SQA Higher Computing Science Flashcards
1/75
Earn XP
Description and Tags
Terms and Definitions from the SQA Higher Computing Science course
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
76 Terms
Cardinality
The relationship 2 entities have between each other.
Each relationship also has a descriptor.
Dry run testing
Manually stepping through an algorithm without a computer.
Trace tables are an example of this.
Standard algorithm types
Find Max.
Find Min.
Linear Search.
Counting Occurrences.
Formal parameter
Information that has been passed into a function.
Actual Parameter
Information that is going to be passed into a module.
Advantages/disadvantages of using global variables
Often problematic. Errors in code can leave the value itself susceptible to accidental change.
Ways to manage traffic control
Adaptive traffic signals.
Intelligent routing systems.
Driverless cars.
Ways to manage a car management system
Intelligent smart stop systems.
Engine Control unit.
Breakpoint
A marker placed at a line of code in a program to halt execution at that point.
Can be placed where a programmer suspects there is a bug.
Disadvantages of using Bitmap Graphics
Have a very large file size as every pixel requires storage.
When scaled larger the picture will pixelate.
Bandwidth fault
Attacker send a large number of IP packets with the IP faked to take up all the available bandwidth.
Resource Starvation
Attacks aimed at taking up all of one resource (Memory, Disk Space)
Domain Name Service
An attack aiemd at taking down the DNS of a company.
Steps of the fetch execute cycle
Memory address of next instruction is placed on address bus
Processor activates Read Line on control bus
Instruction is fetched from memory location using data bus
Instruction decoded and executed
Factors affecting performance
Number of processors(cores)
Width of Data Bus
Clock Speed
Cache Memory
Main environmental impacts from computers
Heating Systems
Traffic Control
Car management system
Manage heating systems
Knowing when the house is empty
Smart Climate Assistant
Remote control of the heating system
Zoning areas of the house
_ & ?
A single character in an SQL wildcard
LIKE
Term in WHERE statement to enable an SQL wildcard
One to one relationship
Where two tables are linked together where a record in one table is only related to a single record in another table
One to many relationship
Most common type of relationship
A row in table A can have many matching rows in table B. But a row in table B can have only a matching row in table A.
Many to many relationship
Occurs when multiple records in a table are associated with multiple records in another table.
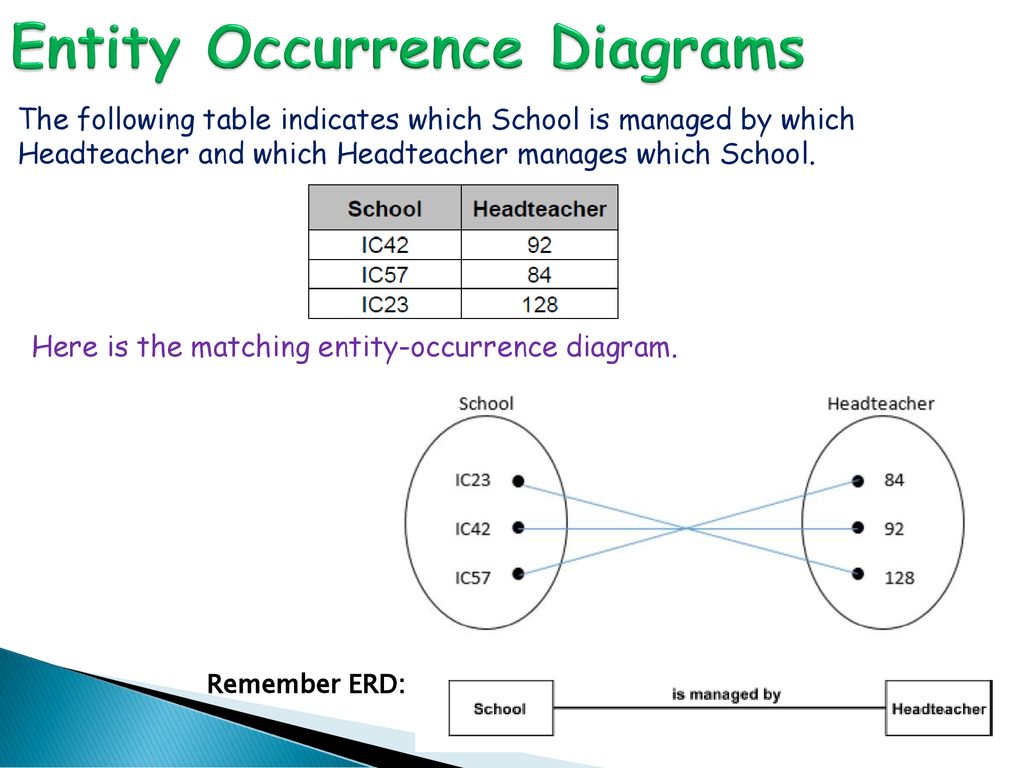
Entity Occurence Diagram
Aggregate functions
AVG()
COUNT()
MIN()
MAX()
SUM()
AVG()
Returns the average value of a numeric field
COUNT()
Returns the number of rows that match the criterias in the WHERE clause.
