LAYER 5 (SESSION) PROTOCOLS
1/5
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
6 Terms
NFS
Network File System
Network File System, is a distributed file system protocol that allows users to access files and directories on a remote server as if they were local to their own computer. It enables shared access to files across a network, making it valuable for collaboration and data sharing.
Key Concepts and Features:
File Sharing:
NFS allows users to share files and directories between different machines on a network.
Transparency:
NFS makes remote files appear as if they are local, simplifying access for users.
Protocol:
NFS is a protocol that defines how clients and servers interact to share files.
Versions:
Different versions of NFS exist, with NFSv4 offering improvements over earlier versions.
pNFS:
NFSv4.1 introduces parallel NFS (pNFS), which allows clients to interact directly with data servers instead of just the metadata server, improving performance.
Configuration:
NFS servers and clients need to be configured to enable file sharing.
Security:
NFS supports various authentication methods and access control mechanisms.
Mounting:
NFS shares can be mounted on a client machine, making them accessible as local file systems.
Examples of NFS Usage:
Collaborative Work: Sharing files and directories among team members for projects.
Data Storage: Centralized storage of files and data across a network.
Virtual Machines: Allowing virtual machines to access shared storage.
Cloud Storage: NFS is implemented in cloud storage services like AWS EFS and Azure Files.
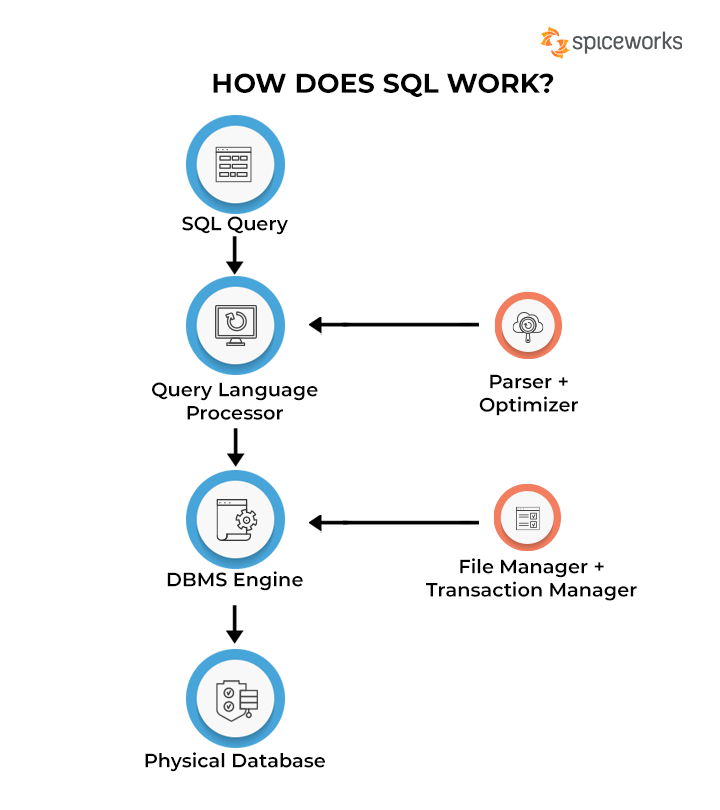
SQL
Structured Query Language
Structured query language (SQL) is a programming language for storing and processing information in a relational database. A relational database stores information in tabular form, with rows and columns representing different data attributes and the various relationships between the data values.
The intention of SQL (often pronounced sequel) is to store, retrieve, manage and manipulate data within a database management system.
RPC
A Remote Procedure Call (RPC) allows a computer program to call a procedure (function) that resides on a different computer across a network. Essentially, it makes a remote function call appear as a local function call to the client. This is achieved by abstracting away the complexities of network communication, including serialization, transport, and deserialization.
How it works:
Client Call: The client application initiates a call to a procedure as if it were local.
Marshalling: The client's stub (a piece of code that handles the network interaction) prepares the arguments for the procedure call by converting them into a format suitable for transmission over the network (marshaling).
Network Transmission: The marshalled data is sent to the server across the network.
Server Reception: The server's stub receives the data and unmarshals it back into the original format.
Procedure Execution: The server executes the procedure with the unmarshalled arguments.
