Fundamentals of Information Security - D340 WGU
1/271
Earn XP
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
272 Terms
Putting yourself at risk
Not updating to new security patches
Use of weak passwords
Downloading programs from the internet
Opening attachments from unknown senders
Using wireless connections w/out encryptions
Confidentiality
Refers to the ability to protect data from those who are not authorized to view it. You could implement this at many levels of the process.
Integrity
Is the ability to prevent people from changing your data in an unauthorized or undesirable manner. To maintain integrity, not only do you need to have the means to prevent unauthorized changes to your data, but you need the ability to reverse unwanted authorized changes.
Availability
Refers to the ability to access our data when we need it. You could lose availability due to the loss of power, operation/application issues, network issues, or the comprising of a system.
The Parkerian Hexad
This concept adds to the CIA Triad with three new categories, possession, utility and authenticity.
Possession
Refers to the physical disposition of the media on which the data is stored. This enables you to discuss your loss of data in its physical medium w/out involving other factors such as availability.
Authenticity
Allows you to say whether you've attributed the data in question to the proper owner or creator. You can enforce this by having digital signatures in emails.
Utility
Refers to how useful the data is to you, this concept can have various degrees/layers to it.
Types of Attacks
There are four main types of attacks in security. Interception, Interruption, Modification and Fabrication.
Interception
This attacks allows unauthorized users to access your data, applications or environments, and they primarily attacks against confidentiality.
Interruption
This attack makes your assets unusable or unavailable to you on a temporary or permanent basis. These attacks affect availability and integrity.
Modification
This attacks involves tampering with an asset. This will usually affect availability and integrity.
Fabrication
This attack involves generating data, processes, communications, or similar materials within a system. These attacks can also affect availability and integrity.
Threats
This is something that has the potential to cause harm to a system.
Vulnerabilities
These are weaknesses or “holes” that threats can exploit that can cause harm to system.
Risks
This is the likelihood that something bad will happen, to have a risk there has to be threat and a vulnerability that the threat could exploit.
Impact
This is another concept added by the NSA (National Security Agency). It takes into account the value of the asset being threatened and uses it to calculate risk.
Risk Management
This process has 5 steps, Identifying assets, Identifying threats, Assessing vulnerabilities, Assessing risks and Mitigating risks.
The 3 types of risk mitigation
They are physical, logical and administrative risk controls.
Physical mitigation
This protects the physical environment in which your systems sit, or where your data is stored.
Logical mitigation
Also known as “technical controls” this protects the systems, networks and environments that process, transmit ad store your data.
Administrative mitigation
These are controls based on rules, laws, guidelines, and other items that are “paper” in nature.
The 5 stages of incident response
These are stages of IR, Preparation, Detection and analysis, Containment, Eradication, Recovery and Post incident analysis.
Preparation
This involves creating policies and procedures that govern incident response and handling, conducting training and education for both incident handlers and those who are expecting incidents, and developing and maintaining documentation.
Detection and analysis
In this phase, you detect an issue, decide if it actually an incident, and respond to it accordingly.
Containment
This involves taking steps to ensure that the situation doesn’t cause any more damage than it already has or at least lessen any ongoing harm.
Eradication
This involves in the attempt to remove the effects of the issue from your environment. In the case of an affected system, you’ll isolate and cut off connection from the command and control center.
Recovery
This involves devices or data from a backup data, rebuilding systems or reloading systems, or rebuilding applications.
Post incident activity
Otherwise known as “post mortem”. This involves attempting to determine specifically what happened, why it happened and what you can do to keep it from happening again.
Defense in Depth
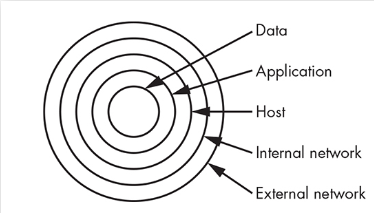
The triple “AAA”
AAA is an information security framework for controlling access to data and system resources, enforcing policies, and auditing actions.
Authentication
Verifies a user’s identification via the process of logging into a system.
Authorization (Access Control)
Determines what a user has the authority to do and have access to.
Accounting
Tracks and records user access and actions with system logs.
Least Privilege
A user, system, process, or application is only given the permissions necessary to complete its assigned tasks or functions and nothing more.
Identification
This is a simple assertion of who we are. This may include who we claim to be as people, who a system claims to be over the network, or who the originating party of an emails claims to be.
Who we claim to Be
This way we can identify ourselves by our full names, shortened versions of our nick names, nick names, account numbers, usernames, IDs, cards, fingerprints or DNA samples.
Identity Verification
This is a step beyond identification but it’s still a step short of authentication. When you have to show your drivers license, social security card, birth certificate. These things are considered forms of verification.
