Practice EExam C Performance-Based Questions
1/89
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
90 Terms
Refer to the following firewall rules:
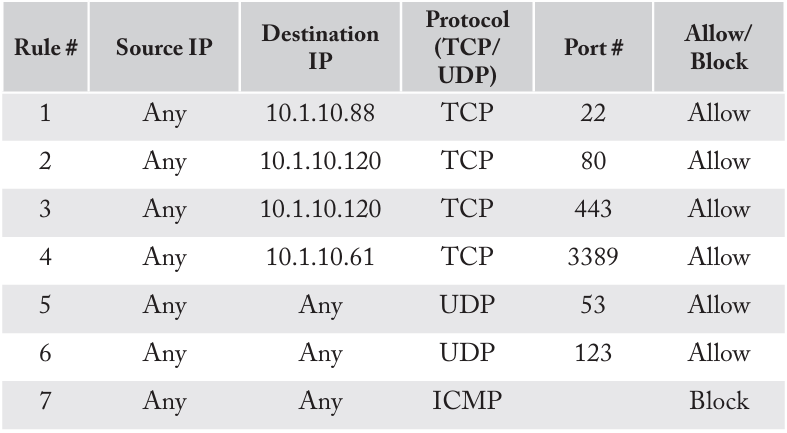
Use a secure terminal to connect to 10.1.10.88 = Allowed
Share the desktop on server 10.1.10.120 = Blocked
Synchronize the clock on a server at 10.1.10.17 = Allowed
View web pages on 10.1.10.120 = Allowed
Perform a DNS query from 10.1.10.88 to 9.9.9.9 = Blocked
Authenticate to an LDAP server at 10.1.10.61 = Blocked
Match the device to the description. Some device types will not be used.
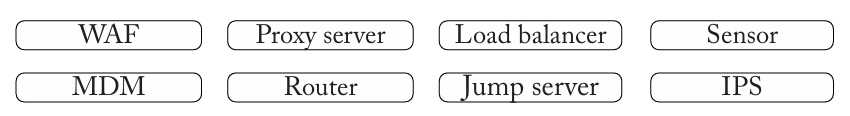
Block SQL injection over an Internet connection = IPS
Intercept all browser requests and cache the results = Proxy server
Forward packets between separate VLANs = Router
Configure a group of redundant web servers = Load balancer
Evaluate the input to a browser-based application = WAF
Match the attack type to the characteristic:
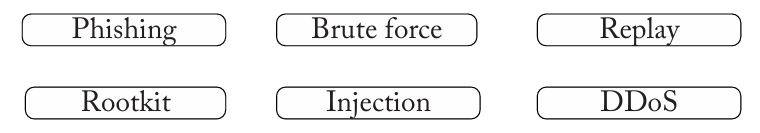
A list of passwords are attempted with a known username = Brute force
An email link redirects a user to a site that requests login credentials = Phishing
The malware is designed to remain hidden on a computer system = Rootkit
Permissions are circumvented by adding additional code as application input = Injection
Data is captured and retransmitted to a server = Replay
A website stops responding to normal requests = DDoS
Match the cryptography technology to the description:
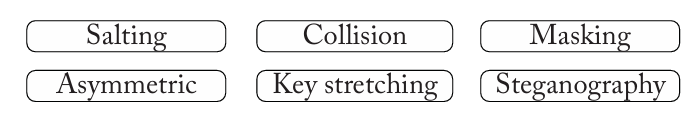
Different inputs create the same hash = Collision
Data is hidden within another media type = Steganography
Information is added to make a unique hash = Salting
Sensitive data is hidden from view = Masking
A different key is used for decryption than encryption = Asymmetric
Create a stronger key using multiple process = Key stretching
Add the most applicable security technologies to the following scenarios:
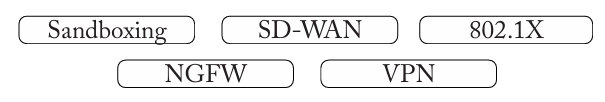
Users connecting to the network should use their corporate authentication credentials = 802.1X
A field service engineer uses their corporate laptop at coffee shops and hotels = VPN
Directly access cloud-based services from all corporate locations = SD-WAN
Software developers run a series of tests before deploying an application = Sandboxing
An administrator prevents employees from visiting known-malicious web sites = NGFW
A finance company is legally required to maintain seven years of tax records for all of their customers. Which of the following would be the BEST way to implement this requirement?
Create a separate daily backup archive for all applicable tax records

