Certified Ethical Hacker (CEHv13) Module 20 Cryptography
1/159
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
160 Terms
Cryptography
Cryptography is the practice of concealing information by converting plaintext into ciphertext using a key or encryption scheme
Objectives of Cryptography
- Confidentiality
- Integrity
- Authentication
- Nonrepudiation
Confidentiality
Assurance that the information is accessible only to those authorized to access it
Integrity
Trustworthiness of data or resources in terms of preventing improper and unauthorized changes
Authentication
Assurance that the communication, document, or data is genuine
Nonrepudiation
Guarantee that the sender of a message cannot later deny having sent the message and that the recipient cannot deny having received the message
Types of Cryptography
- Symmetric Encryption
- Asymmetric Encryption
Symmetric Encryption
Symmetric encryption requires that both the sender and the receiver of the message possess the same encryption key.
Asymmetric Encryption
An asymmetric-key system is an encryption method that uses a key pair comprising a public key available to anyone and a private key held only by the key owner
Asymmetric Encryption Steps
1. An individual finds the public key of the person he or she wants to contact in a directory
2. This public key is used to encrypt a message that is then sent to the intended recipient
3.. The receiver uses the private key to decrypt the message and reads it
Symmetric Encryption Strengths
- Faster and easier to implement
- Requires less processing power
- Can be implemented in application-specific integrated chip (ASIC)
- Prevents widespread message security compromise
- The key is not bound to the data being transferred on the link; therefore, even if the data are intercepted, it is not possible to decrypt it
Symmetric Encryption Weaknesses
- Lack of secure channel to exchange the secret key
- Difficult to manage and secure too many shared keys that are generated to communicate with different parties
- Provides no assurance about the origin and authenticity of a message
- Vulnerable to dictionary attacks and brute-force attacks
Asymmetric Encryption Strengths
- Convenient to use, as the distribution of keys to encrypt messages is not required
- Enhanced security, as one need not share or transmit private keys to anyone
- Provides digital signatures that cannot be repudiated
Asymmetric Encryption Weaknesses
- Slow in processing and requires high processing power
- Widespread message security compromise is possible
- Messages received cannot be decrypted if the private key is lost
- Vulnerable to man-in-the-middle and brute-force attacks
Government Access to Keys (GAK)
GAK refers to the statutory obligation of individuals and organizations to disclose their cryptographic keys to government agencies.
Key escrow
A key exchange arrangement in which essential cryptographic keys are stored with a third party in escrow. The third party can use or allow others to use the encryption keys under certain predefined circumstances
Cipher
An algorithm for performing encryption and decryption
Enchiperment
Process of converting plaintext into a cipher or code
Decipherment
Process of converting ciphertext into plaintext
Types of Ciphers
- Classical (Substitution, Transposition)
- Modern (Symmetric-Key, Asymmetric-Key, Block, Stream)
Classical Ciphers
Classical ciphers are the most basic type of ciphers, which operate on letters of the alphabet (A-Z).
Types of Classical Ciphers
- Substitution
- Transposition
Substitution Cipher
The send replaces units of plaintext with ciphertext according to a regular system. The recipient performs inverse substitution to decipher the text.
Transposition Cipher
Letters in the plaintext are rearranged according to a regular system to produce the ciphertext
Modern Cipher
Uses a one-way mathematical function that is capable of factoring large prime numbers
Types of Modern Ciphers
- Symmetric Key
- Asymmetric Key
- Block
- Stream
Block Cipher
Deterministic algorithms operating on a block (a group of bits) of fixed size with an unvarying transformation specified by a symmetric key.