MIN()
Returns the lowest value of a field.
MAX()
Returns the largest value of a field
SUM()
Returns the total value of a numeric field?
Breakpoint
A marker placed at a line of code in a program to halt execution at that point.
Can be placed where the programmer suspects a bug.
Watchpoint
A way of targeting a specific variable to keep track of during program execution.
Record/class code
class A()
…def_init_(B):
……self.X=””
…….self.Y=0
…….selfZ=0.0
Local variable
Variable is declared inside a function.
Global variable
Variable declared outside of a function.
Advantages/disadvantages of using local variables
Improve maintainability by allowing developers to reuse variable names without conflict.
Purpose of a program
What the program is required to do, usually used to gain an overview of the entire system.
Scope of a program
Involves which deliverables will be created by the end of development.
Assumptions of a program
Beliefs based on previous experience and the information available to you. (Educated guesses)
Boundaries of a program
The limits that help to define what is in the project and what is not. It can also clarify any assumptions made by software developers regarding the request.
Advantages of modularity
Less code has to be written
Allows many people to work on the same program
Code can be stored across multiple files
Functions are short, simple and easy to understand
The same code can be used in many applications
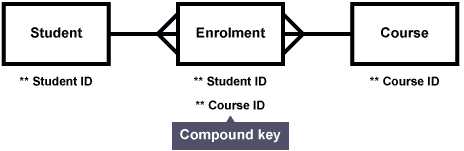
Entity relationship diagram
AS
Word written in the SELECT statement to enable an aggregate function
A = [B]
Written in the WHERE statement to enable an aggregate function
Composite key
A primary key made up of two or more attributes.
Used when no single field is suitable for a primary key.
Compound key
Each attribute that makes up the key is a primary key in another table.
Junction table
Changes a many to many relationship to two one to many relationships instead.
Convert 2’s compliment to Binary
Write out number in standard Binary
Invert the digits
Add 1
Convert Binary to Denary
Invert the number
Add 1
Calculate denary and add a negative symbol
-2n^-1 to (2^n-1)-1
Formula for calculating the range of numbers
Range of Numbers
Do 2^ the number of bits
Divide in half = negative
Take 1 away = positive
Advantages and disadvantages of more bits being allocated to the Exponent
Increased Range
Decreased Accuracy/Precision
Advantages and disadvantages of more bits being allocated to the exponent
Increased Accuracy/Precision
Decreased Range
Processor’s effect on performance
More cores = higher performance because the processor execute more instructions at the same.
Clock speed’s effect on performance
Higher the speed, the faster the performance.
Software development methodologies
Iterative
Adaptive
Iterative development
Client is involved at the beginning and the end
Suitable for larger projects
Predictive
Adaptive development
Client is present at all major stages
Suitable for smaller projects
Effects on performance from width of the data bus
Larger the width the greater the performance as it can transfer more bits at once
Cache Memory’s effect on performance
Uses SRAM whereas RAM uses DRAM. If a computer has to the cache memory, from here the computer can access this instruction faster.
% & * in an SQL wildcard?
0, 1 or many characters.
Calculate the signbit and Mantissa 15 bits of a negative with a positive exponent
Sign Bit. Negative = 1 or Positive = 0
15 bits .Move number to the right of decimal points and fill the rest of the boxes with 0s
Exponent. How many moves to right? Calculate in 8 bit binary.
Unicode
Uses either 16/32 or 64 bits of storage meaning it can show far more characters.
Advantages of Bitmap Graphics
Can be edited at pixel level adding extra details to the image will not increase the file size
Can create photo realistic images
Tracking cookies
Records your details and transmits them back to the author
Used to gather marketing information
Public key
Encrypts the data
Private key
Decrypts the data
Computer Misuse Act actions
Access comptuer material without permission
Access computer material with the intent of commiting futher offences
Modify computer materials without permission
Symptoms and effects of DOS and DDOS attacks
Slow performance
Inability to acces
Disruption to users and business
Costs of DOS and DDOS attacks
Customers not being able to buy goods
Not being able to carry out the organisations business
Having to fix any faults
Reasons for DOS and DDOS attacks
Political
Personal
Reputation
Business
Money
Fetch execute cycle
A series of steps that takes place for a processor to execute an instruction.
Digital signature
Added to information to ensure that the information came from the coreect place.
Digital Certiciate information
The certificate serial number
The expiry date
The name of the holder
A copy of the public key
The digital signature of the certiciate authority.
% or Modulo in Python
Remainder operator
Advantages of modularity