LIGN 17 Midterm 1
1/35
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
36 Terms
Transposition Cipher
symbols maintain their identities but change their positions
Ex: Binary Transposition, just switching 0 and 1. So you should have the same number of characters as the original plaintext for each symbol
or ADTC
Substitution cipher
Characters staying in their places but changing identities
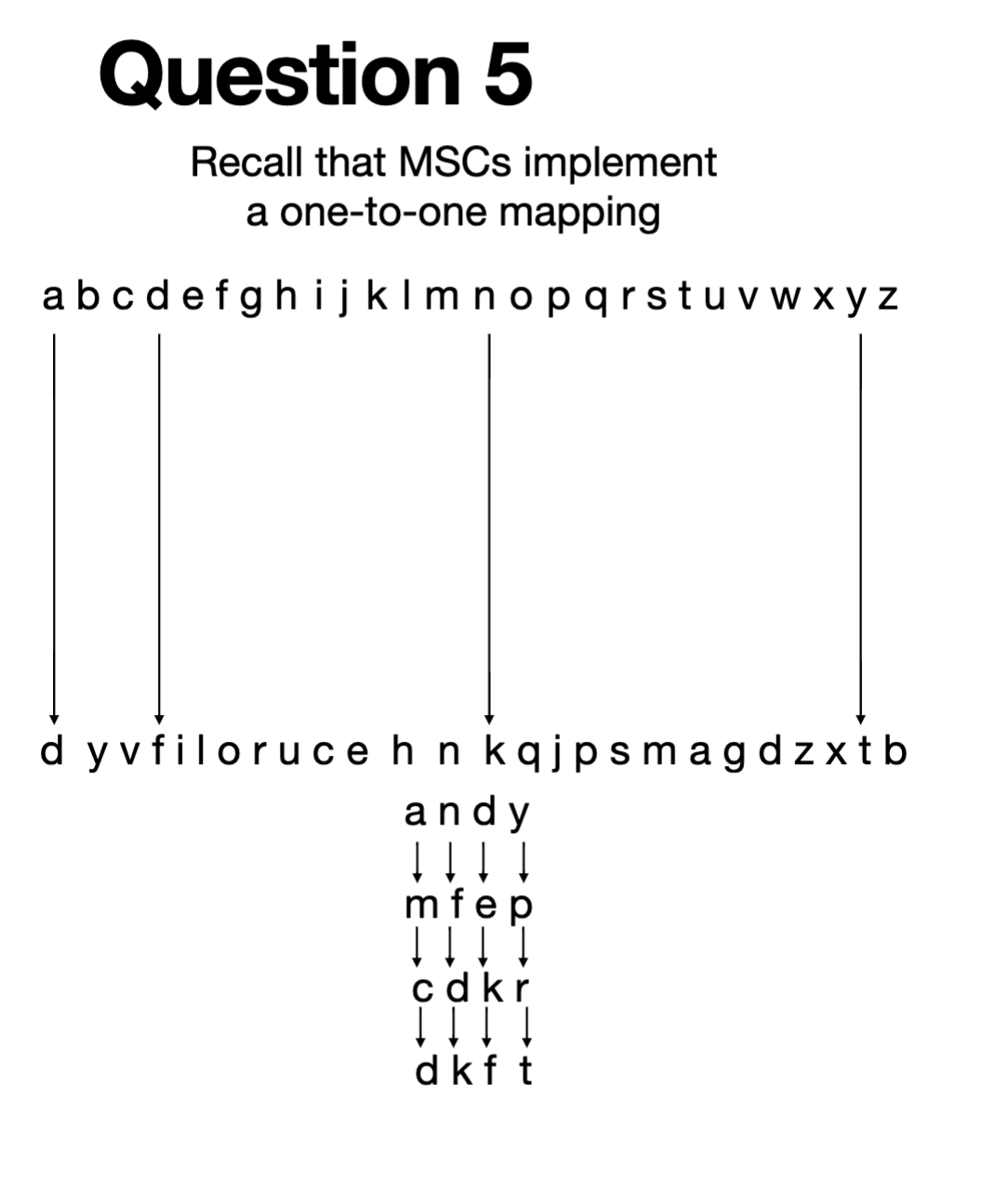
One-to-one Mapping
• Each symbol in the plain alphabet maps to a single
symbol in the cipher alphabet.
