Ch 12 - Managing information security and privacy
1/42
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
43 Terms
Identity theft
Vital information is stolen to create a new identity
Can be done with a persons name, address, date of birth, social insurance number, and mothers maiden name
Can take over a victims financial accounts, open new bank accounts, transfer bank balances, apply for loans, credit cards, and other services
Personal information protection and electronic documents act (PIPEDA)
An act intended to balance an individuals right to the privacy of their personal information, which organizations need to collect, use, or share for business purposes
The privacy commissioner of Canada oversees this act
Governs how data is collected and used
Suggests that organizations should not be able to use the information collected for any purpose other than what the organization agreed to use it for
Suggests that it is the duty of an organization to protect the information they collect
Individuals have the right to know what type of information an organization collects about them and how that information is going to be used
3 sources of security threats in organizations
Human errors and mistakes
Malicious human activity
Natural events and disasters
Human errors and mistakes in security threats
Includes:
Accidental problems: employee accidentally deleting a customers records, employee drives truck through the wall of a computer room
Poorly written programs
Poorly designed procedures
Physical accidents
Malicious human activity in security threats
Includes:
Intentional destruction of data: destroying system components
Hackers
Virus and worm writers
People who send unwanted emails (spam)
Criminals
Terrorists
Natural events and disasters in security threats
Includes:
Fires, floods, hurricanes, etc
Can result in losses of capability and service, and losses from recovery actions
5 types of security problems
Unauthorized data disclosure
Incorrect data modification
Faulty service
Denial of service
Loss of infrastructure
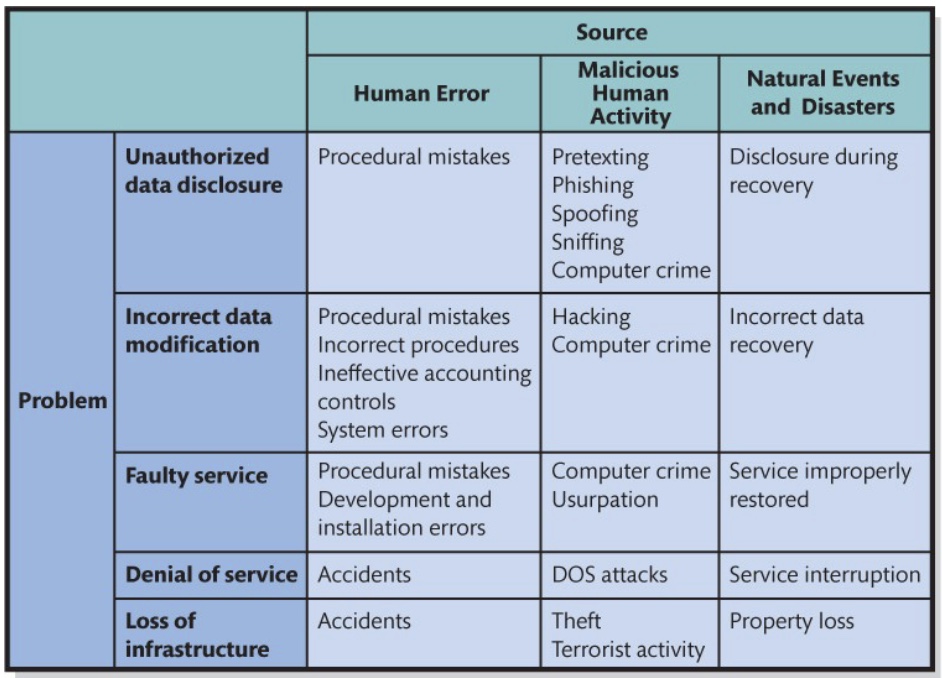
Unauthorized data disclosure
Human errors:
Posting private information in a public place
Placing restricted information on a searchable website
Inadvertent disclosure
Malicious release:
Includes Pretexting: deceiving someone by pretending to be someone else
Phishing: using email to get a user to click on link
Spoofing: spoofing IP addresses or domain names
Sniffing (intercepting): intercepting network communications, such as using unprotected wifi networks
Ransomware: malicious software that encrypts data and renders it useless unless a ransom payment is made
Incorrect data modification
Caused by human errors:
Incorrect entries and information
Procedural problems
Systems errors
Hacking: occurs when a person gains unauthorized access to a computer system
Faulty service
Includes incorrect system operation
procedural mistake
incorrect system development
Denial of service (DOS)
Can result from:
Human error
Denial-of-service attacks
Natural disasters
Loss of infrastructure
Can result from:
Accidents
Theft
Terrorism
Natural disasters
Elements of a security program
Senior management involvement: must establish a security policy, must manage risk by balancing costs and benefits
Safeguards: put in place as protections against security threats
Incident response: planning prior to accidents
Security safeguards relating to 5 components of IS
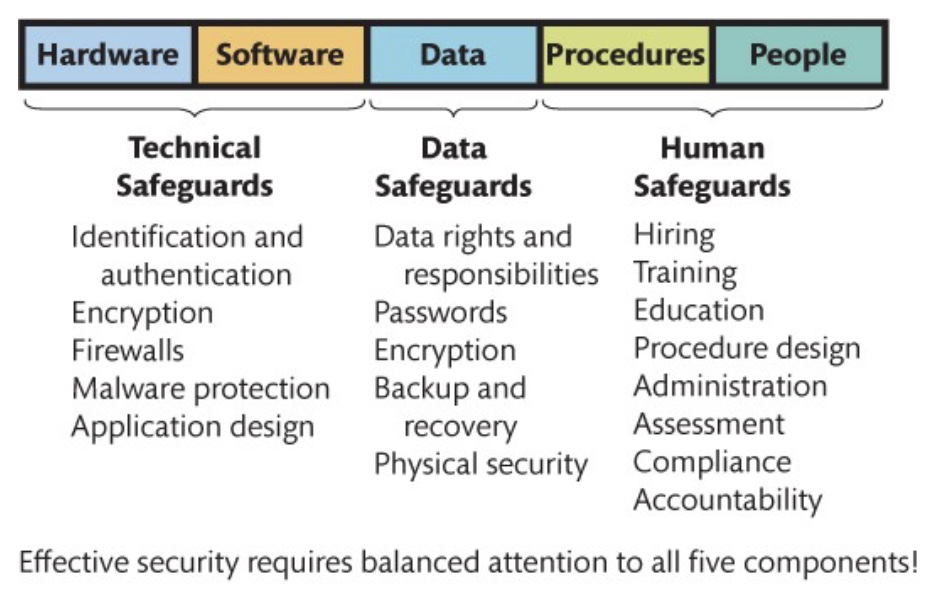
Technical safeguards
Involve the hardware and software components of an information system
Examples:
