GCSE Computer Science (OCR)
1/245
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
246 Terms
Arithmetic Logic Unit (ALU)
Performs operations on data e.g. Addition, subtraction
Control Unit (CU)
Coordinating activities of the CPU
Registers
Quick, small stores of data within the CPU
Memory Address Register (MAR)
Holds memory address for data or a instruction about to be used by the CPU
Memory Data Register (MDR)
Holds actual data or instruction
Accumulator
Stores results of calculations in the ALU
Program Counter (PC)
Holds memory address of the instruction for each cycle
Fetch
The next instruction is retrieved by CPU from main memory
Decode
The instruction is broken down and decided so computer can understand
Execute
The CPU performs what the instructions told
Embedded System
A computer system built within a large device e.g. Camera, washer, car
Volatile
Memory loses its data when power of
Non-volatile
Memory retains its data when power is lost
Random Access Memory (RAM)
Read/write - function is to load open programs and operating system data currently in use - volatile
Read Only Memory (ROM)
Can only be read, can't be changed, stores essential programs to be run in order to boot the computer - non-volatile
Cache
A type memory that stores copies of frequently used data, much faster than RAM, lower capacity - closer to CPU
Buses
Collection of wires that carry signals between various components of the computer system
Central Processing Unit (CPU)
Processes all of the data and instructions that make the system work - can be effected by clock speed, number of cores, cache size
Clock speed
How fast the computer does the FDE cycle
virtual memory
A memory management procedure needed when the RAM is full so a temporary section is made which acts like a part of RAM
Flash memory
Solid state storage, non-volatile, more reliable/durable but can only be overwritten a limited number of times
Graphics Processing Unit (GPU)
Handles graphics and image processing
Optical storage
CD, DVD, Blue-ray
ADV: cheap,easy to transport
DIS: slow, less storage than hard drives, stored data degrades over time, cannot be written over
Magnetic storage
Hard drives
ADV: fast access, stores large amounts of data, low cost
DIS: not very portable, easily be broken
Solid State storage
USB, flash memory, SD
ADV: fast, small, light, easily potable, quiet