A system administrator is designing a data center for an insurance company’s new public cloud and would like to automatically rotate encryption keys on a regular basis. Which of the following would provide this functionality?
Key management system
A newly installed IPS is flagging a legitimate corporate application as malicious network traffic. Which of the following would be the BEST way to resolve this issue?
Tune the IPS alerts

A security administrator has identified an internally developed application which allows modification of SQL queries through the web-based front-end. Which of the following changes would resolve this vulnerability?
Validate all application input

A system administrator is implementing a fingerprint scanner to provide access to the data center. Which of the following authentication technologies would be associated with this access?
Something you are

The IT department of a transportation company maintains an on-site inventory of chassis-based network switch interface cards. If a failure occurs, the on-site technician can replace the interface card and have the system running again in sixty minutes. Which of the following BEST describes this recovery metric?
MTTR
A company maintains a server farm in a large data center. T hese servers are used internally and are not accessible from outside of the data center. The security team has discovered a group of servers was breached before the latest security patches were applied. Breach attempts were not logged on any other servers. Which of these threat actors would be MOST likely involved in this breach?
Insider

An organization has received a vulnerability scan report of their Internet-facing web servers. The report shows the servers have multiple Sun Java Runtime Environment ( JRE) vulnerabilities, but the server administrator has verified that JRE is not installed. Which of the following would be the BEST way to handle this report?
Ignore the JRE vulnerability alert

A user downloaded and installed a utility for compressing and decompressing files. Immediately after installing the utility, the user’s overall workstation performance degraded and it now takes twice as much time to perform any tasks on the computer. Which of the following is the BEST description of this malware infection?
Trojan

Which of the following is the process for replacing sensitive data with a non-sensitive and functional placeholder?
Tokenization

A security administrator has installed a new firewall to protect a web server VLAN. The application owner requires all web server sessions communicate over an encrypted channel. Which of these rules should the security administrator include in the firewall rulebase?
Source: ANY, Destination: ANY, Protocol: TCP, Port: 443, Allow
Which of these would be used to provide multi-factor authentication?
Smart card with picture ID

A company's network team has been asked to build an IPsec tunnel to a new business partner. Which of the following security risks would be the MOST important to consider?
Supply chain attack

A company's human resources team maintains a list of all employees participating in the corporate savings plan. A third-party financial company uses this information to manage stock investments for the employees. Which of the following would describe this financial company?
Processor

A technology company is manufacturing a military grade radar tracking system that can instantly identify any nearby unmanned aerial vehicles (UAVs). The UAV detector must be able to instantly identify and react to a vehicle without delay. Which of the following would BEST describe this tracking system?
RTOS

An administrator is writing a script to convert an email message to a help desk ticket and assign the ticket to the correct department. Which of the following should be administrator use to complete this script?
Orchestration

A security administrator would like a report showing how many attackers are attempting to use a known vulnerability to gain access to a corporate web server. Which of the following should be used to gather this information?
IPS log

During a ransomware outbreak, an organization was forced to rebuild database servers from known good backup systems. In which of the following incident response phases were these database servers brought back online?
Recovery

A security administrator is installing a web server with a newly built operating system. Which of the following would be the best way to harden this OS?
Remove unnecessary software

