2.4 Application Attacks
1/11
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
12 Terms
Injection Attacks
Occur when an attacker adds malicious code into input sent to a server or client device.
Typically, applications should prevent these attacks through proper input validation, but some applications fail to check inputs adequately.
Various data types can be exploited in injection attacks, including HTML, SQL, XML, and LDAP
Buffer Overflow
Occurs when more data is added to a memory area than it can hold, causing the extra data to spill over into adjacent memory.
Developers need to implement bound checks to prevent this.
Are difficult to exploit because they require the attacker to find specific vulnerabilities and avoid crashing the system
if an attacker finds a reliable buffer overflow, it can become a powerful and persistent exploit against the application.
Replay Attack
Occurs when an attacker captures useful information from a network or victim’s computer and replays it to a server to gain unauthorized access.
Main challenge for the attacker is obtaining the raw network data, which can be done through methods like network taps, ARP poisoning, or malware.
Once the information is gathered, the attacker can replay it to impersonate the victim.
Not an on-path attack, but attackers often use an on-path attack to capture the necessary data before executing the replay.
Privilege Escalation
When an someone gains elevated rights or permissions beyond what is intended for their role.
Often achieved by exploiting a vulnerability.
Higher-level access grants more capabilities, including potentially administrator access.
Require urgent patching to prevent unauthorized access.
In some cases, attackers may not escalate to administrator access but instead perform horizontal privilege escalation, where they move from one user’s access rights to another user’s.
Mitigating Privilege Escalation
Patch any system vulnerabilities by keeping applications updated.
Use updated anti-virus and anti-malware software with current signatures helps detect and block known attacks.
Implementing Data Execution Prevention (DEP) limits the areas of memory where executables can run, potentially blocking certain exploits
Address Space Layout Randomization (ASLR) makes it harder for attackers to predict where data is stored in memory by randomizing the location each time an application runs
Privilege Elevation Example
The CVE-2023-29336 vulnerability, known as the Win32k Elevation of Privilege Vulnerability, was discovered in May 2023.
It affects the Win32k Kernel Driver on several versions of Windows, including Server 2008, 2008 R2, 2012, 2012 R2, 2016, and Windows 10.
Allows an attacker to escalate privileges to the SYSTEM level, granting them the highest possible access on the machine.
Cross-Site Requests
Are common and often legitimate.
When you visit a website like professormesser.com, your browser loads content from that site, but it might also retrieve additional resources from other servers, such as videos from YouTube or images from Instagram.
While it appears as though all content is coming from a single server, it is actually being loaded from different servers.
This is facilitated by HTML on the website, which directs your browser to make requests to various other servers.
Most of these requests are unauthenticated, meaning you don’t need to provide credentials for services like YouTube or Instagram to load content on the page.
The Client & The Server
When you visit a website, the code running is divided into two types: client-side and server-side
Client-side code, such as HTML and JavaScript, runs in your browser and is responsible for rendering the content you see, as it was originally designed by the website administrator.
On the other hand, server-side code runs on the web server and handles processes that are invisible to your browser.
For example, the server might process a user's request, generate HTML and PHP, or even perform background tasks like transferring funds or posting information on platforms like YouTube, without your browser being directly involved in those processes.
Cross-Site Request Forgery
After logging into a website, your browser is trusted by the site. An attacker can exploit this by tricking your browser into making requests on their behalf to a trusted server.
Sometimes referred to as a one-click attack or session writing.
This is abbreviated as XZF or CSRF.
We often refer to this as sea surf.
For example, if you're logged into Facebook, the attacker might craft code that causes your browser to post status updates to your account without your consent.
Many web applications defend against CSRF by using anti-forgery techniques, such as cryptographic tokens, which ensure that requests come from a legitimate user and not an attacker.