DIS: more expensive, storage capacity less, limited number erase/write cycles
Cloud stotage
Data is stored on multiple servers in a remote location
ADV: secure, can be accessed anywhere, no need to buy
DIS: needs internet, download and upload can be effected by internet connection, less control if data is held
Operating System
essential software that links the hardware and other software together and generally manages the computer system
Command-line Interface
Text commands where user has to type in command
Graphical User Interface (GUI)
uses icons and other visual indicators to navigate and issue commands
Utility Software
maintains a computer
Defragmentation Software
reorganises data on the hard drive to put fragmented files back together and moves files to collect all the free space
Backup Software
Full Backup - a copy is taken from from every file on the system
Incremental Backup - only files created or edited since last backup are copied
Compression Software
reduces file size so they take up less space on hard disk
Encryption Software
scrambles data to stop others from accessing it
Open Source Software
source code is made freely available and users can modify it
ADV: free, ,made for greater good, can be adapted
DIS: small, buggy, security holes, no warranties, no customer support
Proprietary Software
only the compiled code is released and the source code is kept a secret
ADV: warranties, well-tested, reliable, cheaper
DIS: expensive, software may not fit user needs
Personal Area Network (PAN)
within the range of an individual person
Local Area Network (LAN)
a network that connects devices close to each other e.g. school, house
Wide Area Network (WAN)
a network within a large geographical area e.g. internet
Bandwidth
amount of data that can be transferred in a given time
Network Interface Card (NIC)
allow a device to connect to a network
Switch
connect devices on a LAN
Router
responsible for transmitting data between networks
Ethernet
a set of standards for connecting computers
Client-server Network
client has connection to server, servers can backup and store centrally but can be expensive and difficult to maintain
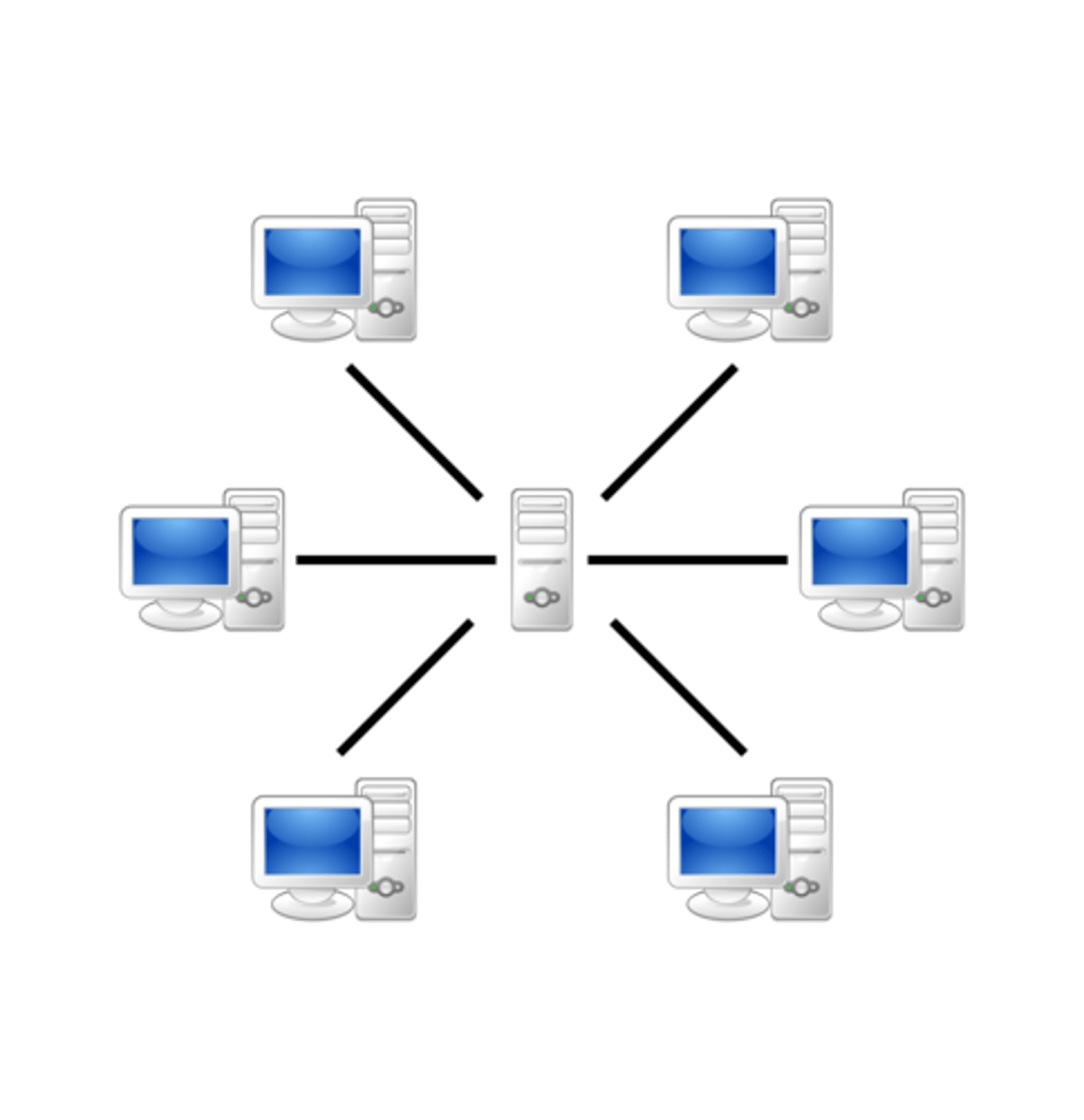
Peer-to-peer Network
no central server, each computer equal in responsibility, have to work as both server and a client.
