Network Security Concepts
1/36
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
37 Terms
CIA Triad
Confidentiality, Integrity, and Availability
Confidentiality
Access Controls: Mechanisms such as passwords, biometric verification, or access cards that limit resource access to authorized personnel
Encryption
Secure Communication: Using secure protocols like SSl/TLS for transmitting data to prevent interception by unauthorized entities
Integrity
Protecting data from unauthorized changes to ensure that it is reliable and correct. Key aspects:
Data accuracy
Data consistency
Data trustworthiness
Various methods are used, such as Cryptographic hash functions and digital signatures, Access controls as well
Availability
Ensuring data, systems, and services are accessible to authorized users when needed. Ways to do so:
Fault tolerance
Backup Systems
Risk
Asset: Anything within an environment that should be protected
Asset Valuation: A dollar value assigned to an asset based on actual cost and non-monetary expenses
Threats: Any potential occurrence that may harm the asset
Threat Agent/Actors: People, programs, hardware, or systems that used threats to cause harm
Threat events
Threat Vectors: A threat/attack vector is the path or means by which an attack/attacker can gain access to a target in order to cause harm
Vulnerabilities: Weakness in an asset or the absence or the weakness of a safeguard or countermeasure that could be exploited
Exposure: Actual or anticipated damage from a threat
Safeguards: Anything that removes/reduces risk
Attack: The threat exploiting the vulnerability, (the attempt to attack/exploit it)
Breach: The occurrence of a security mechanism being bypassed or thwarted by a threat agent (a successful attack)
Identity and Access Management (IAM)
A framework of business processes, policies, and technologies that facilitates the management of electronic or digital identities. Ensures the right people can access the right resources at the right times for the right reasons. Crucial for security and regulatory compliance
MAC (Mandatory Access Controls)
A security model in which access rights are regulated by a central authority based on different levels of security clearance. Use case: Common in government and military systems where classified info is involved.
Key aspect: Users cannot change access permissions… they are set and enforced by a system admin
DAC (Discretionary Access Control)
Security model where the resource owner decides on access levels. Most flexible access model. Used in environments where users need control over the resources they own, like file permissions etc.
Key aspect: Risk of users granting excessive access potentially leading to security breaches
RBAC (Role Based Access Control)
Assigns permissions based on a user’s role in an organization. Common in corporate environments. Streamlines access management
Rule Based Access Control
Access decisions are based on a set of rules defined by a system admin. Useful in environments requiring stringent access control, like securing network resources.
Key aspect: Rules can be based on various criteria, such as source/destination IP in firewalls
Attribute-Based Access Control (ABAC)
Uses policies that evaluate attributes of users, the environment, and resources. Effective in complex environments with diverse and dynamic user attributes.
Key aspect: Provides fine-grained control, allowing for more nuanced access decisions based on multiple factors (like access based on location, time, browser you use, etc)
SSO Importance
Reduced password fatigue
Centralized Authentication Control (Easier to enforce security policies)
Reduced IT workload (Simplified management of user accounts)
LDAP
Protocol for accessing and maintaining distributed directory information services, like user and group details, over a IP network
