Networking Essentials Lesson 9: Explaining Transport Layer Protocols
1/26
Earn XP
Description and Tags
Explaining transport layer protocols
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
27 Terms
Transport Layer Ports and Connections
Port numbers 0 through 1,023 are preassigned by the Internet Assigned Numbers Authority (IANA) to "well-known" server applications.
Other server applications have been registered in the port range 1,024 through 49,151.
The remaining ports (up to 65,535) are designated for private or dynamic use. As well as the server application needing a port, each client application must assign its own port number to track its requests.
Client ports are also referred to as ephemeral ports or source ports.
Identify individual applications as port numbers
Writes left to right
Can show label (HTTP) or port number (port 80) in logs. Depends on what you’re looking for and software
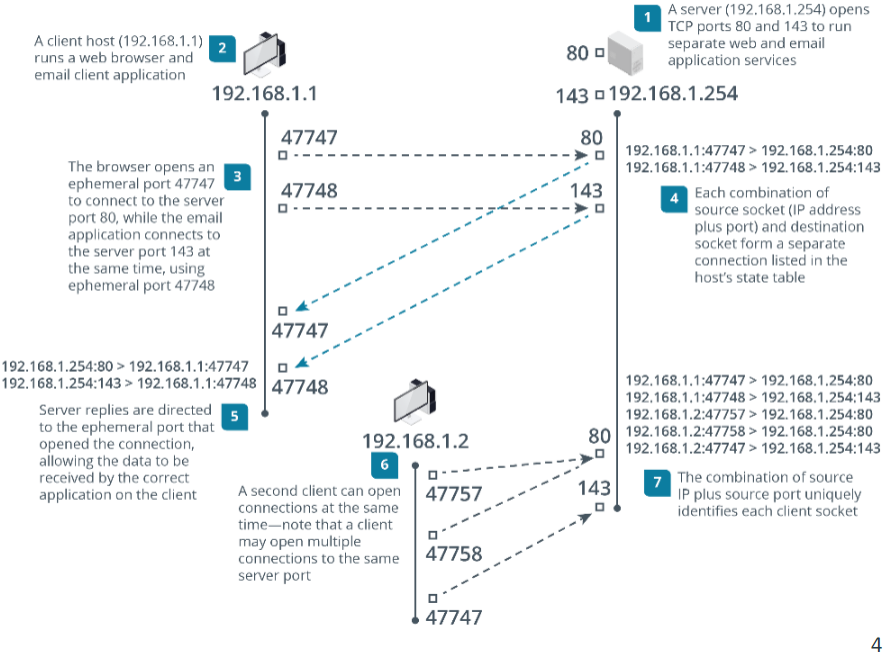
Socket
Source IP + port bound to software process
A client socket can form a connection with a server socket to exchange data.
Connection
Client IP and port connected to server IP and port
A connection is formed when a client socket requests a service from the server socket.
A connection is uniquely identified by the combination of server port and IP address and client port and IP address.
A server socket can therefore support multiple connections from a number of client sockets.
Transmission Control Protocol (TCP)
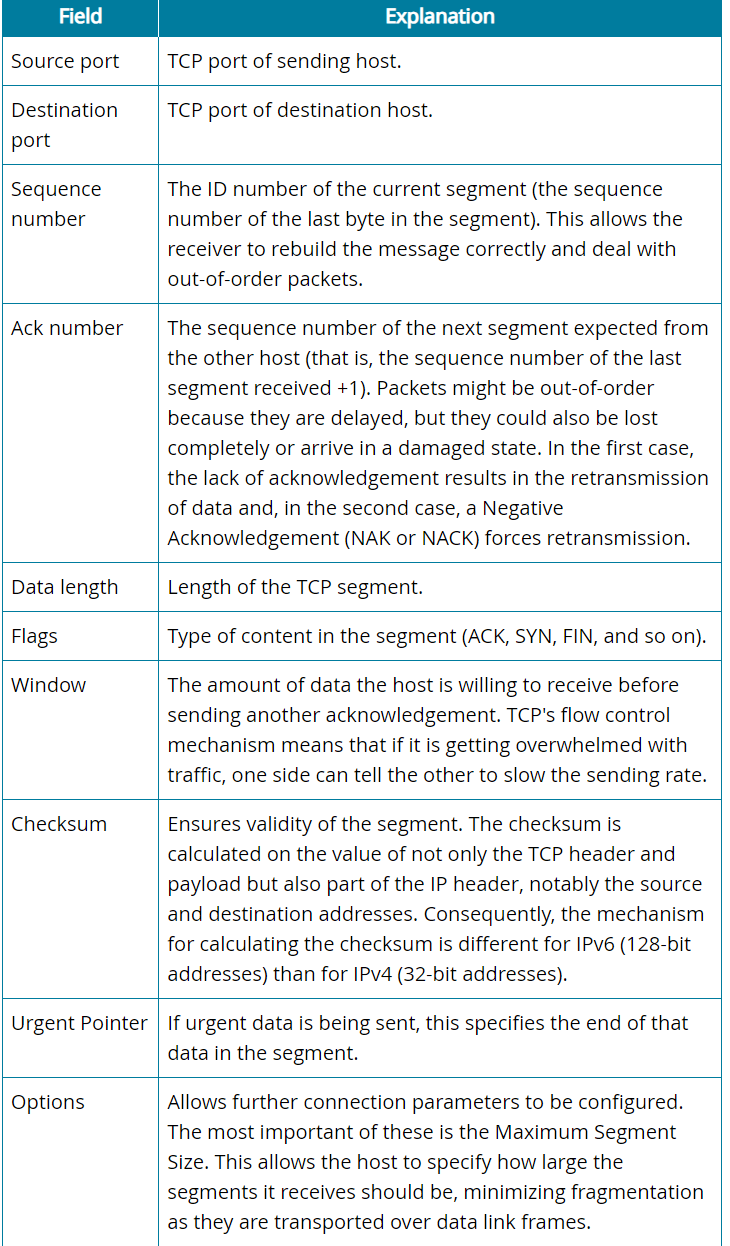
The Transmission Control Protocol (TCP) works at the Transport layer to provide connection-oriented, guaranteed communication using acknowledgements to ensure that delivery has occurred.
If packets are missing, they can be retransmitted.
TCP can be used for unicast transmission only.