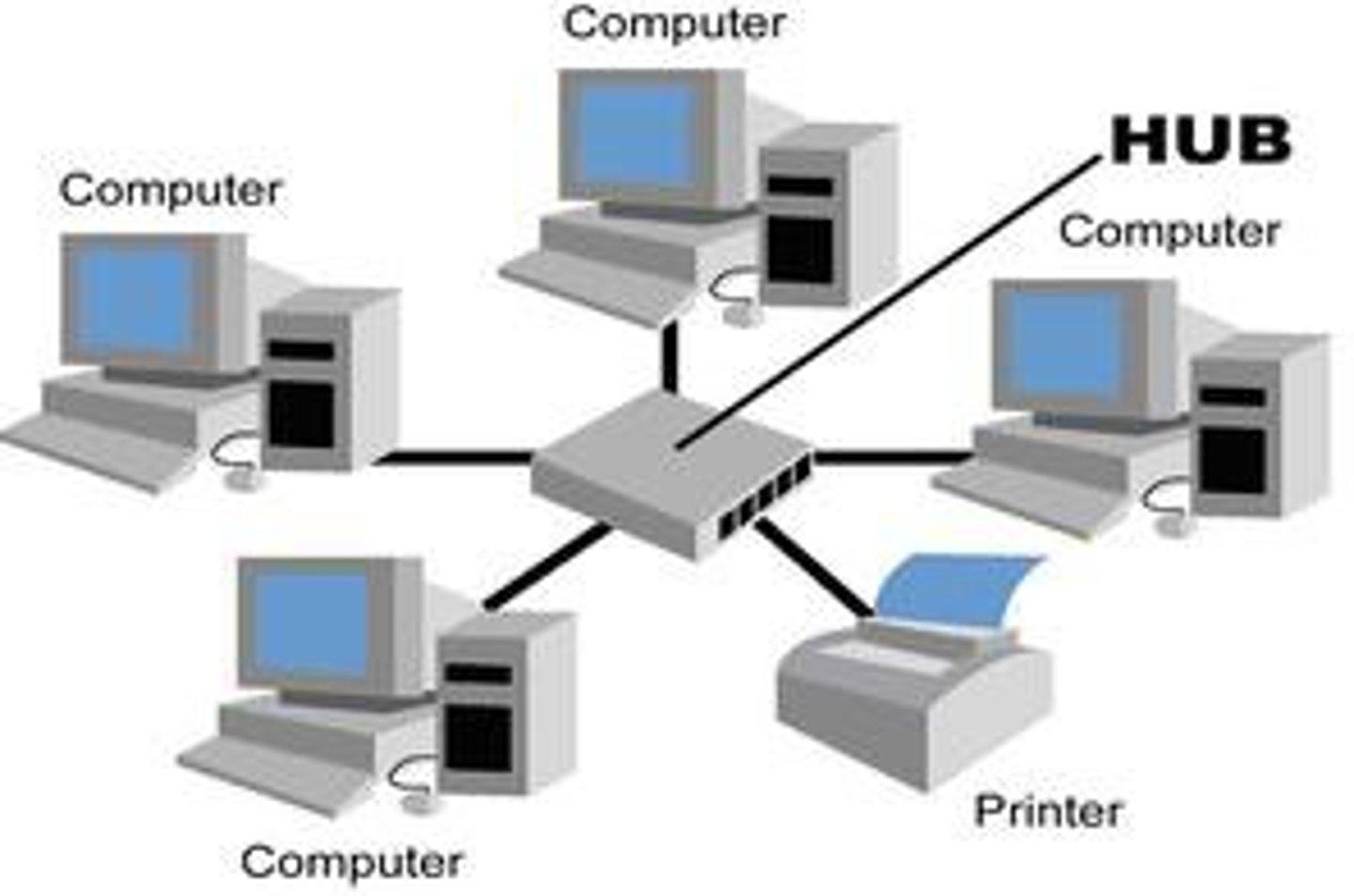
Star Topology
ADV: better performance, rest of network not affected in one fails, simple to add more devices
DIS: wire needed for all devices, expensive
