Security
5.0(2)
Card Sorting
1/90
Earn XP
Description and Tags
Study Analytics
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
91 Terms
1
New cards
when is a system classed as secure?
A system is secure if its resources are used and accessed as intended under all circumstances- only designated users can access and use the correct resources
2
New cards
why is security important?
Security is important as systems containing data could be useful to competitors and loss of data can impair the corporation to function
3
New cards
what is the security problem?
total security cannot be achieved
4
New cards
how can we limit security breaches?
use security mechanisms such as
* antivirus software
* our behaviour
* antivirus software
* our behaviour
5
New cards
what is a ^^security violation^^?
an intentional (malicious) or accidental breach/ breaking of security
intentional = malware
accidental = a link click/ easier to prevent against
intentional = malware
accidental = a link click/ easier to prevent against
6
New cards
what is an ^^attack^^?
an attempt to breach security, doesn’t mean it has breached
7
New cards
what is a ^^threat^^?
a potential security violation, something that may or may not happen, but has the potential to cause serious damage. Threats can lead to attacks on computer devices and networks.
8
New cards
what is an ^^intruder^^?
a person who attempts to gain unauthorised access to a system
9
New cards
what does an intruder try to do?
* attempts to damage a system or disturb the data on a system.
* systems = refers to network systems, own system, house security, operating systems
* attempts to violate security.
* systems = refers to network systems, own system, house security, operating systems
* attempts to violate security.
10
New cards
what are the different types of security violations?
breach of confidentiality
breach of integrity
breach of availability
theft of service
denial of service
\
breach CIA, service ToDay
breach of integrity
breach of availability
theft of service
denial of service
\
breach CIA, service ToDay
11
New cards
what is a breach of confidentiality?
* Involves unauthorised ==access== to data (or theft of information). For example, credit-card information, identity information used for identity theft, etc.
* can be done with an online system or can be physically done
* can result in money for the intruder
* can be done with an online system or can be physically done
* can result in money for the intruder
12
New cards
what is a breach of integrity
* Involves unauthorised ==modification== of data. For example, changing the content of a website, changing the text of a message, modifying the source code of commercial application
13
New cards
what is a breach of availability?
* Involves unauthorised ==destruction== of data. For example, website defacement, etc.
14
New cards
what is a theft of service?
* Involves unauthorised ==use== of resources. For example, an intruder (or intrusion program) may install a daemon on a system that acts as a file server.
* ==recourses no longer accessible==, or on own computer with malicious software that ==prevents own access==
* ==recourses no longer accessible==, or on own computer with malicious software that ==prevents own access==
15
New cards
what is a denial of service? \[security violation\]
* Involves preventing legitimate use of the system. Denial-of-service (DOS) by ==overwhelming the service with illegitimate traffic==
* web servers have capacity to serve number of users. many malicious requests (people/bots) that means legitimate users cannot access the web server.
* e.g. Internet worm that lead into DOS attack when bug failed to delay spread
* web servers have capacity to serve number of users. many malicious requests (people/bots) that means legitimate users cannot access the web server.
* e.g. Internet worm that lead into DOS attack when bug failed to delay spread
16
New cards
what are the different security violation methods?
masquerading
replay attack
man-in-the-middle attack
session hijacking
replay attack
man-in-the-middle attack
session hijacking
17
New cards
what is masquerading?
* One participant in a communication pretends to be someone else (another host or another person).
* This is a ==breach of authentication==, as the participant has access that would not normally be allowed or obtain privileges to which would not normally be entitled.
* the receiver doesn’t know that the communication is not with intended user
* This is a ==breach of authentication==, as the participant has access that would not normally be allowed or obtain privileges to which would not normally be entitled.
* the receiver doesn’t know that the communication is not with intended user
18
New cards
what is a replay attack?
* Consists of the malicious or fraudulent repeat of a valid data transmission.
* replay can be the whole attack eg. repeat of a request to transfer money → ordering online, can repeat the transaction and change the data to order something else, frequently along with message modification.
* replay done with message modification, the attacker changes details in communication without the sender’s knowledge (change authorised details of a user to hackers details during an authentication request )
* replay can be the whole attack eg. repeat of a request to transfer money → ordering online, can repeat the transaction and change the data to order something else, frequently along with message modification.