• Each symbol in the cipher alphabet maps to a single
symbol in the plain alphabet.
Ex: MSC
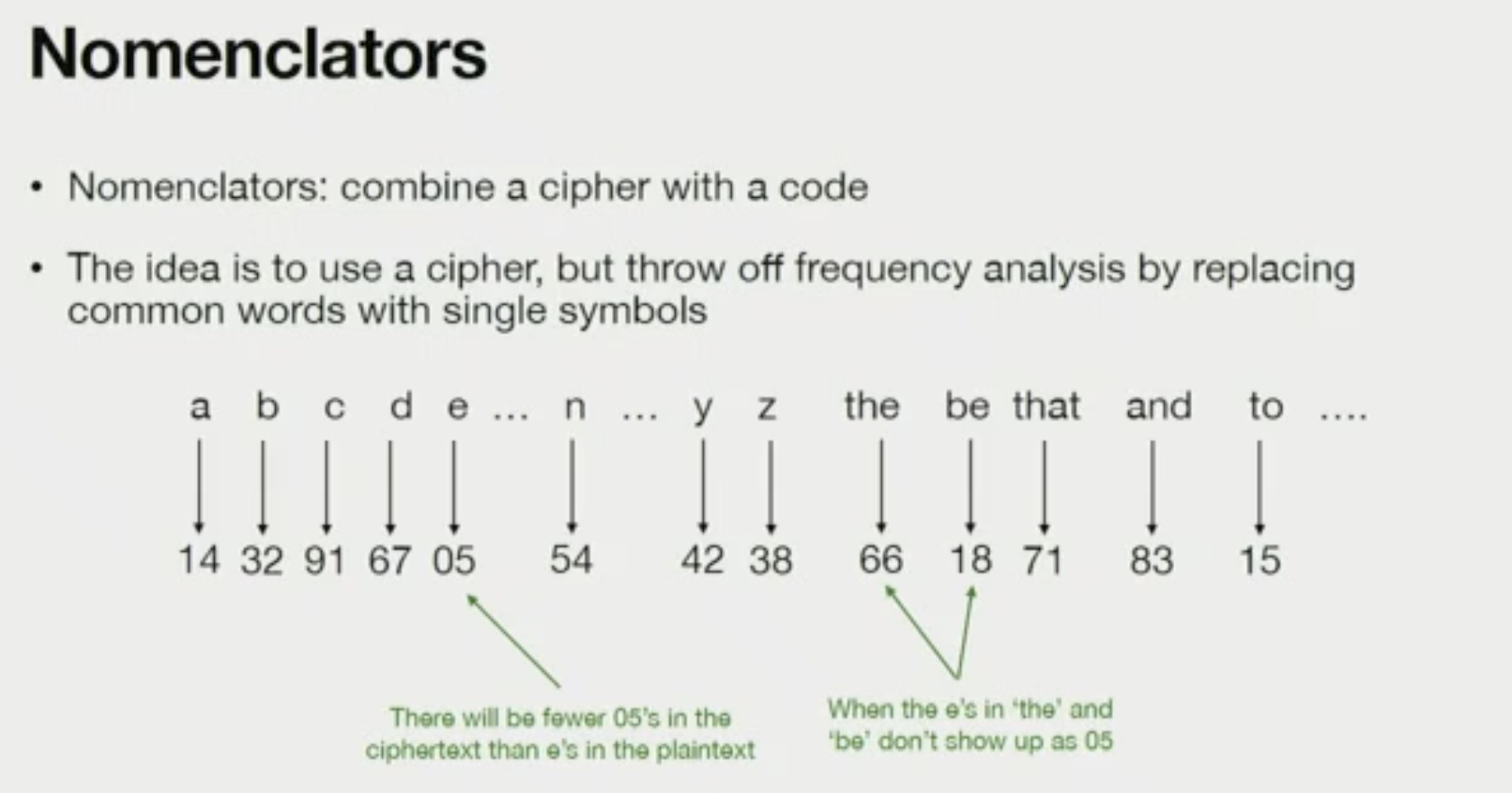
Define nomenclators
a combination of codes and ciphers when a single symbol can map to a single letter AND a symbol can map to a phrase
e.g. 12=t and 34=the
Let’s suppose that instead of using a simple monoalphabetic substitution cipher (MSC), Alice decides to do something different and use three such ciphers, applying them in succession in the following way. First, she encrypts the plaintext using an MSC with her first key, to create the first ciphertext. Then, she encrypts that ciphertext using an MSC with a second, different key, yielding a second ciphertext. Finally, she encrypts that ciphertext with a third key, yielding a third ciphertext that she sends to Bob.