Identification and authentication: passwords, smart cards (PIN numbers), biometric authentication (fingerprints, etc), single sign-on for multiple systems
Encryption
Firewalls
Malware protection against viruses, worms, spyware and adware (what causes slow performance, pop-up ads, etc)
Protection against malware (safeguards)
Install antivirus and antispyware programs
Scan your computer frequently
Update malware definitions (patterns that exist in malware)
Open email attachments only from known sources
Install software updates
Browse only reputable websites
Data safeguards
Protects databases and other organizational data
Methods:
Encryption
Backup copies (store off premise, checking validity - practicing recovery)
Physical security (locking and controlling access to facility, maintaining entry log for resources)
Third party contracts (safeguards written into contracts, right to inspect premesis and interview personnel)
Data administration
An organization-wide function that includes developing data policies and enforcing data standards
Database administration
A database function for each database that includes:
Procedures for multi-user prosessing (many users may access or update data at the same time, which can lead to lost updates, inconsistent reads, etc.)
Change control to structure (reviewing proposed changes, approving and documenting changes, etc)
Protection of database
Human safeguards
Measures involving people and the procedure components of information system to help protect the security of the system and data
Focus on how individuals interact with the systems and what procedures guide that interaction
Includes users, employees, contractors, and anyone interacting with the system
Human safeguards for employees
Includes:
User accounts
Hiring and training
Policy enforcement
Employee termination procedures
User accounts for employee safeguards
Defines job roles clearly to determine access needs
Separates duties to avoid fraud or error
Apply least privilege principle: give only the access necessary for the job
Notes if the job involves high security sensitivity and documents it
Hiring anf training for employee safeguards
Screens employees during hiring to ensure trustworthiness
Trains employees on security policies and potential risks (ex: phishing awareness)
Policy enforcement for employee safeguards
Clearly assigns responsibility for protecting information
Holds employees accountable for violations
Management must set a strong tone at the top by taking security seriously
Employee termination procedures for employee safeguards
If hostile termination, act quickly to disable accounts and access
Prevents sabotage or theft by ensuring exit protocols are followed
Human safeguards for non employees
Includes:
Temporary personnel and vendors
Public users
Partners and external users
Temporary personnel and vendors safeguards (non-employees)
Screen and train them, just like employees
Contracts should include clauses about data protection and compliance
Assign temporary accounts with the least privileges required
Public user safeguards (non employees)
Secure your website and services through “hardening”
Hardening: reducing vulnerabilities by removing unnecessary features, patching software, and limiting access
Partner and external user safeguards (non employees)
Ensure that external parties (customers or business parties) are not affected by internal security issues
Internal breaches shouldnt put external data or systems at risk
Account administration
Management of user access to systems, ensuring that only authorized individuals can use the system and that their access is controlled, monitored, and removed when no longer needed.
