Cybersecurity Module 12
1/83
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
84 Terms
vulnerability management
Also called “infrastructure risk visibility and assurance,” it is an ongoing examination of the organization’s security
seeks to answer such questions as “Where are we exposed?”, “What should we prioritize?”, “Are we reducing our exposure over time?”, and even “How do we compare with our peers?”
vulnerability scan
is an ongoing automated process used to identify weaknesses and monitor information security progress. It is an assessment that is designed to be a cyclical and continual scanning and monitoring process
serves as a system/process audit on both the devices that are used and the processes to protect those devices.
open-source libraries
A “library” is a collection of precompiled and reusable files, functions, scripts, routines, and similar resources that are used by computer programmers for software development.
“Open source” initially referred to software for which the source code was “open” for anyone to examine, but over time it was applied to anything that could be freely used without restrictions
package monitoring tools
which continuously analyze apps for vulnerabilities. Some application _________ even have a dashboard that provides an at-a-glance view of the applications’ current security features, as well as a more detailed audit view to show where security configurations should be modified.
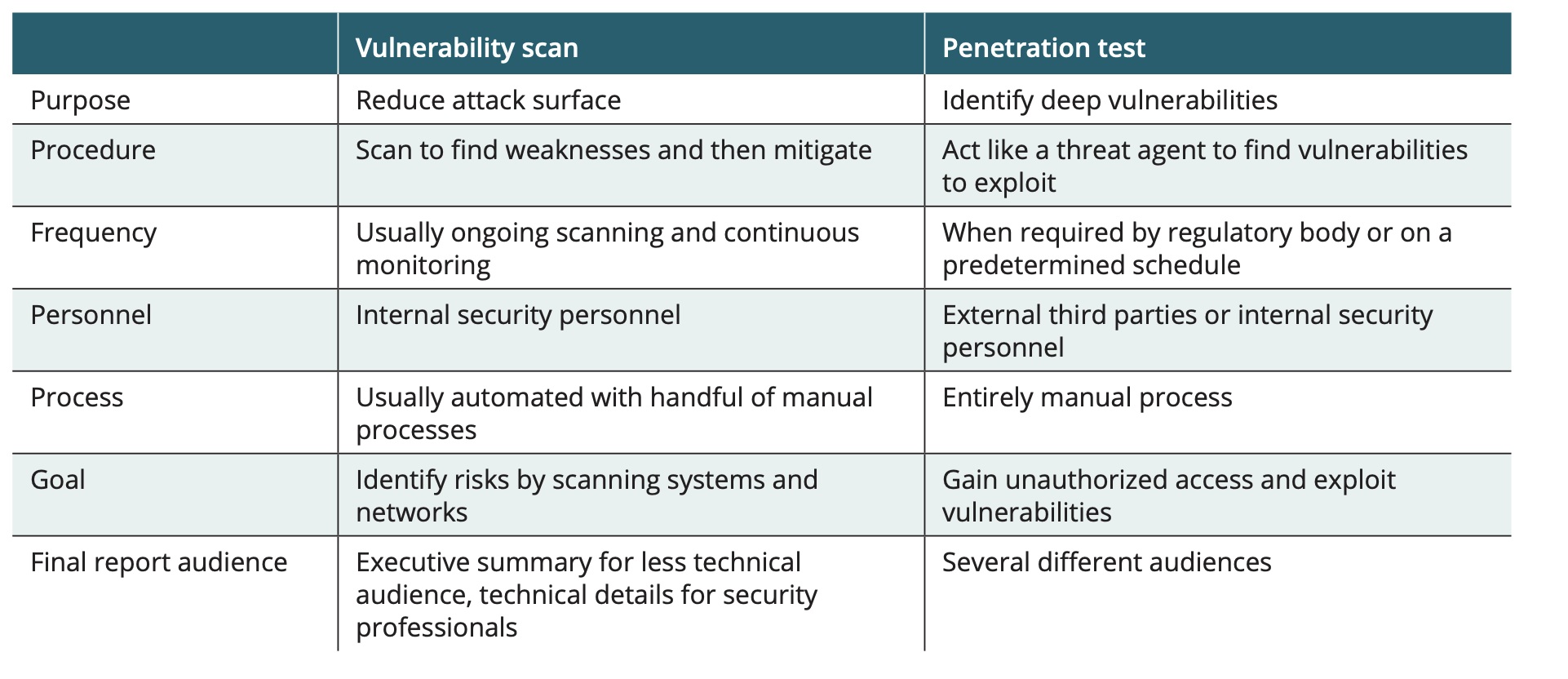
Vulnerability Scan Challenges
Volume of scan data. Vulnerability scans can produce large amounts of data that must be analyzed.
Identification of vulnerabilities. A vulnerability scanner must be able to perform two tasks: (1) locate and identify devices, software, open ports, and other system information and (2) correlate that information with known vulnerabilities from one or more repositories of vulnerabilities. Not every identified system element may be an actual vulnerability and, if a system element is not part of the vulnerability repository, then a weakness may be overlooked.
Technical limitations. Vulnerability scanning that is configured to be aggressive or intrusive can impact performance or even stability of the systems being scanned. Scanning could also cause bandwidth issues on networks. These technical limitations of a vulnerability scan could have an effect on the timeliness and usefulness of the scan.
