2.2 Other Social Engineering Attacks
1/3
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
4 Terms
Misinformation/Disinformation
Are social engineering techniques used to spread factually incorrect information to confuse, divide, or manipulate groups of people. Unlike differences of opinion, these tactics involve deliberately false details.
Influence campaigns are often orchestrated by governments or nation-states, aim to sway public opinion on political or social issues. These campaigns can distract from damaging truths or convince people to believe false narratives.
Social media platforms are often used as powerful tools for disseminating misinformation, where creating, sharing, and amplifying content can significantly influence public perception.
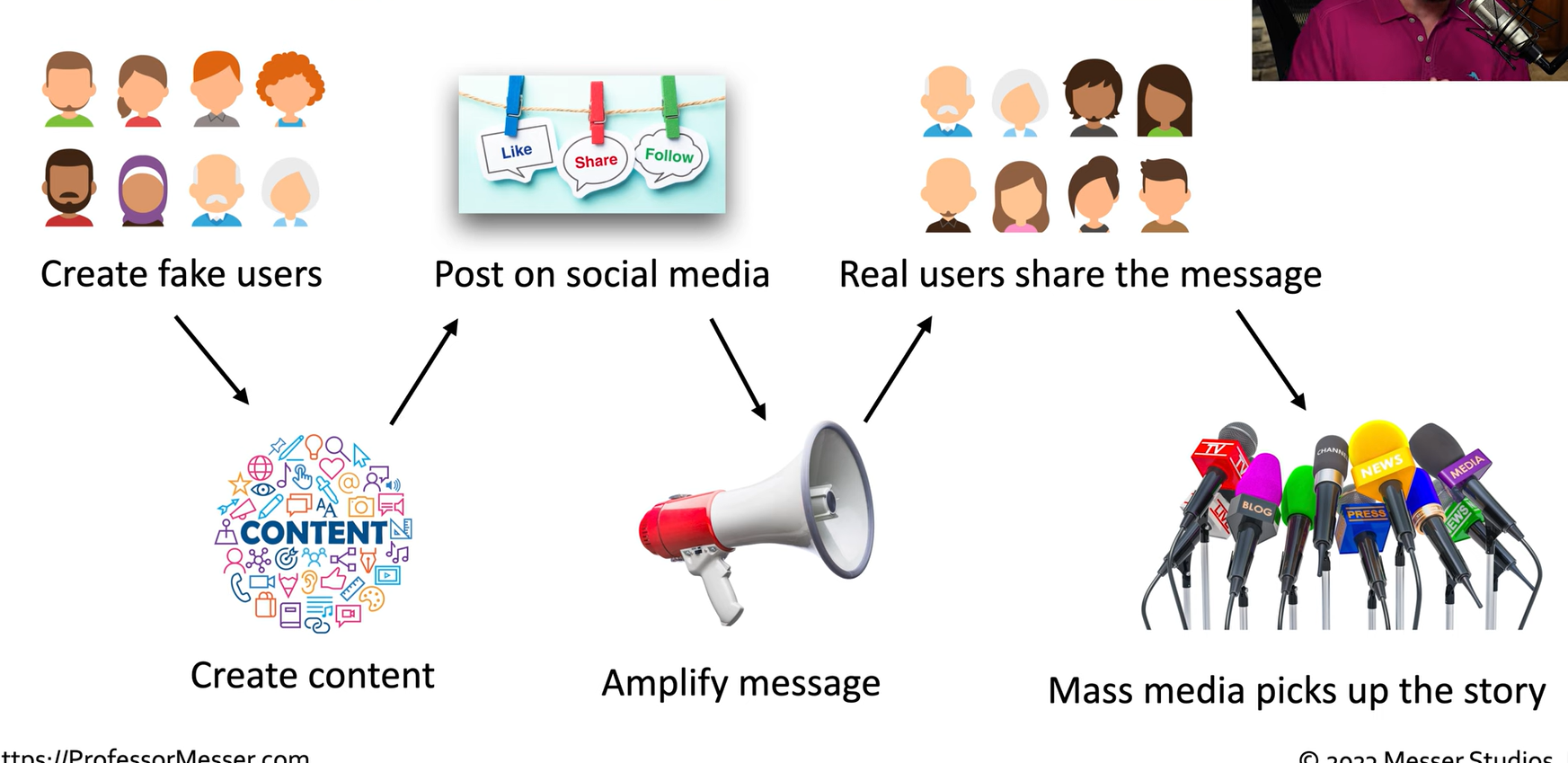
How It Starts
Begins with the attacker creating fake user accounts on social media, which are not real people but controlled by the attacker.
Using one of these fake accounts, the attacker posts misleading or false content.
Social media platforms provide options like "like," "share," or "follow," which allow the attacker to amplify the message.
As the post gains likes and shares, social media algorithms recognize its popularity and show it to more users, leading to further sharing.
Once the misinformation spreads widely enough, mass media may pick up on it, inadvertently promoting a false narrative that originated with the attacker.
Brand Impersonation
Attackers pretending to be well-known brands, like Coca-Cola, McDonald's, or Apple.
Create fake/similar sites
These sites are designed to get indexed by search engines like Google, often tricking users into clicking on ads or receiving messages through platforms like WhatsApp.
Once visitors are on the site, they are typically presented with pop-ups claiming they've won a special offer, prompting them to download a video.
Common method for spreading malware, and it often leads to infections, data exfiltration, or tracking through malicious ads on the site.
Fries
Fries