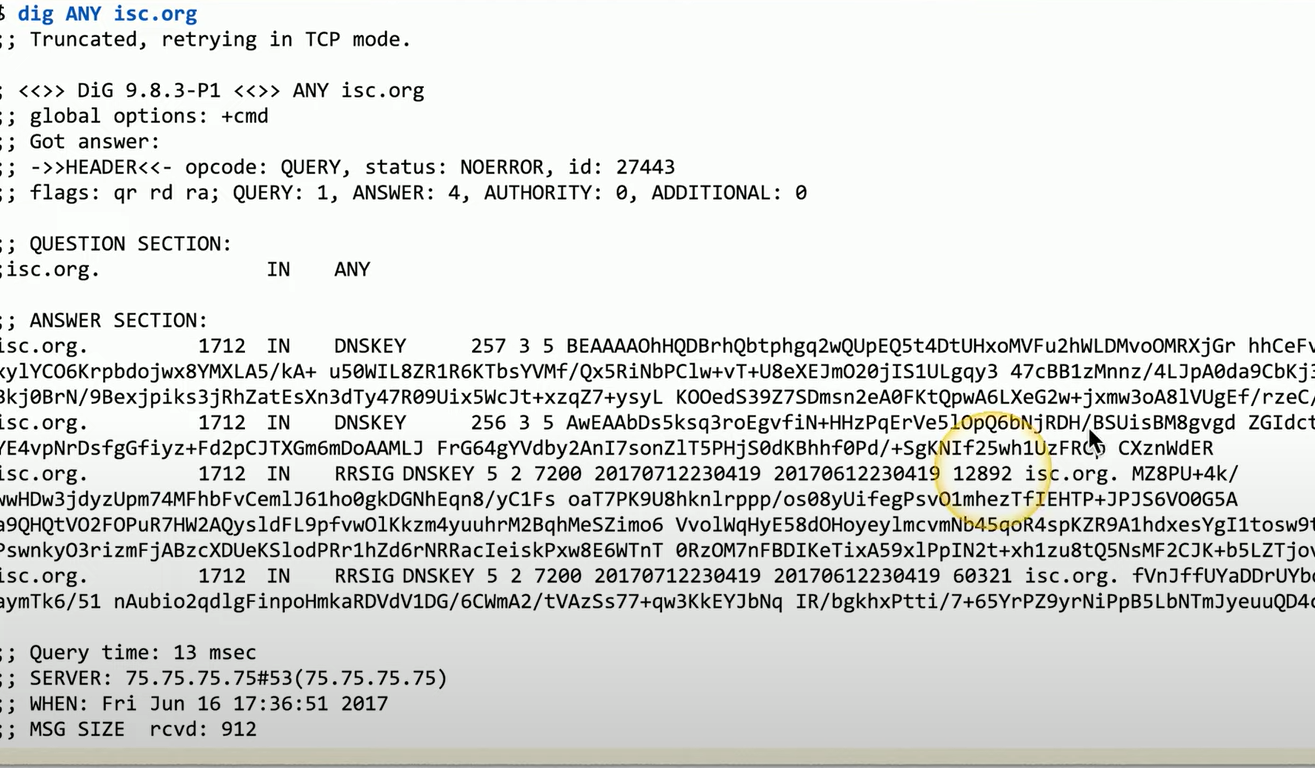
The attacker sends a small amount of data, like a DNS query, which might be only about 15 characters.
The response from the DNS server can be much larger—about 1,300 characters in this case; increases the data volume by roughly 86 times
Open DNS Resolvers
A DNS server that is configured to resolve recursive DNS lookups for anyone on the internet, regardless of the source of the request
The attacker spoofs their IP address to redirect the amplified traffic to the victim's system, rather than to the attacker’s own system.