A network IPS has created this log entry:
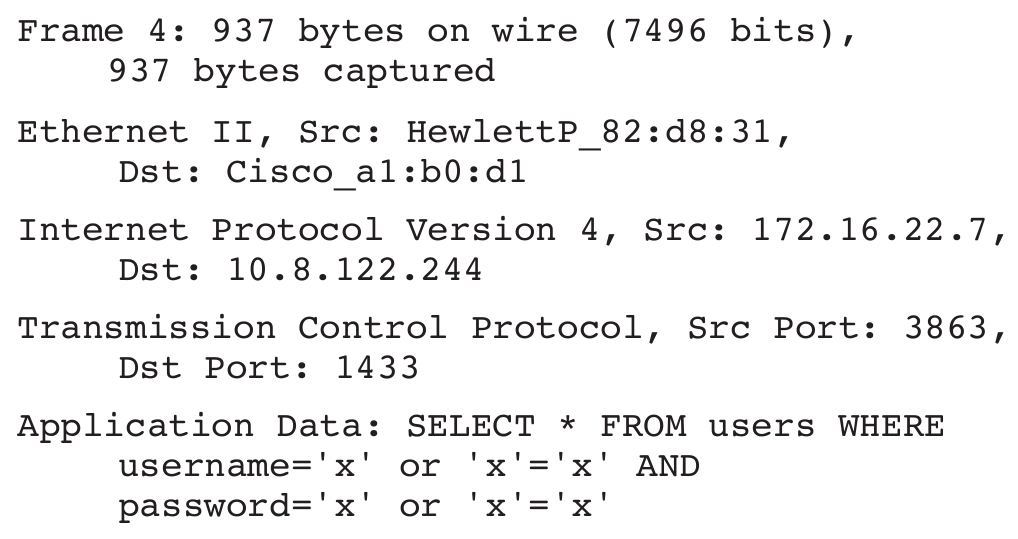
SQL injection

An incident response team would like to validate their disaster recovery plans without making any changes to the infrastructure. Which of the following would be the best course of action?
Tabletop exercise

A system administrator has installed a new firewall between the corporate user network and the data center network. When the firewall is turned on with the default settings, users complain that the application in the data center is no longer working. Which of the following would be the BEST way to correct this application issue?
Create firewall rules that match the application traffic flow

Which of these would be used to provide HA for a web-based database application?
UPS

Each year, a certain number of laptops are lost or stolen and must be replaced by the company. Which of the following would describe the total cost the company spends each year on laptop replacements?
ALE

A network administrator is viewing a log file from a web server:
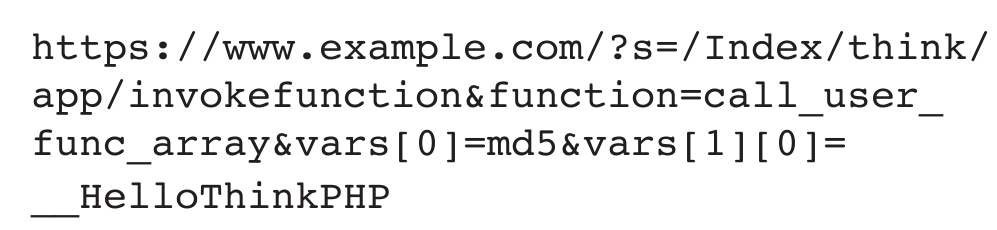
Input validation

Sam would like to send an email to Jack and have Jack verify that Sam was the sender of the email. Which of these should Sam use to provide this verification?
Digitally sign with Sam’s private key

The contract of a long-term temporary employee is ending. Which of these would be the MOST important part of the off-boarding process?
Archive the decryption keys associated with the user account

A cybersecurity analyst has been asked to respond to a denial of service attack against a web server, and the analyst has collected the log files and data from the server. Which of the following would allow a future analyst to verify the data as original and unaltered?
Data hashing

A security administrator is reviewing authentication logs. T he logs show a large number of accounts with at least three failed authentication attempts during the previous week. Which of the following would BEST explain this report data?
Spraying

A security administrator has been asked to block all browsing to casino gaming websites. Which of the following would be the BEST way to implement this requirement?
Add a content filter rule

A company is experiencing downtime and outages when application patches and updates are deployed during the week. Which of the following would help to resolve these issues?
Change management procedures