Stream Cipher
Plaintext bits are combined with a key stream one bit at a time
Data Encryption Standard (DES)
DES is a standard for data encryption that uses a secret key for both encryption and decryption (symmetric cryptosystem). DES uses a 64-bit secret key, of which 56 bits are generated randomly and the other 8 bits are used for error detection
Triple DES (3DES)
Because of the inherent weakness of DES some organizations 3DES, in which they repeat the process three times for added strength
Advanced Encryption Standard (AES)
An iterated block cipher that works by repeating the defined steps multiple times
3DES Potential Key Values/Relationships
- K1 ≠ K2 ≠ K3
- (K1 = K3) ≠ K2
- K1 = K2 = K3
RC4
RC4 is a variable key-size symmetric-key stream cipher with byte-oriented operations, and it is based on the use of a random permutation
RC5
Uses a parameterized algorithm with a variable block size, a variable key size, and a variable number of rounds. The routines used in RC5 are key expansion, encryption, and decryption.
RC5 Key Expansion
In the key expansion routine, the secret key that a user provides is expanded to fill the key table (the size of which depends on the number of rounds)
RC6
RC6 is a symmetric-key block cipher derived from RC5. Two features that differentiate RC6 from RC5 are integer multiplication and the use of four 4-bit working registers rather than two 2-bit registers.
Blowfish
A symmetric block cipher algorithm designed to replace DES or IDEA algorithms
Blowfish Key Expansion Steps
1. Initialize the P-array and S-boxes
2. XOR the P-array with the key bits
3. Encrypt the all-zero string
4. New output is now P1 and P2
5. Encrypt the new P1 and P2 with the modified subkeys
6. New output is now P3 and P4
7. Repeat the process 521 times to calculate new subkeys for the P-array and the four S-boxes
Threefish
A large tweakable symmetric-key block cipher in which the block and key sizes are equal, using 3 operations
Twofish
Allows various levels of performance trade-off on parameters such as encryption speed, hardware gate count, memory usage, etc. This technique of enabling different implementations improves the relative performance of the algorithm.
Serpent
One of the most secure encryption mechanisms in AES contests, but has a slower encryption speed and is more complex
Tiny Encryption Algorithm (TEA)
A Feistel cipher
CAST-128
A symmetric-key block cipher having a classical 12-or 16-round Feistel network
Government Standard (GOST)
A symmetric-key block cipher having a 32-round Feistel network working on 64-bit blocks with a 256-bit key length
Camellia
A symmetric key block cipher that is part of TLS
Digital Signature Algorithm (DSA)
Helps in the generation and verification of digital signatures for sensitive and unclassified applications
Digital Signature
A digital signature is a mathematical scheme used for the authentication of digital messages.
Rivest Shamir Adleman (RSA)
A public-key cryptosystem for Internet encryption and authentication
RSA Signature Scheme
A deterministic digital signature scheme that provides message recovery from the signature itself, making it the most practical and versatile technique available
Diffie-Hellman
A cryptographic protocol that allows two parties to establish a shared key over an insecure channel
Elliptic Curve Cryptography (ECC)
ECC is a modern public-key cryptography developed to avoid larger cryptographic key usage. The asymmetric cryptosystem depends on number theory and mathematical elliptic curves (algebraic structure) to generate short, quick, and robust cryptographic keys.
YAK
YAK is a public-key-based Authenticated Key Exchange (AKE) protocol.
Hash Functions
Hash functions calculate a unique fixed-size bit string representation, called a message digest, of any arbitrary block of information. The main role of a cryptographic hash function is to provide integrity in document management.
MD5
MD5 is a widely used cryptographic hash function that takes a message of arbitrary length as input and outputs a 128-bit (16-byte) fingerprint or message digest of the input.
Hash-based message authentication code (HMAC)
A type of message authentication code
(MAC) that uses a cryptographic key along with a cryptographic hash function. It is widely used to verify the integrity of data and authentication of a message.
Multilayer Hashing
Multilayer hashing, also known as nested hashing or recursive hashing, is a technique in which a hash function is applied multiple times to the input or output of a previous hash operation.
Hardware-Based Encryption
Hardware-based encryption is a technique that uses computer hardware for assisting or replacing the software when the data encryption process is being performed.
Types of Hardware Encryption Devices
- TPM
- HSM
- USB Encryption
- Hard Drive Encryption
Trusted Platform Module (TPM)
A crypto-processor or a chip that is present in the motherboard. It can securely store the encryption keys and perform many cryptographic operations.