Which of the following statements is most true?
The resulting cipher is generally going to be equally secure as if Alice had used just one, since for any three monoalphabetic substitution cipher keys applied one after the other, there exists another, single monoalphabetic substitution cipher key that achieves the same result.
Kerckhoff’s Principle
The security of a cryptogr-system must not depend on keeping secret the crypto-algorithm. The security depends only on keeping secret the key.
I.e. assume that Eve knows everything about the system except for the key
One-to-many Mapping
• Symbols in the plain alphabet can map to more than
one symbol in the cipher alphabet.
• Each symbol in the cipher alphabet maps to a single
symbol in the plain alphabet.
Ex: MSC w/ Homophones
Many-to-many Mapping
• Symbols in the plain alphabet can map to more than
one symbol in the cipher alphabet.
• Symbols in the cipher alphabet can map to more than
one symbol in the plain alphabet.
Ex: Vigenere
Monoalphabetic Substitution Cipher
Each letter in plaintext maps to one symbol in ciphertext.
Ex: Caesar Shift Cipher, Monoalphabetic with key phrase
Monoalphabetic Substitution Cipher w/ Homophones
Based on frequency, letter in plaintext maps to many symbols in ciphertext
Polyalphabetic Substitution Cipher
The letters in the plaintext map to multiple symbols in the cipher text
Ex: Vigenere Cipher
One-time Pad Cipher
• Key has to be as long as plaintext
• Key is generated randomly
• Key is never repeated
• Unbreakable
Book Cipher
• A book or text is the key
• Number each word (or letter) in key
Kasiski-Babbage Method
•A method for breaking Vigenere Cipher
Analyze the text for repetitions, deduce the length of the keyword or phrase (call this N)
• Do frequency analysis on N different (Caesar Shift) ciphers
Binary Transposition Cipher
Reverse pairs of digits i.e. switch 1st and 2nd digits, 3rd and 4th digits
Binary Substitution Cipher
Plaintext and codeword, if digits are the same, put 0 in ciphertext, if different, put 1 in chiphertext
• DECRYPTION ALGORITHM IS SAME AS ENCRYPTION ALGORITHM!
• Reciprocal algorithm
First In First Out (Monoalphabetic Cipher)
• Alice's key to encrypt, Bob's key to encrypt again
• Alice's key to decrypt first, Bob's key to decrypt second
First In First Out (Caesar Cipher)
• First shift 4, then shift 2
• Shift 2 in opposite direction, shift another 4
One-Way Functions
• Easy to compute in a forward direction but difficult to reverse
• Metaphor: mixing paint. We don’t have a way of separating colors once mixed
Diffie-Helman protocol
Z = Y^X (mod P)
a solution to the Key Distribution problem. ALSO, not a form of cryptography!!!
