2.4 Indicators of Compromise
1/10
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
11 Terms
Indicators of Compromise (IOC)
Evidence suggesting that a system has been breached or compromised. Provide high confidence that an attacker has gained unauthorized access to the system.
Common indicators include:
Unusual network activity
File hash changes
Irregular international traffic:
DNS modifications
Unusual authentication patterns
Increased file access
Account Lockout
Occurs when too many incorrect login attempts trigger an automatic security measure, locking the account to prevent further attempts.
Typically done to protect against brute force attacks
An account locked out due to administrative action, such as disabling the account directly through the management system, it can be a sign of a compromise
Attackers might deliberately lock the account as part of a larger plan, possibly to call the help desk, impersonate the user, and request a password reset
Organizations should have strong procedures in place for password resets
Concurrent Session Usage
Traditional physics suggests that if you’re in one location, you can’t be in another at the same time, and the same concept can be applied to login sessions.
If a user is logged in from one facility but also from a different location, it could be an indicator of compromise
Not always the case, as people often use multiple devices (e.g., desktop, laptop, mobile) across different locations, and service logins may also appear as concurrent sessions.
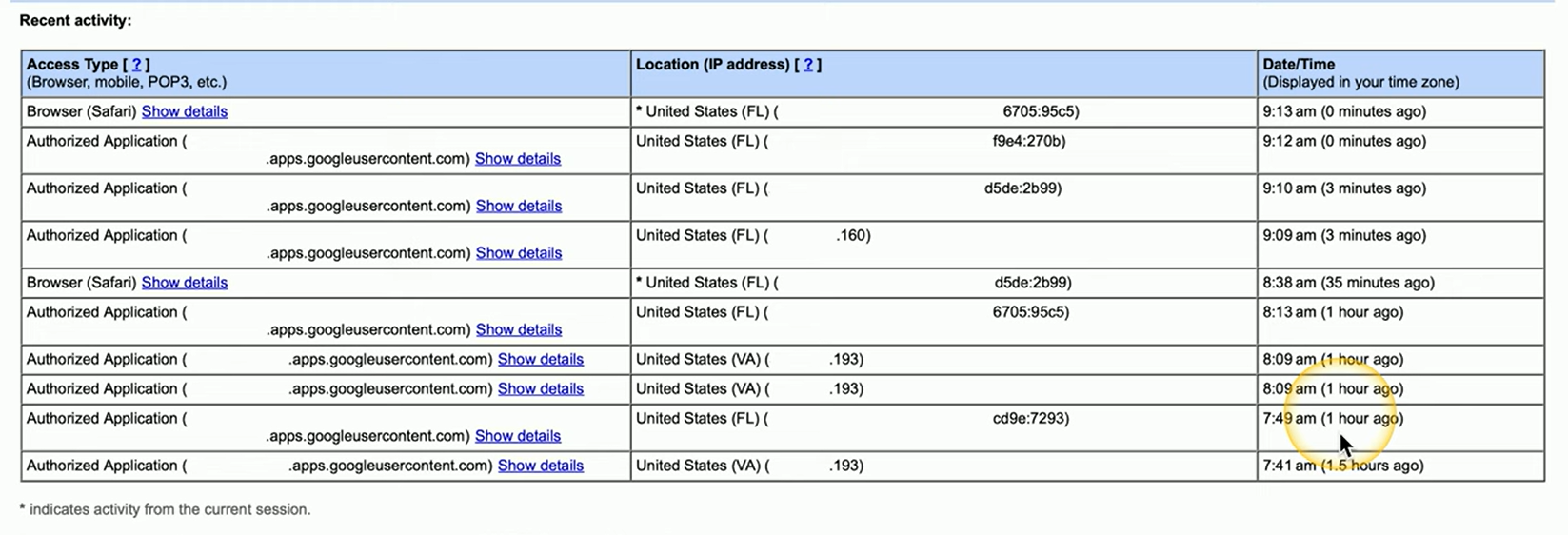
Concurrent Session Example
Report ran from a Google Mail account.
It lists out all of the different types of access, the location with the IP addresses, and when this particular activity occurred.
This can show me if I was the person logged in and using my Google Mail account or if there may be an account running elsewhere that may have access to my mailbox.
Blocked Content
Once an attacker gains access to a system, they often try to maintain control for as long as possible.
One way to do this is by blocking content related to security updates, such as antivirus software updates or security patches.
Commonly blocked content includes:
Auto-update connections
Links to security patches
Websites for third-party anti-malware tools
If a user is unable to connect to these types of security resources, it could indicate that the system has been compromised
Impossible travel
When a user logs in from two locations that are geographically distant, in a time frame that makes it impossible for them to travel between those locations.
For example, if an account logs in from a corporate office in Omaha, Nebraska, and a few minutes later, the same account logs in from Australia, this should trigger an alert.
Should be easily identifiable through log analysis
Automated log analysis can help detect these anomalies and raise alarms, providing early indicators of potential compromise.
Resource Consumption
Every action the attacker takes requires resources, and these actions often leave a trace that can be monitored.
For example, if there is an unexpected spike in network activity at an odd time, like 3:00 AM, it could be a sign of compromise.
Firewall logs showing unusual outgoing transfers, including IP addresses and timeframes, can provide the first indication of a security issue.
In some cases, a small, seemingly insignificant file transfer at an unusual time may be the only sign that an attacker has been active on the network, possibly for months.
Resource Inaccessibility
There are times when a resource being unavailable could be an indicator of compromise.
When a server is down or unresponsive, it may be because an attacker was attempting to exploit a vulnerability, causing the server to crash.
Network disruptions can also occur when the attacker transfers data or intentionally creates issues on the network to divert attention and facilitate other exploits
Encrypted data may suggest a ransomware infection
A brute force attack could lock accounts and prevent legitimate access
Out-of-Cycle Logging
Refers to log entries that occur at unexpected or irregular times, indicating potentially suspicious activity.
For instance, security patches are usually installed on a regular schedule, and everyone within the organization is aware of when updates are applied.
If logs show patches or applications being installed outside of this regular schedule, it could be an indicator of compromise.
If firewall logs show traffic being transferred at unusual times, this could also be an out-of-cycle event
Missing logs
Attackers often delete logs to cover their tracks after gaining access to a system.
Authentication logs, file access logs, firewall logs, proxy logs, and server logs
It's a best practice not only to generate reports based on log data but also to set up notifications for missing logs.
Published/Documented
When private organizational data is suddenly made publicly available on the internet
Could happen after an attacker successfully exfiltrates data without detection
Sometimes as part of a ransomware attack
Raw data may be released without context, forcing researchers to investigate and determine where the information was stolen from.