False Identification
This is also known as “falsification” where forms of fake IDs are used to access areas not meant for certain people, things or places.
Authentication
This is a set of methods used to establish whether a claim of identity is true.
Factors
There are several approaches to authentication, something you know, something you are, something you have, something you do and where you are. These are ideas of factors used daily.
Multifactor Authentication
This type of authentication refers to using two or more steps to verify your identity, IE an atm card and your pin would be considered so.
Mutual Authentication
This type of authentication requires both parties of any given transaction to authenticate each other, they’re usually software based. It is reliant on digital certificates.
Man in the Middle attack
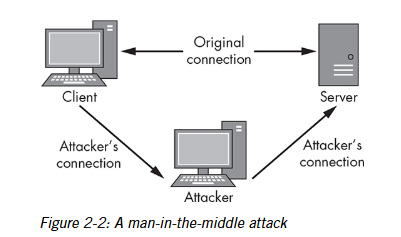
Passwords
This is familiar to the most of us who use computers regularly. When its combined with a username it will give access to systems on your computer, smartphone and other applications.
Biometrics
This is technology that uses the users characteristics unique to them to verify them to access to certain things, it can be a fingerprint, their face or even in the future voice…
Biometrics Factors
These are defined by seven factors: Universality, Uniqueness, Permanence, Collectability, Performance, Acceptability, and Circumvention.
Universality
This allows you to find your chosen biometric type in the majority of the people who are enrolling in the system.
Uniqueness
This allows you to measure how unique a biometric is amongst individuals.
Permanence
This allows the biometric to be tested on how well it resists change over time and advancing ages of individuals.
Collectability
This biometric measures how easy it is to acquire any given characteristic.
Performance
This measures how well a biometric does in the terms of speed, accuracy and error rate.
Acceptability
This biometric looks to see how the acceptance of characteristics rank against the users in the system.
Circumvention
This type of biometric looks to see how easily it can trick the system by using forms of falsified identifiers.
Measuring Performance chart
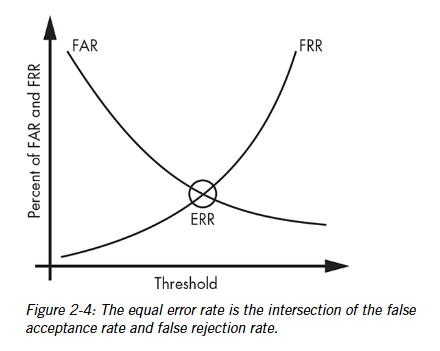
Hardware Tokens
These are devices that can be small or big that can be used to access secured information of any kind, some maybe a USB type “dongle” or a LCD screen that requires a pin/pass.
What are access controls?
Things that are used to provide access to resources.
Four types of access controls
There are four types of access levels, allowing, denying, limiting and revoking.
Allowing access
This gives the party access to certain resources.
Denying access
This is the opposite of granting access, it can be set up this way in various ways. Time based, area based and info based.
Limiting access
This is only allowing access to a certain extent, like only having a low level key that only opens one door while the master key opens all of them.
Revoking access
This is taking away access from a party after it was granted. If you fire an employee this is common to do after because they will have access to the resources.
Sandboxes
These are isolated environments containing a set of resources for a given purpose.
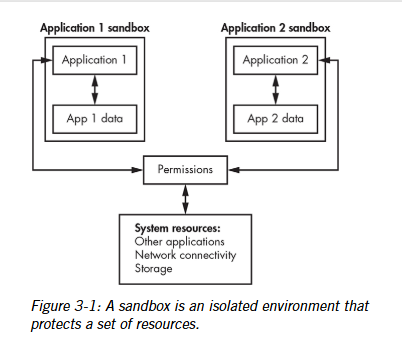
Implementing access controls
The two main ways to implement access controls are through, access control lists and capabilities.
Access control lists (ACLs) or “ackles”
These are lists that contain info about what kind of access certain parties have to any system.
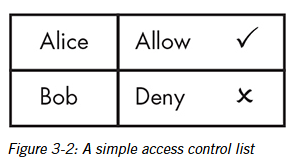
The 3 file system ACLs permissions
These are, read, write and execute.
Read permission
This allows the user to read the contents of a file or directory.
Write permission
This allows the user to write the contents of a file or directory.
Execute permission
This allows the user to execute the contents of a file if the file contains either a program or a script capable of running on the system in question.
Network ACLs
This filters access based on identifiers used for network transaction, such as internet protocols (IP) addresses, media access control (MAC) addresses and ports.
Blackholes
This happens when a user sees any traffic being sent to filtered destinations suddenly disappearing into thin air.