Remediations. Due to several factors, such as a high cost to remediate or a very low risk of exploitation, not all identified vulnerabilities may be addressed. The process for making these determinations can often be challenging and highly debated.
Threat intelligence
is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors. ________ enables organizations to make faster, more informed data-based security decisions. This changes behavior from being reactive to proactive.
three primary sources of threat intelligence
proprietary sources, information-sharing organizations, and open-source intelligence.
proprietary
Some threat intelligence data is owned by an entity and is not available to outsiders. These entities can be the enterprise itself or an outside third party
bug bounty program or a responsible disclosure program
A common practice of large enterprises is to pay security researchers who uncover security bugs in their products and then privately report the bugs so that they can be patched before threat actors find them
Organizations can use the data gathered from their _________ as input into the vulnerability scanner to search for these weaknesses in the organization’s defenses
clear web
which includes ordinary websites (social media, ecommerce, news, and similar sites) that most users access regularly and can be located by a search engine;
deep web
which are exclusive and protected websites (such as corporate email, material behind a digital paywall, and cloud hosting services) that are hidden from a search engine and cannot be accessed without valid credentials;
dark web.
is like the deep web in that it is beyond the reach of a normal search engine, but it is the domain of threat actors. Using special software such as Tor or I2P (Invisible Internet Project), it masks the user’s identity to allow for malicious activity such as selling drugs and stolen personal information and buying and selling malicious software used for attacks
third-party sources
As an alternative, proprietary vulnerability scanners (as opposed to free or open-source scanners) typically offer their own threat intelligence as a paid subscription service.
The threat intelligence data from these sources are based on the information they collect from their own customers and the work of their threat research teams.
threat feeds
These teams are tasked with mapping different types of attacks and the latest threats, suspicious behaviors, vulnerabilities, and exploits they uncover across the entire threat landscape
These are then regularly published and distributed to their customers as direct ________ that serve as input into the scanning software to be used in comparison with the enterprise’s security defenses.
Information sharing organizations
gather, collate, analyze, and then distribute threat intelligence. The sources of their information are often from similar organizations that have gathered their own threat intelligence information.
Cyber Information Sharing and Collaboration Program (CISCP)
“enables actionable, relevant, and timely unclassified information exchange through trusted public-private partnerships across all critical infrastructure sectors.” With the DHS serving as the coordinator, the ____ enables its members (called “partners”) to not only share threat and vulnerability information but also take advantage of the DHS’s cyber resources.
CISCP Services
Analyst-to-analyst technical exchanges. Partners can share and receive information on threat actor tactics, techniques, and procedures (TTPs) and emerging trends.
CISCP analytical products. A portal can be accessed through which partners can receive analysis of products and threats.
Cross-industry orchestration. Partners can share lessons learned and their expertise with peers across common sectors.
Digital malware analysis. Suspected malware can be submitted to be analyzed and then used to generate malware analysis reports to mitigate threats and attack vectors
Automated Indicator Sharing (AIS)
enables the exchange of cyber threat indicators between parties through computer-to-computer communication, not email communication. Threat indicators such as malicious IP addresses or the sender address of a phishing email can be quickly distributed to enable others to repel these attacks.
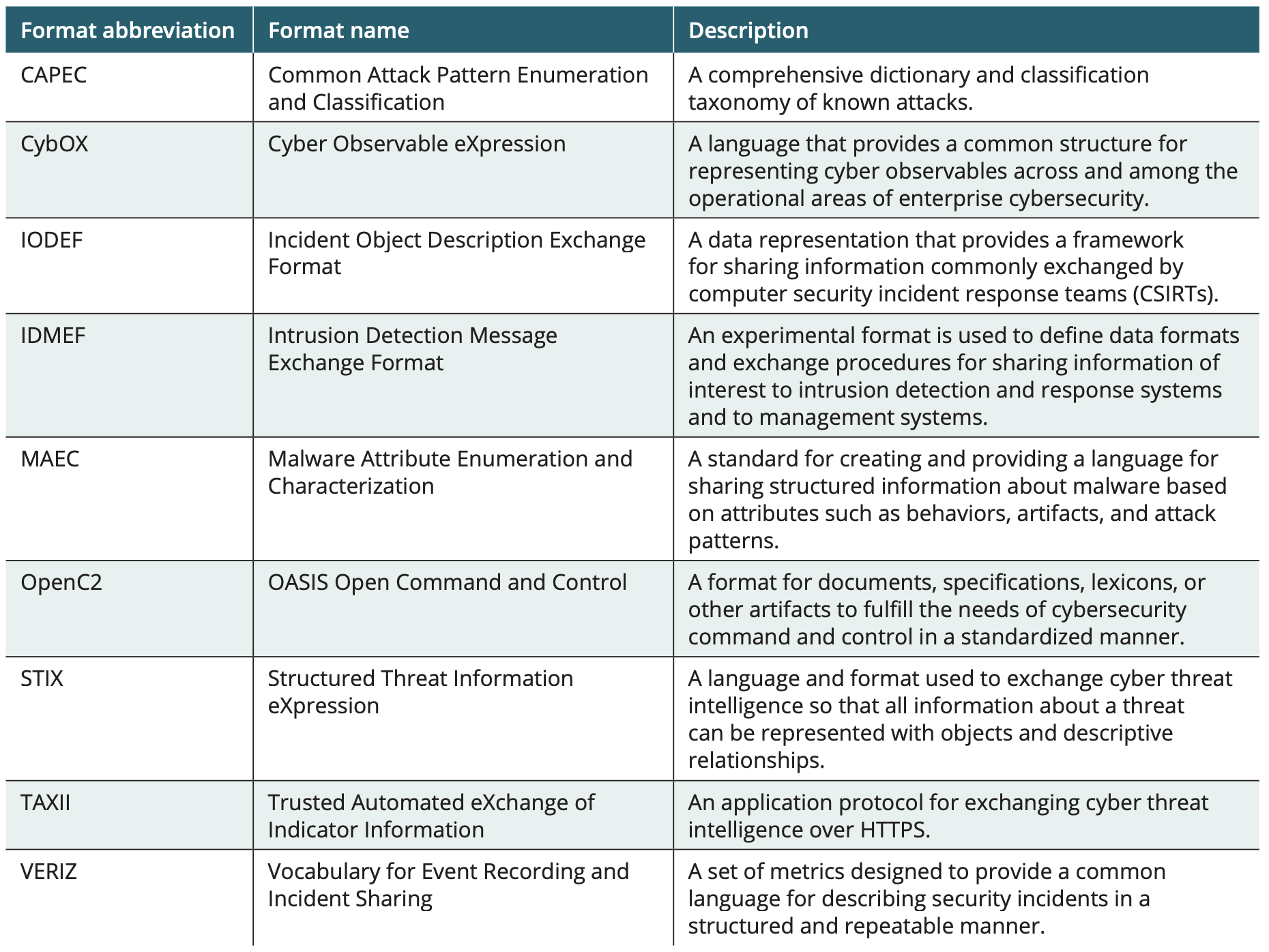
Structured Threat Information Expression (STIX)
is a language and format used to exchange cyber threat intelligence. All information about a threat can be represented with objects and descriptive relationships.