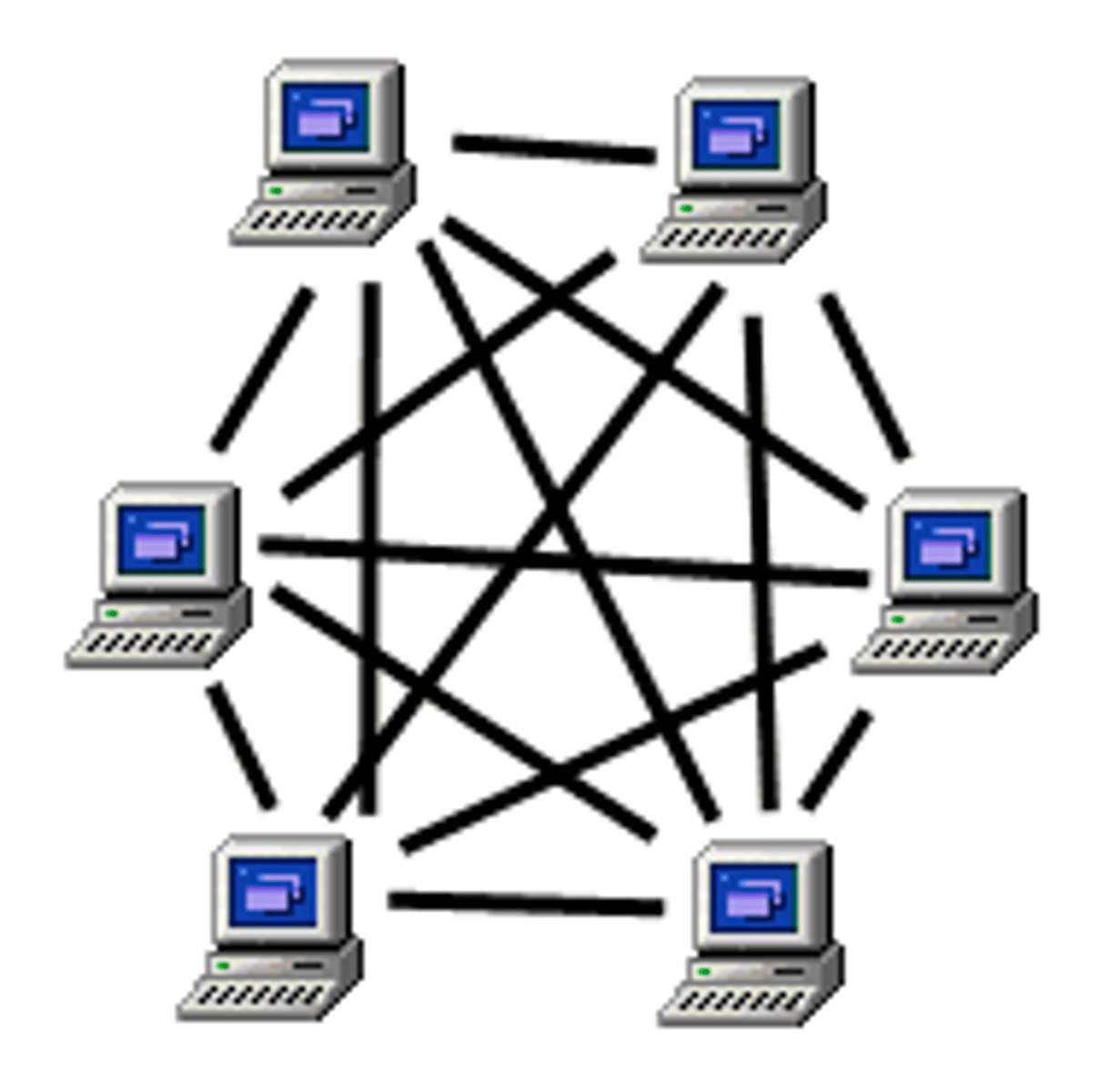
Mesh Topology
ADV: faster
DIS: expensive
MAC Address
assigned to all devices, unique to all devises and cannot be changed, permanent, identifies the actual device.