Hardware Security Module (HSM)
An additional external security device that is used in a system for crypto-processing, and it can be used for managing, generating, and securely storing cryptographic keys.
USB Encryption
USB encryption is an additional feature for USB storage devices, which offers onboard encryption services. Encrypted USB devices need an on-device credential system or software-or hardware-based credentials from a computer. USB encryption provides protection against malware distribution over USB and helps in preventing data loss and data leakage.
Hard Drive Encryption
Hard drive encryption is a technology whereby the data stored in the hardware can be encrypted using a wide range of encryption options. Hard drive encryption devices cannot use an on-device keyboard or fingerprint reader; instead, they need a TPM or an HSM. These devices can be installed as an internal drive on a computer.
Quantum Cryptography
In quantum cryptography, the data elements are encrypted by a sequence of photons that have a spinning trait while traveling from one end to another end. These photons keep changing their shapes during their course through filters: vertical, horizontal, forward slash, and backslash.
Homomorphic Encryption
Homographic encryption allows users to secure and leave their data in an encrypted format even while it is being processed or manipulated.
Post-quantum cryptography
An advanced cryptographic algorithm (mostly public-key based) designed to protect security systems against attacks initiated from both conventional and quantum computers
Lightweight Cryptography
A major challenge in current cryptography techniques is its usage in low-powered devices. The main objective of developing lightweight cryptography is to use less power and less resources without compromising security
Block Cipher Modes of Operation
- Electronic Code Book (ECB)
- Cipher Block Chaining (CBC)
- Cipher Feedback (CFB)
- Counter Mode
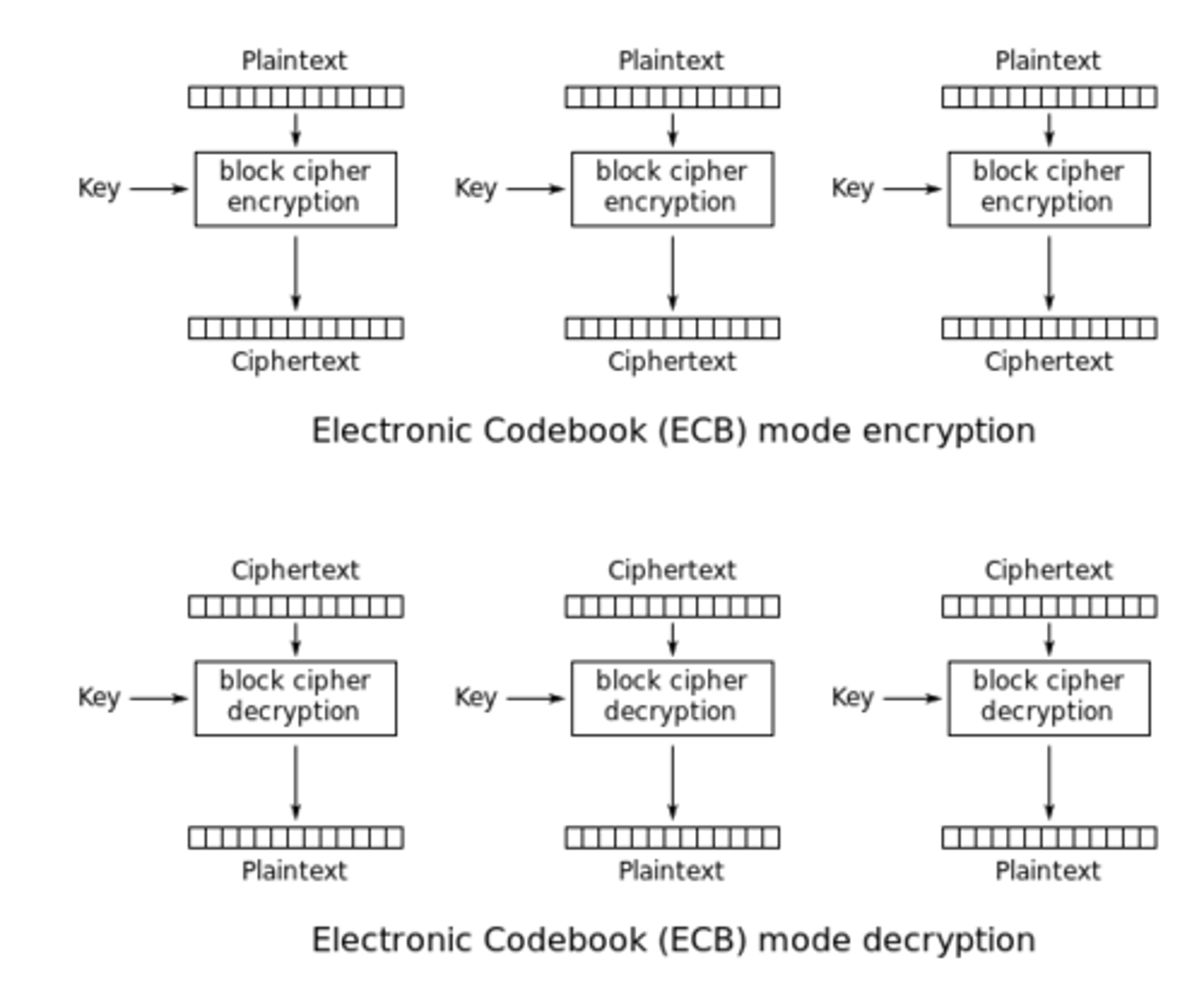
ECB Mode
Each block encrypted separately
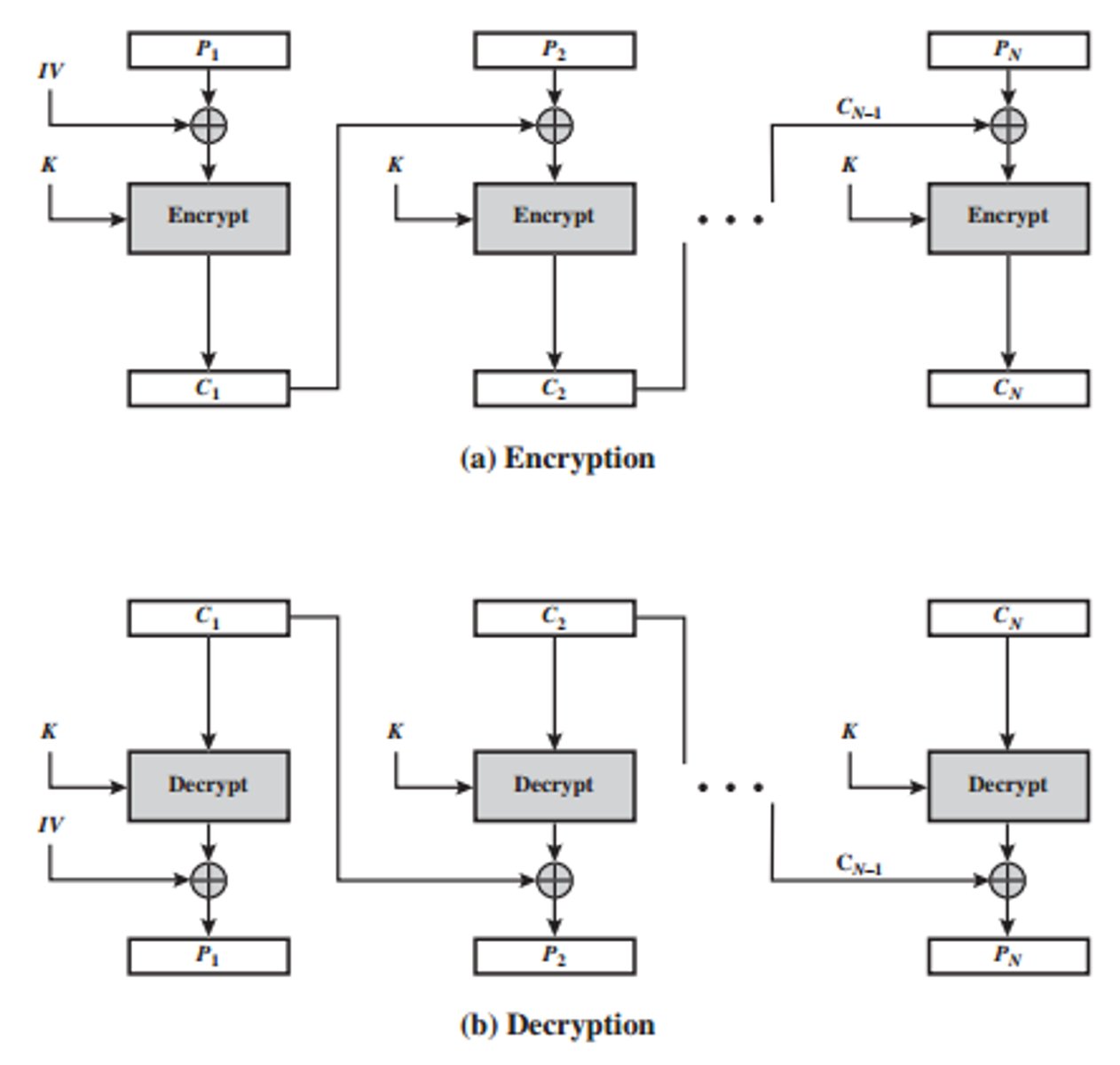
CBC Mode
Previous block used to help encrypt/decrypt the next block