_______ information can be visually represented for a security analyst to view or can be stored in a lightweight format to be used by a computer
Trusted Automated Exchange of Intelligence Information (TAXII)
is an application protocol for exchanging cyber threat intelligence over Hypertext Transfer Protocol Secure (HTTPS). ________ defines an application protocol interface (API) and a set of requirements for _______ clients and servers
Standardized threat intelligence sharing formats
Open-Source Intelligence (OSINT)
is threat intelligence data that has been legally gathered from free and public sources. While in practice this usually means information found on the Internet, any public information falls into the category of ______.threat maps
threat maps
that illustrate cyber threats overlaid on a diagrammatic representation of a geographical area
help in visualizing attacks and provide a limited amount of context of the source and the target countries, the attack types, and historical and near real-time data about threats.
Assigning Data Value (1st step scanning)
Determining the value of data can be aided by first categorizing data into distinct classifications and then protecting these classifications accordingly. Instead of grouping data into categories such as customer data, financial data, and human resources data—which may have varying levels of importance and thus need different levels of control—it is far more beneficial to use data classifications to group like data that needs similar protections. These classifications include confidential, private, sensitive, critical, public, and restricted.
different data types include regulated, intellectual property, trade secret, and enterprise information. Once data has been properly identified, then its value can be determined and the type and frequency of a vulnerability scan can be calculated.
Identifying Data Locations
This ensures that specific devices containing high-value data can be scanned more frequentlyTypes of vulnerability scans over assets
Types of vulnerability scans over assets
Network - Can identify possible network security attacks and vulnerable systems on wired networks
Endpoint - Can locate and identify vulnerabilities in servers, workstations, or other network endpoints and provide visibility into the configuration settings and patch history of the endpoints
Wireless network - Can identify rogue access points and validate that the wireless network is secure
Database - May identify the weak points in a database
Applications - Web applications and other software assets can be scanned in order to detect known software vulnerabilities and erroneous configurations
Active versus Passive Scanning (3rd step scanning)
Extracting this data is called enumeration and is intended to build a picture of the endpoint and network (mapping)
Active scanning sends test traffic transmissions into the network and monitors the responses of the endpoints.
Passive scanning, on the other hand, does not send any transmissions but instead only listens for normal traffic to learn the needed information.
Advantages of Active Scanning
A primary advantage of conducting active scanning over passive scanning is that active scanning can accelerate the collection of the data; it is not necessary to wait for normal network traffic to or from each asset to generate a complete profile of information. In addition, not all parts of a network may always be available, which can limit the ability to passively monitor traffic.
Disadvantages of Active Scanning
● Smaller networks can become overloaded with high volumes of test traffic.
● Sending test traffic increases the risk of the endpoints malfunctioning if incompatible queries are sent.
● Some devices such as Internet of Things (IoT) devices may not be able to perform their normal tasks while receiving and returning test traffic and could become overloaded.
● Many IoT devices are proprietary and may react differently to test traffic.
internal vulnerability scan
is performed from the vantage point inside the internal network; that is, it is launched and then conducted from inside the corporate network. An ________ typically has the primary benefit of identifying at-risk systems
external vulnerability scan
is performed from the vantage point outside the network. It targets specific IP addresses that are within the network to identify vulnerabilities. An ________ can also detect open ports and protocols.