Federation
The process of linking and managing identities/credentials across different systems and organizational boundaries (SSO for multiple sites/apps/websites)
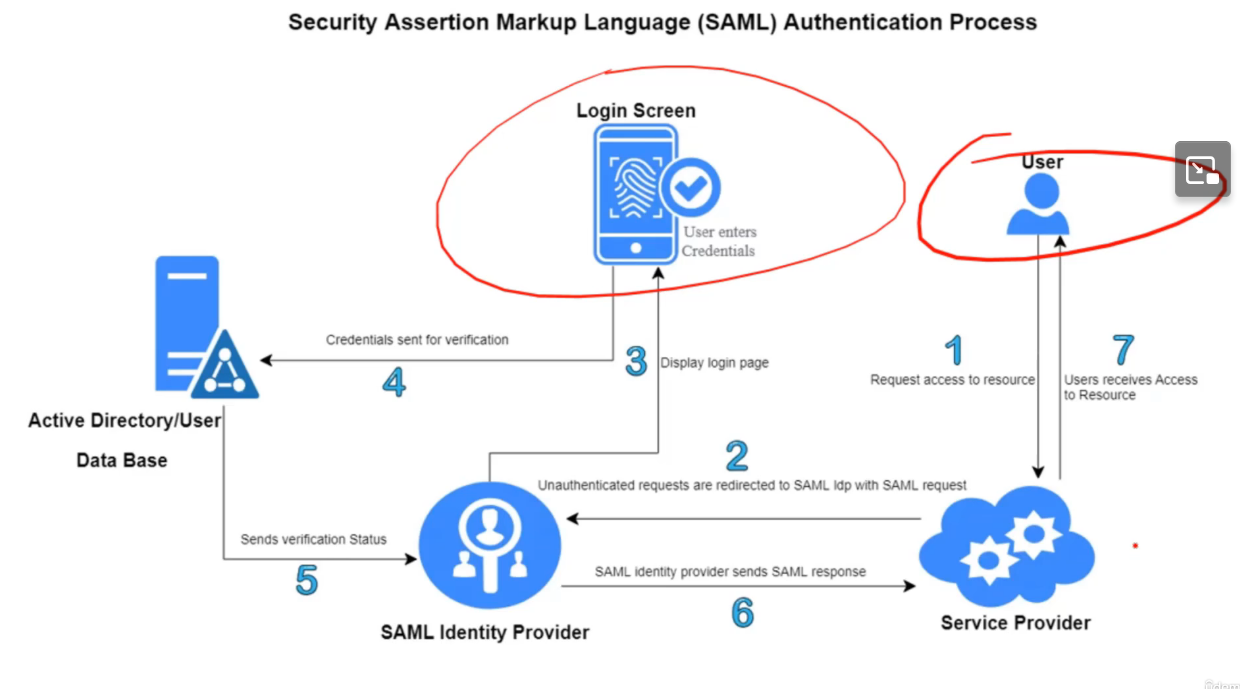
SAML
Security Assertion Markup Language, an open standard for exchanging authentication and authorization data between parties, specifically between an identity provider and a service provider. Very popular for federation
Usage: Widely used for SSO to allow users to log in to multiple applications with one set of credentials
Uses XML for data exchange. Particularly useful in enterprise-level SSO
Key Components:
Identity Providers (IdPs): Services that authenticate users and provide identity information to service providers. Examples: Okta, Microsoft Azure AD, and Google Identity. Attestation (formal verification that something is true) is done with the IdPs.
Service Providers: The applications or services that rely on information from the IdP to provide access to the user (like Best Buy, Facebook, New sites, etc)
OAuth
Open standard for access delegation. Used to grant websites or applications access to their information on other websites but without giving them the passwords. Commonly used for authorizing third-party applications to access a user’s data without exposing their credentials.
Is about authorization not authentication, and is used to grant limited access on behalf of the user
OpenID Conect
An identity layer on top of OAuth 2.0. Allows clients to verify the identity of the end-user based on authentication performed by an authorization server. Primarily used for authentication in modern web applications and mobile applications
Geofencing
Limiting access to resources (using GPS, RFID, WiFi, or cellular data) based on location, using either a mobile device or RFID tag for instance.
Deception and Disruption Technology
Refers to a set of cybersecurity strategies/tools designed to mislead, confuse, or disrupt the actions of malicious actors. used to create traps or illusions that protect real network assets by diverting attackers to decoy systems/files
Honeypot
A security mechanism setup to detect, deflect, or study hacking attempts. Acts as a decoy, imitating a real computer system, network, or information system, but is isolated and monitored. Provides valuable info about their techniques/intentions without endangering the actual network
Honeynet
A network of honeypots. Simulates a network environment to attract attackers. More complex, but can provide deeper insights
Honeyfiles
Decoy files placed with an network’s file systems. Appears legitimate and contains attractive data, but are monitored for access. Unauthorized access can alert security personnel
Honeytoken
Any decoy data or token inserted into a system. Could be a fake user account, database record, or any other type of digital bait that when interacted with indicates a compromise or unauthorized access
Data locality
Refers to the geographical location where data is stored, processed, and managed. Compliance with data locality regulations ensures that data handling practices meet regional legal requirements
PCI DSS
Payment Card Industry and Data Security Standards. Involves implementing encryption, access control, and regular monitoring to protect cardholder data from breaches and fraud
GDPR
General Data Protection Regulation. Comprehensive data protection regulation that governs the processing of personal data with the EU and beyond. Has strict requirements on organizations, including obtaining consent for data collection (like cookies), ensuring data accuracy, implementing security measures, and providing individuals with rights over their data
Way to reduce security risks from BYODs?