Includes:
Account administration procedures
Password management
Help-desk policies
System procedures
Standardized procedures
Account administration procedures
Create new user accounts securely when someone joins the organization
Modify account permissions when job roles change (such as a promotion or department transfer)
Remove unneeded accounts immediately to prevent unauthorized access
Password management in account administration
Users should sign acknowledgment forms agreeing to protect passwords
Requires frequent password changes to reduce the risk of misuse or guessing
Help desk policies in account administration
Help desks must authenticate users who claim they’ve lost or forgotten passwords (ex: security questions, ID verification).
Never email passwords directly, only send a notification that a password was changed. Passwords should be reset through a secure process.
System procedures in account administration
Define procedures for:
Normal operations: How the system runs day-to-day.
Backup: How and when data is saved to prevent loss.
Recovery: Steps to restore operations after system failure or breach.
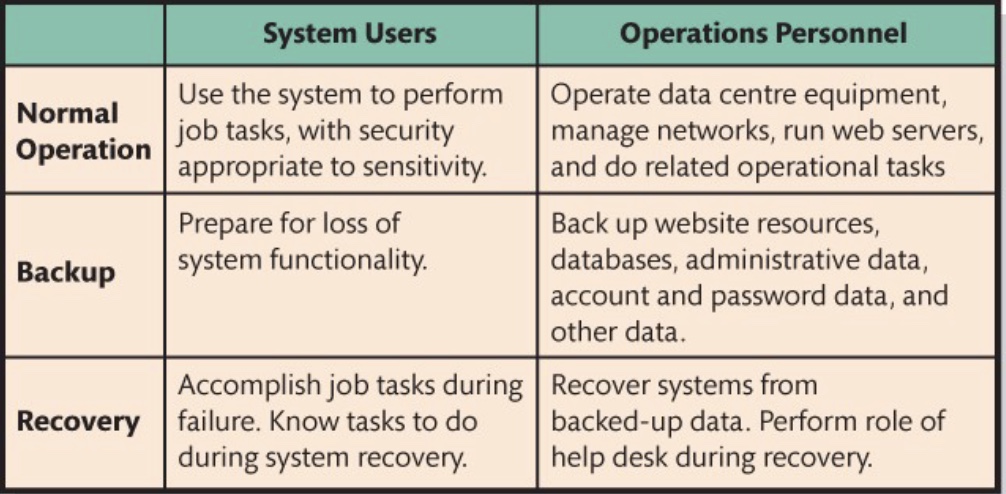
Standardized procedures in account administration
Each information system should have clear procedures for:
Account creation and removal
Backup and recovery
Normal use
Standardization reduces errors and makes it harder for internal threats or external attackers to exploit inconsistencies
Define separate procedures for system users (regular employees) - focus on access to tools/data, and for operations personnel (IT staff) - focus on managing systems and infrastructure
Security monitoring
The ongoing process of tracking, analyzing, and responding to system activity to detect and prevent unauthorized access, data breaches, or system failures.
Maintains confidentiality, integrity, and availability of IS
Components of security analysis
Activity log analysis
Security testing
Investigation of incidents
Lessons learned
Activity log analysis in security analysis
Organizations collect and analyze logs from various sources to monitor system behaviour:
Firewall logs: show incoming and outgoing traffic, helping detect unauthorized access attempts or malware communications
Database management systems (DBMS) log-in records: Track who accessed the database, when, and whether the access was successful or denied, useful for identifying suspicious activity.
Web server logs: Records details about website visitors, including IP addresses, pages accessed, and error messages, useful for spotting hacking attempts or bot traffic.
Security testing in security analysis
Conducted by in-house security teams or external cybersecurity professionals
Includes:
Penetration testing (simulating attacks to find weaknesses)
Vulnerability scans
Code audits or social engineering tests
Helps find and fix weaknesses before they are exploited
Investigation of incidents in security analysis
When a security incident happens (ex: unauthorized access, data breach, system crash), it’s important to investigate
Must determine the root cause:
Was it a phishing email?
A weak password?
An outdated system vulnerability?
This helps prevent recurrence by identifying the exact method attackers used.
Lessons learned in security analysis
After an incident or test, organizations should:
Document what happened.
Identify what went wrong, and what was handled well.
Use the findings to:
Fix vulnerabilities
Update policies, training, or technical controls
Improve response procedures for the future
Disaster predparedness
Should be prepared for a substantial loss of computing infrastructure caused by acts of nature, crime, or terrorist activity
The best safeguard is an appropriate location
Backup data centres should be in a geographically removed site
Identify mission-critical systems and resources needed to run those systems
Prepare remote backup facilities
Train and rehearse cutover of operations (if you had to cut over to new operations)
How should organizations respond to security incidents?
Organizations must have a plan (detailed reporting and response)
Centralized reporting of incidents (allows for application of specialized expertise)
Speed is of the essence
Preparation pays off (identify critical employees and contact numbers, training is vital)
Practice indidence response