IP Adress
assigned either manually or automatic, the location of your device on the internet
Packet Switching
split data into packets to be sent across the network, each packet given a number order of data, each router reads packet header and decides which way to send it according to IP rules, packets then arrive and reassemble them in the right order.
TCP/IP
sets of rules for how devices connect on the network.
Hyper Text Transfer Protocol (HTTP)
used to access websites and communicate with web servers
HTTPS
more secure - encryption
File Transfer Protocol (FTP)
used to access, edit and move files between devices
Post Office Protocol (POP3)
used to retrieve emails from a server, holds until download - then deletes from server
Internet Message Access (IMAP)
used to retrieve emails, server holds until you actually delete it- only download a copy
Simple Mail Transfer Protocol (SMTP)
used to send emails, used to transfer emails between servers
Layer
ADV: manageable pieces, self-contained can change without effecting others
Application Layer
turning data into websites
Transport Layer
controlling data flow - splitting data into packets
Network Layer
making connections between networks
Data link Layer
passing data over physical network-
Domain Name Server (DNS)
translates websites' domain name into its IP address
Virtual Network
network that is entirely software based, created by partitioning of some physical network
Blagging
invented scenario to engage a targeted victim in a manner that increases the chance the victim will divulge information
Phishing
used to gain personal information for purposes of identity theft, using fraudulent e-mail messages that appear to come from legitimate businesses.
Shouldering
used to obtain information such as personal identification numbers (PINs), passwords and other confidential data by looking over the victim's shoulder.
Malware
malicious software - computer programs designed to infiltrate and damage computers without the users consent.
Virus
program loaded onto a user's computer without the user's knowledge and performs malicious actions. It can self-replicate, inserting itself onto other programs or files, infecting them in the process.
Worm
program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it.
Trojan Horse
program which misleads users of its true intent.
Spyware
aims to gather information about a person or organization without their knowledge
Adware
unwanted advertisements to the user of a computer
Brute Force Attack
trail and error to gain information
Denial of Service Attack (DOS)
hacker stop users from accessing a part of a network, flooding network with useless traffic making computer very slow
Data Interception And Theft
The unauthorized taking or interception of computer-based information. Data theft is the act of stealing computer-based information from an unknowing victim with the intent of compromising privacy or obtaining confidential information.
SQL Injection
programming language used to search and query databases.
Zero-day Attack
before software is released it is tested as much as possible
Penetration Testing
organisations employ specialists to stimulate potential attacks on their network
Anti-malware Software
designed to find and stop malware from damaging a network
Encryption
data is translated into code which only someone with the correct key can access
Data Protection Act
your data should be protected and kept safe from hackers
Freedom of Information Act
allows members of the public to access information held by a public organisation
Computer Misuse Act
stop hacking and cyber crime - stop unauthorized access to private network
Copyright Act
protect intellectual property - anything someone has created
alphanumeric
collective name for letters, digits, symbols
analogue signal
a continuous signal which can't be processed by a computer
argument
a value that a parameter of a subprogram actually takes
ALU
part of CPU that carries out arithmetic and Boolean operations
array
data structure where all data is stored and defined under one variable name
ASCII
A 7-bit character set consisting of 128 characters
assembler
a program that turns assembly language into machine code
assembly language
low-level langauge
authentication
a process for checking user identity
binary
a counting system using base-2 consisting of 0s and 1s
binary shift
moving the bits in a binary number left or right and filling gaps with 0s
BIOS
Basic Input Output System
bitmap image
a graphic made up of pixels
bit
a binary digit either 0 or 1