Connection-oriented, guaranteed delivery
Segments with header fields to track sequence and acknowledgements
The use of sequencing, acknowledgments, and retransmissions means that TCP requires numerous header fields to maintain state information.
TCP Handshake and Teardown
Three-way handshake
Client SYN
Client sends synchronous pack
Server SYN/ACK
Server sends acknowledgement of that packet like “Hey I’m going speed 10 and you’re going speed 100 can u slow down plz”
Client ACK
Client says “Okay u can meet me at 10? I agree”
Can also compromise with 10, 20, as 15
Graceful teardown
FIN (finish)
ACK (acknowledgement)
Session termination
RST (reset)
Like “let me call u back” if the phone is breaking up
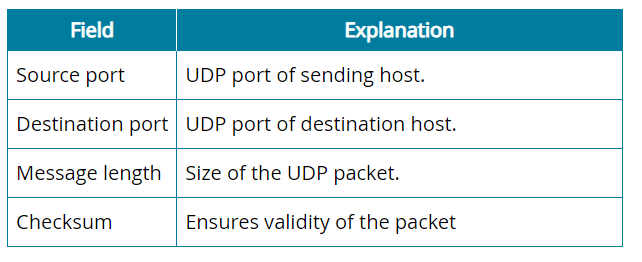
User Datagram Protocol (UDP)
Connectionless, non-guaranteed communication
Ex. letting a video buffer before it plays, going back 5 seconds, etc
Fewer header fields required
Used by protocols that can tolerate lost or out-of-order packets
A cellphone- you can ask someone to repeat themselves
Good for sending small amounts of data. Doesn’t require acknowledgement either (wish that were me)
The header size is 8 bytes, compared to 20 bytes (or more) for TCP.
Common TCP and UDP Ports
yuh
How many port numbers are required to establish a connection at the Transport layer?
Two-a server port and a client port.
What is the purpose of the window field in a TCP segment?
It is used for flow control. The window indicates the amount of data that the host can receive before sending another acknowledgement.
What are the sizes of TCP and UDP headers?
TCP is 20 bytes (or more) while UDP is 8 bytes.
True or False? User Datagram Protocol (UDP), like TCP, uses flow control in the sending of data packets.
False.