When should it be scanned? (4th step scanning)
The optimum frequency for vulnerability scanning is continual: all systems are scanned all the time. However, different constraints call for scanning on a routine basis instead of around the clock
Technical constraints
Limitations based on technologycan dictate how frequently a scan may be performed. For an organization with a very large network with many devices, it simply may not be possible to scan the entire network within a desired time period. Other ________ include limitations on network bandwidth and vulnerability scan software license limitations. When dealing with ________, spreading out the scans to run at specific times may be a necessary alternative.
Workflow interruptions
Continual vulnerability scans may impact the response time of a system so that the daily workflow or normal business processes are hindered. Moving the scans to “off hours” such as nights or weekends can limit the interruptions.
Regulatory requirements
Specific regulations can dictate how frequently a vulnerability scan must be performed. For example, some regulatory bodies state how often vulnerability scans must be conducted.
Risk appetite
A final consideration is the organization’s tolerance for exposure to a vulnerability. The _______ for different systems may be different: those systems with sensitive data for which there is a low-_______ may be scanned more frequently than those systems that contain only public data and have a high-________
Open Vulnerability Assessment Scanner (OpenVAS)
is considered a full-featured vulnerability scanner that currently includes over 50,000 vulnerability tests and receives daily updates. Greenbone Networks has maintained ________ since 2009 and serves as part of Greenbone’s proprietary vulnerability management system. However, ________ itself has been contributed as open source under the GNU General Public License (GNU GPL).
Invicti
is a tool for scanning website applications for vulnerabilities and is a type of application package monitoring tool. It provides a detailed directory structure breakdown and remediation guidance for discovered vulnerabilities. Scans can be triggered on a scheduled or ad-hoc basis
Nexpose
is a well-known vulnerability scanner from Rapid7.
A _______ Community Edition is a scaled-down version of Rapid7’s more comprehensive vulnerability scanner. The Community Edition will run on physical machines under either Windows or Linux and is also available as a virtual appliance to run within a virtual machine. However, the Community Edition has several limitations: only a maximum of 32 IP addresses can be scanned and it can only be used for 12 months
Nessus
It is a product of Tenable and contains a wide array of prebuilt templates. Nessus advertises that new plug-ins are available as soon as 24 hours after a new vulnerability is disclosed. ________ has a free version that will only scan 16 IP addresses.
Plug-In (Updates)
These module updates, known as a _______ can be downloaded and installed as needed. However, plug-ins generally go beyond basic updates. Many _______ contain advanced vulnerability information, a set of remediation actions, and updated algorithms to test for the presence of the security issue.
Vulnerability and Threat Feeds
To provide a set of vulnerabilities to vulnerability scan software, there are various vulnerability feeds, which are sources of data related to potential or current threats that provide this data. Some feeds are proprietary from third parties. Other feeds are from information sharing organizations or OSINT. Some of the best-known vulnerability feeds are the NIST National Vulnerability Database (NVD), MITRE Common Vulnerabilities and Exposures (CVE), AlienVault, and FBI InfraGard Portal. Vulnerability scanning tools allow for these feeds to be input into the scanning software.
Configuring the Scan Software
Configuring vulnerability scan software involves setting specific parameters so that the scan meets the intended objective. These parameters include the scope, sensitivity levels, and data types.
scope
The _______ of a vulnerability scan is the target devices to be scanned. This generally include a range of hosts or subnets, as shown in Figure 12-6. The _______ of a scan should be designed to meet the intended goals of the scan. If a specific vulnerability for Windows 11 computers is being targeted in the scan, for example, then it makes sense to only scan systems running that OS
environmental variables (scope)
which are variables whose values are set outside the program, typically through functionality built into the OS or a microservice. An _______, for example, can point to a directory that is to be excluded from a scan.
sensitivity level
is the depth of a scan. That is, what type of vulnerabilities are being searched for? While a general scan may search for all vulnerabilities, often a scan is looking for a specific type of vulnerability. The sensitivity configuration variable can be used to limit how deeply a system is examined.
Data Type
Another configuration setting specifies the ________ to be scanned. Like the sensitivity level, this can be used to “drill down” when searching for a specific vulnerability in a known file type instead of searching all files on a system.
Scanner Permissions and Access
Yet just as the scanner needs permissions to access the network, from another standpoint, an additional set of scanner permissions are also needed. These are permissions for a user to access and use the scanner itself
Testers using a vulnerability scanner should have permissions from internal supervisors to use the software, and this software should only be used to access approved systems.