A company is implementing a series of steps to follow when responding to a security event. Which of the following would provide this set of processes and procedures?
Playbook

A transportation company maintains a scheduling application and a database in a virtualized cloud-based environment. Which of the following would be the BEST way to backup these services?
Snapshot
In an environment using discretionary access controls, which of these would control the rights and permissions associated with a file or directory?
Owner

A security administrator has installed a network-based DLP solution to determine if file transfers contain PII. Which of the following describes the data during the file transfer?
In-transit

A medical imaging company would like to connect all remote locations together with high speed network links. The network connections must maintain high throughput rates and must always be available during working hours. In which of the following should these requirements be enforced with the network provider?
Service level agreement

A company is implementing a security awareness program for their user community. Which of the following should be included for additional user guidance and training
Information on proper password management

A security administrator is preparing a phishing email as part of a periodic employee security awareness campaign. T he email is spoofed to appear as an unknown third party and asks employees to immediately click a link or their state licensing will be revoked. Which of the following should be the expected response from the users?
Report the suspicious link to the help desk

A security administrator would like to minimize the number of certificate status checks made by web site clients to the certificate authority. Which of the following would be the BEST option for this requirement?
OCSP stapling
A company is concerned their EDR solution will not be able to stop more advanced ransomware variants. Technicians have created a backup and restore utility to get most systems up and running less than an hour after an attack. What type of security control is associated with this restore process?
Compensating

To upgrade an internal application, the development team provides the operations team with instructions for backing up, patching the application, and reverting the patch if needed. The operations team schedules a date for the upgrade, informs the business divisions, and tests the upgrade process after completion. Which of the following describes this process?
Change management

A company is implementing a public file-storage and cloud-based sharing service, and would like users to authenticate with an existing account on a trusted third-party web site. Which of the following should the company implement?
Federation

A system administrator is viewing this output from Microsoft’s System File Checker:
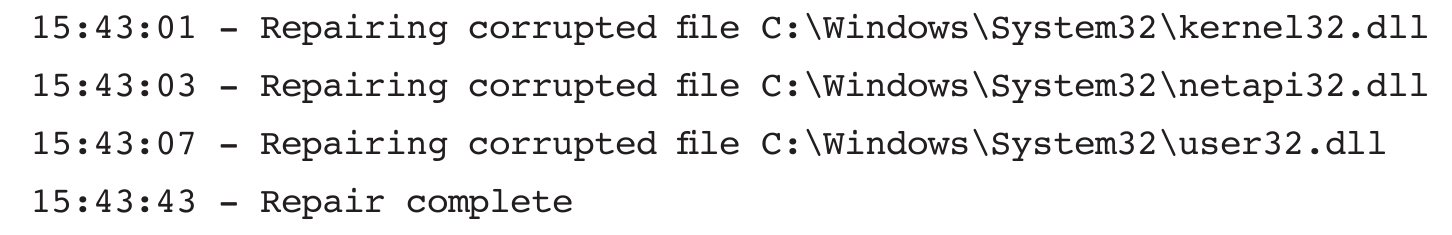
Which of the following malware types is the MOST likely cause of this output?
Rootkit

What type of vulnerability would be associated with this log information?

Directory traversal

A developer has created an application to store password information in a database. Which of the following BEST describes a way of protecting these credentials by adding random data to the password?
Salting

Which of the following processes provides ongoing building and testing of newly written code?
Continuous integration

Which of the following BEST describes a responsibility matrix?
A visual summary of cloud provider accountability

A security administrator is implementing an authentication system for the company. Which of the following would be the best choice for validating login credentials for all usernames and passwords in the authentication system?
LDAP