* replay done with message modification, the attacker changes details in communication without the sender’s knowledge (change authorised details of a user to hackers details during an authentication request )
19
New cards
what is a man-in-the-middle attack?
An attacker sits in the data flow of a communication, masquerading as the sender to the receiver, and vice versa.
20
New cards
what is session hijacking?
* Intercept an active network communication to bypass authentication.
21
New cards
what is a security measure?
an action to make it difficult or costly for an attack and be successful in order to deter perpetrators
22
New cards
do we need to PREVENT or DETECT attacks?
both, but in some cases e.g. DOS attack
* better to PREVENT attacks
* sufficient to DETECT attacks so counter measures can be taken
* better to PREVENT attacks
* sufficient to DETECT attacks so counter measures can be taken
23
New cards
what are the different security level measures?
physical
human
operating system
network
human
operating system
network
24
New cards
what is the physical security measure level?
* the sites containing the computer systems must be physically secured from intruder entry
* Data centres, servers, connected terminals
* (eg. door locked, access cards, access to the physical space/ resource)
* Data centres, servers, connected terminals
* (eg. door locked, access cards, access to the physical space/ resource)
25
New cards
what is the human security measure level?
* authorization ensures only authorised users, but authorised users can be encouraged or tricked into giving away their access
* Avoid ^^social engineering^^ such as phishing (fake email), dumpster diving
* @@phishing@@ - urgent, legitimate-looking emails, when replying IP address and our info is stored somewhere, or we are submit sensitive information
* @@dumpster dive@@- searching our bins, notebooks and gaining access
* Avoid ^^social engineering^^ such as phishing (fake email), dumpster diving
* @@phishing@@ - urgent, legitimate-looking emails, when replying IP address and our info is stored somewhere, or we are submit sensitive information
* @@dumpster dive@@- searching our bins, notebooks and gaining access
26
New cards
what is the operating system security measure level?
* operating system needs to have protection mechanisms from accidental or purposeful security breaches, debugging
* eg. runaway process = accidental DOS attack, bad query can reveal password, stack overflow can launch unauthorised processes
* preventative measures include passwords managers, updating the os to get latest security patches
* eg. runaway process = accidental DOS attack, bad query can reveal password, stack overflow can launch unauthorised processes
* preventative measures include passwords managers, updating the os to get latest security patches
27
New cards
what is the network security measure level?
* data travels over private leased lines, shared lines (Internet), wireless connections etc.
* can lead to intercepted communications, interruption, DOS
* firewalls
* can lead to intercepted communications, interruption, DOS
* firewalls
28
New cards
which security measure level is the weakest?
Security is as weak as the weakest link in the chain so all levels need to be maintained - physical and human levels must be ensured to allow operating system security to be ensured as weakness at higher levels allows lower level security to be circumnavigated
29
New cards
what are program threats?
programs that can do malicious actions like attacking other programs, by using a weakness in the protection mechanisms of a system
30
New cards
what are the types of program threats?
trojan horse
trap door
logic bomb
stack and buffer overflow
virus
\
\[ turtle took lil squishes’s virus \]
trap door
logic bomb
stack and buffer overflow
virus
\
\[ turtle took lil squishes’s virus \]
31
New cards
what is a trojan horse?
* a code segment that %%misused its environment%% eg. program runs in the users domain and is able to do anything that the user can do like block, modify, delete data
* a program that %%pretends to be something else%%, e.g. login in system. the users details are stolen before the torjan redirects to the genuine page to not look suspicious
* ==Install backdoor daemon== = provides information/ allows easy access to information even if the original exploit is blocked
* ==includes spyware== - a program accompanied by another program the user has installed with goal to download ads, create popups, or capture user information
* Can not self-replicate
* a program that %%pretends to be something else%%, e.g. login in system. the users details are stolen before the torjan redirects to the genuine page to not look suspicious
* ==Install backdoor daemon== = provides information/ allows easy access to information even if the original exploit is blocked
* ==includes spyware== - a program accompanied by another program the user has installed with goal to download ads, create popups, or capture user information
* Can not self-replicate
32
New cards
what is a trap door?
* a code designer leaves a “hole” for accessing the system that they can take advantage of later on
* e.g. hardcoded credentials allows somebody else to access it without using the normal security procedures
* difficult to detect as we have to analyse all of the source code
* e.g. hardcoded credentials allows somebody else to access it without using the normal security procedures
* difficult to detect as we have to analyse all of the source code
33
New cards
what is a logic bomb?