Pull
is when you are seeking information, such as the answer to a question, so you _____ that information into you
Push
is when you are using the Internet in a more passive way and content comes to you. By posting the information about the restaurant’s closing time in your social media account, it is then _____ed to your friends
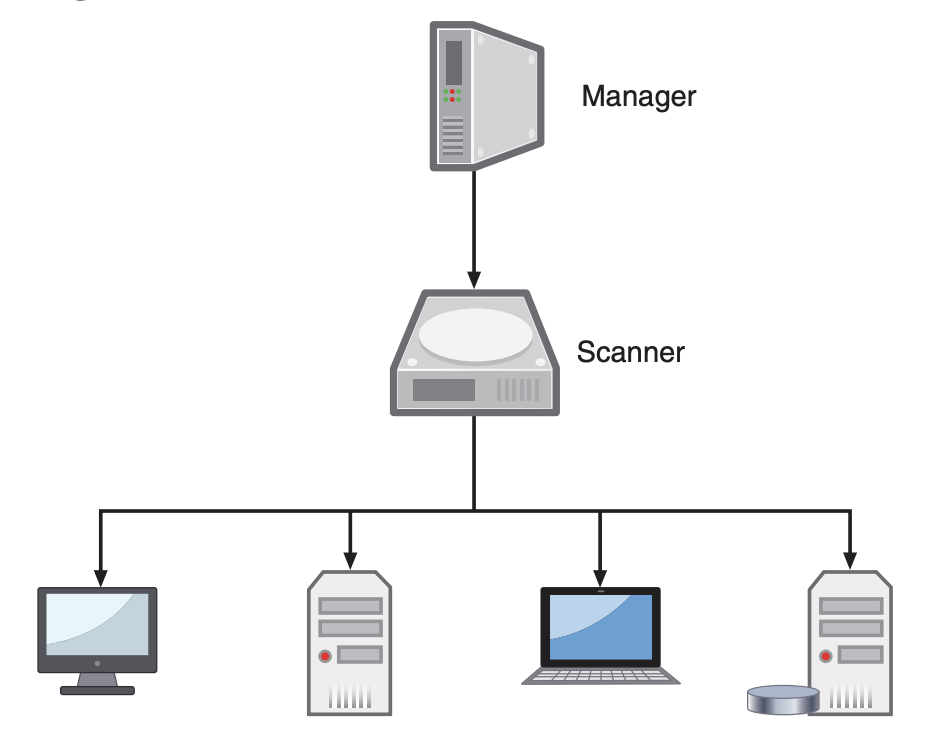
server-based (pull) scanner technology
Vulnerability scanners have traditionally used a pull approach: a scanner manager connects to a scanner engine that probes each system for information that is then gathered (pulled) back for analysis
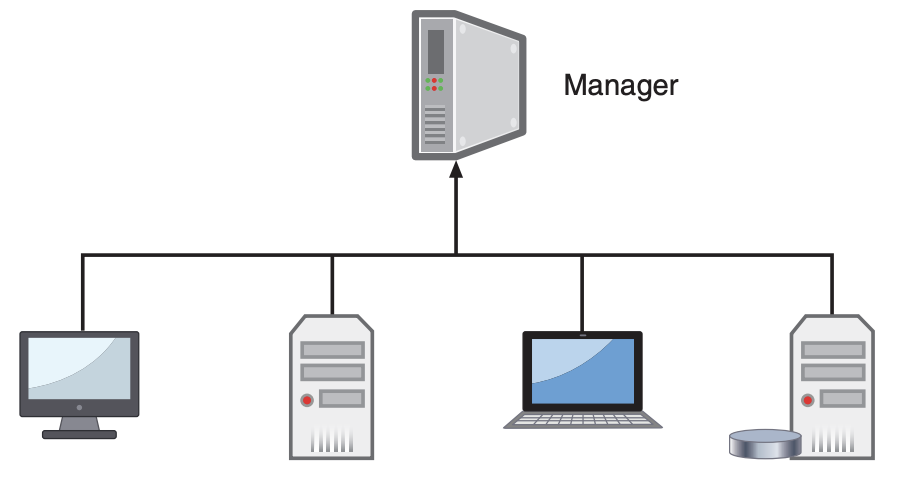
agent-based (push) scanner technology
tend to have less impact on network performance. However, the software agents could become the target of threat actors so that they would not accurately report the true status of a compromised computer
credentialed scan
is a scan for which valid authentication credentials are supplied to the vulnerability scanner to mimic the work of a threat actor who possesses these credentials
are slower but can provide a deeper insight into the system by being able to access a fuller range of software installed on the system and examine the software’s configuration settings and current security posture.
noncredentialed scan
provides no such authentication information
run faster because they are performing fundamental actions such as looking for open ports and finding software that will respond to requests
Network Appliance Configurations
Vulnerability scanners should set off alarms on security appliances such as intrusion detection systems (IDSs), intrusion prevention systems (IPSs), and firewalls. One approach is to mitigate these alarms by instructing the IDS/IPS to ignore attacks originating at the vulnerability scanner and to also configure the vulnerability scanner to correspond to the IDS/IPSAnalyzing Vulnerability Scans
Analyzing Vulnerability Scans
If the scan were 100 percent accurate, then the organization would know that a future attack would accurately trigger an alarm (true positive) while the absence of an attack would not trigger an alarm (true negative). However, it is possible that the scan could generate an error. There are two types of these errors. A false positive is an alarm that is raised when there is no problem, while a false negative is the failure to raise an alarm when there is an issue.
