networks midterm
1/120
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
121 Terms
What are the important things that network apps must do?
they must run on different end systems and communicate over a network
What are the 5 layers in the 5 layer model?
Application, Transport, network, Data Link, Physical
In the client-server paradigm, what are servers?
They are always-on hosts, they have permanent IP addresses, and are often in data centers
In the client-server paradigm, what are clients?
They are other end devices that contact and communicate with the server, but are only intermittently connected. They may have a dynamic IP address and they DO NOT communicate directly with each other
How does a p2p (peer to peer) architecture differ from a client-server one?
in P2P, there is no server. Arbitrary end systems directly communicate and request/provide servers to each other. These end systems are intermittently connected to each other and change IP addresses, making managing them complicated.
How do processes communicate?
by exchaning messages
What are the two types of processes and how do they differ?
Child and Server; child processes initiate communication and server processes wait to be contacted.
What is a socket?
The “door” for which a process sends and receives messages. There is a socket in each process that facilitates this communication, and they rely on the transport on either side to deliver messages.
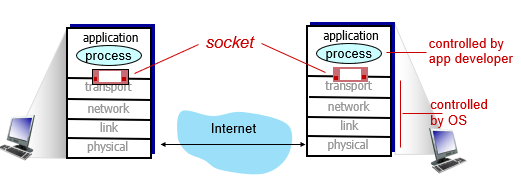
How does the transport layer know where to send messages?
Through the identifier of the processes, to include the IP address and the port number of the process on the host machine.
What does the 80 and 25 port numbers typically refer to?
an HTTP server and a mail server respectively
What are the 4 things defined by the application layer protocols?
The types of messages exchanged, the message syntax, the message semantics, rules for sending/responding.
What are the two types of application layer protocols?
open (where everyone has access to the protocol definition and allows for interoperability) and proprietary
What types of metrics are transport services measured on?
timing, data integrity, throughput, and security
What are the strengths of TCP?
It provides reliable transport and has congestion control algorithms in places
What are the weaknesses of TCP?
It does not think about timing, only has a minimum throughput guarantee, and has lacking security, and requires setup between the client and server processes.
Why do people use UDP?
When you need to send a couple messages REALLY FAST. like temporary data, or data that is very small and expects no or a very small answer.
What is TLS?
TLS is transport layer security, and it provides encrypted TCP connections and further data integrity, as well as end-point authentication.
What makes of a web page?
objects, which are stored on different web servers.
What is HTTP?
Hypertext transfer protocol; it is the web’s application later protocol
What is the server and client in the context of HTTP?
The client is the browser that requests, receives, and displays web objects. the server is the web server that sends objects in response to requests.
Explain the process for how HTTP uses TCP.
The client initiated a TCP connection to the server (port 80), the server accepts this connection, the HTTP messages are exchanges between the browser and the web server, and the connection is closed.
Does HTTP maintain information about past client requests?
NO. it is stateless.
What are the two types of HTTP connections?
Non-persistent (one object is sent per TCP connection) and persistent (multiple objects are sent over one TCP connection)
What is RTT?
The Time it takes for a small packet to travel from client to server and back.
for HTTP, how long does it take to send one object in a non-persistent context?
2 RTT
What are the two types of HTTP messages?
request and response
What are four basic HTTP request methods?
POST (for page with form input), HEAD (requests header), PUT (uploads object to server), GET (send data to server)
What are HTTP response status codes? What are some examples?
They are numbers in the 1st line in server-to-client response messages. examples are 200 OK, 400 Bad Request, 404 Not Found, and 301 Moved Permanently.
What are cookies used for?
They are used to maintain some state between transactions, they are stored in files kept on the user’s host and manages by the user’s browser.
What does transport protocols provide?
logical communication between application processes running on different hosts.
What do transport protocols do in end systems?
in sender it breaks application messages into segments, passes to network layer. Then in receivers it reassembles segments into messages, and passes them to the application layer.
What does TCP and UDP stand for?
Transmission Control Protocol, and the User Datagram Protocol
What does TCP providing “full duplex data” mean?
It means that it provides a bi-directional data flow in the same connection and is based around a MSS
What does it mean that TCP does “pipelining”?
it has congestion and flow control based on a set window size
What are sequence numbers?
they are the byte stream “number” of the first byte in a segment’s data.