* program activated under certain circumstances, e.g. coded to activate at at specific date/time eg. activated if employee is fired to damage the system
* difficult to detect as the program acts normally under normal operations
* difficult to detect as the program acts normally under normal operations
34
New cards
what is a stack and buffer overflow?
* The hacker exploits a bug in the program as a result of poor programming to write arguments into the return address on stack
* hacker can write code in the stack that includes the commands that the hacker wants to execute
* hacker can write code in the stack that includes the commands that the hacker wants to execute
35
New cards
what is a virus?
* A fragment of code embedded in a legitimate program
* can come from spam emails downloading viral programs, exchanging infected disks, contained in documents that will execute automatically when in programs from Office suite like word or powerpoint.
* a ==virus dropper== inserts the virus into the system. once installed the virus can self-replicate, infect other programs and spread over a network, infect other machines e.g. email itself to other machines
* can modify or destroy files, cause program malfunction and system crash
* can come from spam emails downloading viral programs, exchanging infected disks, contained in documents that will execute automatically when in programs from Office suite like word or powerpoint.
* a ==virus dropper== inserts the virus into the system. once installed the virus can self-replicate, infect other programs and spread over a network, infect other machines e.g. email itself to other machines
* can modify or destroy files, cause program malfunction and system crash
36
New cards
what are the type of viruses?
file/ parasitic
boot/ memory
macro
source code
polymorphic
encrypted
stealth
tunnelling
multipart
armoured
\
viruses find big, manly, snakes playing energetically to slowly make armour
boot/ memory
macro
source code
polymorphic
encrypted
stealth
tunnelling
multipart
armoured
\
viruses find big, manly, snakes playing energetically to slowly make armour
37
New cards
what is a file/ parasitic virus?
infect system by appending self to file, causes system to jump to infected code and then return control to og program to leave no trace
38
New cards
what is a boot/ memory virus?
executes every time the system is booted and before operating system loaded, do not appear in file systems
39
New cards
what is a macro virus?
virus written in high level language like visual basic, triggered when a program is capable of executing a macro eg. macro contained in an excel spreadsheet. requires the user to do something to activate the macro
40
New cards
what is a source code virus?
modifies the source code to include the virus and help it to spread
41
New cards
what is a polymorphic virus?
virus that changes each time it is installed to avoid detection from antivirus - changes the virus signature but not virus function.
*signature* = pattern used to identify a virus
*signature* = pattern used to identify a virus
42
New cards
what is an encrypted virus?
virus includes decryption code to decrypt self and then execute to avoid detection
43
New cards
what is a stealth virus?
modifies parts of system that can detect viruses in order to be undetected
44
New cards
what is a tunnelling virus?
installs itself in the interrupt handler chain in order to bypass antivirus scanner detection
45
New cards
what is a multipart virus?
able to infect multiple parts of the system making it difficult to detect and contain
46
New cards
what is an armoured virus?
virus that is coded to make it hard for antivirus software to unravel and understand, eg. compression, unviewable file names
47
New cards
what are system/network threats?
* threats that involve the abuse of services and network connections.
* create a situation in which operating-system resources and user files are misused.
* sometimes used to launch a program attack and vice versa.
* create a situation in which operating-system resources and user files are misused.
* sometimes used to launch a program attack and vice versa.
48
New cards
what are the different types of system/ network threats?
worms
port scanning
denial of service
\
wow, plz dos
port scanning
denial of service
\
wow, plz dos
49
New cards
what are worms?
* a process that uses the ^^Spawn^^ mechanism to copy itself / consume resources and lock other processes
* Can self-replicate
* ^^Standalone^^ → Unlike virus, doesn’t need the user to do anything for it to replicate
* made up of 2 programs:
* ^^grappling hook^^ - connects to the machine and uploads the main program onto the hooked system
* ^^main program^^ - searches for other machines that the system can connect to and infect
* E.G. MORRIS INTERNET WORM
* Can self-replicate
* ^^Standalone^^ → Unlike virus, doesn’t need the user to do anything for it to replicate
* made up of 2 programs:
* ^^grappling hook^^ - connects to the machine and uploads the main program onto the hooked system
* ^^main program^^ - searches for other machines that the system can connect to and infect
* E.G. MORRIS INTERNET WORM
50
New cards
what is port scanning?