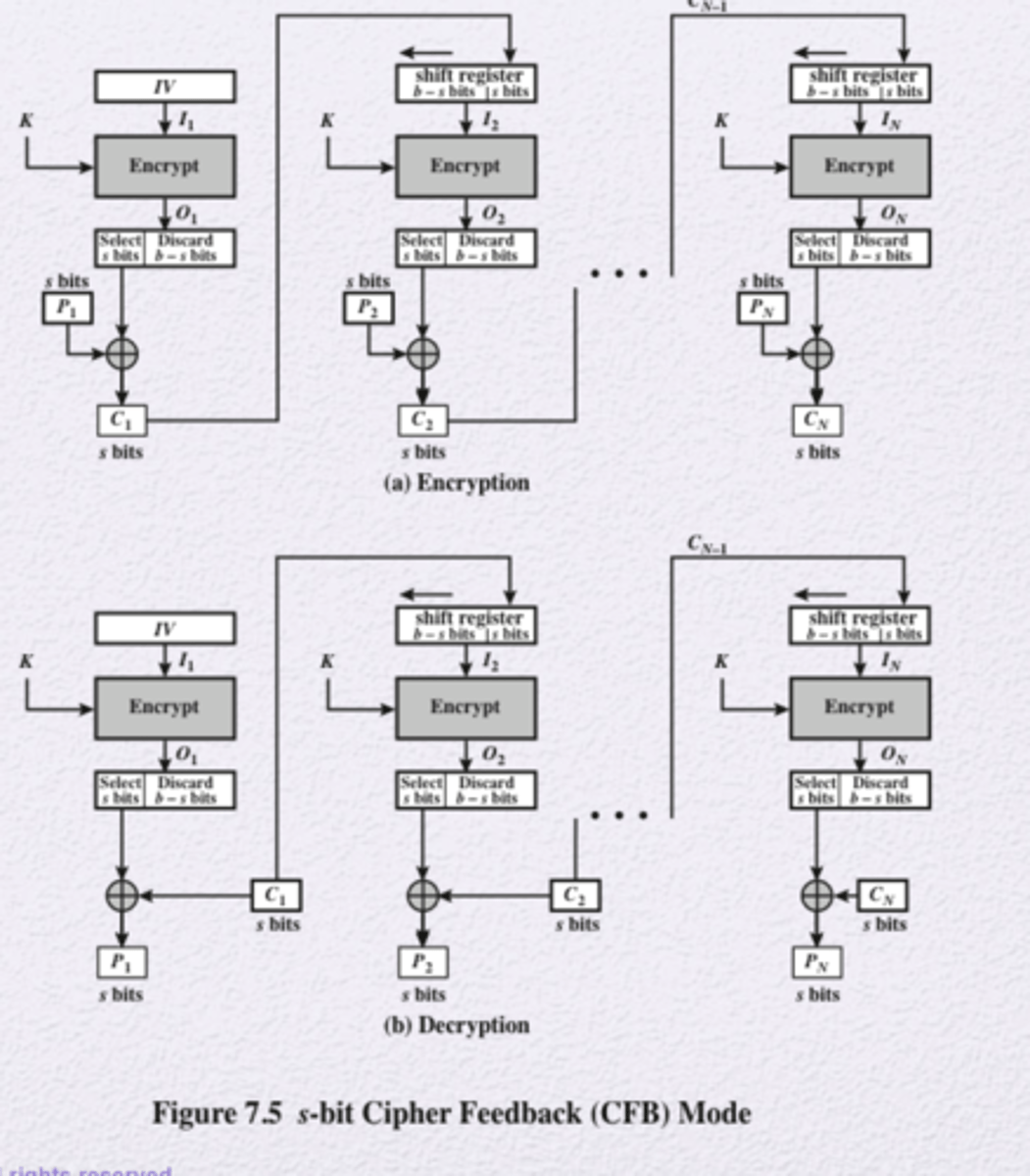
Cipher Feedback (CFB) Mode
Input is processed s bits at a time. Preceding ciphertext is used as input to the encryption algorithm to produce pseudorandom output, which is XORed with plaintext to produce next unit of ciphertext.
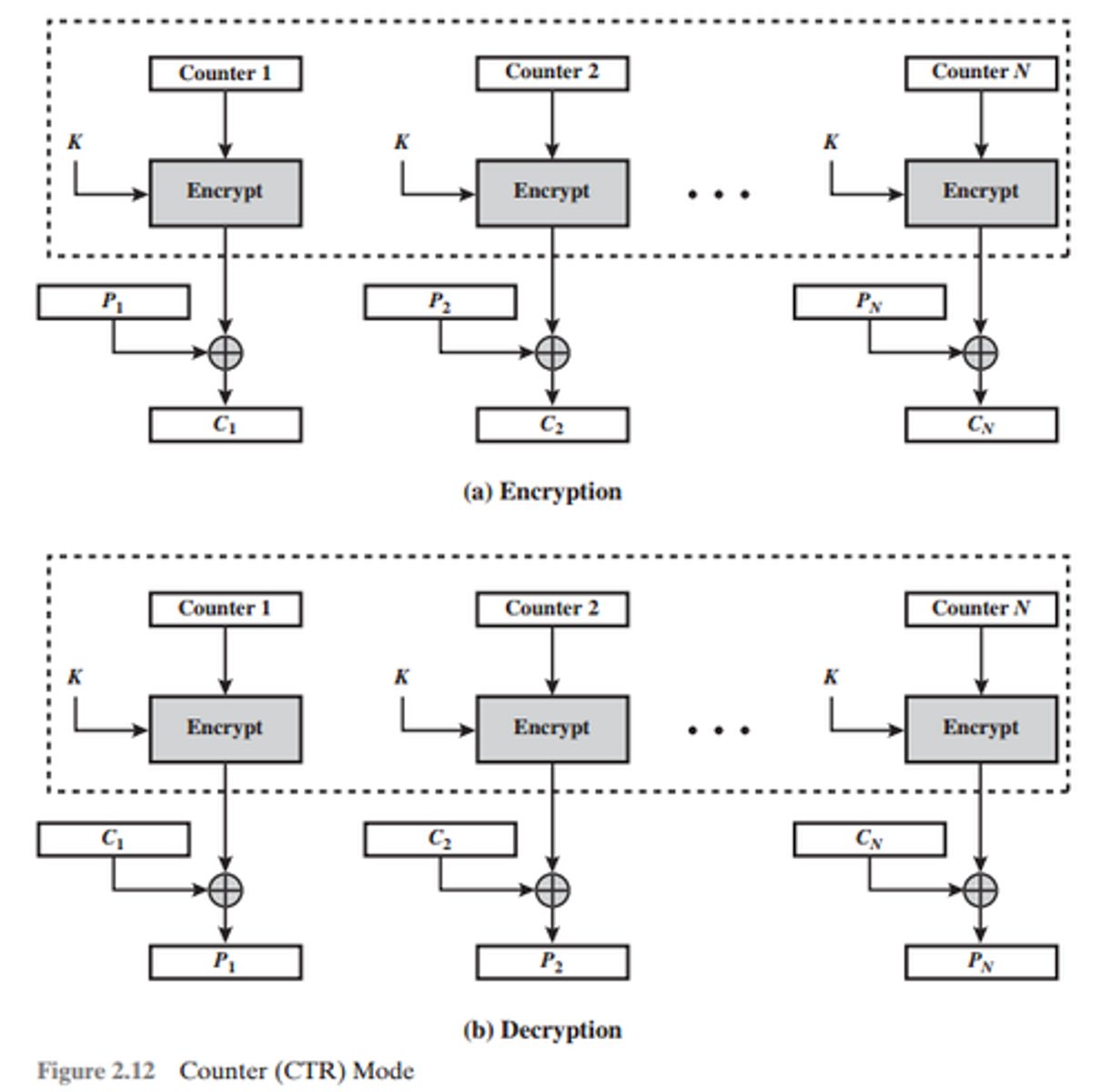
Counter Mode
An encryption mode of operation where a numerical counter value is used to create a constantly changing IV. Also referred to as CTM (counter mode) and CM (counter mode).
Authenticated Encryption
AE modes of operation provide integrity and confidentiality for a transmitted message
Message Authentication Code (MAC)
A MAC is a value obtained by hashing a plaintext message using a shared secret key. It provides integrity for the message, and the receiver can verify the message using the hash value attached to it.
Encrypt-then-MAC (EtM)
The plaintext is first encrypted using a secret key. For the obtained ciphertext, a hash value called message authentication code (MAC) is generated. The MAC is attached to the ciphertext and transmitted.
Encrypt-and-MAC (E&M)