reporting
Distributing the results of the scan to the appropriate parties
Vulnerability scan reporting Types
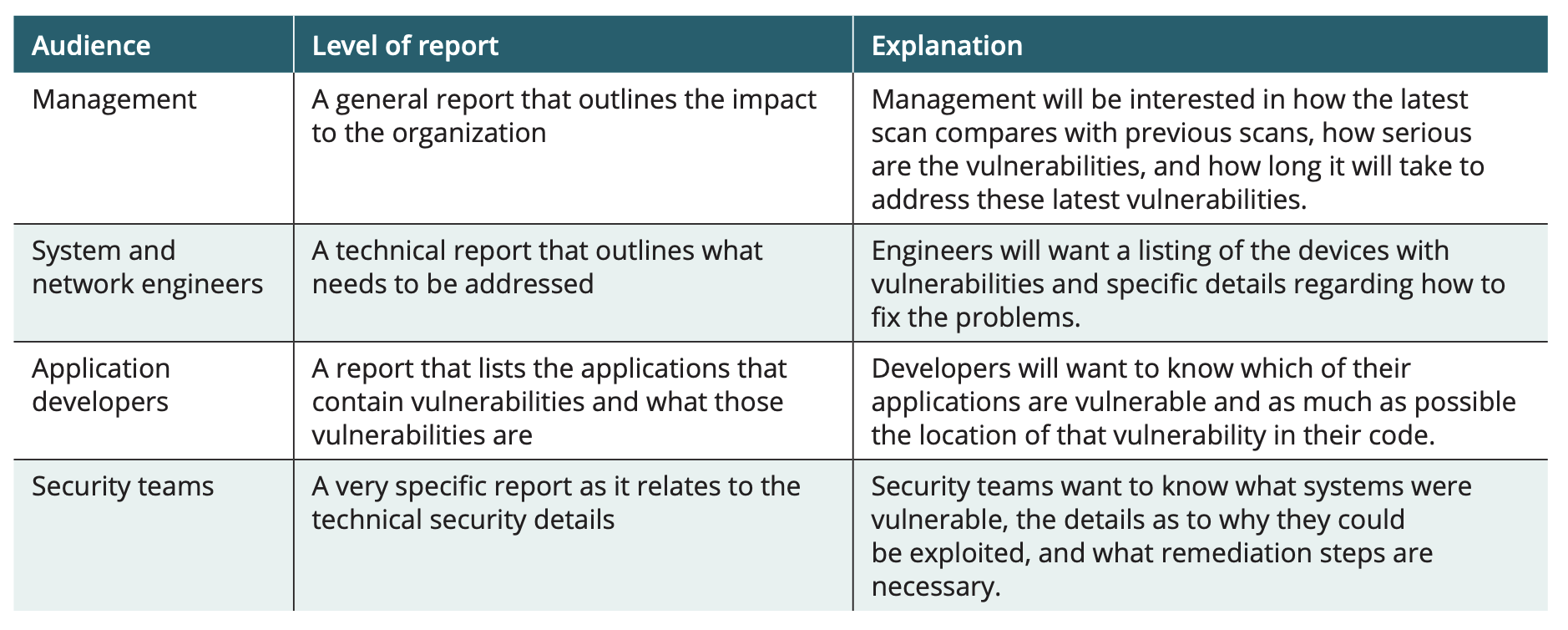
Addressing Vulnerabilities (final step scanning)
This involves remediating vulnerabilities. To remediate vulnerabilities, the first step is to prioritize the vulnerabilities. Then action steps should be taken to address those vulnerabilities that have been prioritized as most important.
Common Vulnerability Scoring System (CVSS)
contains numeric scores generated using a complex formula that considers such variables as the access vector, attack complexity, authentication, confidentiality of the data, and the system’s integrity and availability. The vulnerabilities with the highest numeric ______ scores are generally considered to require early attention.
Common Weakness Enumeration (CWE)
is another categorical system for hardware and software weaknesses and vulnerabilities. The ______ rankings are based on a vulnerability classification system or categories of similar vulnerabilities. The ______ has over 600 different categories with rankings, including classes for buffer overflows, directory tree traversal errors, race conditions, cross-site scripting, hard-coded passwords, and insecure random numbers.
Take Action Steps
Once the vulnerabilities are prioritized, a series of action steps can be taken to actively address these uncovered vulnerabilities.
Patch and harden (action steps)
Vulnerabilities should first be addressed by patching systems that are missing existing software updates. This is the easiest, quickest, and most economical approach and generally will address a high number of exposed vulnerabilities. After patching, the systems should be hardened as necessary with new hardware or software
Address difficult vulnerabilities (action steps)
Some vulnerabilities that need to be addressed will not have a quick and easy solution; instead, the options are very difficult or impractical at the present time. In these cases, it may be necessary to determine an alternative action (compensating control), such as removing an endpoint from the network.
Identify exceptions and exemptions (action steps)
In some cases, it may be necessary to declare that certain vulnerabilities fall outside the bounds of what the organization will address (exceptions and exemptions). This may be due to a low exposure factor (exposure factor is a subjective estimate of the loss to an asset if the specific threat occurs) or low industry/organizational impact (a determination that an attack will have a small effect). In some cases, it may be appropriate to pay a third-party for insurance so that if an attack occurs based on the vulnerability, the organization will be compensated for it. Different organizations will approach these exceptions and exemptions differently based on their willingness to assume a level of risk in order to achieve a result (risk tolerance).
Analyze network segmentation (action steps)
The work of a threat actor to penetrate a system often follows a similar pattern. The threat actors first conduct reconnaissance against the systems, looking for vulnerabilities, and when a path to a vulnerability is exposed, they gain access to the system through it. Once initial access is gained, they escalate to more advanced resources by tunneling through the network looking for additional systems they can access from their elevated position. In order to thwart this movement by threat actors, it is important that network segmentation be utilized. Network segmentation is designed to architect a network so that parts can be cordoned off or segmented into isolated sections. This allows an organization to treat different segments of the network differently based on the classification of the data in that segment: low-risk segments may have fewer restrictions while high-risk segments are more heavily protected. Vulnerability scans can be used to identify vulnerabilities in network segmentation, and several regulatory requirements even mandate that segmentation controls be scanned.