* a way for the attack to detect the systems vulnerabilities to attack
* an automated attempt to make TCP/IP connection to a range of ports on one or a range of IP addresses
* created sockets have port numbers, sockets help us communicate with systems. hacker will scan the ports to see which sockets are available and send the virus through that port, exploit bugs, install trojan horses, back door programs etc.
* an automated attempt to make TCP/IP connection to a range of ports on one or a range of IP addresses
* created sockets have port numbers, sockets help us communicate with systems. hacker will scan the ports to see which sockets are available and send the virus through that port, exploit bugs, install trojan horses, back door programs etc.
51
New cards
what are zombie systems?
systems that have previously been compromised and act as attackers by launching port scanners without even knowing
52
New cards
what is denial of service? \[system/network threat\]
* Overload the targeted computer preventing legitimate use
* easier than an attack to break the machine
* 2 categories
* use up all resources that no useful work can be done e.g. a Java applet to start pop up windows infinitely using up all CPU time
* disrupt the network
* result from abusing the TCP/IP functionality where TCP session partially started and can use up network resources
* easier than an attack to break the machine
* 2 categories
* use up all resources that no useful work can be done e.g. a Java applet to start pop up windows infinitely using up all CPU time
* disrupt the network
* result from abusing the TCP/IP functionality where TCP session partially started and can use up network resources
53
New cards
what is DDOS?
distributes denial of service - a DOS attack launched from multiple sites at once by zombies
54
New cards
what is cryptography?
the science/ study of secret writing + cipher systems
55
New cards
what is encryption?
the process of encoding a message in a way that the information can not be accessed by unauthorised parties, or if accessed, cannot be understood
56
New cards
what is decryption?
the process of decoding a message using a key
57
New cards
what is a key?
a secret that is selectively distributed used for encryption and decryption
58
New cards
what is a cipher/ cypher?
an algorithm used to perform encryption / decryption
59
New cards
what is plaintext?
the original message (unencrypted)
60
New cards
what s ciphertext?
the coded message (encrypted)
61
New cards
what is cryptosystem/ cipher system?
a set of algorithms for performing cryptography actions (e.g. encryption, decryption, key generation)
62
New cards
what is cryptanalysis?
the study of how to crack encryption algorithms
63
New cards
why do we need cryptography in a computer?
Source and destination of messages can be known and protected
64
New cards
why do we need cryptography in a network of computers?
* No immediate and reliable way of determining the sender (machine or process) or the receiver
* No way of knowing if there is an eavesdropper
* No way of knowing if there is an eavesdropper
65
New cards
how are IP addresses used in a network?
used to identify senders and receivers of messages
* e.g. a request message arrives with a source IP address, a response messages is sent to this IP address
* identifying the receiver from an ip address alone is not secure, cannot tell if there is a middle man etc.
* e.g. a request message arrives with a source IP address, a response messages is sent to this IP address
* identifying the receiver from an ip address alone is not secure, cannot tell if there is a middle man etc.
66
New cards
what are the security weaknesses of IP addresses?
IP addresses can be spoofed
* Cannot reliably determine who has sent the request
* Cannot reliably determine who will receive the response
* Cannot reliably determine who has sent the request
* Cannot reliably determine who will receive the response
67
New cards
how does this IP address weakness affect the operating system?
If source IP addresses can not be trusted, difficult for operating system to
* decide whether to grant a request
* provide protection for a request or data when it cannot determine who will receive the response
* decide whether to grant a request
* provide protection for a request or data when it cannot determine who will receive the response
68
New cards
why is cryptography needed?
since no network is trusted, cryptography is used to eliminate the need to trust the network for secure communication
69
New cards
what does cryptography enable?