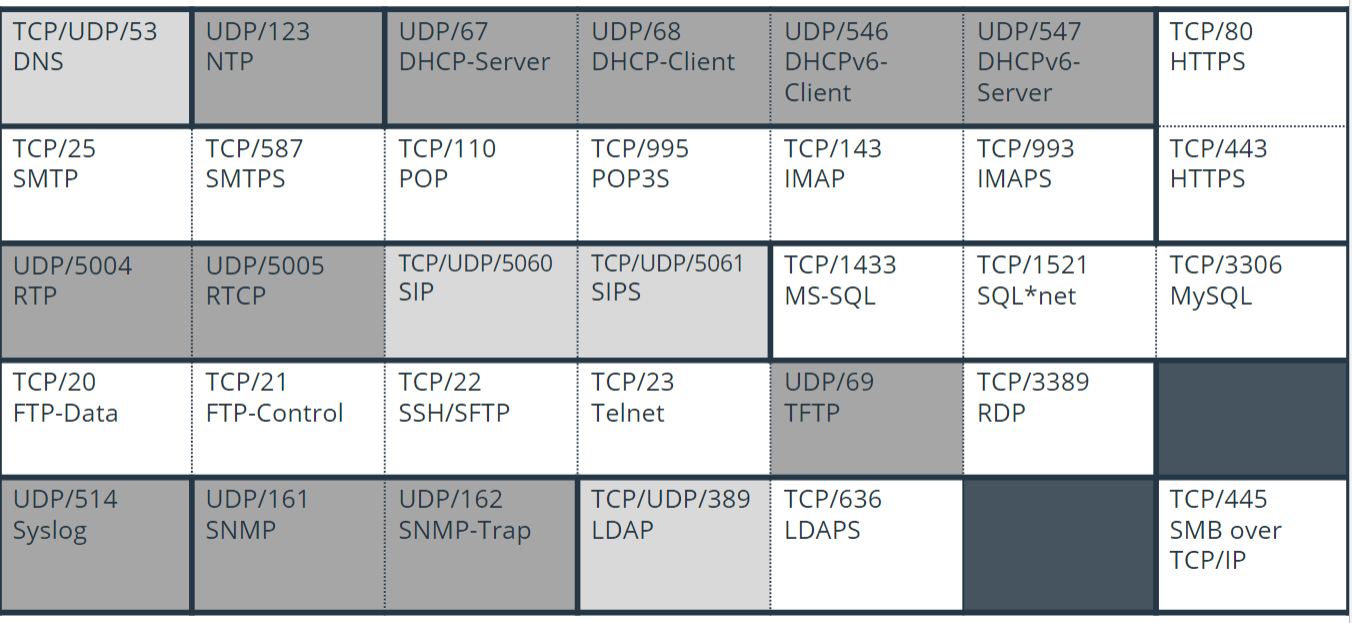
What port and protocol does TFTP use at the Transport layer?
UDP/69.
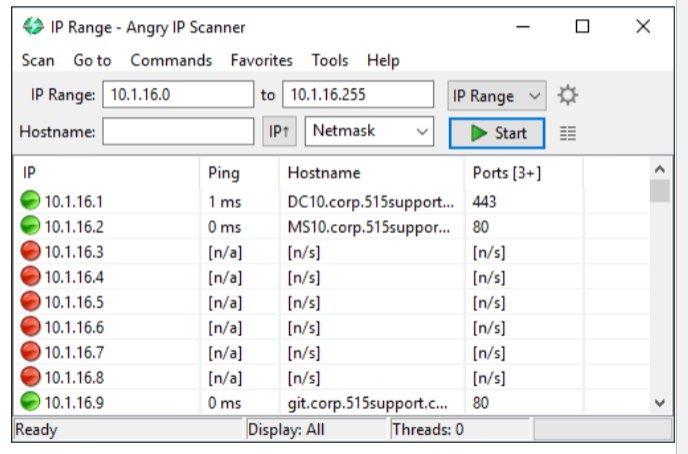
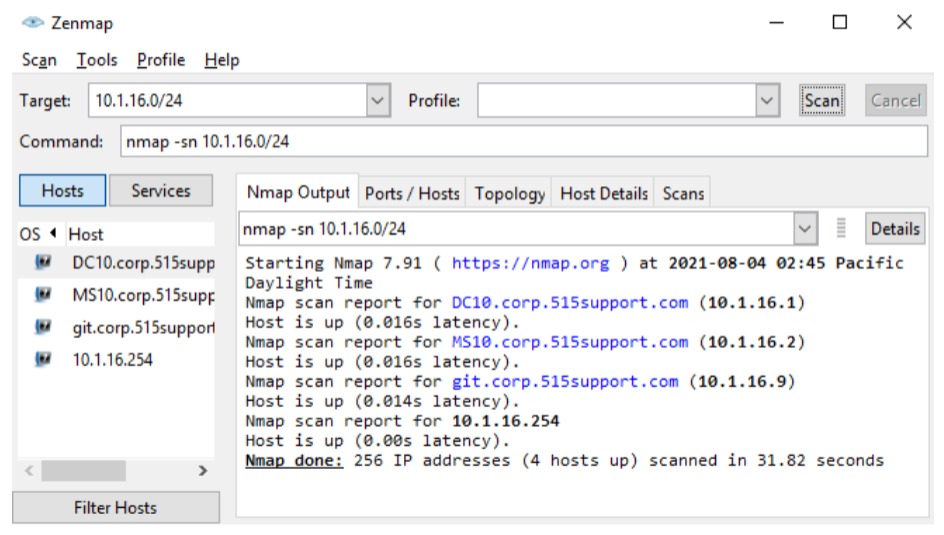
IP Scanners
Perform host and topology discovery to maximize network visibility
Standalone tools
u download the tool and. “if you don’t own this range you shouldn’t be scanning this bc it could be malicious”
IP Address Management (IPAM)
Determining “up” status
ping, arp, traceroute
Simple Network Management Protocol (SNMP)
Query DHCP/DNS
Nmap
Network management tool