Verify mitigation (action steps)
It is important to corroborate that the vulnerabilities have indeed been properly addressed (validation of remediation). This is done by performing another vulnerability scan (rescanning) followed by an analysis of the results (audit) for validation of their accuracy (verification). In addition, once the changes have been approved and applied to the production system, these changes need to be formally communicated and recorded.
audit
is an examination of results to verify their accuracy
Someone performs this other than the person responsible for producing the results.
assessment
is a judgment made about those results. An assessment goes further than an audit: it involves actions necessary to make what was assessed brought back into conformity with the required standards.
internal audits (or self-assessments)
because they are “inward focused” on the organization itself. The goal of internal audits is to identify the actions needed to put what was assessed back into compliance or conformity to mandated standards.
audit committee
one of the major operating committees of a company’s board of directors. The _______ oversees the organization’s financial statements and reporting by providing proof (attestation) that the organization is in compliance with required standards. At least one person on the committee must qualify as a financial expert. All U.S. publicly traded companies must maintain a qualified audit committee to be listed on a stock exchange
External assessments
are performed by professionals from outside the organization. Because they are not employees whose welfare could be jeopardized by a poor review, these professionals perform an independent third-party audit. Their assessments or examinations of the organization are often to ensure that the company is compliant with regulatory requirements as set forth by outside bodies. There are numerous federal regulatory agencies as well as regulatory organizations that are industry specific.
penetration testing (“pen test”)
attempts to uncover vulnerabilities and then exploit them, just as a threat actor would. Unlike a vulnerability scan that is considered a defensive assessment because it only looks at the protections of a system, a penetration test is an offensive assessment that probes the system for weaknesses
involves a significant amount of time and resources
can go further to find and exploit “deep” vulnerabilities using manual techniques.
physical penetration testing
probing for weaknesses in physical security controls such as fencing and lighting to determine if the testers can enter restricted areas
integrated penetration tests
Penetration tests that probe both technical and physical weaknesses
Internal Security Personnel
Using internal employees to conduct a penetration test has advantages in some cases. First, there is little or no additional cost. Also, the test can be conducted much more quickly. Finally, an in-house penetration test can be used to enhance the training of employees and raise the awareness of security risks. When conducting an in-house pen test, an organization often divides security employees into opposing teams to conduct a “war game” scenario
Penetration testing war game teams
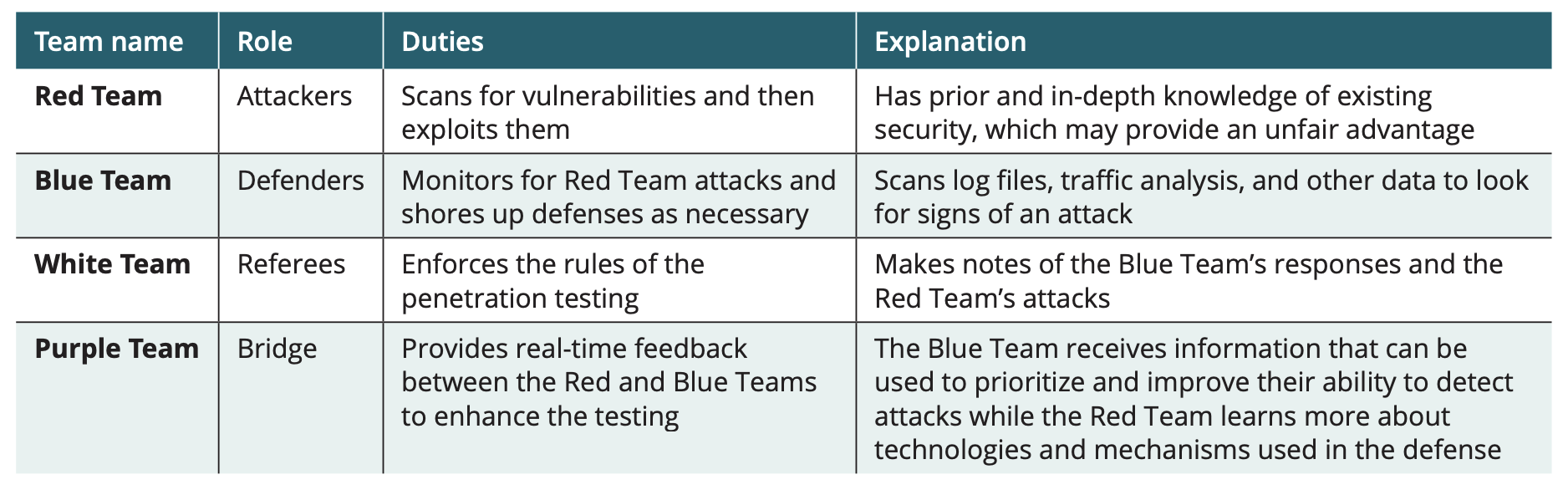
Disadvantages of internal penetration testing
Inside knowledge. Employees often have in-depth knowledge of the network and its devices. A threat actor, on the other hand, would not have the same knowledge, so an attack from employees would not truly simulate that of a threat actor.