* a sender to encode its message so that only a computer with a certain key can decode the message
* a recipient of a message to verify that the message was created by some computer possessing a certain key
* a recipient of a message to verify that the message was created by some computer possessing a certain key
70
New cards
what are the components of an encryption algorithm
5 components
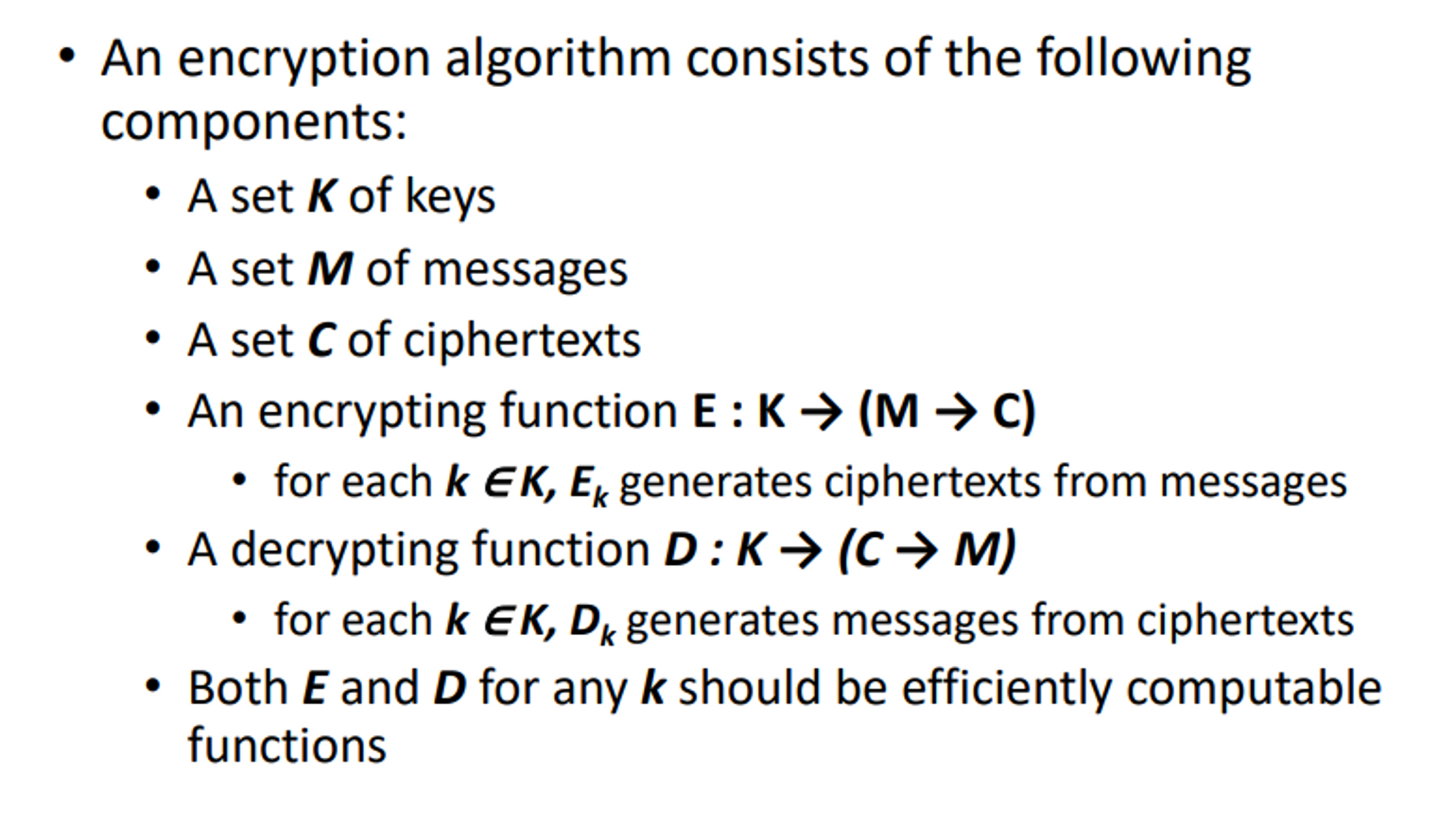
71
New cards
what essential property must the encryption algorithm provide?
explanation -
only the computer holding the key \[k\] can decrypt the plaintext from the ciphertext
only the computer holding the key \[k\] can decrypt the plaintext from the ciphertext
![explanation -
only the computer holding the key \[k\] can decrypt the plaintext from the ciphertext](https://knowt-user-attachments.s3.amazonaws.com/0250a88204a445ab8d6d1e0c3503b89b.jpeg)
72
New cards
what is important to consider when creating keys?
must be infeasible to derive a key \[k\] from the ciphertext \[c\] as c is exposed
73
New cards
what are the 2 main types of encryption algorithm
symmetric
asymmetric
asymmetric
74
New cards
what is symmetric encryption?
the same key is used to encrypt and decrypt a message
75
New cards
how are keys handled in symmetric encryption?