Server, client, what ports are open, etc
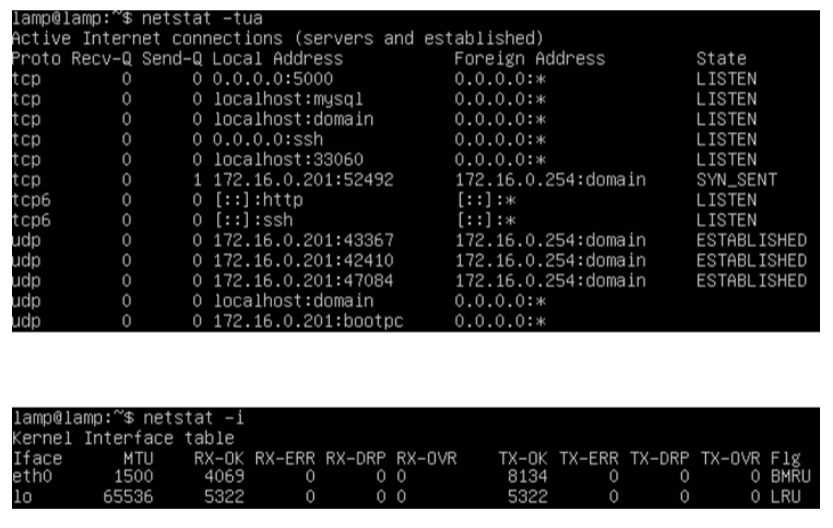
netstat
means “network statistics”
Report local port status
TCP vs. UDP
80% TCP if secure, like a bank
If it’s multimedia 80% UPD, like video games and videos bc u need less security
Local IP and port
Remote IP and port
State (Listening, Established,…)
Listening: Open and waiting for someone to talk to me
Established: I’m actually talking to someone and working with someone!
If u get hit with virus, why are you listening on port 80 or 21 and 20? we’re not a web server of an ftp server!