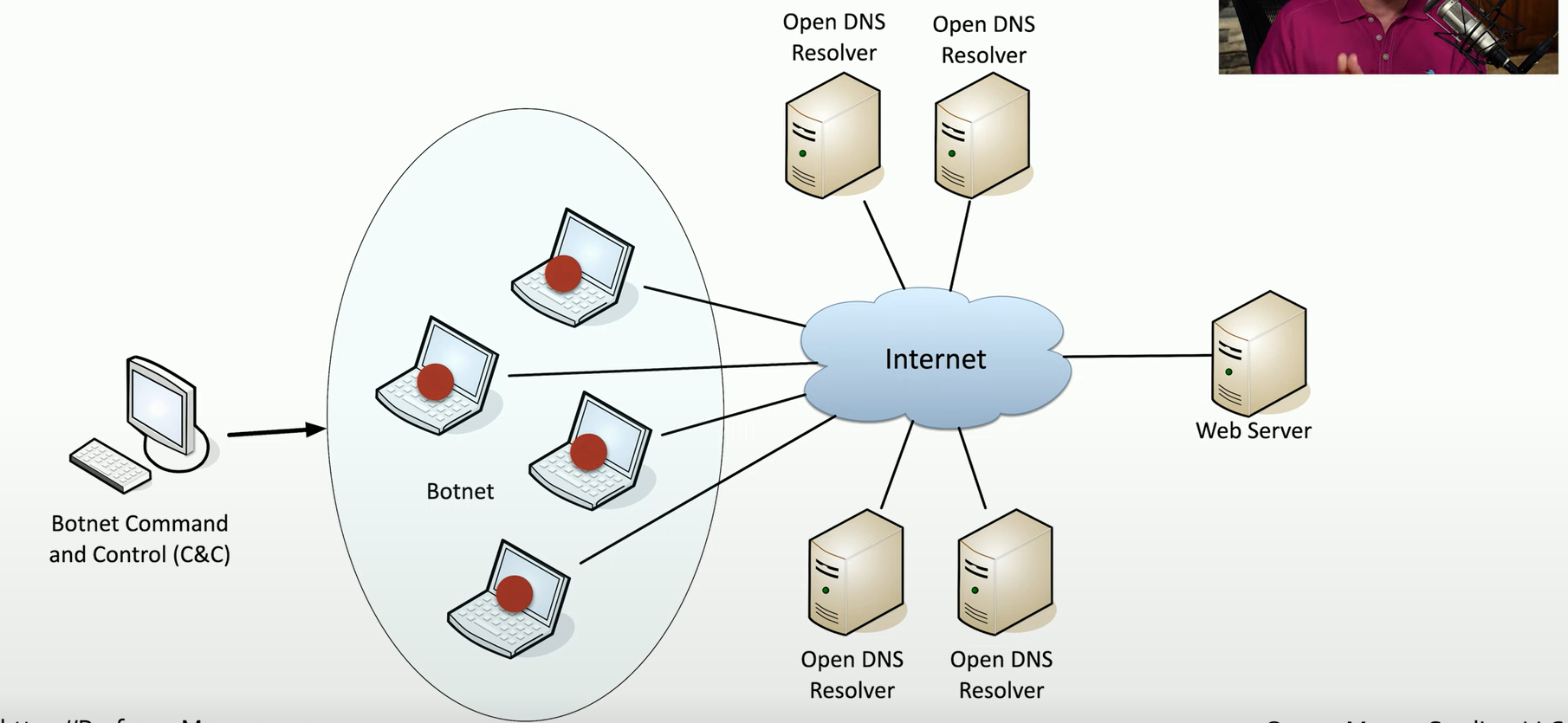
DNS Amplification DDoS:
Begins with the botnet command and control sending instructions to the botnet
The botnet devices are instructed to send queries to open DNS resolvers, with the IP address of the target web server being spoofed in the request.
The botnet devices send these queries to the open DNS resolvers.
The DNS resolvers, in turn, send their amplified responses to the spoofed web server IP address, overwhelming it with excessive traffic