A MAC is first generated for the plaintext, following which the plaintext is encrypted using a secret key. Finally, both the ciphertext and MAC are combined and transmitted.
MAC-then-encrypt (MtE)
In the MtE approach, a MAC is first generated for the plaintext using the hash function, and the MAC is combined with the plaintext. The combination of the plaintext and MAC is encrypted with a secret key to produce ciphertext. The ciphertext contains the encrypted MAC
Authenticated Encryption with Associated Data (AEAD)
AEAD is another approach used to ensure the integrity and authenticity of a message that contains both encrypted and unencrypted data. This approach adds additional data to the ciphertext at certain places to thwart chosen ciphertext attacks. The message header is kept unencrypted so that the receiver can verify the source of the message, and the payload is encrypted to ensure confidentiality
Public Key Infrastructure (PKI)
PKI is a security architecture developed to increase the confidentiality of information exchanged over the insecure Internet. The PKI helps to bind public keys with corresponding user identities.
Components of PKI
- Certificate Management System
- Digital Certificates
- Validation Authority (VA)
- Certification Authority (CA)
- End User
- Registration Authority (RA)
Certificate Management System
Generates, distributes, stores, and verifies certificates
Digital Certificate
Establishes credentials of a person when performing online transactions
Validation Authority (VA)
Stores certificates (with their public keys)
Certification Authority (CA)
Issues and verifies digital certificates
PKI End User
Requests, manages, and uses certificates
Registration Authority (RA)
Acts as the verifier for the CA
Steps Involved in PKI
1. End user applies for a certificate to the registration authority (RA)
2. The RA receives the request from the subject, verifies the subject's identity, and requests the CA to issue a public key certificate to the user
3. The CA issues the public key certificate binding the subject's identity with the subject's public key; then, the updated information is sent to the validation authority (VA).