Result Marshalling: If the procedure returns a result, the server stub marshals the result for transmission.
Network Return: The marshalled result is sent back to the client over the network.
Unmarshalling and Return: The client's stub unmarshals the result, and the return value is delivered to the client application.
PPTP
Point-to-Point Tunneling Protocol (PPTP) is a VPN protocol that establishes a secure tunnel for data transmission over a public network, like the internet. It's an older protocol, widely considered outdated and less secure than modern alternatives like OpenVPN, WireGuard, and IPSec.
Here's a more detailed explanation:
Function:
PPTP creates a virtual tunnel between two points (a client and a server) to allow data to be transmitted securely as if they were directly connected to a private network.
How it works:
PPTP uses TCP port 1723 to establish a connection and then creates a Generic Routing Encapsulation (GRE) tunnel, which is then used to encapsulate and transmit data packets.
Data Encapsulation and Encryption:
PPTP encapsulates PPP (Point-to-Point Protocol) frames and can encrypt the data using encryption methods like MPPE (Microsoft Point-to-Point Encryption).
Authentication:
PPTP uses various authentication methods, including passwords, to verify the identity of the client and server.
Outdated and Insecure:
PPTP is no longer considered secure due to vulnerabilities in its encryption algorithms and authentication protocols, making it susceptible to various cyberattacks.
Alternatives:
Modern alternatives like OpenVPN and IPSec offer stronger security, faster speeds, and more robust features.
SIP
The Session Initiation Protocol (SIP) is a signaling protocol used to initiate, manage, and terminate multimedia communication sessions, including voice, video, and messaging. It's widely used in VoIP (Voice over IP) and other multimedia communication applications.
Key aspects of SIP:
Signaling:
SIP is a signaling protocol, meaning it focuses on setting up the communication, not transmitting the actual data.
Multimedia:
SIP supports a wide range of multimedia formats, including voice, video, and messaging.
VoIP:
SIP is a fundamental protocol for VoIP systems, enabling voice calls over IP networks.
Scalability:
SIP is designed to handle large numbers of users and sessions.
Flexibility:
SIP is a flexible protocol that can be adapted to various network environments.
How it works:
SIP uses a request-response model similar to HTTP (Hypertext Transfer Protocol). When a user wants to initiate a call, a SIP request is sent to a SIP server, which then relays the request to the intended recipient. The recipient then responds to the request, either accepting or rejecting the call. Once the call is established, SIP is used to manage and maintain the session.
NetBIOS
NetBIOS (Network Basic Input/Output System) is an application programming interface (API) and a naming convention that allows applications on separate computers to communicate and access shared resources over a local area network (LAN). It essentially enables computers to communicate using names instead of IP addresses, making it easier for users to identify and connect to other devices on the network.
What NetBIOS Does:
Name Resolution:
.Opens in new tab
NetBIOS provides a way for applications to resolve network names to IP addresses. This is crucial for devices to find each other on a network and establish communication.
Session Management:
.Opens in new tab
It facilitates connection-oriented communication between devices, allowing applications to establish sessions for data exchange.
Datagram Service:
.Opens in new tab
NetBIOS also supports connectionless communication, allowing devices to send messages or data packets without establishing a dedicated connection.
How NetBIOS Works:
Names:
.Opens in new tab
NetBIOS names are 16-character strings, with the 16th character serving as a NetBIOS suffix that describes the type of service or name record.
Name Resolution:
.Opens in new tab
When an application needs to communicate with another computer, it uses the NetBIOS name. NetBIOS then resolves this name to an IP address using broadcasts or unicast queries.
Services:
.Opens in new tab
NetBIOS provides three main services: name service for name registration and resolution, datagram distribution service for connectionless communication, and session service for connection-oriented communication.
NetBIOS over TCP/IP:
Routability:
NetBIOS was originally designed for small, non-routable networks. However, NetBIOS over TCP/IP (NBT) extends the reach of NetBIOS to routers and wider networks by encapsulating NetBIOS packets within IP packets.
TCP/IP:
NBT uses the TCP/IP protocol stack to handle the underlying network communication, enabling NetBIOS applications to operate over routers and different network segments.
Ports:
NBT uses specific ports for different NetBIOS services, such as port 137 for name service, 138 for datagram service, and 139 for session service.