Cross-Site Request Forgery Example
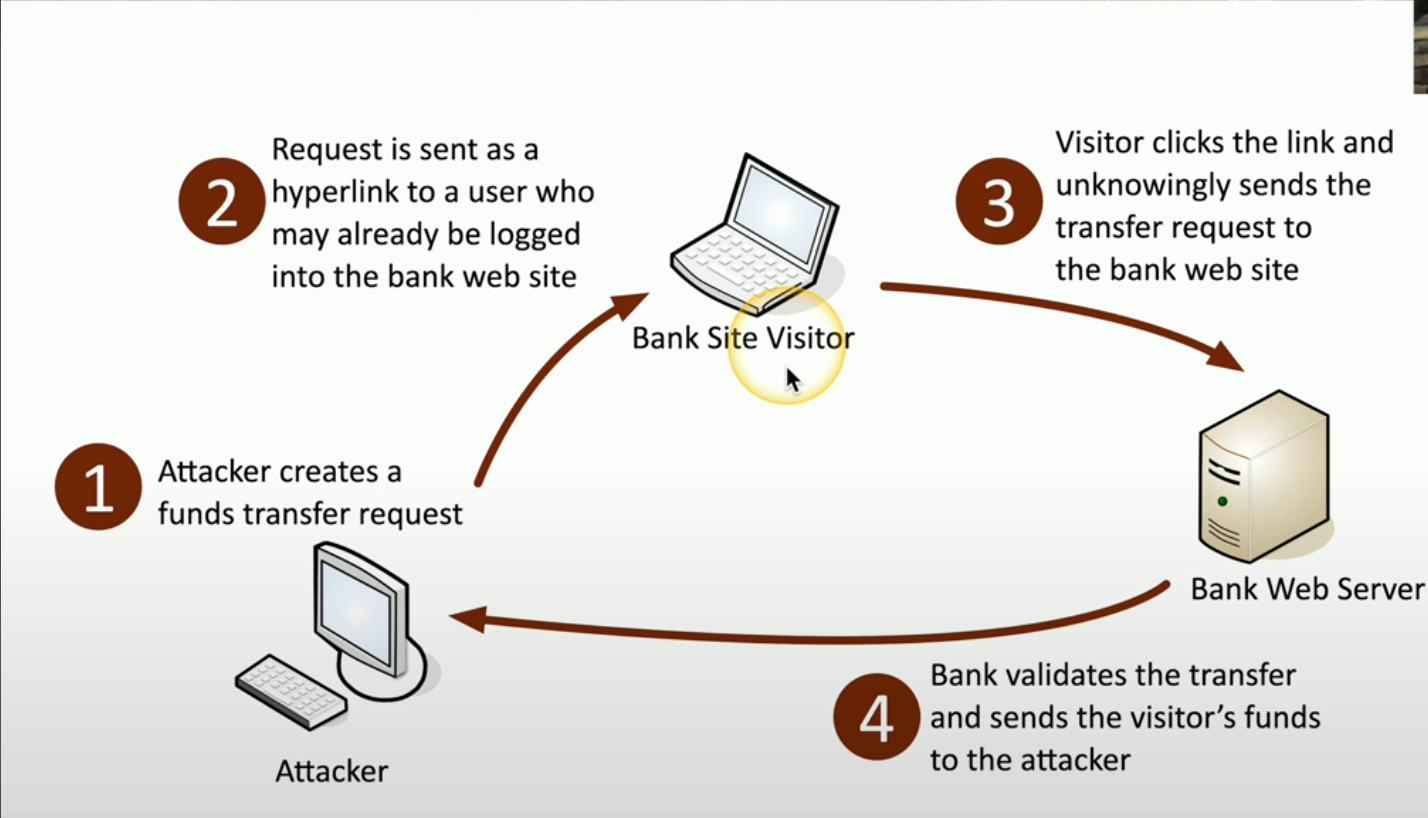
The victim is already authenticated on a website, such as a bank.
The first step is the attacker is going to create a funds transfer request, but it needs to get that request into the hands of the bank site visitor. They might send a hyperlink to a user to have them click on it.
If the victim is logged into the bank and they click one of those malicious links, there may be information sent to the web server that causes that victim’s account to transfer information and money to the attacker’s account.
Directory Traversal
Allows attackers to access files outside the website's designated directory, often exposing sensitive files on the server.
For instance, on a Windows server, directories like "Program Files" or "Windows" are normally off-limits to a web server.
If the server is misconfigured, an attacker may gain unauthorized access to these restricted directories.
A vulnerability that typically results from improper web server configuration, though it can also be caused by software vulnerabilities.
Directory Traversal Example
GET https://www.example.com/show.asp?view=../../Windows/system.ini HTTP/1.1 The
../../part in the URL indicates a directory traversal attempt, where..moves the request up one directory in the file system. IIf you see
../used in URLs, it could be a sign that the attacker is probing the server for directory traversal vulnerabilities.