* the key \[k\] must be a shared secret - the key is kept between the 2 communicating entities only
* key exchange can happen directly between 2 parties or via a trusted third party called a certificate authority
* key exchange can happen directly between 2 parties or via a trusted third party called a certificate authority
76
New cards
what are examples of symmetric encryption algorithms?
block ciphers
stream ciphers
stream ciphers
77
New cards
what is a block cipher?
* works to encrypt a block of bits at a time.
* if the same key is used for encrypting an extended amount of data it becomes vulnerable to attack.
* can become slow when the communication to encrypt is too long
* if the same key is used for encrypting an extended amount of data it becomes vulnerable to attack.
* can become slow when the communication to encrypt is too long
78
New cards
what are examples of block ciphers?
@@DES@@ - data-encryption standard cipher
@@Triple DES@@
@@AES@@ - advances encryption standard cipher
@@Triple DES@@
@@AES@@ - advances encryption standard cipher
79
New cards
what is DES?
* used by @@NIST@@ - national institute of standards and technology
* takes a 64-bit value and a 56-bit key and performs transformations with substitution and permutation operations
* takes a 64-bit value and a 56-bit key and performs transformations with substitution and permutation operations
80
New cards
what is Triple DES?
* DES is insecure for applications so Triple DES created → DES algorithm repeated 3 times (2 encrypt, 1 decrypt) using 2 or 3 keys
81
New cards
what is AES?
* also a block cipher adopted by NIST
* more compact and efficient than DES
* more compact and efficient than DES
82
New cards
what is a stream cipher?
* designed to encrypt a stream of bits rather than a block.
* good for long communication lengths as block cipher would be too slow.
* a key is an input into a pseudo-random bit generator to generate random bits used to form a keystream
* good for long communication lengths as block cipher would be too slow.
* a key is an input into a pseudo-random bit generator to generate random bits used to form a keystream
83
New cards
what is a keystream?
infinite set of bits that encrypts a plaintext stream by XOR it with the plaintext
84
New cards
what is an example of a stream cipher?
@@RC4@@ - Rivest cipher 4
85
New cards
what is RC4?
* invented by Ron Rivest 1987
* considered insecure and has vulnerabilities
* considered insecure and has vulnerabilities
86
New cards
what is asymmetric encryption?
also called public key encryption
different keys are used for encryption and decryption
encryption key = public
decryption ket = private
different keys are used for encryption and decryption
encryption key = public
decryption ket = private
87
New cards
how are keys handled in asymmetric encryption?
1. the person who receives the encrypted message will generate a pair of private-public keys
2. public key is available to everyone meaning anyone can encrypt messages
3. private key is available to the private key holder meaning only they can decrypt the messages
88
New cards
what is an example of an asymmetrical encryption algorithm?
@@RSA@@
89
New cards
what is RSA?
* most widely used encryption algorithm based on the difficulty of the factorisation of the product of two large prime numbers
* relatively slow algorithm and often used for exchanging encrypted shared keys for symmetric key cryptography
\
1. A user creates and publishes a public key based on two large prime numbers and an auxiliary value
2. Anyone (any sender) can use the public key to encrypt a message
3. The prime numbers must be kept secret – if the public key is large enough, only knowing the prime numbers enables decoding the message feasibly
* relatively slow algorithm and often used for exchanging encrypted shared keys for symmetric key cryptography
\
1. A user creates and publishes a public key based on two large prime numbers and an auxiliary value
2. Anyone (any sender) can use the public key to encrypt a message
3. The prime numbers must be kept secret – if the public key is large enough, only knowing the prime numbers enables decoding the message feasibly
90
New cards
how does asymmetric encryption compare to symmetric encryption?
Asymmetric is more computationally expensive to execute as it’s easier to encode and decode with symmetrical keys
91
New cards
when is asymmetric encryption best used?
* Asymmetric is not good for general-purpose encryption of large amounts of data
* Best used for encrypting small amounts of data, authentication, confidentiality, key distribution
* Best used for encrypting small amounts of data, authentication, confidentiality, key distribution