What are ACKnowledgement numbers?
they are the sequence number of the next byte expected from the other side
When does a timeout occur?
when the sender does not receive an ACK for a sent packet within a predefined time interval.
How is a sample RTT estimated?
It is the measured time from segment transmission until the ACK receipt (ignoring retransmission)
What is an EWMA (the mathematical term for the type of calculation that produces an estimated RTT)?
Exponential Weighted Moving Average
What is a timeout interval typically set to?
The estimated RTT and some sort of safety margin, often a scalar of the deviation of the sample RTT from the calculated estimate RTT.
What does the TCP sender do when it receives data from the application?
it creates a segment with a sequence number and (sometimes) starts a the timeout timer.
What does the TCP sender do when it timesout?
it transmits the segment that caused the timeout and resets the timeout timer.
what is a TCP Retransmission?
If the sender receives 2 additional ACKs for the same data, it will resend the unACKed segment with the smallest sequence number, and this is likely to prevent timeout by sending back what is probably the lost segment.
what is flow control?
A method for which the receiver controls the sender so that the sender doesn’t overflow the receiver’s buffer by transmitting too much, too fast.
How is flow control achieved?
The TCP receiver advertises its free buffer space in the rwnd (receive window) field of the TCP header. This is the “Calculated window size". This causes the sender to limit the amount of unACKed "(in flight) data to the rwnd.
How do the sender and receiver begin a connection in TCP?
with a handshake where they agree on the parameters and rules of the connection
What is the difference between a 2 and 3 way handshake?
the three way handshake includes a SYN and SYNACK message (i do not know beyond that. cant figure it out)
How are TCP connections closed?
the client and server each close their side of the connection by setting the FIN bit in the header to 1.
What are the two manifestations of network congestion?
long delays (from queuing in router buffers) and packet loss (from buffer overflow)
What is the difference between congestion control and flow control?
congestion controls deals with stopping too many senders from sending things too fast, while flow control deals with stopping one sender from sending to much too fast.
What is the approach congestion control algorithms (or at least the ones we talked about) take?
AIMD, additive increase and multiplicative decrease.
What are the three TCP control algorithm phases?
slow start, fast recovery, and congestion avoidance
what happens in is slow start?
when the cwnd (originally at 1) begins doubling every RTT until it reaches the ssthresh
what happens in congestion avoidance?
the ssthresh is set to half of the current cwnd and the cwnd is set to 1 (in tahoe and reno when there is a timeout) or the ssthresh (in reno when there is a triple ACK)
what happens in fast recovery?
after the ssthresh has been reached, the cwnd increases by one MSS each RTT.
What is the benefit of TCP cubic?
it produces higher throughput most of the time
What are the two main paradigms to congestion control?
end to end and network assissted
How does end-end congestion control work?
There is no explicit feedback from the network, so any congestion isnt known but inferred by an observed loss and delay. This is what TCP does.
How does network assisted congestion control work?
Routers provide direct feedback to hosts with flows passing through the congested router, this may indicate congestion level or explicitly set the sending rate.
When is an Explicit Congestion Notification used and what does it do?
It is used in network assisted congestion control for TCP deployments. It is 2 bits found in the IP header that indicates the state vis a vis congestion wise. W
What is fairness in the context of TCP?
It is if K TCP sessions share the same bottleneck link of bandwidth R, then each should have an average rate of R/K
What is the goal of the network layer?
to transport segments from the sending to receiving host
What does the network layer do for the sender?
encapsulates segments into datagrams and then passes those to the link layer
What does the network layer do for the receiver host?
if delivers segments to the transport layer
What are the two key functions of the network layer?
forwarding (moving packets from a router’s input link to the appropriate router output link) and routing (determine the route needed to be taken by packets from source to destination)
What is the data plane?
it is local, used on a router level. It determines how datagrams arriving at a router input port is then forwarded to a router output port.
What is the contorol plane?
used on a network wide level, determines how datagrams are routed among routers along end-end paths from source host to destination host.
How do routers interact with the control plane?
There are individual routing components in each router
How does software defined networking work?
from the routers data planes, a remote control computes forwarding tables in routers to facilitate transmission.
What piece of a routers architecture does the data plane live in
The switching fabric between the input and output ports.
How does a router input port function?
information is received through the physical layer into a line termination point, then a link layer protocol (like ethernet) sends it to queue where the dataframes wait before they can be sent to the switch fabric.
How does destination based forwarding work?