Established IS NO GOOD. THAT’S BAD they are IN YOUR HOUSE
Options
Skip name resolution, show process, report statistics, …
Windows vs. Linux syntax differences
iproute2 ss and nstat commands replace netstat
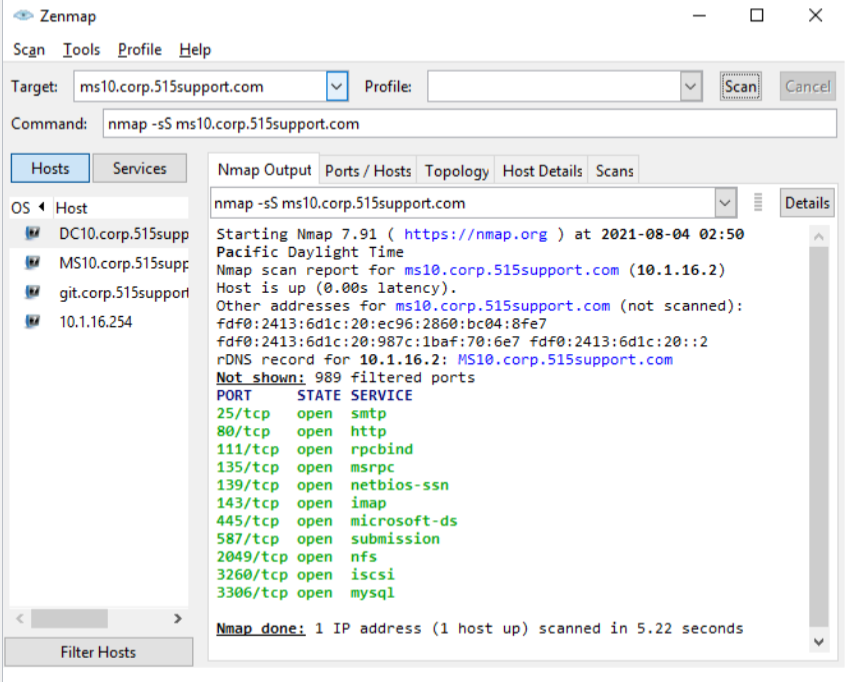
Remote Port Scanners
Report port status from a remote host
Scan types
Half-open, full connect, UDP, port range, …
Open: Responding back
Closed: Don’t bother me go home
Filtered: we don’t know if it’s opened or closed bc of the filter… there’s a curtain in front of the door… is it open??? is it locked…??
Host and service fingerprinting
This is windows 10, or this is whatever (specific)
Protocol Analyzers
Decode frames captured by sniffer
Live capture or saved capture file (pcap)
Parse header fields to reveal packet metadata
IPv4 most commonly
Reconstruct TCP streams
Analyze traffic statistics
Per-host utilization
“Who’s the most talkative machine? If that’s not a server, and it’s a client, and it’s talking a lot, it might be compromised!”
Someone backs up to the cloud a whole gig? That’s most talkative
Per-protocol utilization
VoIP? Web traffic? Mail? Who is the most talkative?!?!
What type of scanning tool outputs a "Host is up" status report.
IP scanner.
Note that while most IP scanners can also function as port scanners they are distinct types of scanning activity.
You are auditing the service configuration of a Linux server. Which command can you use to check the PID associated with a TCP port, even if there are no active connections?
Run netstat with the -p switch to show the process ID (PID).
-a switch to show all active and listening sockets
optionally -t to filter by TCP
-n to suppress name resolution and display output quicker:
netstat -patn
A technician has identified an undocumented host using an IP address in a range set aside as unallocated. The technician is going to run a fingerprinting scan. What type of information could this yield about the host?
A fingerprinting scan compares specific responses to known information about hardware platforms, OS types and versions, and application/service types and versions.
You need to analyze the information saved in a .pcap file. What type of command-line tool or other utility is best suited to this task?
This type of file will contain a network packet capture.
You could use a command-line protocol analyzer such as tcpdump to display the contents, but a graphical tool such as Wireshark will make analysis easier.
A penetration tester has performed a quick service enumeration with Nmap and now wants to further enumerate the findings. Which parameter should the pen tester use in the command?
-sU
-sV
-sT
-sS
Answer: 2 (-sV)
When services get discovered, the pen tester can use Nmap with the -sV switch to probe a host more intensively to discover the software or software version operating each port.
UDP scans (-sU) scan UDP ports. As these do not use ACKs, Nmap needs to wait for a response or timeout to determine the port state, so UDP scanning can take a long time.
TCP connect (-sT) is a half-open scan that requires Nmap to have privileged access to the network driver so that it can craft packets.
TCP SYN (-sS) is a fast technique (also referred to as half-open scanning) as the scanning host requests a connection without acknowledging it.
A security analyst is reviewing UDP traffic headers. Which of the following is NOT a field in a UDP traffic header?
Source port
Destination Port
Window
Checksum
Answer: 3 (Window)
The window field is in Transmission Control Protocol (TCP) traffic, not User Datagram Protocol (UDP) traffic. It is the amount of data the host is willing to receive before sending another acknowledgment. TCP's flow control mechanism means if it is getting overwhelmed, one side can slow the sending rate.
UDP traffic has a source port field, which can be set to zero if the destination computer doesn't need to reply to the sender.
The UDP Destination Port refers to the port on the device receiving the traffic.
The checksum ensures the validity of the packet. It is also present in both TCP and UDP headers.
A server administrator is analyzing a normal Transmission Control Protocol (TCP) Teardown connection to their servers. How many FIN-WAIT states does the client go through during this process?