Socket
When you combine two attributes together to become more secure.
Media access control (MAC)
These are addresses that have unique identifiers hard coded into each network interface in a given system.
IP addresses
These are unique addresses assigned to each device on any network that uses the internet protocol for communication.
Port
These are numerical designation for one side of a connection between two devices, and we use them to identify the application to which traffic should be routed.
Confused deputy problem
This occurs when the software with access to a resource (the deputy) has a greater level of permission to access the resource than the user who is controlling the software.
Cross site request forgery (CSRF) attack
This attack misuses the authority of the browser on the user’s computer.
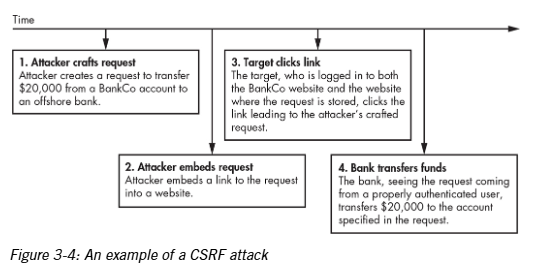
Clickjacking attack
This is also known as “user interface redressing” which takes advantage of some of pages rendering features that are available in newer web browsers.
Capabilities
These are permissions based on a user’s token, or key otherwise know as a capability.
Access control models
This is used to determine who should have access to what resources.
Most common access control models
These are discretionary, mandatory, rule based, role based, attribute based and multilevel access control.
Discretionary access control (DAC)
In this model, the owner of the resource determines who gets access to it and exactly what level of access they can have.
Mandatory access control (MAC)
In this model, the owner of the resource doesn’t get to decide who gets to access it. Instead, a separate group or individual gets to.
Rules based access control
This model allows access according to set of rules defined by the system administrator.
Role based access control (RBAC)
This model allows access based on the role of the individual being granted access.
Attribute based access control
This model allows access based on the specific attributes of a person, resource, or environment.
The principle of least privilege
This ideology states that you should give a party only the bare minimum level of access it needs to perform its functionality.
Multilevel access control
This model allows access to the combination of several access controls to be used together to protect information while access is controlled.
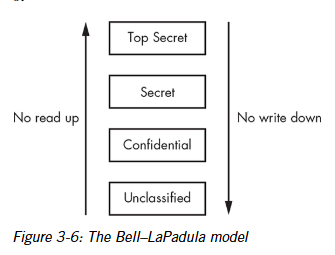
Bell lapadula model
This model combines the discretionary (DAC) and mandatory (MAC) access controls, primarily concerning the confidentiality of a resource. In other words, making sure unauthorized people can’t read it.
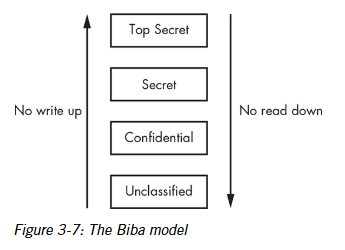
Biba model
This model is concerned with protecting the integrity of data, even at the expense of confidentiality. This means its more important to keep people from altering the data than from viewing it.
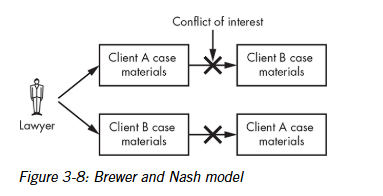
Brewer and nash model
This model is also known as the “chinese wall” which prevents the conflict of interest.
Three resources of brewer and nash
Objects: resources, such as the files of a single company.
Company groups: all objects of a single company.
Conflict classes: all groups of objects concerning competing parties.
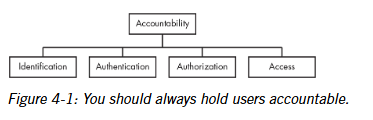
Accountability
This means making sure that a person is held responsible for their actions.
4 steps of reviewing accountability
Nonrepudiation
This renders someone unable to successfully deny that they have made a statement or take an action, generally because they have sufficient evidence that they did it.
deterrence
in accountability, this relates to help against misbehavior in a companies environments. This usually has penalties associated with the unaccepted behavior.
Intrusion detection and prevention
The two major ways you can use tools to monitor systems and alert you on strange activity, are intrusion detection systems (IDS) or intrusion prevention systems (IPS).
Intrusion detection systems (IDS)
This strictly monitors and alerts you on attacks and undesirable activity taking place.
Intrusion prevention systems
This works with data provided from the IDS to directly take action in the ongoing environment.
Admissibility of records
This can be considered a “chain of custody”, where you track information such as the location of the evidence over time, how exactly it passed from one person to another, and how it was protected while it was stored.