Segment them onto a separate network
ICS
Industrial Control Systems, general term for systems in industrial production (gas, electrical, water, etc). Ran on the SCADA protocol, distributed control systems (DCS) and other smaller control system configurations such as PLC (programmable logic controllers)
IoT Safety/Security
Password Management
Updates
Network segmentation
Ciphertext
The encrypted version of data that requires the cryptographic key to decrypt
Encryption of Data in Transit
Data be transferred over a network. Protects it from interception/tampering. Common protocols: HTTPS, SSL/TLS, and VPN
Goals of Cryptography
Confidentiality: Converting plaintext to ciphertext and back again with the decryption key
Integrity: Guaranteeing that data is protected from unauthorized or accidental changes. Cryptographic hash functions, for example, are used to produce a unique hash value for data, that can be used to verify the data hasn’t been altered
Authentication: Verifying the identity of a user, device, or entity in a communication process. For example, digital certificates are cryptographic techniques that can be used to confirm the identity of the parties involved in a communication. Passwords are another
Non-repudiation: Preventing an entity from denying their involvement in a transaction or activity. Digital signatures ensure that once a party signs a document or message, they can’t later claim they didn’t
Symmetric Encryption
Uses the same key for encryption and decryption (secret/private key cryptography)
Key sharing: Since the same key is used for both, it must be shared and kept secret between parties. Securely distributing and managing this key is crucial for symmetric encryption
Speed and Efficiency: Generally faster and more efficient than asymmetric, suitable for large amounts of data
Applications: Used in various applications like encrypting data in secure storage, data in transit, and encrypting files and databases
Security: Strength depends on the key length
Key Challenges:
Key Management
Scalability issues: For N users to communicate securely with each other, N(N-1)/2 unique key pairs are needed. This exponential growth can make key management impractical in large systems or networks
Key Storage and Protection: If a key is stolen or exposed, an attacker can decrypt any data encrypted with that key. Becomes more complex as the number of users increases
Lack of Non-repudiation: Can’t determine which specific user performed an encryption or decryption, which is a drawback in scenarios where proof of authorship is important
Asymmetric Encryption
AKA Public Key Cryptography. Uses pairs of keys: a public key, which can be shared by anyone, and a private key, which is known only to the owner
Process:
Encryption: Sender encrypts the data using the recipient’s public key. Once encrypted, the data can only be decrypted by the associated private key.
Decryption: Recipient uses their private key to decrypt the data.
Advantages:
Solves the key distribution problem
Provides a method for digital signatures, important for authentication and non-repudiation
Disadvantages:
More computationally intensive than symmetric encryption, making it slower for large amounts of data
Requires careful management of the private key, if the private key is compromised, so is the security of the system
PKI
Public Key Infrastructure. Framework used to create, manage, distribute, use, store, and revoke digital certificates and manage public key encryption. Purpose is to facilitate the secure electronic transfer of information for a range of network activities, like e-commerce, internet banking, and confidential email
Functioning of PKI:
Encryption/Decryption: Allows users to encrypt and decrypt data using public and private keys
Digital Signatures: Provides for creation and verification of digital signatures, ensuring the authenticity and integrity of the data
Certificate Management: The CA issues/revokes certificates as needed.
TLS (HTTPS/FTP/etc) utilizes PKI to function
Utilizes hybrid-cryptography
PKI (Cont)
X.509 Digital Certificate format.
CRL Distribution Point: An attribute telling if a certificate has been revoked
Certificate Types:
CA Certificate: Grants organization ability to be a certificate authority
End Entity Certificates:
Domain Validation (DV) is issued if control of a domain is proven
Extended Validation (EV) is a higher level assurance if the CA can verify that the applicant is a legitimate business
Wildcard Certificates:
Type of digital certificate used in SSL/TLS encryption, typically for securing websites
Versatile SSL certificate that allows multiple subdomains of a single domain to be secured with one certificate
Self Signed vs Third-Party
Third Party (CA Signed Certificates):
Issued and signed by a trusted CA. CA verifies the identity of the entity
Trust level: High. Central to most secure internet communications, like HTTPS
Widely used on the public internet for websites, email servers, and other public facing services where establishing trust with end users is crucial.
Typically involves a cost
Self Signed:
Created and signed by the entity it represents, rather than by a trusted third-party CA
Not inherently trusted, since there’s no independent verification
Often used in test environments, internal networks, or applications where the users can reliably verify the certificate’s authenticity without needing an external CA, or in situations where the overhead of obtaining a CA signed certificate isn’t justified
Zero cost