Lack of expertise. Employees may not have the credentials needed to perform a comprehensive test. Their lack of expertise may result in few deep vulnerabilities being exposed.
Reluctance to reveal. Employees may be reluctant to reveal a vulnerability discovered in a network or system that they or a fellow employee have been charged with protecting.
External Consultants Advantages
Expertise. External contractors that conduct penetration tests have the technical and business expertise to conduct a thorough test.
Credentials. Pen test contractors usually employ people who hold several security certifications to validate their pen testing knowledge and experience.
Experience. Because they have conducted numerous penetration tests, contractors know what to look for and how to take advantage of a vulnerability.
Focus. Reputable penetration testing firms generally deliver expert security services and are highly focused on the task.
Penetration testing levels
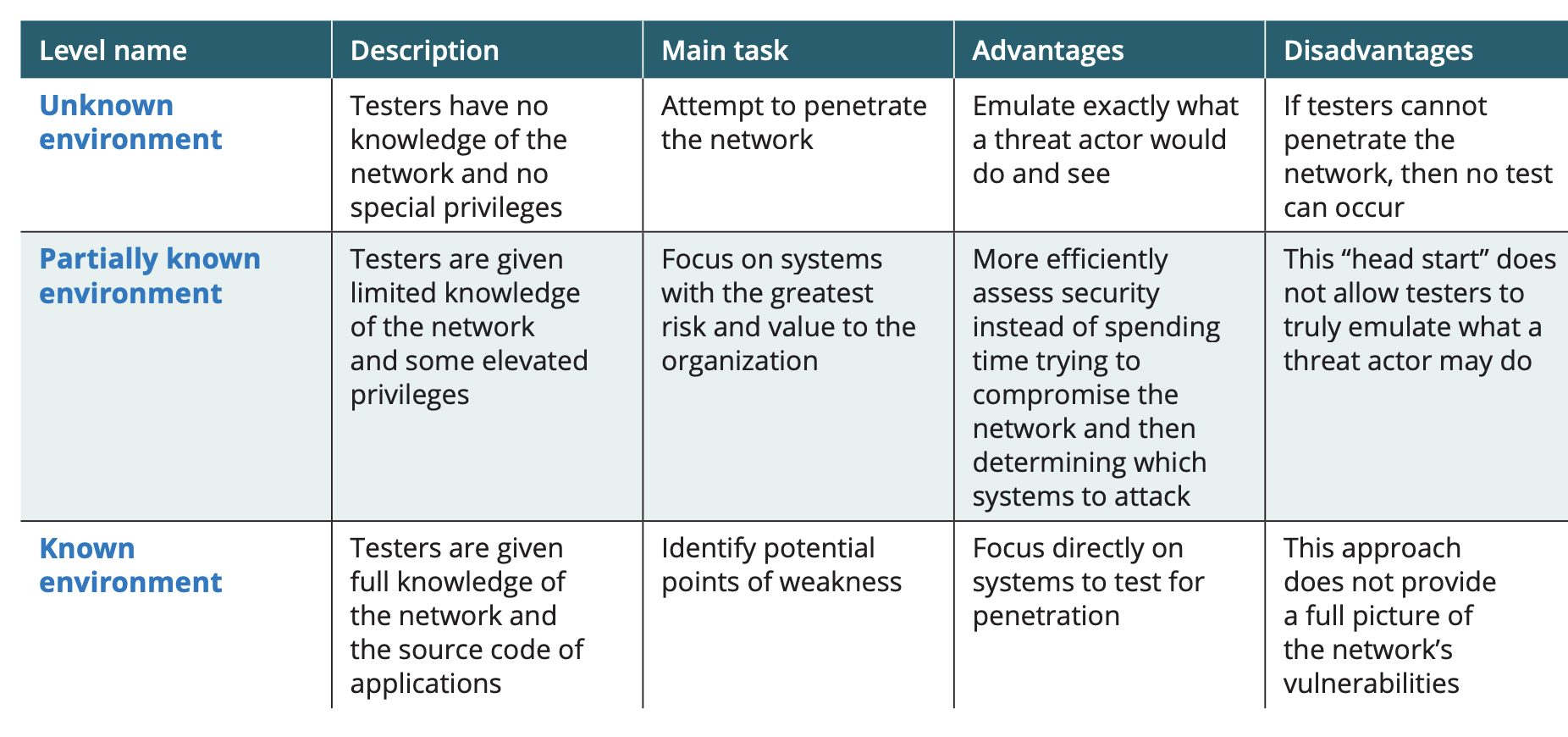
footprinting
One of the first tasks of testers with unknown or partially unknown environments is to perform preliminary information gathering from outside the organization
Active reconnaissance
involves directly probing for vulnerabilities and useful information, much like a threat actor would do. For example, unprotected wireless data transmissions from wireless local area networks can often be used to gather information or even circumvent security protections.
The disadvantage of a_______ in a pen test is that the probes are likely to alert those security professionals within the enterprise who did not know about the pen test that something unusual is occurring. This may result in them “locking down” the network to become more restrictive and thus more difficult to probe.
Passive reconnaissance
takes an entirely different approach: the tester uses tools that do not raise any alarms. This may include searching online for publicly accessible information like OSINT that can reveal valuable insight about the system.
Vulnerability scan versus penetration test