One
Two
Three
Four
Answer: 2 (Two)
The client goes through two FIN-WAIT states. In the first step, the client sends a FIN segment to the server and then enters the FIN-WAIT1 state.
The client does not go through one FIN-WAIT state. After the client sends a FIN, the server responds with an ACK segment and enters the CLOSE-WAIT state.
The client does not go through three FIN-WAIT states. The third step occurs when the client receives the ACK segment and enters the FIN-WAIT2 state. This is the second and final FIN-WAIT state.
The client does not go through four FIN-WAIT states. After entering the second FIN-WAIT state, the client responds with an ACK and enters the TIME-WAIT state.
A security analyst is looking at traffic from older devices between ports 2,000 - 3,000. What is this traffic most likely?
Well-known applications
Dynamic use
Client ports
Sockets
Answer: 3 (Client ports)
OS implementations of Transmission Control Protocol/Internet Protocol (TCP/IP) have not always conformed to recommendations. For example, earlier versions of Windows and UNIX/Linux used 1,024—5,000 for client ports.
Port numbers 0 through 1,023 are preassigned by the Internet Assigned Numbers Authority (IANA) to "well-known" server applications.
The remaining ports (49,152 up to 65,535) are for private or dynamic use. Also, for the server application that needs a port, each client application must assign its own port number to track its requests.
The port number is used in conjunction with the source IP address to form a socket. Each socket is bound to a software process.
A network administrator is looking at packet captures from the network and trying to isolate email traffic. Which of the following should the network administrator include? (Select all that apply.)
UDP 161
TCP 25
TCP 123
TCP 143
Answer: 2 and 4 (TCP 25, TCP 143)
Transmission Control Protocol (TCP) 25 is Simple Mail Transfer Protocol (SMTP) traffic which the network administrator should include when searching for email traffic.
TCP 143 is Internet Message Access Protocol (IMAP) traffic which would also be email traffic, and the administrator should include it as well.
User Datagram Protocol (UDP) 161 is used for simple network management protocol (SNMP). UDP 161 is considered to be a common port, but is NOT used for email traffic.
TCP 123 is not a common protocol. UDP 123 is Network Time Protocol/Simple NTP. This allows hosts to sync and set a common time, which is especially important for security.
A systems engineer is looking at running services on the company's Linux hosts and wants to include ports in the listening state in the output. Which netstat switch should the engineer use?
-a
-u
-w
-x
Answer: 1 (-a)
Using the -a switch includes ports in the listening state in the output. The netstat command allows the administrator to check the state of ports on the local host.
Netstat allows the use of switches for Internet connections for Transmission Control Protocol (-t) and User Datagram Protocol (-u). The administrator can use netstat to check for service misconfigurations, such as a host running a web or File Transfer Protocol (FTP) server that a user installed without authorization.
Using the -w switch can view raw connections. The administrator may also be able to identify suspicious remote connections to services on the local host or from the host to remote IP addresses.
The -x switch can view UNIX sockets/local server ports.
A systems administrator needs network visibility to establish the logical topology of routers and subnets. Which of the following is a lightweight standalone tool which will allow the administrator to easily scan for IPs?
PRTG
IPAM
DDI
ManageEngine
Answer: 1 (PRTG)
IP scanning uses lightweight standalone open source or commercial tools, such as Nmap, AngryIP, or PRTG. An IP scanner is a tool that performs host discovery.
Enterprise network management suites will also be able to keep a record of inventory information about each host. This functionality is often known as IP Address Management (IPAM).
Suites that integrate with Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) servers are also known as DHCP, DNS, and IPAM (DDI).
DDI vendors and solutions include ManageEngine, Infoblox, SolarWinds, Bluecat, and Men & Mice. Windows Server bundles with a DDI product.
A penetration tester wants to perform remote port scanning. Which Nmap scan fast technique as the scanning host requests a connection without acknowledging it?
-sU
-sV
-sT
-sS
Answer: 4 (-sS)
TCP SYN (-sS) is a fast technique (also referred to as half-open scanning) as the scanning host requests a connection without acknowledging it. The target's response to the scan's SYN packet identifies the port state.
UDP scans (-sU) scan UDP ports. As these do not use ACKs, Nmap needs to wait for a response or timeout to determine the port state, so UDP scanning can take a long time.
When services get discovered, the pen tester can use Nmap with the -sV switch to probe a host more intensively to discover the software or software version operating each port.
TCP connect (-sT) is a scan that requires Nmap to have privileged access to the network driver so that it can craft packets.