Book cipher is most similar to
Monoalphabetic substitution cipher with homophones
Define Steganography
Secret communication is achieved by masking the existence of a message (hidden message)
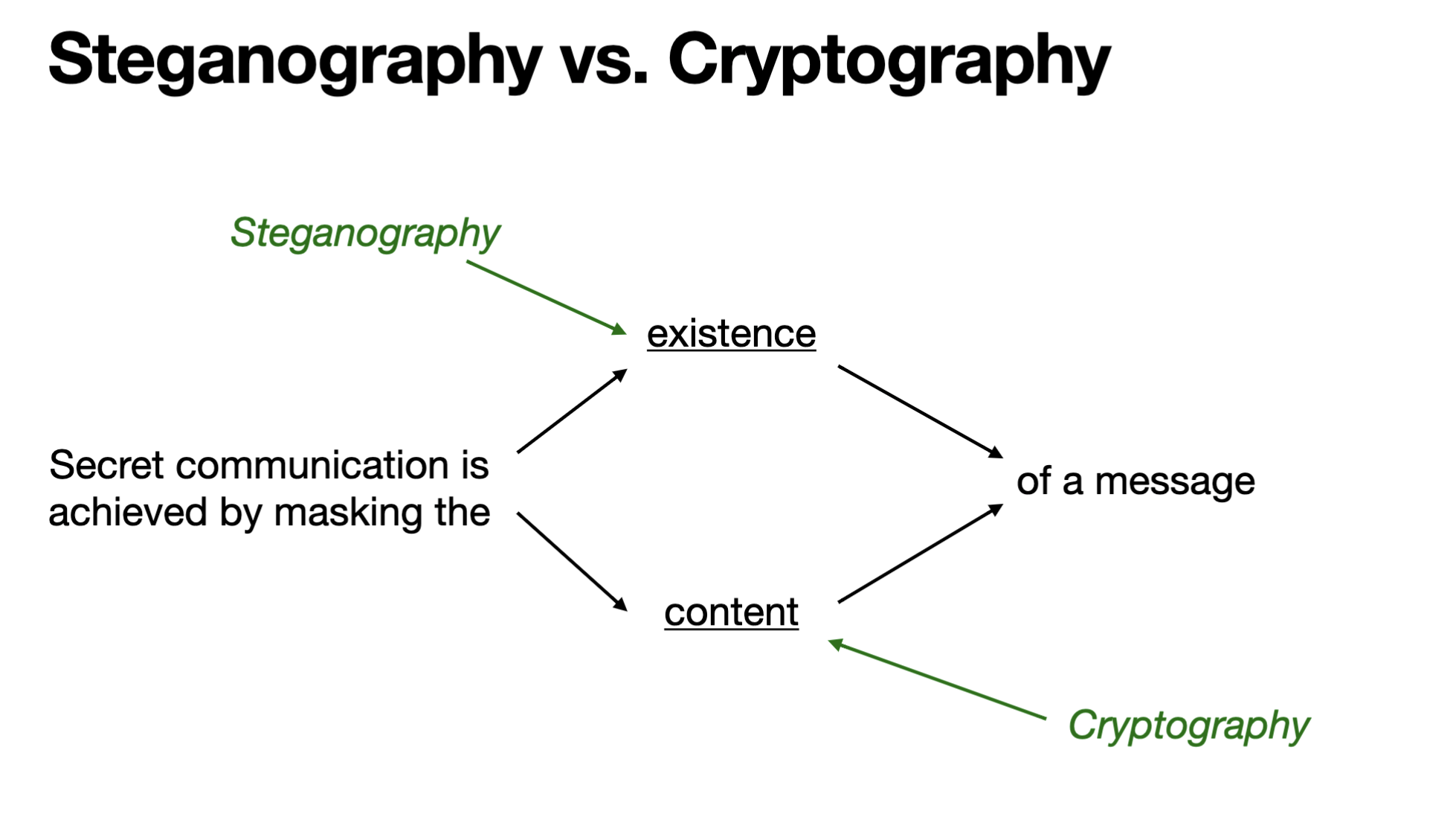
Define cryptography
Secret communication is achieved by masking the content (scrambled message)
Null
a symbol in the ciphertext that corresponds to nothing in the plaintext
What ____% of letters in English are E?
12.7
What ____% of letters in English are T?
9.1
What is a Dowbleth?
A symbol in the ciphertext that means "repeat the letter beside me" on the left or right to eliminate double letter giveaways.
Cryptographic crib
When Eve hypothesizes possible pieces of the plaintext to deduce the key
Decimal
Base 10. What humans use
XOR Cipher
A type of Binary substitution cipher. Switching the zeros and ones that are next to each other.
bit
short for binary digit
DES (Data Encryption Standard)
In the 70s, computers used this combination of transposition and substitution. 56-bit keys. By 1999, it took less than a day for a computer to break this.
key distribution problem
How can Alice and Bob agree on a key when Eve is intercepting all communication?
Which are the two ciphers in which the padlock metaphor actually would work?
XOR and Caesar shift
Binary addition
Modular Arithmetic
You divide by the mod. Your answer is the remainder (if there is a remainder)