4. When a user makes a transaction, the user duly signs the message digitally using his private key and sends the message to the client
5. The client verifies the authenticity of the user by inquiring with the VA about the validity of the user's public key certificate (which was updated in step 3)
6. The VA compares the public key certificate of the user with that of the updated information provided by the CA and determines the certificate
Signed PKI Certificate
The user gets a digital certificate from a trustworthy CA. The digital certificate contains name of the certificate holder, a serial number, expiration dates, a copy of the certificate holder's public key and the digital signature of the CA. The user signs the document using the private key and sends to the receiver. The receiver can verify the certificate by enquiring with validation authority (VA). VA verifies the validity of the certificate.
Self Signed PKI Certificate
The user creates self-signed digital certificate using certification creation tools. The certificate contains name of the user, user's public key and his digital signature. The user signs the document using the self-signed certificate and sends to the receiver. The receiver can verify the certificate by enquiring with the user. The user verifies the certificate to the receiver
Secure Sockets Layer (SSL)
An application layer protocol for managing the security of message transmission on the Internet. It is used to provide a secure authentication mechanism between two communicating applications. SSL requires a reliable transport protocol, such as TCP, for data transmission and reception. It uses RSA asymmetric (public-key) encryption to encrypt data transferred over SSL connections.
SSL Handshake Protocol Flow
1. The client sends a hello message to the server, to which the server must respond with a hello message
2. The server sends a certificate to the client for authentication
3. The server sends a "hello done" message to inform the client that the handshake phase is complete and waits for the client's response
4. If the client receives a certificate-request message, the client must respond to the message by sending a certificate message or "no certificate" alert. The server sends the client key-exchange message. If the certificate sent by the client has signing ability, a digitally signed certificate verifies the message, and the client transmits it
5. The client transmits the changed cipher-spec message and copies the pending cipher spec into the current cipher spec. The client sends a message to initiate the completion of the message under the new algorithm, keys, and secrets
6. In response, the server replies by sending its own changed cipher-spec message, transfers the pending cipher spec to the current cipher spec, and initiates the completion of the message under the new cipher spec. At this point, the handshake is complete and the server starts exchanging the application-layer data
Transport Layer Security (TLS)
TLS is used to establish a secure connection between a client and a server and ensure the privacy and integrity of information during transmission.
TLS Layers
- TLS Record Protocol
- TLS Handshake Protocol
TLS Record Protocol
The TLS Record Protocol is a layered protocol. It provides secured connections with an encryption method such as DES. It secures application data using the keys generated during the handshake and verifies its integrity and origin
TLS Handshake Protocol
The TLS Handshake Protocol allows the client and server to authenticate each other and
select an encryption algorithm and cryptographic keys prior to data exchange by the application protocol.
Pretty Good Privacy (PGP)
A protocol used to encrypt and decrypt data with authentication and cryptographic privacy. It combines the best features of both conventional (around 1,000 times faster than public-key encryption) and public-key cryptography (solution to key distribution and data transmission issues) and is thereby, known as a hybrid cryptosystem
PGP Encryption Steps
1. When a user encrypts data with PGP, PGP first compresses the data
2. PGP then creates a random key that is a one-time-only secret key
3. PGP uses the random key generated to encrypt the plaintext, resulting in a ciphertext
4. Once the data is encrypted, a random key is encrypted with the recipient's public key
5. The public-key-encrypted random key is sent along with the ciphertext to the recipient
GNU Privacy Guard (GPG)
A software replacement of PGP and free implementation of the OpenPGP standard
Web of Trust (WOT)
A trust model of PGP, OpenPGP, and GnuPG accessible systems. It is an idea of decentralizing the key distribution among PGP users.
Secure/Multipurpose Internet Mail Extensions (S/MIME) Encryption
S/MIME certification is a technique that allows users to encrypt their email messages
Office 365 Message Encryption (OME)
Allows users to send an encrypted email message to any email address. OME requires receivers to login to a Microsoft Office 365 account or use a one-time password to authenticate themselves