The router looks at the forwarding table provided by the control plane and determines the “best” route based on the source and destination IP address (by finding the longest prefix match) before sending the datagram to its next destination.
What is the longest prefix match?
When looking for a forwarding table entry for a given destination address, it uses the longest address prefix that matches up with the destination address.
What does the switching fabric do?
it transfers packets from the input link to the appropriate output link
What is the switching rate?
the rate at which packets can be transferred from inputs to outputs. This is often measured as multiple input/output line rate.
What are the three major types of switching fabrics?
memory, bus, and interconnection network
What type of switch fabric did first generation routers use?
memory
how does switching via memory work?
switching was controlled directly by the CPU, the packet would be copies to the system’s memory, however the speed was limited by memory bandwidth
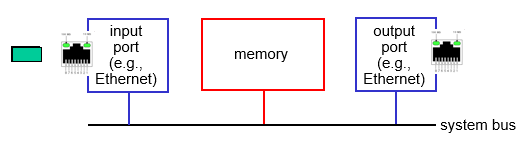
How does switching via a bus work?
The datagram is moved from the input port memory to the output port memory, however the speed is limited by the bus bandwidth.
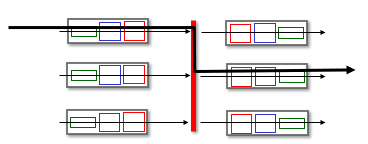
how does switching via an interconnection network work?
Generally, crossbar networks were developed to connect processors in mutliprocessors. However they can do a multistage switch, where nxn switch from multiple stages of smaller switches. These exploit parallelism by sending fragments of the datagram at a time, and then reassembles them at the exit.
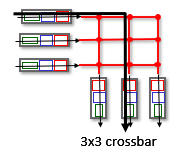
How can interconnection network switching fabrics be scaled?
by having more than one fabric plane at a time, it can send datagrams extremely quickly by doing it in as many pieces as the planes allow. So it can be scaled by adding more switching planes.
How does round robin scheduling work?
Traffic arriving is classified by looking at header information. the server cyclically, repeatedly scans class queues, sending one from each class in turn.
What is Head of the Line (HOL) blocking and when does it occur?
It is when there is a backup in the input queues of a routers input ports, and not all of the information can be sent in the switch fabric at a time.
In output port queueing, what is buffering?
buffering is when datagrams arrive from the fabric faster than the link transmission rate, so the output port has to decide what packets to drop to prevent further congestion.
In output port queuing, what is scheduling discipline?
It is how the output port chooses among queued datagrams for transmission, normally it uses priority scheduling (who has the best performance, or achieves network neutrality.
What is buffer management?
The two part process for which the output port handles the queue: it will decide which packets to drop if the buffer queue is full (either by dropping new packets that arrive or on a priority basis) and then marking packets to signal congestion (like with ECN)
What are the four types of packet scheduling?
FCFS, round robin, priority, weighted fair queuing
How does FCFS scheduling work?
Packets are transmitted in the order of arrival to output port (also like FIFO)
How does priority scheduling work?
Arriving traffic is classified by header information, and then it sends out the packet from the highest priority queue that has buffered packets (FCFS within priority class)
How does Round Robin Scheduling work?
arriving traffic is classified and then queued by class. The server cycles between these classes and sends out one from each at a time.
How does weighted fair queuing work?
This is a version of round robin where each class has a weight and gets a weighted amount of service each cycle.
What is an IP address?
a 32 bit identifier associated with each host or router interface, of which a router might have many a host will only have one or two (wired and wireless)
What is a subnet?
a subsect of a larger network connected by a router that can interface with each other without passing through an intervening router.
What are the two parts of an IP address?
subnet part and host part/
What is CIDR?
Classless Inter Domain Routing, and its the notation with \x at the end of an IP where the x is the number of bits in the subnet portion.
How do things get an IP address dynamically?
through the Dynamic Host configuration protocol, which allows things to enter and leave the network and reuse and renew “leases” on IP addresses.
What are the four messages that are sent between a router and a host in a DHCP interaction?
a discover message, an offer message, and a request message, and an ack
What are the two reserved IP addresses?
0.0.0.0 and 255.255.255.255
What organization gives ISP’s their IP address block?
ICANN, or the Internet Corporation for Assigned Names and Numbers
what is NAT?
Network Address Translation; which basically means that lal devices in a local network share just one IPv4 address as far as the outside world is concerned.