User Authentication
1/31
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
32 Terms
Authentication
the determination of the identity of someone
What steps does authentication consist of?
• Identification
• Verification
Identification
present an identifier to the authentication system
Verification
verify the validity of the presented identifier
What are the main approaches for user authentication?
➢ something the person knows (e.g., password),
➢ something the person has (e.g., smart card, a radio key fob storing secret keys),
➢ something the person is (e.g., human fingerprint)
Authentication vs. authorization
Who you are vs. what you can do
Who has to be authenticated?
The client and the server
Issues with password authentication?
> People use the same passwords for multiple websites
> People have predictable passwords
Manual Guessing
Cracking a password using personal information
Interception
Intercepting a password as it is transmitted over a network
Brute force
Automated guessing of billions of passwords until a correct one is found
Shoulder Surfing
Observing someone typing their password
Stealing passwords
Stealing insecurely written passwords
Social Engineering
Using social engineering techniques to trick people into revealing passwords
Searching for passwords
IT infrastructure can be searched for stored password information
Key logging
Installing a keylogger that intercepts passwords as they are typed by monitoring each keystroke the user types on her/his keyboard.
How to counteract phishing
A fake site can steal a password so counteract this you could use server-side authentication such as SSL/TLS
How are keyloggers installed?
by attaching the program to an image or file and then send it via email
Popular keyloggers
• Refog • Revealer • KidLogger
Dumpster diving
Attacker looks into the trash for piece of papers or documents with written passwords
How to countermeasure shoulder-surfing and dumpster diving ?
User Awareness and Training
Exhaustive search brute force attack
• Try all possible combinations of symbols up to a certain length
• The size of the password space is |A|n where n is the length of our password and A is the alphabet
alphabet (A) is composed of upper- and lowercase letters, digits, common symbols
96 characters
Online dictionary attack
• Intelligent search
• Try passwords associated with the user
• e.g., name, name of friends, car brand
• Try words in a dictionary
• Try popular passwords
Positive of online dictionary attack
Saves attackers time
Issue with online dictionary attack
No guarantee the right password is found
Simple Countermeasures to password attacks?
• Password policies : minimal length, needed format and avoid obvious passwords
• Changing passwords: force users to change passwords regularly
• Machine-generated passwords: generate long and difficult passwords
More effective countermeasures for password attacks?
• Lockout mechanics : lock user account after several unsuccessful login attempts
• Throttling : introduce time delays between unsuccessful login attempts
• Protective monitoring: monitor login to detect unusual use and notify the user with details of attempted login
• Password blacklisting : Check if an input password is in a list of common words
Password strength
measures the effectiveness of a password against brute force attack. It estimates the number of trials an attacker should make to guess the password correctly
How is password strength normally computed?
|A|^n
• A is our alphabet (the set of symbols composing the password)
• n is the length of the password
How else can password strength be computed
Using entropy:
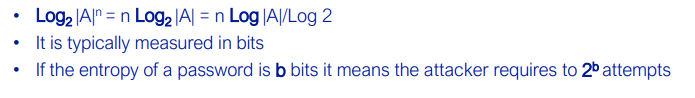
What is the issue with using entropy for the security of a password?
Entropy mathematically means security but it does not take into account dictionary attacks.