A technician is reviewing this information from an IPS log:
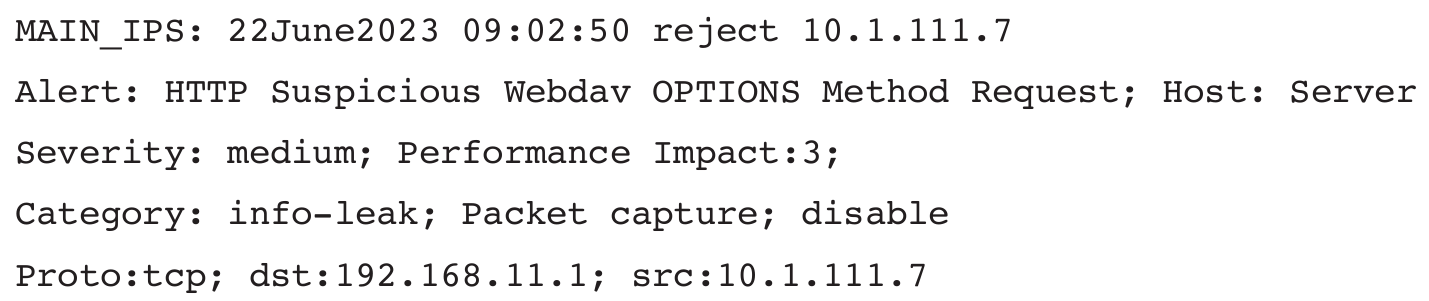
Which of the following can be associated with this log information? (Select TWO)
The source of the attack is 10.1.111.7 & The attacker sent an unusual HTTP packet to trigger the IPS

A company has contracted with a third-party to provide penetration testing services. The service includes a port scan of each externally-facing device. This is an example of:
Active reconnaissance

An access point in a corporate headquarters office has the following configuration:
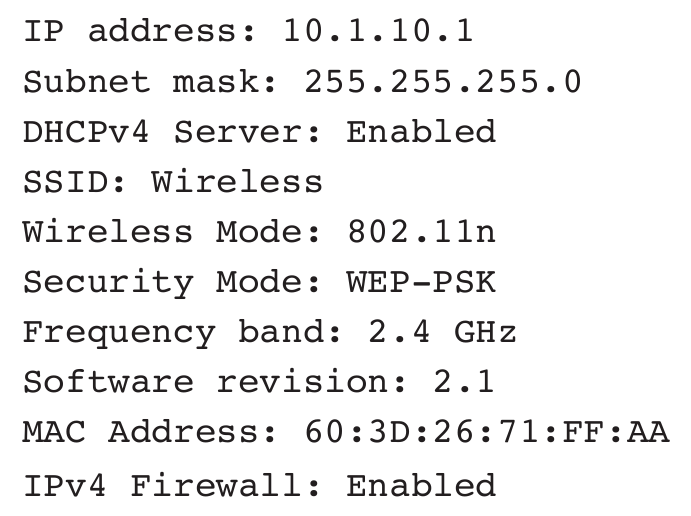
following configuration:
Which of the following would apply to this configuration?
Weak encryption

An attacker has gained access to an application through the use of packet captures. Which of the following would be MOST likely used by the attacker?
Replay

A company is receiving complaints of slowness and disconnections to their Internet-facing web server. A network administrator monitors the Internet link and f inds excessive bandwidth utilization from thousands of different IP addresses. Which of the following would be the MOST likely reason for these performance issues?
DDoS

A company has created an itemized list of tasks to be completed by a third-party service provider. After the services are complete, this document will be used to validate the completion of the services. Which of the following would describe this agreement type?
SOW

A company is deploying a series of internal applications to different cloud providers. Which of the following connection types should be deployed for this configuration?
SD-WAN

A company is updating components within the control plane of their zero-trust implementation. Which of the following would be part of this update?
Policy engine

Which of the following malware types would cause a workstation to participate in a DDoS?
Bot

Which of these are used to force the preservation of data for later use in court?
Legal hold

A company would like to automatically monitor and report on any movement occurring in an open field at the data center. Which of the following would be the BEST choice for this task?
Microwave sensor
A company is releasing a new product, and part of the release includes the installation of load balancers to the public web site. Which of the following would best describe this process?
Capacity planning

A system administrator would like to prove an email message was sent by a specific person. Which of the following describes the verification of this message source?
Non-repudiation

A security administrator has created a policy to alert if a user modifies the hosts file on their system. Which of the following behaviors does this policy address?
Risky

A company has identified a web server data breach resulting in the theft of financial records from 150 million customers. A security update to the company’s web server software was available for two months prior to the breach. Which of the following would have prevented this breach from occurring?
Patch management

During the onboarding process, the IT department requires a list of software applications associated with the new employee's job functions. Which of the following would describe the use of this information?
Access control configuration

A system administrator has identified an unexpected username on a database server, and the user has been transferring database files to an external server over the company’s Internet connection. The administrator then performed these tasks:
Physically disconnected the Ethernet cable on the database server
Disabled the unknown account
Configured a firewall rule to prevent file transfers from the server
Containment

Which of the following would be the MOST effective use of asymmetric encryption?
Create a shared session key

Each salesperson in a company receives a laptop with applications and data to support their sales efforts. The IT manager would like to prevent third-parties from gaining access to this information if the laptop is stolen. Which of the following would be the BEST way to protect this data?
Full disk encryption

A security administrator has compiled a list of all information stored and managed by an organization. Which of the following would best describe this list?
Data inventory

A security administrator would like to monitor all outbound Internet connections for malicious software. Which of the following would provide this functionality?
Forward proxy

What type of security control would be associated with corporate security policies?
Managerial

Which of the following would be the MOST significant security concern when protecting against organized crime?
Maintain reliable backup data

An application team has been provided with a hardened version of Linux to use with a new application installation, and this includes installing a web service and the application code on the server. Which of the following would BEST protect the application from attacks?
Implement a secure configuration of the web service

A system administrator has configured MAC filtering on their corporate access point, but access logs show unauthorized users accessing the network. Which of the following should the administrator configure to prevent future unauthorized use?
Enable WPA3 encryption

A system administrator has been tasked with performing an application upgrade, but the upgrade has been delayed due to a different scheduled installation of an outdated device driver. Which of the following issues would best describe this change management delay?
Dependency

During an initial network connection, a supplicant communicates to an authenticator, which then sends an authentication request to an Active Directory database. Which of the following would BEST describe this authentication technology?
802.1X
A security researcher has been notified of a potential hardware vulnerability. Which of the following should the researcher evaluate as a potential security issue?
Firmware versions

Visitors to a corporate data center must enter through the main doors of the building. Which of the following security controls would be the BEST choice to successfully guide people to the front door?
Bollards & Fencing

A company's employees are required to authenticate each time a file share, printer, or SAN imaging system is accessed. Which of the following should be used to minimize the number of employee authentication requests?
SSO

A company has recently moved from one accounting system to another, and the new system includes integration with many other divisions of the organization. Which of the following would ensure that the correct access has been provided to the proper employees in each division?
Internal self-assessment

An attacker has circumvented a web-based application to send commands directly to a database. Which of the following would describe this attack type?
SQL injection

A group of business partners is using blockchain technology to monitor and track raw materials and parts as they are transferred between companies. Where would a partner find these tracking details?
Ledger

A network technician at a bank has noticed a significant decrease in traffic to the bank's public website. After additional investigation, the technician finds that users are being directed to a web site which looks similar to the bank's site but is not under the bank's control. Flushing the local DNS cache and changing the DNS entry does not have any effect. Which of the following has most likely occurred?
Domain hijacking

A company runs two separate applications in their data center. The security administrator has been tasked with preventing all communication between these applications. Which of the following would be the BEST way to implement this security requirement?
Air gap

A receptionist at a manufacturing company recently received an email from the CEO asking for a copy of the internal corporate employee directory. It was later determined that the email address was not sent from the CEO and the domain associated with the email address was not a corporate domain name. What type of training could help identify this type of attack in the future?
Recognizing social engineering

Which of the following deployment models would a company follow if they require individuals to use their personal phones for work purposes?
BYOD
